The six built-in SCEP reports can be broken up into two categories: user-centric reports and system-centric reports . This recipe focuses on the group of system-based reports.We will be executing and interrupting the computer malware details, anti-malware activity report, and infected computers. Although these reports can be accessed either through the SCCM console or with a web browser, for this recipe, we will access them from the SCCM console.
In order to complete this recipe, you'll need to utilize an account that has at least the Endpoint Protection Manager roles assigned to it. If your installation of SCEP is in a lab, or is very new and has not yet detected any malware on your systems, then it's recommended that you utilize Eicar test file to simulate a malware detection. Eicar test file is a completely safe file that all major anti-malware vendors add to their definitions for testing purposes. It can be downloaded from http://www.eicar.org/ . Please remember to allow up to five minutes, after the time you trigger the Eicar detection, to start executing reports.
Follow these steps:
- Log into your SCCM CAS server and launch your SCCM 2012 management console.
- Navigate to
MonitoringOverviewReportingReportsEndpoint Protectionand select the Antimalware Activity Report. - Click on Values at the end of the Collection Name field and select any of the collections to which SCEP has been applied, as shown in the following screenshot:
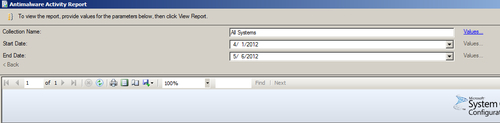
- Choose Start Date and End Date and click on View Report.
- Take note of blue links, any of these can be clicked to drill-down and learn more about a given aspect of the report. For now, click on the number value below Total Remediations. This should take you to a sub-report titled Infected Computers. Refer to the following screenshot:
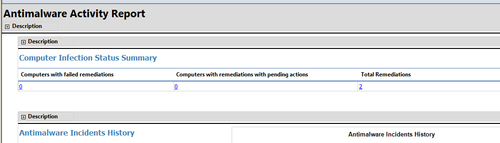
- Find the PC on which you ran the Eicar test string and click on the name; this will launch the Computer Malware details report for this PC, as shown in the following screenshot:
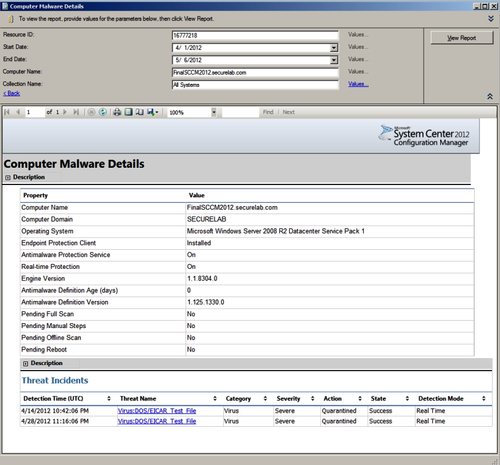
- To learn more about the malware with which this system has been afflicted, click on the link under Threat Name.This will take you to the malware details report. Here, you can see the link that will launch an Internet Explorer browser and direct you to the page within the Microsoft Virus Encyclopedia for this threat.
- Next, we will export this report in order to distribute it to other users. Click on the Export button in the report workspace bar and select PDF as the file format. Enter a destination in the Save As window and click on the Save button to complete, as shown in the following screenshot:

One of the biggest improvements in SCEP over FEP is the consolidation of databases. FEP stored data in two different DBs that were separated from the core SCCM DB and SCEP, whereas, SCCM 2012 shares the same database. This means you no longer have to wait for data to be moved from one database to another before a malware event is reflected in your reports. In FEP, it could take up to 45 minutes for a malware event to be reflected in a report. With SCEP, the malware event should be reflected in a report almost instantly once the message is received by the SCCM server (usually within five minutes).
The system-centric group of SCEP reports allows you to quickly look at incidents on multiple PCs, or drill-down to the Computer Malware Details report to review the status of a single PC. The Computer Malware Details report shows all relevant SCEP client details, such as engine and definition versions, in addition to a history of malware events.
Exporting the Computer Malware Details as a PDF will allow you to quickly share information with other users even if they do not have access to the SCCM console or the SQL Reporting Services for your SCCM server.
