Chapter 11
Network Scanning and Vulnerability Scanning
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
 Understand how to verify the security of a system
Understand how to verify the security of a system Probe a system for vulnerabilities
Probe a system for vulnerabilities Use vulnerability scanning tools
Use vulnerability scanning tools Evaluate potential security consultants
Evaluate potential security consultants
Introduction
At this point, it should be clear that it is necessary to periodically assess any system for vulnerabilities. There are a variety of methods for assessment, including vulnerability scanning, penetration testing, and auditing. The first part of this chapter discusses the essential steps that you should follow in assessing a system for vulnerabilities. The purpose of this chapter is to get someone who is new to computer security to begin thinking about these issues. This chapter is not meant to provide a comprehensive treatment of the subject or be a substitute for getting an expert consultant. In fact, most security topics, such as disaster recovery, cryptography, and policies, have had entire volumes written on them. This chapter should give you a basic blueprint you can follow. Specific details will depend on your particular environment, budget, skills, and security needs. The second part of this chapter discusses various tools you can use to scan your network for vulnerabilities.
In this book, you have thus far examined a number of threats to individual computers and networks. You have also learned about specific defenses against each of these dangers. However, you have not yet looked at a comprehensive approach to security. In the second part of this chapter, you will learn about many of the security procedures that can be implemented to provide an environment with more secure computing. Note that this chapter is about overall procedures that you need to perform in securing a system rather than specific step-by-step techniques.
Basics of Assessing a System
Knowing where to begin with system security can be daunting for those new to security. To keep it simple and easy to remember, the stages of assessing a system’s security can be categorized into the six Ps:
 Patch
Patch Ports
Ports Protect
Protect Policies
Policies Probe
Probe Physical
Physical
Patch
The first rule of computer security is to check patches. This is true for networks, home computers, laptops, tablets, smart phones,…literally any computer. The operating system, database management systems, development tools, Internet browsers, and so forth all need to be checked for patches. In a Microsoft environment, this should be easy, as the Microsoft website has a utility that will scan your system for any required patches to the browser, operating system, or Office products. It is a very basic tenet of security to ensure that all patches are up to date. This should be one of the first tasks when assessing a system.
It is also important to consider the types of patches. The most important patches are labeled important or critical. (Microsoft labels them critical, but other vendors may use another designation.) These patches must be applied; without them, your system simply is not secure. Recommended patches should be applied unless you have some compelling reason not to. Finally, optional patches usually enhance or correct some minor functionality in the system but are not necessary for security. Your system will not be vulnerable without them.
While home users might benefit from automatic patching, automatic patching is not appropriate for network administrators. It is always possible that a patch might interfere with some custom software or some system configuration. Therefore, patches need to be deployed first to a test system to ensure that they do not disrupt any other software or configurations. Once the testing is complete, you can push a patch out to the production network. Even then, patches should be rolled out in stages, in case something goes wrong. This does not mean that patches are not applied in a timely manner. If there is a critical patch, it must be tested promptly so that it can be rolled out to the production network.
Fyi: Patching and Applications
Whenever there is a patch to an operating system or application, there is documentation (sometimes in a Read Me file, sometimes at the download site) that indicates what the patch is fixing and that lists any known adverse interactions with other applications. You should always read this documentation before installing a patch. In most cases, the problems are minimal and often involve obscure situations. But it is always good to ensure that a service or an application upon which you are dependent will not be adversely impacted.
Fyi: Ports on Routers
One security flaw seen in many organizations that are otherwise security conscious is a failure to close ports on routers. This is particularly a problem for large organizations with wide area networks (WANs) spread over multiple locations. The routers between locations should be filtered but too often are not.
Once you have ensured that all patches are up to date, the next step is to set up a system to ensure that they are kept up to date. One simple method is to initiate a periodic patch review during which, at a scheduled time, all machines are checked for patches. There are also automated solutions that can patch all systems in an organization. It is imperative that all machines be patched, not just the servers.
An important issue is when to patch. For home users, it is usually recommended that automatic patching be turned on so that their systems get patched as soon as patches are available. However, this is not recommended for network administrators. It is entirely possible that a particular patch might not be compatible with some software on the network. A good example occurred in May 2022, when Microsoft’s “patch Tuesday” update caused Windows Active Directory authentication errors. Microsoft stated:1
1. https://threatpost.com/microsofts-may-patch-tuesday-updates-cause-windows-ad-authentication-errors/179631/
After installing updates released May 10, 2022 on your domain controllers, you might see authentication failures on the server or client for services such as Network Policy Server (NPS), Routing and Remote Access Service (RRAS), Radius, Extensible Authentication Protocol (EAP), and Protected Extensible Authentication Protocol (PEAP).
It is recommended that you install patches on a test machine that has an identical configuration to your network’s workstations. Then after the patch has been tested, it can be pushed out to the network.
Ports
As you learned in Chapter 2, “Networks and the Internet,” all communication takes place via some port. Any port you do not explicitly need should be shut down. Any unused services on servers and individual workstations should be shut down. Both Windows (XP, Vista, 7, 8, 10, and 11) and Linux have built-in port-filtering capability. Windows 2000 Professional was the first Windows operating system to include port-filtering capability. Windows XP expanded this to a fully functional firewall. Windows 7 added a firewall that could block outgoing as well as incoming traffic and that continues to Windows 11. Shutting down a service in Windows and port filtering are both discussed in more detail in Chapter 9, “Computer Security Technology.”
You should also shut down any unused router ports in your network. If your network is part of a larger WAN, then it is likely that you have a router connecting you to that WAN. Every open port is a possible avenue of entry for malware or an intruder. Therefore, every port you close eliminates an opportunity for such attacks to affect your system.
In Practice
Shutting Down a Service in Windows
For an individual machine that is not running firewall software, you do not directly close ports; instead, you shut down the service using a port. For example, if you do not use an FTP service but you see that the FTP port is on, chances are that you have an FTP service running on that machine. In Windows (any Windows version since Windows 7, including Windows 11) or in Windows Server (any version from 2008 on), if you have administrative privileges, you can take the following two steps to shut down an unneeded service:
Go to the Control Panel and double-click Administrative Tools. (Note that in Windows 10 you go to Control Panel, click on System and Security, and double-click Administrative Tools.)
Double-click Services. You should see a window similar to the one shown in Figure 11.1.
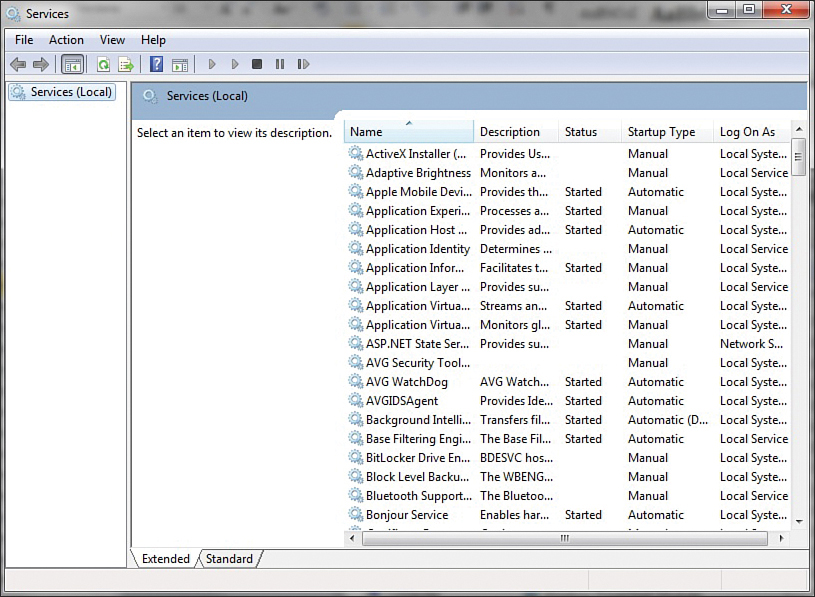
Figure 11.1 Windows services.
The window in Figure 11.1 shows all services installed on the machine, whether they are running or not. Notice that the window also displays information about whether a service is running, whether it starts up automatically, and so forth. In Windows, more information can be seen by selecting an individual service. When you double-click on an individual service in any version of Windows (Windows XP through Windows 11, Server 2003 through Server 2019), you see a dialog box similar to the one in Figure 11.2 that provides details about that service.
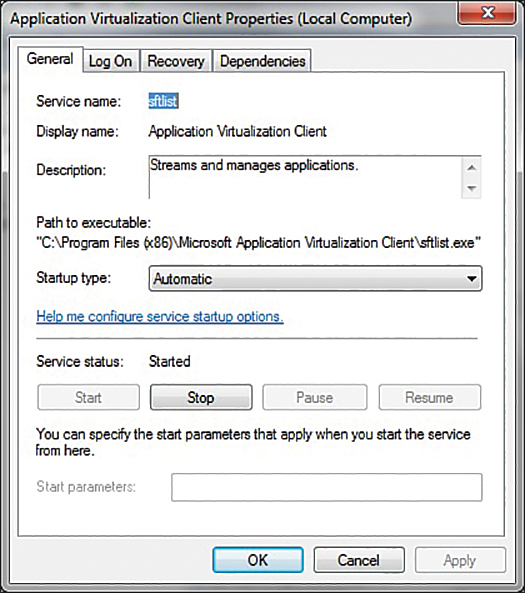
Figure 11.2 Disabled services.
In the example shown in Figure 11.1, you can see a service on a machine that does not require it. In Figure 11.2 you see how to disable that service. To illustrate the procedure, next we will walk through disabling this service. (Before you turn off any service, however, you need to check whether other services depend on the one you are about to shut off. If other services depend on the one you want to turn off and you proceed to turn it off, you will cause the other services to fail.) Follow these steps to turn off a service:
Click on the Dependencies tab. In this case, the service has no dependencies.
Click the General tab.
Change the Startup type to Disabled.
Click the Stop button in the Service status section, if necessary. Your dialog box should look similar to the one in Figure 11.2. The fax service is now shut down.
Click OK to accept the edits made and close the Properties dialog box. Close the Services dialog box and the Administrative Tools dialog box.
Shutting down unneeded ports and services is an essential and very basic part of computer security. As mentioned, every port that is open (and every service that is running) is a possible avenue for a hacker or virus to get to your machine. Therefore, keep in mind this important rule: If you don’t need it, shut it down and block it.
Of course, you should make certain you are not shutting down services you do indeed need. Some services depend on other services. Fortunately, Windows gives you information about what services depend on a given service. If you are not certain, take the time to research a service before shutting it down. You don’t want to disable software and services that you do, in fact, need.
It is often the case that one will use a system that has an identical configuration to your production workstations and that system is used as a test. Either adding patches or shutting down services should be done on a test system. Then if there are no issues, you can roll the changes out to production machines. Even after using a test system, you should roll out to production in stages rather than roll out the entire network at one time. There is always the possibility of some issue occurring.
It is a best practice to make a list of all software that you are running. Then look up the ports and protocols that you need for that software and allow only those. It is important to keep in mind that these are ports for incoming traffic. If your machine is not used as a database server, web server, or other type of server and if your machine is a stand-alone one, you can (and should) close all ports. Workstations on networks may need some ports open for network utilities. We will examine some interesting utilities later in this chapter.
Protect
The next phase of assessing a system’s security is to ensure that all reasonable protective software and devices are employed. This means, at a minimum, having a firewall between your network and the outside world (refer to Chapter 2). You should also consider using an intrusion detection system (IDS) on that firewall and any web servers. (We discussed the Snort IDS in Chapter 9.) Some security experts consider IDSs to be nonessential; you can certainly have a secure network without one. However, using an IDS is the only way to know of impending attacks; there are free, open-source IDSs available, and I highly recommend using them. A firewall and an IDS will provide basic security to your network’s perimeter, but you also need virus scanning. Each and every machine, including servers, must have a virus scanner that is updated regularly. The point has already been made that a virus infection is the greatest threat to most networks. As also previously discussed, it is probably prudent to consider installing antispyware software on all of your systems to prevent users of your network from inadvertently running spyware on the network.
In Practice
Finding a Firewall
When selecting a firewall to use, you have a number of options: You can purchase a very inexpensive router-based firewall for your high-speed Internet connection, you can get a router that is separate from your DSL or cable router, or you can get a cable or DSL router that includes a firewall. The following websites can help you find more information on these options and determine which one would best suit your needs:
 Linksys: https://www.linksys.com/ (Note: Linksys was purchased by Cisco.)
Linksys: https://www.linksys.com/ (Note: Linksys was purchased by Cisco.) Firewall Guide: www.firewallguide.com
Firewall Guide: www.firewallguide.com CDW: https://www.cdw.com/content/cdw/en/articles/security/firewall-type-comparison.html
CDW: https://www.cdw.com/content/cdw/en/articles/security/firewall-type-comparison.html
In addition to the information on the firewall options available, you can find many free or very inexpensive firewall packages on the Internet. Following is a list of six popular firewalls available via the Internet:
 Norton Personal Firewall: This product is inexpensive and is available for multiple operating systems. A free trial download is available from https://us.norton.com/feature/firewall.
Norton Personal Firewall: This product is inexpensive and is available for multiple operating systems. A free trial download is available from https://us.norton.com/feature/firewall. McAfee Personal Firewall: This product is similar in price and basic function to Norton Personal Firewall. You can find out more about this product at http://us.mcafee.com.
McAfee Personal Firewall: This product is similar in price and basic function to Norton Personal Firewall. You can find out more about this product at http://us.mcafee.com. Comodo: This product has a free version and a commercial version. See https://www.comodo.com/home/internet-security/firewall.php.
Comodo: This product has a free version and a commercial version. See https://www.comodo.com/home/internet-security/firewall.php. ZoneAlarm: This product also comes in both free and commercial versions. See https://www.zonealarm.com/pc-protection/#fw-section.
ZoneAlarm: This product also comes in both free and commercial versions. See https://www.zonealarm.com/pc-protection/#fw-section. Bitdefender Total Security: This product includes a firewall along with other security features. See https://www.bitdefender.com/solutions/total-security.html?awc=2873_1659205504_91a428fcb027d4a97b11ad7579cbaf9d.
Bitdefender Total Security: This product includes a firewall along with other security features. See https://www.bitdefender.com/solutions/total-security.html?awc=2873_1659205504_91a428fcb027d4a97b11ad7579cbaf9d. AFWall+: This firewall is for Android devices such as phones and tablets. See https://play.google.com/store/apps/details?id=dev.ukanth.ufirewall&hl=en.
AFWall+: This firewall is for Android devices such as phones and tablets. See https://play.google.com/store/apps/details?id=dev.ukanth.ufirewall&hl=en.
For medium-sized or larger networks that have more flexible budgets, you will want something more than a personal firewall. Most major network product vendors include firewalls in their products. Cisco routers and Juniper routers both include firewall capabilities. For your network’s routers and switches, you should consult the vendor documentation and ensure that you have properly configured the firewall functionality included with that device.
Finally, Linux has a built-in firewall called iptables. It is an excellent solution for any system using Linux. The first firewall widely available for Linux was called ipchains. This product worked but had limitations. It was first introduced in version 2.2 of the Linux kernel and superseded ipfwadm. The iptables service, which is now the primary firewall for Linux, was first introduced in Linux kernel 2.4. On most Linux systems, iptables is installed as /usr/sbin/iptables; however, if it was not included in the installation, you can add it later.
Policies
While policies are discussed in detail in Chapter 10, “Security Policies,” we briefly review some aspects of policies here. It is absolutely essential that any organization have clearly written policies on computer security—and that those policies be strongly enforced by management. Those policies should cover acceptable use of organizational computers, the Internet, email, and any other aspect of the system. Policies should prohibit the installation of any software on the systems. Only IT personnel should install software—and only after they have verified its safety.
Policies should also advise users against opening unknown/unexpected attachments. I recommend that people within an organization or department use a code word. If that code word does not appear in the body of an email (or in the subject line), then they do not open the attachment. Most virus attacks spread via email attachments. The subject line and body of such email messages are generated automatically by the virus itself. All of your legitimate attachments can have a code word in the subject line; it is highly unlikely that this word would be in the subject line of an email sent by a virus. This alone could prevent your users from inadvertently opening a virus.
Policies should also clearly delineate who has access to what data, how backups are performed, and what to do to recover data in the case of a disaster (commonly called a disaster recovery plan). Data access must be limited to only those personnel with an actual need to access the data. For example, not everyone in the human resources department needs access to disciplinary files on all employees. Does your organization have a plan for what to do if a fire destroys your servers and all their data? Where do you get new machines? Who gets them? Is there an offsite copy of the data backup? Such questions must be addressed in a disaster recovery plan.
There should be a policy regarding passwords: acceptable minimum length, lifetime of a password, password history, and passwords to be avoided, such as any word that has a direct connection to the user. For example, a user who is a big fan of the Dallas Cowboys should not use a password that has any relationship to that sports team. Also, passwords that relate to personal data, such as spouse’s birthday, children’s names, or pet names, are poor choices. A password policy could also include recommendations or restrictions on a password.
Fyi: Good Passwords
Many sources claim that a good password is at least 8 (preferably 15) characters long; contains letters, numbers, and characters; and combines upper- and lowercase letters. After learning about rainbow tables earlier in this book, you are probably aware that an even longer password might be needed. I usually recommend a passphrase. Start with something easy like “cheeseburgers from Burger King.” Now put it all together in one word, use some capitalization, and change some letters to numbers, and you might end up with a password like this: !l!k3ch33s3burg3rsfrombuRG 3rk1ng. You can memorize such a password with surprising ease, and it is very difficult to guess or even to crack with a rainbow table.
Additionally, a password should not be kept for long periods of time. A 90- or 180-day password replacement schedule is good for most situations. More secure environments might require 30 or even fewer days. Microsoft recommends 42 days (6 weeks). This is referred to as password age. (The frequency of required password changes, of course, must be based on the user’s access to sensitive information or data. A company financial officer might change her password weekly; a nuclear arms engineer might change his password daily; and a mail clerk might need to change her password on a much less frequent basis.) You can set many systems (including Windows) to force the user to get a new password after a certain period of time. You should also make sure the person does not merely reuse old passwords, referred to as password history and also referred to in some operating systems as uniqueness. A good rule of thumb is a history depth of five—meaning that the person cannot reuse any of her previous five passwords. Additionally, you may need to implement a minimum password age to prevent users from immediately changing their password five times to return to her current password. Generally, a minimum of 1 day is recommended.
Fyi: How Extensive Should Policies Be?
How extensive should policies be? Should they be a few brief pages or a lengthy manual? Various computer security experts have different opinions. My opinion is that the policies should be lengthy enough to cover your organizational needs but not so lengthy as to be unwieldy. In short, overly long policy manuals are likely to be left unread by employees and hence not be followed. If you absolutely must have a long policy manual, then create a few brief submanuals for specific employee groups to increase the chances of the policies being read and followed. It is probably a good idea to have new hires briefed on security policies by someone from the IT security department.
Fyi: Checklists and Policies
For your convenience and to assist in getting you started in securing your systems and establishing good policies, the SANS Institute website provides examples of checklists and policies (see www.sans.org/security-resources/policies/). Each of these is also available electronically through the companion website for this text.
Finally, policies should include specific instructions on what to do in case of an employee termination. It is imperative that all of that person’s login accounts be immediately disabled and any physical access to any part of the system be immediately discontinued. Unfortunately, many organizations fail to address this properly and end up providing opportunities for disgruntled former employees to inflict retribution on the former employer.
Probe
An important step in assessing any network is to probe the network. We will look at several probes later in this chapter. The key is to periodically probe your own network for security flaws. This should be a regularly scheduled event—perhaps once a quarter. At a minimum, a complete audit of your security should be completed once per year. That would, of course, include probing your ports. However, a true security audit would also include a review of your security policies, your patching system, any security logs you maintain, personnel files of those in secure positions, and so forth.
Physical
Finally, you cannot ignore physical security. The most robustly secure computer that is left sitting unattended in an unlocked room is not at all secure. You must have some policy or procedure governing the locking of rooms with computers as well as the handling of laptops, PDAs, and other mobile computer devices. Servers must be in a locked and secure room with as few people as is reasonably possible having access to them. Backup tapes should be stored in a fireproof safe. Documents and old backup tapes should be destroyed before disposal (for example, by melting tapes, magnetizing hard disks, destroying external storage devices, and so on).
Physical access to routers and hubs should also be tightly controlled. Having the most high-tech, professional information security on the planet but leaving your server in an unlocked room to which everyone has access is a recipe for disaster. One of the most common mistakes in the arena of physical security is co-locating a router or switch in a janitorial closet. This means that, in addition to your own security personnel and network administrators, the entire cleaning staff has access to your router or switch, and any one of them could leave the door unlocked for an extended period of time.
There are some basic rules you should follow regarding physical security:
 Server rooms: The room where servers are kept should be the most fire-resistant room in the building. It should have a strong door with a strong lock, such as a deadbolt. Only those personnel who actually have a need to go in the room should have a key. You might also consider a server room log wherein each person logs in when she enters or exits the room. There are actually electronic locks that record who enters a room, when she enters, and when she leaves. You may also wish to consider using biometric locks on critical areas such as server rooms. Consult local security vendors in your area for more details on price and availability.
Server rooms: The room where servers are kept should be the most fire-resistant room in the building. It should have a strong door with a strong lock, such as a deadbolt. Only those personnel who actually have a need to go in the room should have a key. You might also consider a server room log wherein each person logs in when she enters or exits the room. There are actually electronic locks that record who enters a room, when she enters, and when she leaves. You may also wish to consider using biometric locks on critical areas such as server rooms. Consult local security vendors in your area for more details on price and availability. Workstations: Every workstation should have an engraved identifying mark. You should also routinely inventory them. It is usually physically impossible to secure them as well as you secure servers, but you can take a few steps to improve their security. Some companies choose to attach the workstations to the desks with cables. This can be effective and affordable.
Workstations: Every workstation should have an engraved identifying mark. You should also routinely inventory them. It is usually physically impossible to secure them as well as you secure servers, but you can take a few steps to improve their security. Some companies choose to attach the workstations to the desks with cables. This can be effective and affordable. Miscellaneous equipment: Projectors, CD burners, laptops, and so forth should be kept under lock and key. Any employee who wishes to use one should be required to sign it out, and it should be checked to see that it is in proper working condition and that all parts are present when it is returned.
Miscellaneous equipment: Projectors, CD burners, laptops, and so forth should be kept under lock and key. Any employee who wishes to use one should be required to sign it out, and it should be checked to see that it is in proper working condition and that all parts are present when it is returned.
Having appropriate locks on doors is important. Locks that work with a passkey or swipe card that records who opened the door and when are recommended. Such recording of physical access should be done at least for sensitive areas like server rooms. Video monitoring has become quite inexpensive, and cameras can provide high-definition and night vision, as well as backup to the cloud. Such systems are even commonly found in homes.
Securing Computer Systems
In this section, we will examine various security specifics for an individual workstation, a server, and a network. You should be aware, however, that you do not need to reinvent the wheel. A number of very reputable organizations, including the following, have put together step-by-step guides, or security templates, that you can use in your network setting:
 National Security Agency: The NSA’s website offers a number of specific network security guides. See https://nsacyber.github.io/publications.html.
National Security Agency: The NSA’s website offers a number of specific network security guides. See https://nsacyber.github.io/publications.html. Center for Internet Security (CIS): CIS offers a number of security guides and benchmarks at https://www.cisecurity.org.
Center for Internet Security (CIS): CIS offers a number of security guides and benchmarks at https://www.cisecurity.org. SANS Institute: SANS has a number of sample policies you can download and use or modify. See www.sans.org/resources/policies/.
SANS Institute: SANS has a number of sample policies you can download and use or modify. See www.sans.org/resources/policies/.
You can modify these resources to fit your particular organization or use them as a starting point in forming your own security strategy.
There are also templates that can be applied to many operating systems and applications (such as Microsoft Windows and Microsoft Exchange) that will implement certain security precautions. These templates can be found for many products and then simply installed on the appropriate machine. Some security professionals prefer to handle the details of security themselves, but many administrators find these templates to be useful—and they can be invaluable for the beginner.
 Windows security templates: https://support.microsoft.com/en-us/kb/816585
Windows security templates: https://support.microsoft.com/en-us/kb/816585 Understanding Windows templates: http://www.windowsecurity.com/articles-tutorials/misc_network_security/Understanding-Windows-Security-Templates.html
Understanding Windows templates: http://www.windowsecurity.com/articles-tutorials/misc_network_security/Understanding-Windows-Security-Templates.html
The use of these templates will at least give you a baseline of security on the applications to which they are applied.
Securing an Individual Workstation
There are a number of steps that any prudent individual can take to make his own computer secure. These steps should be taken for both home computers and workstations on a network. In the former case, securing the individual computer is the only security option available. In the latter case, securing the individual computers as well as the perimeter allows for a layered approach to security. While some network administrators simply secure the perimeter via a firewall and/or proxy server, it is generally believed that you should also secure each machine in your organization. This is particularly vital in protecting against virus attacks and some of the distributed denial of service attacks that you learned about in Chapter 4, “Denial of Service Attacks.”
Fyi: Hardening a System
The process of securing a computer system against hackers, malware, and other intruders is sometimes referred to as hardening a system. You may see the terms server hardening and router hardening commonly used.
The first step with an individual computer is to ensure that all patches are appropriately applied. Microsoft’s website has utilities that will scan your machine for needed patches for both Windows and Microsoft Office. It is critical that you do this on a regular basis—once per quarter as a minimum. You should also check your other software vendors to see whether they have some similar mechanism to update patches for their products. It is amazing how many virus outbreaks have been widespread despite patches being available to secure the flaws they exploited. Too many people simply do not ensure that patches are applied regularly. For a home computer, this is the most critical step in your security strategy and will protect you from a number of attacks designed to exploit security flaws. For a networked workstation, this is still a vital piece of the overall security strategy and cannot be ignored.
The second step in securing an individual computer is restricting the ability to install programs or alter the machine configuration. In a network environment, this would mean that most users do not have permissions to install software or change system settings. Only network administrators and designated support staff should have that ability. In a home environment, this would mean that only a responsible party or parties (such as the parents) have access rights to install software.
One of the reasons for this particular precaution is to prevent users from accidentally installing a Trojan horse or other malware on their machine. If a person is prevented from installing any software, then there is no chance of inadvertently installing improper software such as a Trojan horse, adware, or other malware. Blocking users from altering the machine’s configuration also prevents them from changing system security settings. Novice users may hear of some way to change some setting and will do so, not realizing the security risks they are exposing their system to.
A perfect example in which a novice might adversely alter security settings involves the Windows Messenger service. This is not used for chat rooms or instant messaging, as many novices incorrectly assume. It is instead used for network administrators to send a broadcast message to all people on a network. Unfortunately, some adware programs also use that service to circumvent pop-up blockers and inundate you with ads. Thus, a security-conscious person might disable that service. You would not want an inexperienced person to turn it back on by thinking it is needed for instant messaging.
It is absolutely critical in any network environment that limits be placed on what the average user can do to a machine’s configuration. Without such limits, even well-meaning employees could eventually compromise security. This particular step is often met with some resistance from the organization. If you are in charge of a system’s security, it is your job to educate the decision makers as to why this step is so critical.
The next step has been discussed previously in this book. Each and every computer must have antivirus and antispyware software. You must also set it to routinely automatically update its virus definitions. Updated, running antivirus software is an integral part of any security solution. The two-pronged approach of antispyware and antivirus software should be a major component in your individual computer security strategy. Some analysts feel that antispyware is a nice extra but not a critical component. Others contend that spyware is a rapidly growing problem and will probably eventually equal or surpass the dangers of virus attacks.
Of course, if your operating system has a built-in firewall, it is a good idea to configure it and have it turned on. Windows (10 and 11) and Linux both come with built-in firewall features. Turn them on and configure them properly. The only significant problem you may encounter in implementing this step is that most networks require a certain amount of traffic between key servers (such as the DNS server) and individual computers. When you configure your firewall, make certain you are allowing appropriate traffic through. If you are at home, you can simply block all incoming traffic. If you are on a network, you must identify what traffic you need to allow.
Passwords and physical security, as discussed earlier in this chapter, are a critical part of computer security. You must ensure that all users utilize passwords that are at least eight characters long and consist of a combination of letters, numbers, and characters. In general, make sure that your password policy is complete and that all employees follow it. This will ensure that your physical security system is sound.
Following these guidelines will not make your computer totally impervious to danger, but these guidelines will make your workstation as secure as it reasonably can be. Remember that, even in a network environment, it is critical to also secure each computer as well as the perimeter.
Securing a Server
The core of any network is its servers—database servers, web servers, DNS servers, file and print servers, and so on. These computers provide the resources for the rest of the network. Generally, your most critical data will be stored on these machines. This means that these computers are an especially attractive target for intruders, and securing them is of paramount importance.
Essentially, to secure a server, you should apply the same steps that you would apply to any workstation and then add additional steps. There will not be a user on that machine routinely typing documents or using spreadsheets, so extra-tight restrictions are unlikely to cause the same difficulties for end users that they might on a workstation.
To begin with, you must follow the same steps you would for a workstation. Each and every server should have its software routinely patched. It should also have virus-scanning software and perhaps antispyware as well. It is critical that access to these machines, both via logging on and physical access, be limited to only those people with a clear need. There are, however, additional steps you should take with a server that you might not take with a standard workstation.
Most operating systems for servers (for example, Windows 2019 Server, Linux) have the ability to log a variety of activities. These activities would include failed logon attempts, software installation, and other activities. You should make sure that logging is turned on and that all actions that might pose a security risk are logged. You then must make certain that those logs are checked on a periodic basis.
Remember that the data on a server is more valuable than the actual machine. For this reason, data must be backed up on a regular basis. A daily backup is usually preferred but, in some cases, a weekly backup might be adequate. The backup tapes should be kept in a secure offsite location (such as a bank safety deposit box) or in a fireproof safe. It is critical that you limit access to those backup tapes just as you would limit access to the servers themselves.
With any computer, you should shut down any service you do not need. However, with a server, you may wish to take the extra step of uninstalling any software or operating system components you do not need, meaning that anything not required for the server to function should be removed. But think carefully about this before proceeding. Clearly, games and office suites are not needed for a server. However, a browser might be necessary to update patches.
There is another step that should be taken with servers that is not necessary with workstations. Most server operating systems have built-in accounts. For example, Windows has built-in administrator, guest, and power user accounts. Any hacker who wants to try to guess passwords will begin by trying to guess the passwords that go with these standard users. In fact, there are utilities on the Web that will do this automatically for the would-be intruder. First, you should create your own accounts with names that do not reflect their level of permission. For example, disable the administrator account and create an account called basic_user. Set up basic_user as the administrator account, with appropriate permissions. (Of course, only give that username and password to those people you want to have administrator privileges.) If you do this, a hacker would not immediately guess that this account is the one that he wants to crack. Remember, hackers ultimately want administrative privileges on a target system; concealing which accounts have those privileges is a vital step in preventing the hacker from breaching your security.
Fyi: Handling Old Backup Media
Unfortunately, many network administrators simply throw old backup media in the trash. Persons with malicious intent who retrieve this discarded media could restore it to their own machine. This could give them access to your older data without breaking in to your system or could give them very valuable clues as to your current security practices, depending on what is found on that media. Old media (tapes, DVDs, hard disks) should be thoroughly destroyed. For a DVD, this means physically breaking it. For a tape, this means partially or completely melting it. Hard disks should be magnetized with a powerful magnet.
There are a variety of Registry settings in any version of Windows that can be altered to increase your security. If you use a scanning tool, such as Cerberus, it returns a report stating the weaknesses in your Registry settings. What items in the Registry settings might cause security problems? A few items that are commonly examined include the following:
 Logon: If your Registry is set so that the logon screen shows the last user’s name, you have done half of the hacker’s work for her. Since she now has a username, she only needs to guess the password.
Logon: If your Registry is set so that the logon screen shows the last user’s name, you have done half of the hacker’s work for her. Since she now has a username, she only needs to guess the password. Default shares: Certain drives/folders are shared by default. Leaving them shared like this presents a security hazard.
Default shares: Certain drives/folders are shared by default. Leaving them shared like this presents a security hazard.
These are just a few of the potential problems in the Windows Registry. A tool such as Cerberus will not only tell you what the problems are but will make recommendations for corrections. To start the Registry editor, go to Start, select Run, and then enter regedit. You can then edit the Registry.
Securing a Network
Obviously, the first step in securing a network is to secure all computers that take part in that network, including all workstations and servers. However, this is just one part of network security. By now it should be clear that using a firewall and proxy server are also critical elements in network security. Chapter 12, “Cyber Terrorism and Information Warfare,” provides more details on these devices. For now, it is important to realize that you need to have them. Most experts also recommend using an IDS. There are a number of such systems available—and some are even free. These systems can detect things, such as port scanning, which might indicate that a person is preparing to attempt a breach of your security perimeter.
If your network is at all large, then you might consider partitioning it into smaller segments with a firewall-enabled router between segments. Of course, “large” is a vague term, and you will have to decide if your network is large enough to require partitioning. In this way, if one segment is compromised, the entire network will not be compromised. In this system, you might consider putting your most important servers (database, file) on a secure segment.
Because web servers must be exposed to the outside world and are the most common point of attack, it then makes sense to separate them from the rest of the network. Many network administrators will put a second firewall between the web server and the rest of the network. This means that if a hacker exploits a flaw in your web server and gains access to it, then he will not have access to your entire network. This brings up the issue of what should be on your web server. The answer is: only what you need to post web pages. No data, documents, or other information should be stored on that server, and certainly no extraneous software. The operating system and web server software are all that are required. You may add a few other items (such as an IDS) if your situation requires it. Any other software running on that server is a potential security risk.
Another concept you should consider is the DMZ (which stands for demilitarized zone). A DMZ essentially involves two firewalls: one outer and one inner. Resources that must be accessible to the outside world are between the two firewalls. The outer firewall is more permissive, and the inner firewall is highly restrictive. There are even routers that include this functionality in a single box. By plugging into certain ports, you are adding a device either behind the inner firewall or in the DMZ. This is shown in Figure 11.3.

Figure 11.3 DMZ.
You must also have policies that guide users in how to use the system, as we discussed earlier in this chapter. The most robust security in the world will not be of much use if a careless user inadvertently compromises your security. Keep in mind that you must have policies in place that guide users in what is considered appropriate use of the system and what is not.
Just as you take steps to harden your servers (such as patching the operating system and shutting down unneeded services), you should also harden your router. The specifics of what needs to be done will be contingent on your particular router manufacturer and model, but a few general rules should be followed:
 Use good passwords: All routers are configurable. They can be programmed. Therefore, you must obey the same password policies on a router that you would use on any server, including minimum password length and complexity, age of password, and password history. If your router allows you to encrypt the password (as Cisco and other vendors do), then do it.
Use good passwords: All routers are configurable. They can be programmed. Therefore, you must obey the same password policies on a router that you would use on any server, including minimum password length and complexity, age of password, and password history. If your router allows you to encrypt the password (as Cisco and other vendors do), then do it. Use logging: Most routers allow for logging. You should turn this on and monitor it just as you would monitor server logs.
Use logging: Most routers allow for logging. You should turn this on and monitor it just as you would monitor server logs. Security rules: Some basic router security rules should also be followed:
Security rules: Some basic router security rules should also be followed: Do not answer to Address Resolution Protocol (ARP) requests for hosts that are not on the user local area network (LAN).
Do not answer to Address Resolution Protocol (ARP) requests for hosts that are not on the user local area network (LAN). If no applications on your network use a given port, that port should be also shut down on the router.
If no applications on your network use a given port, that port should be also shut down on the router. Packets not originating from inside your LAN should not be forwarded.
Packets not originating from inside your LAN should not be forwarded.
These rules are simply a beginning. You will need to consult your vendor’s documentation for additional recommendations. You must absolutely pay as much attention to securing your router as you do to securing your servers. The following links might be helpful:
 Router security: www.mavetju.org/networking/security.php
Router security: www.mavetju.org/networking/security.php Cisco router hardening: https://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
Cisco router hardening: https://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
Scanning Your Network
The only way to be sure your network is secure is to actually check for vulnerabilities and flaws. In this section, we will look at some commonly used vulnerability scanners. These tools can be an invaluable asset for any network administrator.
NESSUS
Nessus (www.Nessus.org) is the premiere network vulnerability scanner. There was formerly a free version for personal use and a commercial version. It is now only available for a fee. This is perhaps the most widely used vulnerability scanner available today. It is not nearly as simple to use as MBSA but has many more capabilities. We will explore the basic functionality. If you have an interest in learning more about Nessus, then it is recommended that you consult the documentation available at the Nessus website.
Nessus is a well-known vulnerability scanner. It has been used for many years. Unfortunately, it is not free. The license, which costs over $3300 per year, can be obtained from https://www.tenable.com. Its price has been a barrier for many penetration testers. The primary advantage of Nessus is that the vendor is constantly updating the vulnerabilities it can scan for. Nessus also has a very easy-to-use web interface, as shown in Figure 11.4.

Figure 11.4 Nessus main screen.
If you click New Scan, you are given a number of options, as shown in Figure 11.5.
Figure 11.5 Nessus scan options.
You can select Basic Network Scan to see a number of intuitive basic settings. You have to name your scan and select a range of IP addresses, as shown in Figure 11.6.

Figure 11.6 Nessus basic network scan options.
Then you can either schedule the scan to run later or launch it right away. Nessus scans can take some time to run because they are quite thorough. The results are presented in a very organized screen, as illustrated in Figure 11.7.
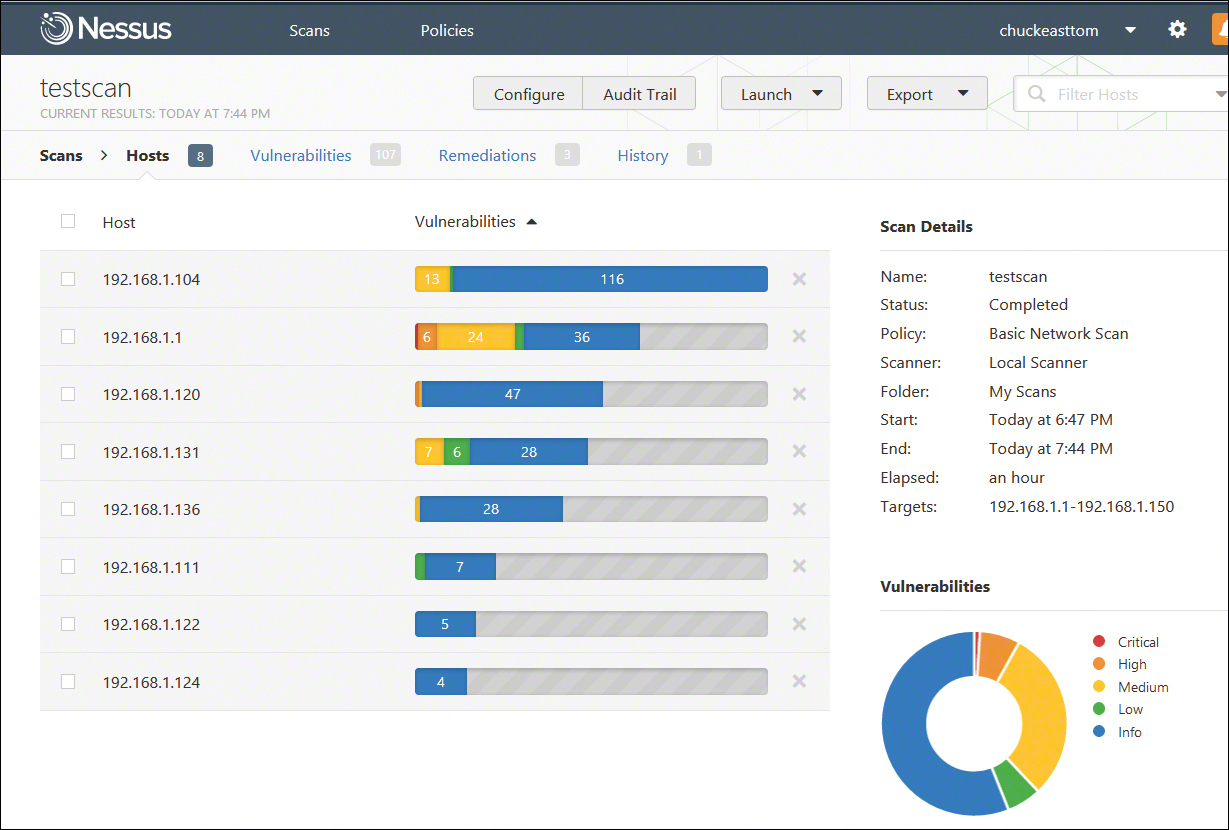
Figure 11.7 Nessus results.
You can then drill down on any item of interest. If you double-click on a specific IP address, you can see details for that address, as illustrated in Figure 11.8.

Figure 11.8 Drilling down into Nessus results.
You can then double-click on any individual item for more details about the issues and how to remediate them.
OWASP Zap
The Open Web Application Security Project (OWASP) is the standard for web application vulnerability. OWASP offers a free vulnerability scanner called the Zed Attack Proxy, commonly known as OWASP ZAP. You can download it from https://www.zaproxy.org/download/. The interface, shown in Figure 11.9, is very easy to use.
Just type in the URL of the site you wish to scan and click Attack. After a few moments, the results are displayed at the bottom of the screen. You can then expand any item. If you click on a specific item, details are loaded as shown in Figure 11.10.
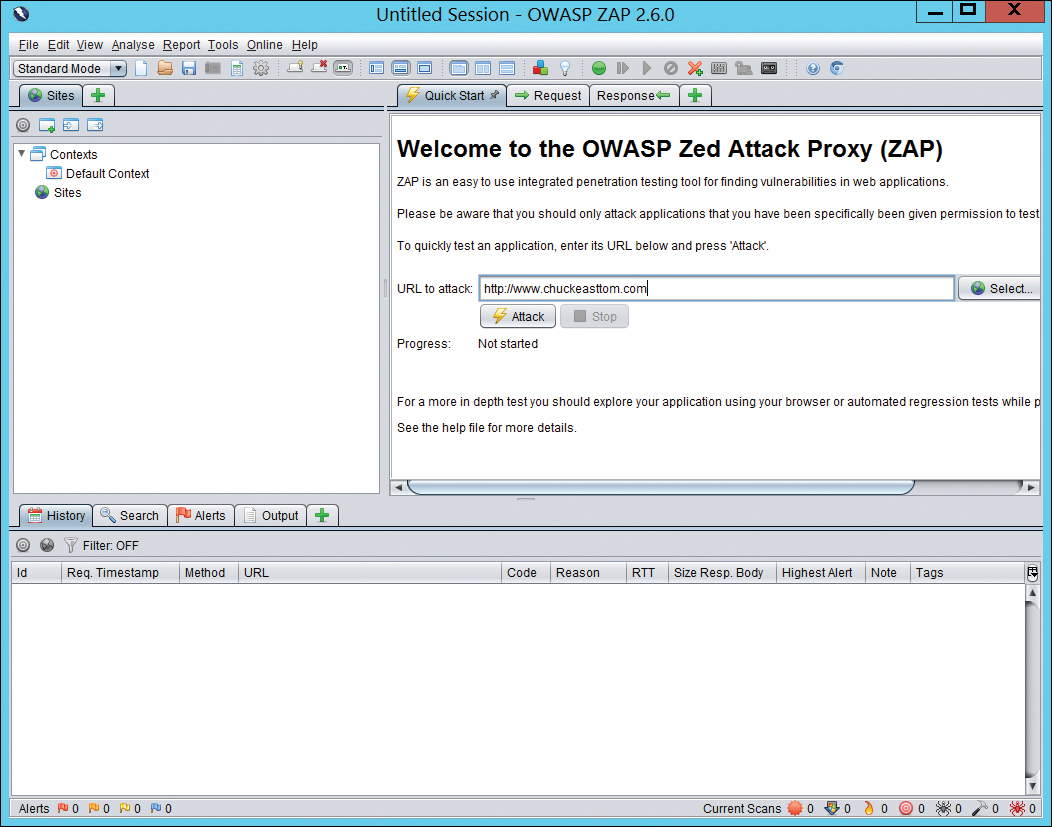
Figure 11.9 OWASP ZAP main screen.
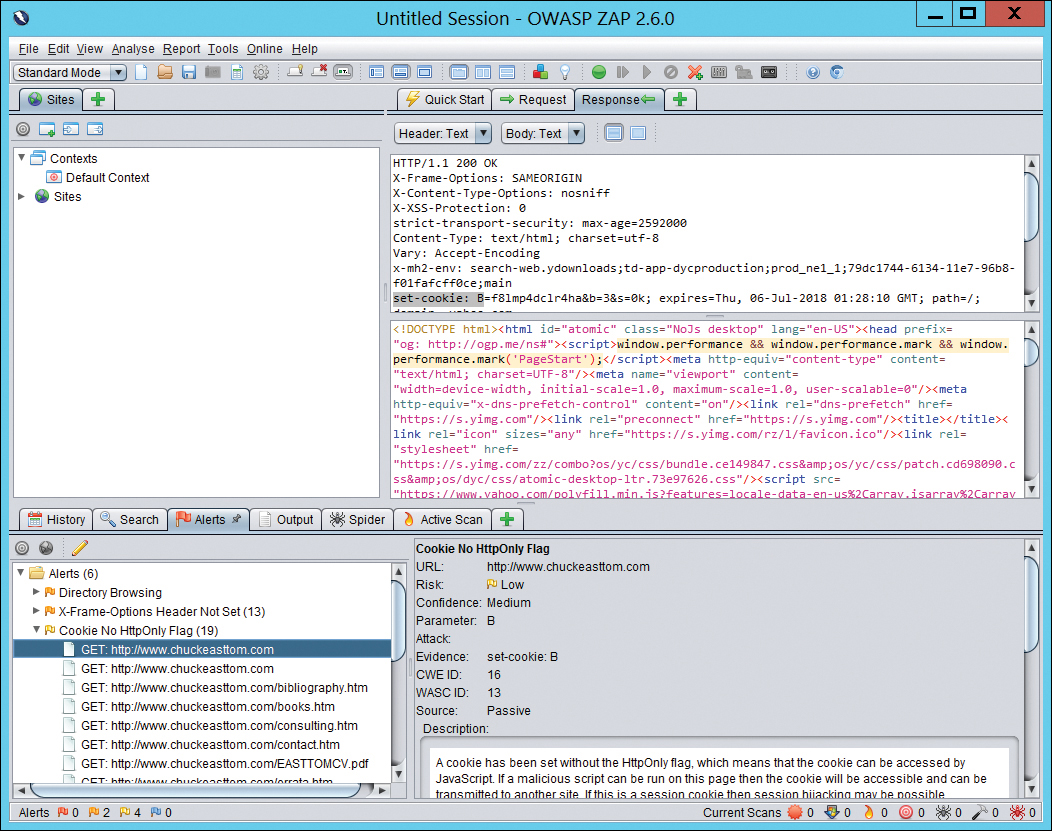
Figure 11.10 OWASP ZAP results.
OWASP ZAP is a very easy-to-use tool. The basics can be mastered in a few minutes. And given that OWASP is the organization that tracks web application vulnerabilities, it is a very good source for testing the vulnerabilities of a website.
Shodan
The Shodan tool is widely used by black hat hackers and security professionals alike. The website https://www.shodan.io is essentially a search engine for vulnerabilities. You need to sign up for a free account to use it, but then it can be invaluable to a pen tester trying to identify vulnerabilities. Of course, the site can also be invaluable to attackers. You can see the website in Figure 11.11.

Figure 11.11 Shodan.io.
Shodan allows you to search using a number of options, including the following:
 Search for default passwords, using search terms such as the following:
Search for default passwords, using search terms such as the following: default password country:US
default password country:US default password hostname:chuckeasttom.com
default password hostname:chuckeasttom.com default password city:Chicago
default password city:Chicago
 Find Apache servers, using search terms such as the following:
Find Apache servers, using search terms such as the following: apache city: “San Francisco”
apache city: “San Francisco”
 Find webcams, using search terms such as the following:
Find webcams, using search terms such as the following: webcamxp city:Chicago
webcamxp city:Chicago
 OLD IIS, using search terms such as the following:
OLD IIS, using search terms such as the following: “iis/5.0”
“iis/5.0”
With Shodan you can use a number of filters, including these:
 city: Find devices in a specific city.
city: Find devices in a specific city. country: Find devices in a specific country.
country: Find devices in a specific country. geo: Specify coordinates (such as latitude and longitude).
geo: Specify coordinates (such as latitude and longitude). hostname: Find values that match a specific hostname.
hostname: Find values that match a specific hostname. net: Search based on an IP address or an /x CIDR address.
net: Search based on an IP address or an /x CIDR address. os: Search based on operating system.
os: Search based on operating system. port: Find particular ports that are open.
port: Find particular ports that are open. before/after: Find results within a specified time frame.
before/after: Find results within a specified time frame.
For example, Figure 11.12 shows the results of a search for default password city:Miami.

Figure 11.12 Shodan search results.
When you are performing a penetration test, it is a good idea to search Shodan for your company domain to find information that can guide your penetration testing efforts. Of course, would-be attackers can also use Shodan to find the same information. You can restrict your search to the hostname or domain name of a client who has hired you to conduct a penetration test. You can use Shodan to seek out default passwords, old web servers, unsecured web cameras, and other vulnerabilities in the target network.
The search shown in Figure 11.12 was conducted using the free version of Shodan. Shodan also offers a paid version that starts at $69 and provides additional tools. There are also small business and corporate memberships available at a higher price.
Kali Linux
Kali Linux is a Linux distribution that comes packed with open-source tools for cybersecurity, digital forensics, and penetration testing. There are several scanners in Kali Linux you should be familiar with, as described in the sections that follow.
Lynsis
Lynsis is a host-based, open-source security auditing application that can evaluate the security profile and posture of Linux and other UNIX-like operating systems. This tool comes installed with the Kali Linux distribution. Figure 11.13 shows a basic scan process with Lynsis.
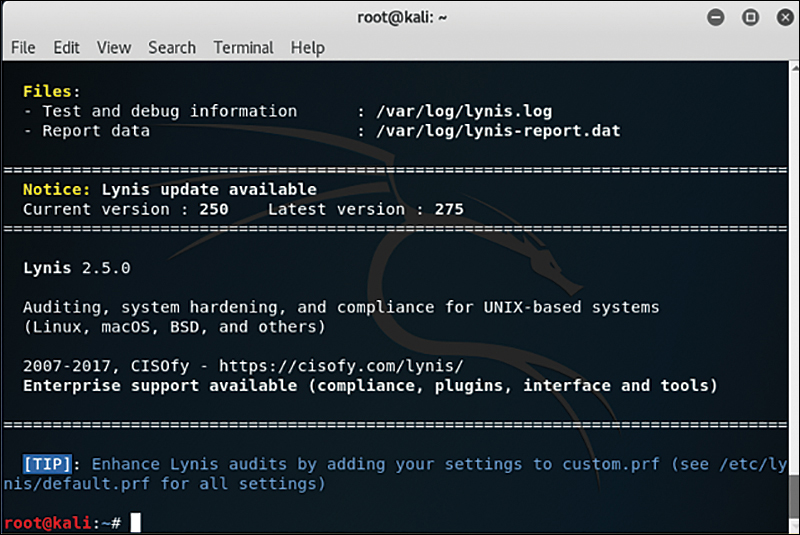
Figure 11.13 Lynsis scan.
Nikto
Nikto is a Kali Linux tool that scans websites for common vulnerabilities. There is no convenient graphical user interface; rather, you run Nikto from the Linux shell, and it is very simple to learn and use. You can see Nikto being used to scan my website in Figure 11.14.
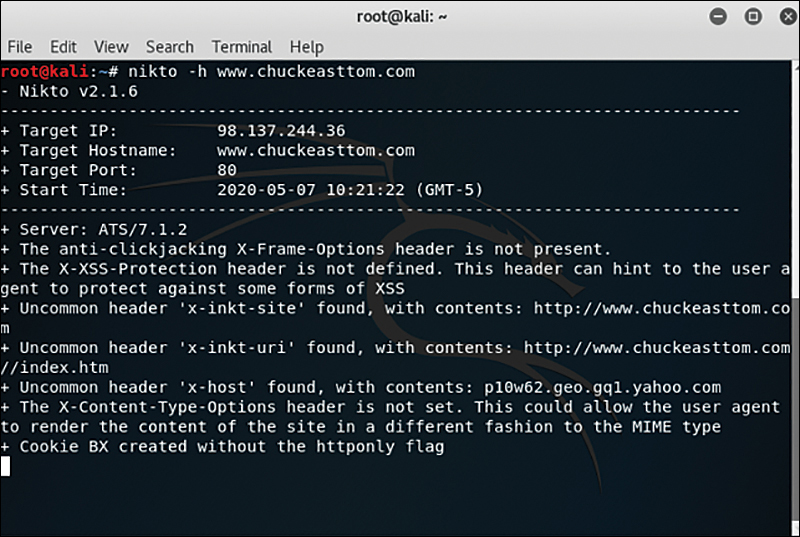
Figure 11.14 Nikto scan.
The options with Nikto are easy to understand and use. For example, you can scan a group of IP addresses by just putting them all in a text file and using the command nikto -h targetIP.txt.
You can choose from several formats for output:
 csv: Comma-separated-values format
csv: Comma-separated-values format htm: HTML format
htm: HTML format nbe: Nessus NBE format
nbe: Nessus NBE format sql: Generic SQL format
sql: Generic SQL format txt: Plain text
txt: Plain text xml: XML format
xml: XML format
If not specified, the format is taken from the file extension that is passed to -output.
Sparta
Sparta is a vulnerability scanner that comes with Kali Linux and includes a number of other tools all in one package, including:
 Mysql-default
Mysql-default Nikto
Nikto Snmp-enum
Snmp-enum Smtp-enum-vrfy
Smtp-enum-vrfy Snmp-default
Snmp-default Snmp-check
Snmp-check
Sparta also has an easy-to-use graphical user interface. Figures 11.15 through 11.17 show a basic Sparta scan.

Figure 11.15 Sparta step 1.

Figure 11.16 Sparta step 2.

Figure 11.17 Sparta step 3.
Vega
Vega, like OWASP ZAP, is a scanner for web applications. It is free and open source. Using both OWASP ZAP and Vega on your web applications will help validate your findings. You can download Vega from https://subgraph.com/vega/download/. As with OWASP ZAP, you only need to type in the URL and select the modules, and Vega does the rest, as shown in Figure 11.18.

Figure 11.18 Vega scan.
OpenVAS
OpenVAS is an open-source vulnerability scanner that was created by Greenbone Networks. The OpenVAS framework includes several services and tools that enable you to perform detailed vulnerability scanning against hosts and networks. OpenVAS can be downloaded from https://github.com/greenbone/openvas-scanner, and the documentation can be accessed at https://docs.greenbone.net/#user_documentation.
OpenVAS also includes an API that allows you to programmatically interact with its tools and automate the scanning of hosts and networks. The OpenVAS API documentation can be accessed at https://docs.greenbone.net/#api_documentation.
Running OpenVAS is very easy. The result screen will prompt you to purchase the full version by upgrading to a pro account, but you can ignore that if you wish and continue using the free version (see Figure 11.19).

Figure 11.19 OpenVAS results.
Testing and Scanning Standards
Specific standards are relevant to vulnerability scans and penetration tests. Some of the more prominent standards are briefly discussed in this section.
NIST 800-115
NIST 800-115, “Technical Guide to Information Security Testing and Assessment,” is a general guide for testing—not just penetration testing. This standard covers items one would include as part of a system audit, such as document review, log review, and similar items. However, the standard also covers items that should be included in both penetration tests and vulnerability scans. Most importantly, NIST 800-115 uses three specific phases:
 Planning
Planning Execution
Execution Post-execution
Post-execution
This may seem like a rather simplified plan, but these phases are described in detail in the NIST 800-115 documentation. In fact, the standard recommends specific tools, many of which you have seen in this chapter already.
NSA-IAM
The National Security Agency InfoSec Assessment Methodology (NSA-IAM) is an excellent guide for penetration tests. The document describes three general phases, each subdivided into specific tasks:
 Pre-assessment
Pre-assessment Determine and manage the customer’s expectations
Determine and manage the customer’s expectations Gain an understanding of the organization’s information criticality
Gain an understanding of the organization’s information criticality Determine customer’s goals and objectives
Determine customer’s goals and objectives Determine the system boundaries
Determine the system boundaries Coordinate with customer
Coordinate with customer Request documentation
Request documentation
 On-site assessment
On-site assessment Conduct opening meeting
Conduct opening meeting Gather and validate system information (via interview, system demonstration, and document review)
Gather and validate system information (via interview, system demonstration, and document review) Analyze assessment information
Analyze assessment information Develop initial recommendations
Develop initial recommendations Present out-brief
Present out-brief
 Post-assessment
Post-assessment Additional review of documentation
Additional review of documentation Additional expertise
Additional expertise Report coordination
Report coordination
The NSA-IAM has three levels of security testing. Assessment Level I involves reviewing policies and procedures; it is essentially an audit. Assessment Level II involves the use of tools for diagnosing and finding flaws; this is a vulnerability scan. Assessment Level III involves red team exercises; this is where the penetration testing occurs. So you can see that audits, vulnerability scans, and penetration tests are all covered in this standard.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is the standard used by Visa, MasterCard, American Express, and Discover. There are in fact a great many parts to the standard, but here we will focus on the penetration testing part. Obviously, if you have a system that deals with credit cards, this is an important standard.
The main focus of PCI DSS is the security controls and objectives that companies that process credit cards should implement. Security auditing and penetration testing are done to ensure that such controls are implemented and the objectives are met. You need a basic understanding of PCI DSS in order to truly understand a PCI DSS penetration test.
National Vulnerability Database
The National Vulnerability Database is not a standard but rather a database of known vulnerabilities. When checking your network for vulnerabilities, it should be rather clear that you need to check for known vulnerabilities. An excellent place to start is the National Vulnerability Database, which is a U.S. government repository of vulnerability data that uses the Security Content Automation Protocol (SCAP, pronounced “ess-cap”). The National Vulnerability Database is essentially a set of open standards that allows interoperability among vulnerability scanners. The SCAP protocol is used to enable automated vulnerability management. It can also be used to support policy compliance, including compliance with the Federal Information Security Modernization Act of 2002 commonly referred to as FISMA. You can view the NVD website in Figure 11.20.

Figure 11.20 National Vulnerability Database website.
Getting Professional Help
You may decide that you need outside help to set up and test your system’s security. This option is one that most security professionals would highly recommend if at all possible, particularly if you are new to security. It can be extremely helpful to get a professional consultant to assist you in setting up your initial security strategy and policies and perhaps do a periodic audit of your security. As mentioned in Chapter 1, “Introduction to Computer Security,” there are a number of people who claim to be hackers who are not. Frankly, there are also a number of self-proclaimed security experts who simply do not have the requisite skills. The question here is: How do you determine whether an individual is qualified? Following are some guidelines to consider in making this decision.
Experience is the most important factor when looking for a security professional. You want someone with a minimum of 5 years of IT experience, with 2 years related to security. Often, this will be a network administrator or programmer who has moved into security. Note that this is a minimum level of experience. More experience is always better. It is certainly possible that someone with less experience might have the requisite skill, but it is unlikely. Everyone needs a place to start, but you do not want your systems to be the place where someone is learning.
The quality of the person’s experience is as important as the length of experience. Ask details about the person’s experience. For example, exactly what role did she play in computer security? Did she simply set up policies, or did she actually do hands-on security work? What was the result? Was her system free from virus infections and hacker breaches or not? Can you contact her references? In short, simply because a person states that she was responsible for information security on her resume is not enough. You need to find out exactly what she did and what the results were.
Another important aspect of a security professional is education. Remember that computer security is a very broad subject. One needs an understanding of networks, protocols, programming, and more. It is entirely possible for a person with no formal education to have these skills, but it is less likely than if they had a formal education. Generally, these skills will most likely be found in a person with experience and a degree in a computer- or math-related field. That may sound somewhat intellectually snobbish, but it is a fact. There are many people in IT who are self-taught, such as people with history degrees who are network administrators or psychology majors who are now programmers. However, the more areas a person focuses in, the harder it is to obtain mastery. This is not to say that a person cannot be a security professional without a computer science, math, or engineering degree. The point is simply that this is one factor you should consider. If someone has an unrelated degree but meets or exceeds all other qualifications, you might still consider him. Some colleges are beginning to offer security-specific curriculum, and a few even offer security degrees. Clearly, specific training in computer security would be the most preferable security background.
Certifications have become very controversial in the IT profession. Some people swear by them. You can easily find many job advertisements that demand certain certifications, such as the CNE (Certified Novell Engineer) or MCITP (Microsoft Certified Information Technology Professional). Cisco certifications are also common (for example, Cisco Certified Network Associate through Cisco Certified Internetworking Engineer). On the other hand, you would have no problem finding some IT professionals who denigrate certifications and consider them utterly worthless. That second position stems from the fact that there are some people who hold certifications who don’t have the skills one would expect. But that is true of any credential. There are medical doctors who are incompetent. But if you need medical help, your odds are much better if you consult someone who has a medical degree. Employers often take this approach to hiring. If they only interview those with certain degrees or certifications, then they have a higher chance of interviewing qualified candidates.
A more reasonable position is somewhere between the two extremes. A certification can be a good indicator of a candidate’s knowledge of a specific product. For example, if you want someone to secure your Microsoft network, looking at people who are Microsoft certified is not a bad idea. You should balance that, however, by keeping in mind that it is entirely possible for someone with a good memory to use the various study guides available on the Internet and pass a test they don’t actually understand. That is where experience comes in. A certification coupled with appropriate experience is a good indicator of skill. Put another way, a certification in and of itself is not enough. But a combination of one or more certifications with experience and perhaps a related degree can be a strong indicator of technical skills.
In addition to the certifications for network administrators, there are a number of security-related certifications. Some have more credibility than others. The Security+ exam from CompTIA and the CIW Security Analyst are both conceptual exams. This means that they test a candidate’s knowledge of security concepts and not their ability to actually implement a security solution. By themselves, they may not indicate the skill level you need. But if, for example, you are securing a network using Novell, a candidate who is a CNE and has CIW Security Analyst or Security+ might be a good person to consider. It should be noted that CompTIA has recently added the Certified Advanced Security Practitioner (CASP), which is designed for those with 10 years of experience in security.
The most respected security certification is the CISSP (Certified Information Systems Security Professional). This test is a 6-hour exam and also requires 4 years of security-related experience if you also have a degree or 5 years of experience if you do not have a degree. CISSP holders are also required to submit a recommendation from another CISSP or an officer of their company and to take continuing education credits to maintain the certification. This is probably the most respected security-related certification. The vendor that produces CISSP (ISC2) also has advanced, post-CISSP certifications, such as the Information Systems Security Architecture Professional (ISSAP), Information Systems Security Engineering Professional (ISSEP), and Information Systems Security Management Professional (ISSMP).
The Certified Ethical Hacker certification is sponsored by the EC-Council (www.eccouncil.org). This test has also been the subject of some controversy. Keep in mind that it tests basic hacking skills, not a mastery of hacking. It is good for an introduction to hacking/penetration testing.
Offensive Security (https://www.offensive-security.com) specializes in penetration testing certifications. What makes their certification tests most interesting is that they all involve a hands-on component. You don’t simply take a test; you have to actually hack into their test systems.
CompTIA also offers several security exams, including Security+, CompTIA Advanced Security Practitioner (CASP), and Pentest+.
There are a number of general forensics certifications. EC-Council (www.eccouncil.org) has the Certified Hacking Investigator. There are also specific certifications for particular forensics tools. A good knowledge of basic forensics is useful for a security professional.
GIAC (www.giac.org) has a number of security-related certifications. All have a very solid reputation in the security industry. They are, however, more expensive than other tests, and for that reason there are fewer security professionals who have them. GIAC has security certifications (GSEC), penetration testing certifications (GPEN), and forensics certifications (GCFA and GCFE).
All certifications get some critics. The fact is that some people do attend boot camps and cram in just enough information to pass a certification. However, the same can be said of any qualification. It is certainly the case that there are medical doctors who are incompetent, but I am certain that if you are sick or injured, you seek out a medical doctor. The reason is that you are more likely to get qualified help from a doctor than if you simply select some random person. The same is true of certifications. Keep in mind that certifications reflect a minimum skill level, not mastery. I recommend having at least one general security certification (Security+, CASP, CISSP, and so on), one penetration testing certification (GPEN, CEH, Offensive Security, and so on), and one forensics certification (CCFP, GCFA, CHFI, and so on).
You should never hire a person based solely on certifications. Those certifications should simply be one element that you consider.
Finally, you should consider personal background. A security consultant or full-time employee will, by definition, have access to confidential information. Any legitimate security professional will not mind giving you any of the following:
 References
References Permission to check their credit history
Permission to check their credit history Permission to check their criminal background
Permission to check their criminal background
Anyone who seems reluctant to provide any of these items should be avoided. Therefore, an ideal security consultant might be a person with 5 or more years of experience, a degree in a computer-related discipline, a certification in your organization’s operating systems as well as one of the major security certifications, and a completely clean background, with references. As a rule, you simply cannot be too careful in hiring a security consultant.
Unless you have a highly trained security expert on staff, you should consider bringing in a security consultant to assess your system at least once. In our current legal environment, liability for security breaches is still being hotly debated. Companies are being sued for failing to practice due diligence in computer security. It is simply a wise move, both from a computer industry perspective as well as from a legal perspective, to do everything reasonable to ensure the security of your systems.
Summary
This chapter has outlined some basic items to look for in any security assessment. You should periodically assess your network/system for security vulnerabilities. A general recommendation would be a quarterly assessment for noncritical/low-security sites and perhaps as frequently as a weekly assessment for high-security sites. In any case, what are outlined in this chapter are the basics of assessing the security of a network, and they should give you a start toward securing your own network.
Safe computing is a matter of securing your computer, your network, and your servers and using common sense on the Web. It is important to rigorously apply security practices and standards to all computers, whether they are home computers or part of an organizational network.
Test Your Skills
Multiple Choice Questions
1. Which of the following is not one of the phases listed in NIST 800-115?
A. Planning
B. Execution
C. Post-assessment
D. Post-execution
2. John is now responsible for system security at a small bookkeeping firm. He wants to ensure that he implements good fundamental security. What is the most basic rule of computer security?
A. Keep systems patched.
B. Always use an IDS.
C. Install a firewall.
D. Always use antispyware.
3. You work in the network security department of a large bank. One of your jobs is to keep all systems patched. How might you ensure that system patches are kept up to date?
A. Use an automated patching system.
B. Patch any time you receive a vendor notification of a new patch.
C. Patch whenever a new threat is announced.
D. Use periodic scheduled patching.
4. Teresa is explaining basic security to a new technician. She is teaching him how to secure ports on any server or workstation. What is the rule about ports?
A. Block all incoming ports.
B. Block ICMP packets.
C. Block all unused ports.
D. Block all nonstandard ports.
5. Miguel is trying to secure a web server. He has decided to shut down any services that are not needed. His supervisor has told him to check dependencies first. Which of the following is a good reason to check dependencies before shutting down a service?
A. To determine whether you will need to shut down other services as well
B. To determine whether shutting down this service will affect other services
C. To find out what this service does
D. To find out whether this service is critical to system operations
6. If your machine is not used as a server and is not on a local network, what packet-filtering strategy should you use?
A. Block all ports except 80.
B. Do not block any ports.
C. Block all ports that you don’t need.
D. Do not block well-known ports.
7. You are trying to implement good fundamental security for a small company. Which of the following is the least essential device for protecting your network?
A. Firewall
B. Virus scanners on all machines
C. IDS system
D. Proxy server
8. Mohammed is responsible for security policies at a university. He is trying to ensure proper access policies. What is the rule of thumb on data access?
A. Data must be available to the widest range of people possible.
B. Only administrators and supervisors should access sensitive data.
C. Only those with a need for the specific data should have access.
D. All employees should have access to any data used in their department.
9. What are the main phases of the NSA-IAM process?
A. Planning, on-site assessment, post-assessment
B. Planning, execution, post-execution
C. Pre-assessment, execution, post-assessment
D. Pre-assessment, on-site assessment, post-assessment
10. What is the minimum frequency for system probing and audits?
A. Once per month
B. Once per year
C. Every other year
D. Every other month
11. An audit should check what areas?
A. Perform system patching, review policies, check personnel records of all managers, and probe for flaws
B. Only probe for flaws
C. Perform system patches, probe for flaws, check logs, and review policies
D. Check all machines for illicit software, perform complete system virus scan, and review firewall policies
12. Jerod is setting up security for a server room for a university. Which of the following is true of the room in which the server is located?
A. It should be in the most fire-resistant room in the building.
B. It should have a strong lock with a strong door.
C. It should be accessible only to those who have a need for access.
D. All of these answers are correct.
13. Elizabeth is responsible for security policies at her organization. She is trying to implement sound end-user security policies. What would be most important to block end users from doing on their own machine?
A. Running programs other than those installed by the IT staff
B. Surfing the Web and using chat rooms
C. Changing their screensaver and using chat rooms
D. Installing software or changing system settings
14. What is the preferred method for storing backups?
A. Near the server for quick restore if needed
B. Offsite in a secure location
C. In the IT manager’s office for security
D. At the home of one of the IT staff
15. Which of the following is a step you would definitely take with any server but might not be required for a workstation?
A. Uninstall all unneeded programs/software.
B. Shut down unneeded services.
C. Turn off the screensaver.
D. Block all Internet access.
16. Which of the following is a step you might take for large networks but not for smaller networks?
A. Use an IDS.
B. Segment the network with firewalls between the segments.
C. Use antivirus software on all machines on the network.
D. Do criminal background checks for network administrators.
17. Which of the following is a common way to establish security between a web server and a network?
A. Block all traffic between the web server and the network.
B. Place virus scanning between the network and the web server.
C. Put a firewall between the web server and the network.
D. Do not connect your network to the web server.
18. What is the rule on downloading from the Internet?
A. Never download anything.
B. Only download if the download is free of charge.
C. Only download from well-known, reputable sites.
D. Never download executables. Only download graphics.
19. Which of the following certifications is the most prestigious?
A. CISSP
B. PE
C. MCSA
D. Security+
20. Which of the following set of credentials would be best for a security consultant?
A. Ten years of IT experience, 1 year in security, CIW Security analyst, M.B.A.
B. Eight years of IT experience, 3 years in security, CISSP, B.S. in computer science
C. Eleven years of IT experience, 3 years in security, MCSE and CISSP, M.S. in information systems
D. Ten years of experience as a hacker and cracker, MCSE/CIW and Security+, Ph.D. in computer science
Exercises
EXERCISE 11.1: Patching Systems
Using a lab system, find and apply all operating system patches.
Check with all vendors of software installed on that machine and apply patches for those applications as well (if available).
Note the time taken to fully patch a machine. Consider how long it would take to patch a 100-machine network.
Write an essay that answers the following questions: Are there ways you could speed the process of patching a 100-machine network? How might you approach such a task?
Fyi: Helpful Resources
For Exercises 11.2, 11.3, and 11.4, you may find the following resources helpful:
EXERCISE 11.2: Learning About Policies
Using the resources given or other resources, find at least one sample security policy document.
Analyze that document.
Write a brief essay giving your opinion of that policy. Did it miss items? Did it include items you had not thought of?
EXERCISE 11.3: Learning About Disaster Recovery
Using the resources given or other resources, find at least one sample disaster recovery plan.
Analyze that document.
Write a brief essay giving your opinion of that disaster recovery plan. Also note any changes you would recommend to that policy.
EXERCISE 11.4: Learning About Audits
Using the resources given or other resources, find at least one sample security audit plan.
Analyze that document.
Write a brief essay giving your opinion of that plan. Do you feel the audit plan is adequate? What changes might you recommend?
EXERCISE 11.5: Securing Your Computer
Using either your home computer or a lab computer, follow the guidelines given in this chapter to secure that computer. Those steps should include the following:
Scan for all patches and install them.
Shut down all unneeded services.
Install antivirus software. (A demo version can be used for this exercise.)
Install antispyware software. (A demo version can be used for this exercise.)
Set appropriate password permissions.
EXERCISE 11.6: Secure Passwords
Using the Web or other resources, find out why longer passwords are harder to break.
Also find out what other things you should do to make a password harder to crack.
Write a brief essay describing what makes a perfect password.
EXERCISE 11.7: Securing a Server
This exercise is for those students with access to a lab server. Using the guidelines discussed in this chapter, secure a lab server. The steps taken should include the following:
Scan for all patches and install them.
Shut down all unneeded services.
Remove unneeded software.
Install antivirus software. (A demo version can be used for this exercise.)
Install antispyware software. (A demo version can be used for this exercise.)
Set appropriate password permissions.
Enable logging of any security violations. (Consult your operating system documentation for instructions.)
EXERCISE 11.8: Backups
Using the Web and other resources as a guide, develop a backup plan for a web server. The plan should cover how frequently to back up and where to store the backup media.
EXERCISE 11.9: User Accounts
This exercise is best done with a lab computer, not a machine actually in use.
Locate user accounts. (In Windows 8 or Windows 10, this is done by going to Start > Control Panel > Administrative Tools > Computer Management and looking for Groups and Users.)
Disable all default accounts (Guest, Administrator).
Projects
PROJECT 11.1: Writing and Executing an Audit Plan
With the knowledge you have gained while studying six chapters of this text and in examining security policies in the preceding exercises, it is now time to devise your own audit plan. This plan should detail all the steps in an audit.
Note: The second part of this project is contingent upon getting permission from some organization to allow you to audit its security. It is also ideal for a group project.
Taking the audit plan you wrote, audit a network. This audit can be conducted for any sort of organization, but you should make your first audit one with a small network (fewer than 100 users).
PROJECT 11.2: Forming a Disaster Recovery Plan
Using the knowledge you have gained thus far, create an IT disaster recovery plan for an organization. You may use a fictitious organization, but a real organization would be better.
PROJECT 11.3: Writing a Security Policy Document
Note: This project is designed as a group project.
It is now time to bring all you have learned thus far together. Write a complete set of security policies for an organization. Again, you may use a fictitious company, but real organizations are better. This set of policies must cover user access, password policies, frequency of audits (both internal and external), minimum security requirements, guidelines for web surfing, and so on.
PROJECT 11.4: Secure Web Servers
Using the information in this chapter as well as other resources, come up with a strategy specifically for securing a web server. This strategy should include the security of the server itself as well as securing the network from the server.
PROJECT 11.5: Adding Your Own Guidelines
Note: This project is ideal for a group project.
This chapter has outlined some general procedures for security. Write an essay detailing your own additional guidelines. These can be guidelines for individual computers, servers, networks, or any combination thereof.
Case Study
Juan Garcia is the network administrator for a small company that also maintains its own web server. He has taken the following precautions:
 All computers are patched, have antivirus software, and have unneeded services shut down.
All computers are patched, have antivirus software, and have unneeded services shut down. The network has a firewall with proxy server and IDS.
The network has a firewall with proxy server and IDS. The organization has a policy requiring passwords of 10 characters in length, and they must be changed every 90 days.
The organization has a policy requiring passwords of 10 characters in length, and they must be changed every 90 days.
Consider the following questions:
Has Juan done enough to secure the network?
What other actions would you recommend he take?
