In order to add the new privileges to the instance profile, we are going to edit the template we created earlier in the chapter.
Edit the file jenkins-cf-template.py we created earlier. We are going to add a policy to grant permissions to the Jenkins instance to communicate with CodePipeline. This step is very similar to the change we made to grant S3 access to our web server.
Above the instance variable instantiation, add the following:
t.add_resource(IAMPolicy("Policy",
PolicyName="AllowCodePipeline",
PolicyDocument=Policy(
Statement=[
Statement(Effect=Allow,
Action=[Action("codepipeline", "*")],
Resource=["*"])
]
),
Roles=[Ref("Role")]
))
Then, save the changes and regenerate the template. The new template should look like this http://bit.ly/2djBqbb:
$ git add jenkins-cf-template.py
$ git commit -m "Allowing Jenkins to interact with CodePipeline"
$ git push
$ python jenkins-cf-template.py > jenkins-cf.template
And using the web interface, update the stack:
- Open https://console.aws.amazon.com/cloudformation.
- Check the checkbox next to the Jenkins stack and in the Actions menu, select Update Stack.
- Browse to the newly generated jenkins-cf.template and click on Next until you get to the review screen:
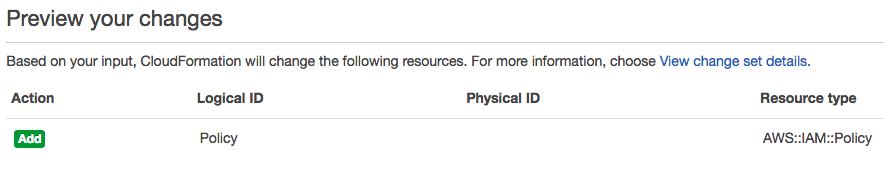
- As shown in the preceding screenshot, because we created our instance with an instance profile, only the IAM policy is being added. Our EC2 instance will stay untouched, making that change very safe. Click on Update to confirm the change.
The instance policy will get updated giving our Jenkins enough permissions to interact with CodePipeline. We can now install the Jenkins plugin for CodePipeline.
