

Authentication requirements for IBM SmartCloud Storage Access
In the IBM SmartCloud Storage Access solution a directory service is required to manage the authentication and authorization of users to the storage cloud environment. Specifically, to manage user access to the IBM SmartCloud Storage Access portal and authentication with the file storage systems.
This authentication service is provided by external software, which enables the integration of existing authentication servers with IBM SmartCloud Storage Access after some simple configuration steps. After IBM SmartCloud Storage Access is connected to the authentication server, all of the existing users and groups can be easily imported into the cloud environment.
IBM SmartCloud Storage Access supports Windows and UNIX-based operational system users by integration with a Microsoft Active Directory (AD) or Lightweight Directory Access Protocol (LDAP) authentication server. Only one authentication server can be configured with IBM SmartCloud Storage Access, however federated authentication (FA) is supported with AD to allow users from different domains and AD servers to access the same storage cloud environment.
This chapter is intended to describe the compatibility, requirements, and consideration for IBM SmartCloud Storage Access integration with the following types of servers:
4.1 Lightweight Directory Access Protocol
IBM SmartCloud Storage Access supports IBM Tivoli Directory Server V6.1 or later (see Table 4-3 on page 53) as an LDAP authentication service in the storage cloud solution. Other LDAP software, such as OpenLDAP for Linux, is not officially supported by IBM SmartCloud Storage Access, and it is not included in this description. If you require a different LDAP provider for your IBM SmartCloud Storage Access storage cloud solution, open a request for price quotation (RPQ) with IBM.
This section describes the considerations for the Tivoli Directory Server configuration as the authentication service in the storage cloud solution.
4.1.1 Planning
Before installing Tivoli Directory Server, be sure that the hardware and software meet the installation requirements. Be aware that the planning information in this section applies only to Tivoli Directory Server. If you are planning to install other software on the same server, such as IBM Tivoli Storage Productivity Center, see 6.1, “Planning” on page 112.
For detailed information about Tivoli Directory Server, see the following web page:
Also, during planning, consider that IBM SmartCloud Storage Access and the file storage subsystems must use the same authentication server, so that user and group information matches when accessing the cloud and provisioning storage.
The following hardware and software requirements are based on Tivoli Directory Server V6.3, but can be use as a guideline for earlier versions of Tivoli Directory Server. For more detailed information in the system requirements for Tivoli Directory Server, see the following link:
Hardware planning
Table 4-1 lists the suggested minimum requirements for Tivoli Directory Server V6.3.
Table 4-1 Hardware planning for the Tivoli Directory Server component
|
Product
|
Minimum hardware requirements
|
Suggested minimum hardware production
|
|
Tivoli Directory Server
|
1 processor
|
2 processors
|
|
128 MB of memory
|
2 GB of Memory
|
|
|
2 GB of disk space
|
10 GB of disk space
|
Table 4-2 shows the hardware used to install Tivoli Directory Server V6.3 in the environment used for this publication.
Table 4-2 Publication environment hardware for a Tivoli Directory Server V6.3 installation
|
Hardware component
|
Description
|
|
Processor
|
1 processor x 1.799 GHz Intel Xeon processor
|
|
Memory
|
1 GB of RAM
|
|
Disk space
|
80 GB file system on the Linux operating system
|
Software planning
Table 4-3 shows the Tivoli Directory Server 6.3 software prerequisites.
Table 4-3 Software planning for Tivoli Directory Server
|
Software component
|
Description
|
|
OS
|
•IBM AIX® system
•Red Hat Linux X86 32-bit, 64-bit, Linux for IBM Power Systems™, Linux for IBM System z®
•Intel 32-bit, 64-bit Windows
•Solaris SPARC, Solaris X64
|
|
Web browsers
|
•Microsoft Internet Explorer V6.0 Service Pack 1 or Service Pack 2 or later
•Firefox 2.0.x or later
|
|
Database
|
•IBM DB2® Enterprise Server Edition V9.5 FixPack 3 or higher1
•IBM DB2 Enterprise Server Edition V9.7 FixPack 2a
|
|
Web application servers
|
•IBM WebSphere Application Server 7.0a
|
1 Notice that for DB2 and IBM WebSphere® Application Server, these two software components are part of Tivoli Directory Server, and are installed automatically during Tivoli Directory Server installation.
Table 4-4 lists the pre-required software used to install Tivoli Directory Server V6.3 for this publication environment.
Table 4-4 Publication environment pre-required software for a Tivoli Directory Server V6.3 installation
|
Software component
|
Description
|
|
Operating system (OS)
|
Red Hat Enterprise Linux 5.8 64‑bit
|
|
Web browsers
|
Firefox 3.6.26
|
Installation and configuration planning
The following list describes various key parameters to consider when setting up LDAP services:
IP address This address is the IP address that is used by the directory server.
Administrator distinguished name (DN) and password
The administrator account that is used to manage LDAP content. The Administrator DN is by default cn=root.
Encryption seed A random string that is used as a key to perform encryption. The encryption seed must contain only printable ISO-8859-1 ASCII characters, with values in the range 33 to 126, and must be a minimum of 12 and a maximum of 1016 characters in length.
Suffix DN The DN to identify the IBM SmartCloud Storage Access account management domain. A suffix (also known as a naming context) in a DN identifies the top entry in a locally held directory hierarchy. Because of the relative naming scheme that is used in LDAP, this DN is also the suffix of every other entry in that directory hierarchy.
A directory server can have multiple suffixes, each identifying a locally held directory hierarchy. This IBM SmartCloud Storage Access solution has one Suffix DN to manage all the accounts.
Domain An entry in the LDAP to contain all of the management items. The domain DN can be a sub DN, or the same DN of the suffix DN.
User container and Group container
Entries in the LDAP to contain users and groups. These two containers should be under the domain entry.
Users and Groups The users and groups to be managed by Tivoli Directory Server, and created under the User container and Group container.
Table 4-5 shows the parameters for the environment that is used for this publication.
Table 4-5 Parameter Planning Example
|
Parameters
|
Settings
|
|
IP
|
9.111.67.202
|
|
Administrator DN
|
cn=root
|
|
Encryption seed
|
!$*-0369<?BEH
|
|
Suffix DN
|
dc=SmartCloud Storage Access,dc=ibm,dc=com
|
|
Domain
|
dc=SmartCloud Storage Access,dc=ibm,dc=com
|
|
User container
|
cn=users, dc=SmartCloud Storage Access,dc=ibm,dc=com
|
|
Group container
|
cn=groups, dc=SmartCloud Storage Access,dc=ibm,dc=com
|
|
Users
|
cn=clouduser01, cn=users, dc=SmartCloud Storage Access,dc=ibm,dc=com, …
|
|
Groups
|
cn=cloudgroup01, cn=groups, dc=SmartCloud Storage Access,dc=ibm,dc=com, …
|
For more information about LDAP and DN, see the following website:
4.1.2 Tivoli Directory Server installation and configuration reference
The detailed Tivoli Directory Server V6.3 installation and configuration procedure for all supported operating systems can be found at the following IBM information center:
4.1.3 Tivoli Directory Server configuration considerations for an IBM SmartCloud Storage Access setup
There are some considerations that need to be taken into account when configuring LDAP for the storage cloud environment:
•The user’s full name and email can be configured while importing users into IBM SmartCloud Storage Access if not previously set in LDAP.
•The default configuration of Tivoli Directory Server supports the Network File System (NFS) protocol for use in a UNIX environment. However, additional steps are required to use the Common Internet File System (CIFS) protocol from a Windows server or client. For more information, see the following section, “Configuring Tivoli Directory Server for use with the CIFS protocol”.
Configuring Tivoli Directory Server for use with the CIFS protocol
If you plan to enable CIFS access in the storage cloud with IBM SmartCloud Storage Access, some additional configuration is required for the Tivoli Directory Server user authentication server. For detailed configuration information, see the following IBM information center:
4.2 Active Directory
IBM SmartCloud Storage Access supports Microsoft AD server as user registries with Windows Server 2008 R2 or later with the latest fix pack (see Table 2-3 on page 28). Active Directory Domain Services (AD DS) perform the following tasks:
•Store information about the identities of users, computers, and services.
•Authenticate a user or computer.
•Provide a mechanism to access resources.
The following section describes the considerations during the installation and configuration of Microsoft AD as the authentication server for the IBM SmartCloud Storage Access solution. The environment of this publication is based on Windows server 2008 R2, however it can be used as a guideline for newer versions. Reference for more detailed information will be provided where required.
Unless otherwise specified, Windows server refers to either 2008 or 2012 R2 versions that IBM SmartCloud Storage Access can support.
4.2.1 Planning
Windows Server 2008 and 2012 R2 are available in different editions to support the various server and workload needs of network environments. Each edition of Windows server is packaged with a unique set of features that target that edition to a particular environment, or even a specific role. Windows server editions with AD DS can be used for AD authentication for IBM SmartCloud Storage Access.
In the Windows Server 2008 R2 version, Identity Management for UNIX (IMFU) components, (previously known as Windows Services for UNIX, or SFU, on Windows 2003) is supported natively with AD, which makes CIFS and NFS support for network-attached storage (NAS) authentication implementation easier.
This chapter describes how to plan AD and Identity Management for UNIX components with the Windows Server 2008 software. Also, during planning, consider that IBM SmartCloud Storage Access and the file storage subsystems must use the same authentication server so that user and group information matches when accessing the cloud and provisioning storage.
Hardware planning
Windows Server Enterprise expands upon Windows Server Standard Edition. It offers the most commonly used features, and is designed to meet most general server computing requirements. The Windows Server Enterprise version is the supported version for AD configuration for the IBM SmartCloud Storage Access solution.
As a reference, the minimum hardware requirements of Windows Server are shown in Table 4-6.
Table 4-6 Hardware planning for Windows Server for the AD software component
|
Component
|
Minimum hardware requirements
|
|
Windows Server 2008 and 2012 R2
|
1 processor
1 GB of memory
40 GB disk space
|
Hardware requirements can vary based on the number of users, groups, and computers registered in the AD server. For detailed hardware requirements, see the information on the following websites:
•Windows Server 2008 R2
•Windows Server 2012 R2
As an example, Table 4-7 is the environment created for this publication that is used for AD on Windows Server 2008 R2 Enterprise edition.
Table 4-7 Publication environment hardware for AD installation
|
Hardware component
|
Description
|
|
Processor
|
2 processor x 1.799 GHz Intel Xeon processor
|
|
Memory
|
2 GB of RAM
|
|
Disk space
|
40 GB file system on Windows Server
|
Installation and configuration planning
Plan the following parameters before setting up AD:
IP address This server's IP address.
Fully qualified domain name (FQDN)
FQDN is a domain name that specifies its exact location in the tree hierarchy of the Domain Name System (DNS).
Domain NetBIOS name The NetBIOS name provides services related to the session layer of the open systems interconnection (OSI) model that enable applications on separate computers to communicate over a LAN.
Forest functional level and domain functional level
Forest and domain functional levels define the level of AD functionality supplied by all domain controllers in a domain forest or domain. For best compatibility, select Windows 2003.
Additional domain controller options
Active Directory Service requires the DNS server. The default value for additional domain controller options is the DNS server.
Directory Services Restore Mode administrator password
This administrator password uses the Directory Services Restore Mode (DSRM) on a Microsoft Windows Domain Controller to take the AD on that machine offline.
User ID/Group ID range Design the range for User ID/Group ID (UID/GID) distribution for IMFU. This value is required for IBM Storwize V7000 Unified and IBM Scale Out Network Attached Storage configuration.
Table 4-8 shows an example of the settings that were planned and used in the environment for this publication.
Table 4-8 Parameter settings for the test IBM SmartCloud Storage Access solution
|
Parameter
|
Setting
|
|
IP address
|
9.111.67.200
|
|
Gateway
|
9.111.67.1
|
|
DNS
|
9.111.67.200 (same as AD)
|
|
FQDN
|
scsa.ibm.com
|
|
Functional level
|
Windows 2003
|
|
Administrator Password
|
Passw0rd
|
|
UID/GID range
|
10000-50000
|
4.2.2 Active Directory installation and configuration reference
AD services are embedded in Windows Server 2008 and 2012 R2. However, the following roles are required to be installed to enable the Windows server as the AD authentication server for the IBM SmartCloud Storage Access solution:
•Active Directory Domain Services (AD DS)
•DNS Server (in case AD server is planned to be used as DNS server)
•IMFU (for UNIX users support)
Active Directory Domain Services installation
The detailed installation procedure for AD DS can be found in the following links:
•For Windows Server 2008 R2:
•For Windows Server 2012 R2:
After the installation is completed, the role of AD DS is listed in the Server Manager panel. Figure 4-1 shows the AD DS role in a Windows Server 2008 R2.

Figure 4-1 The role of Active Directory Domain Services in Server Manager
DNS server installation
When using AD as the authentication server for IBM SmartCloud Storage Access, a DNS server is required to resolve the computer and user host names, and domain names in the TCP/IP cloud network.
The DNS server installation in a Windows server involves installing the DNS server role in the Server Manager. This role is set as default to be enabled during the AD DS installation. As you can see in Figure 4-2, the DNS Server option needs to be selected at the “Additional Domain Controller Option” step in the Active Directory Domain Services Installation Wizard. This is the preferred method for installing the DNS Server role if you want to integrate your DNS domain namespace with the AD DS domain namespace.
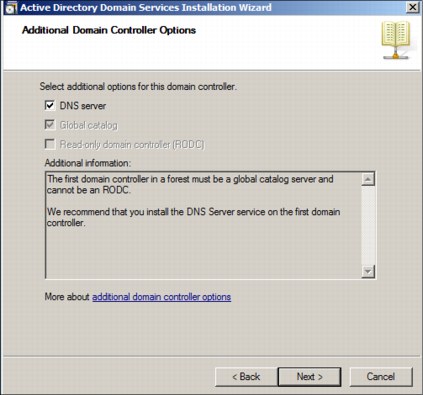
Figure 4-2 Server options for AD
If you have an existing DNS infrastructure and you do not want this AD server to be a DNS server, clear the DNS server check box.
The DNS Server role can be installed independently from the AD DS using the Server Manager. For detailed instructions about how the DNS server role can be installed without the AD DS installation wizard, go to the following link:
After the DNS server role is installed in the Windows server, it is listed in the Server Manager panel, as shown in Figure 4-3.
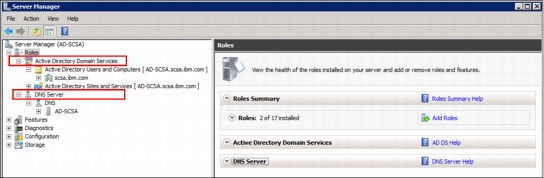
Figure 4-3 AD DS and DNS server roles in the Server Manager pane
Installing Identity Management for UNIX
AD has a service called IMFU that simplifies the use of NAS with CIFS and NFS protocols. IMFU must be enabled in the AD server to allow UNIX users to authenticate into IBM SmartCloud Storage Access, and to provision NAS from the cloud.
To enable this service in the AD server, go to the following link and choose the version of your Windows server to see the detailed installation instructions:
|
Important: During the IMFU installation, make sure that you choose all of the components in the Select Role Services window, as shown in Figure 4-4 on page 60.
|
Figure 4-4 shows the Select Role Services window with all of the IMFU components selected.

Figure 4-4 Select Role Services for IMFU
After the installation is completed, you can now see all of the components required by IBM SmartCloud Storage Access to use AD as the authentication server in the Server Manager pane, as shown in Figure 4-5:
•Active Directory Domain Services
•Identity Management for UNIX
•DNS Server

Figure 4-5 Server Manager pane after IBM SmartCloud Storage Access required roles in AD server
4.2.3 AD configuration considerations for IBM SmartCloud Storage Access
This section describes the considerations that must be taken while performing the following tasks in the AD server to allow integration with IBM SmartCloud Storage Access:
Basic user and group configuration
To make resources from the AD compatible with IBM SmartCloud Storage Access, it is important to pay attention to the following settings during the creation of users and groups.
Validate these settings during user creation:
1. The value set in the Full name field when creating a user in AD is the same as that shown in the IBM SmartCloud Storage Access environment, and the User logon name is the one used to log in to the IBM SmartCloud Storage Access portal. In the example in Figure 4-6, Mary Johnson uses maryjohnson to log in to the IBM SmartCloud Storage Access portal.

Figure 4-6 User full name and login name information
2. The User must change password at next logon option is not supported by IBM SmartCloud Storage Access, and must be disabled when creating a new user, as seen in Figure 4-7. If you intend to use this option, the user must log in to a Windows client with this account, and change the user password before using this account in IBM SmartCloud Storage Access.

Figure 4-7 Disable the User must change password at next logon option
3. You can update the user properties by double-clicking the user name to open the properties. Populate the blank fields with additional information, including telephone number, email, and so on. See Figure 4-8.

Figure 4-8 The email address is mandatory for IBM SmartCloud Storage Access
Validate these options during groups creation:
1. The task to create a group is similar to the task for creating a user. You must enter a group name, and select a group scope and group type. For more information about group scope, see the following Microsoft TechNet document:

Figure 4-9 Group creation in AD
At this point, the basic configuration for users and groups is complete.
DNS server configuration
When using AD in the IBM SmartCloud Storage Access cloud solution, the AD and IBM SmartCloud Storage Access server must be added in both the Forward Lookup Zone and the Reverse Lookup Zone of the DNS server. This is so users and groups are found from IBM SmartCloud Storage Access.
First, a new Reverse Lookup Zone must be created. To do so, follow these steps:
1. In the DNS server Server Manager, right-click Reverse Lookup Zones and select New Zone, as shown in Figure 4-10.

Figure 4-10 Create a Reverse Lookup Zone
2. Click Next on the New Zone Wizard page.
3. Select the zone type that you want to create and click Next, in our environment we create a Primary zone as shown in Figure 4-11.
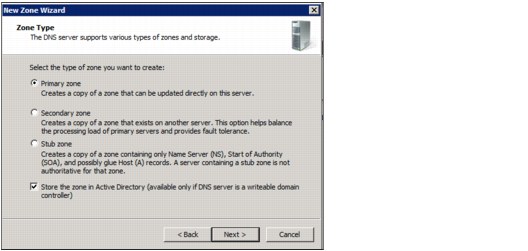
Figure 4-11 Type of zone for Reverse Lookup Zone
4. Leave the default selection (DNS servers in the domain) in the Active Directory Zone Replication Scope window, as shown in Figure 4-12.

Figure 4-12 Settings for zone data replication
5. Choose what kind of addresses are going to be used in the Reverse Lookup Zone, either IPv4 or IPv6. This publication environment used IPv4, as shown in Figure 4-13.

Figure 4-13 Reverse Lookup Zone addresses
6. Enter the network ID where the AD and the IBM SmartCloud Storage Access are located. In this example, the AD and IBM SmartCloud Storage Access are installed in the 9.111.67.xxx network. See Figure 4-14.

Figure 4-14 Network ID for Reverse Lookup Zone
7. Leave the defaults in the Dynamic Update window and click Next.
8. Review the specified settings and click Finish to close the wizard and create the new zone.

Figure 4-15 Reverse Lookup Zone created in the DNS Server
Now, the AD and the IBM SmartCloud Storage Access must be added into the Forward and Reverse Lookup Zones. If the DNS server was installed during the AD DS installation, the AD server will be in the Forward Lookup Zone by default.
The following steps show how to add the IBM SmartCloud Storage Access server in the Forward and Reverse Lookup Zone (these same steps can be used if the AD is not in both of the zones already):
1. Right-click domain in the Forward Lookup Zone where you want to add the IBM SmartCloud Storage Access server and select New Host (A or AAAA). For this publication environment, the domain is scsa.ibm.com, as shown in Figure 4-16 on page 67.

Figure 4-16 New Host in the Forward Lookup Zone
2. Type the host name of the IBM SmartCloud Storage Access server and the IP address. In the example, we named the IBM SmartCloud Storage Access server scloud.scsa.ibm.com with the IP 9.111.67.202, as shown in Figure 4-17. Click Add Host.
|
Important: Make sure that the Create associated pointer (PTR) record box is selected. This will create the IBM SmartCloud Storage Access server record in the Reverse Lookup Zone.
|

Figure 4-17 Name of new host record in Forward Lookup Zone
3. A message confirms that the new host record was successfully created, as shown in Figure 4-18.

Figure 4-18 New host record successfully created
4. Now right-click in the Reverse Lookup Zone and select Refresh so that the IBM SmartCloud Storage Access server record is listed, as seen in Figure 4-19.

Figure 4-19 Refresh Reverse Lookup Zone to see modifications
The DNS server is now configured so that IBM SmartCloud Storage Access can find the users and groups configured in the AD. Read the following section for considerations when you create users and groups in AD for IBM SmartCloud Storage Access.
Configuring Identity Management for UNIX
This section explains how to configure IMFU by performing these overall steps:
1. Configuring the user and group UNIX attributes
2. Setting up and testing on Linux client
3. Configuring password synchronization between Windows and UNIX
The following procedure describes these steps in detail:
1. Configure the user and group UNIX attributes:
a. After successful installation of IMFU and configuration for AD, you can now view the UNIX Attributes from both the user and group attributes panel.
b. Set the NIS Domain which is automatically recognized by IMFU when you set the AD FQDN. In this publication environment, the NIS domain is scsa.
c. Also set the GID to be 10000. Ensure that the number is in the range that was designed in the planning section, which is 10000-50000. See Figure 4-20.

Figure 4-20 Set UNIX attributes for group in AD
d. Perform a similar configuration for the users. In this example, clouduser01 was configured with the NIS Domain to be IBM SmartCloud Storage Access, and UID to be 10000, which is between 10000 and 50000.
Notice that the Primary group name/GID is shown to be LabServices. It is because we previously set LabServices to be the primary group of user clouduser01. See Figure 4-21.

Figure 4-21 Set UNIX attributes for user in AD
2. Set up and initially test the Linux client.
In our testing environment, we use the Red Hat Enterprise Linux (RHEL) V5.6 client to perform the validation. Because IMFU works as a Network Information Service (NIS) server for Linux, the Linux client must be configured as an NIS client to access IMFU:
a. Ensure that RPM Package Manager (RPM) and the following software is installed on the Linux client:
• ypbind
• portmap
• yp-tools
• nscd
b. Configure the /etc/sysconfig/network network file for the NIS domain:
• NETWORKING=yes
• Host name=client-hostname
• NISDOMAIN=name-of-domain
Figure 4-22 shows the settings for this example.

Figure 4-22 Network checking result
c. Configure the /etc/yp.conf file for NIS server information:
domain <name-of-domain> server <XXX.XXX.XXX.XXX>
See the following statement for the setting in this example:
domain SmartCloud Storage Access server 9.111.67.200
Table 4-9 NIS authentication configuration
|
Setting
|
Configuration
|
|
passwd
|
files nis
|
|
shadow
|
files nis
|
|
group
|
files nis
|
e. Create the domain with the nisdomainname <name-of-domain> command. In this case, the command is nisdomainname SmartCloud Storage Access.
f. Restart the NIS client services. Run the following commands to start the NIS client services:
Service portmap restart
Service ypbind restart
Service nscd restart
g. All of the configurations on Linux are now complete. You can use the ypcat passwd command to validate if you can see any user information from the AD server side.
See Figure 4-23.
See Figure 4-23.

Figure 4-23 Verify user information from AD Server
Additional configuration is required before it is possible to authenticate with clouduser01. Password synchronization must be configured to enable authentication in the Linux client.
3. Configure password synchronization between the Windows operating system and the UNIX system.
Configure the password for Windows and UNIX synchronization. This step is important and cannot be skipped. If this step is skipped, the Linux server cannot recognize the password of the user that is set in the Windows operating system.
First, change the Password Synchronization properties:
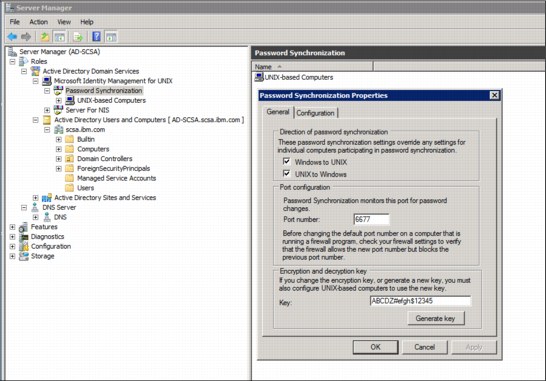
Figure 4-24 Password Synchronization Properties for AD
b. Switch to the Configuration tab, mark Enable, and click Apply.
c. On the UNIX-based Computers tab, right-click a system and select Add Computer.
d. Specify the IP address of Linux clients that are going to be connected to this AD server, select all synchronization options, and click Apply. See Figure 4-25.

Figure 4-25 Add a UNIX Computer for password synchronization
e. After completing the password synchronization, reset the user's password to make it synchronized with the UNIX computer. Now you can su to the clouduser01 user from the Linux server.
For more information about password synchronization, see the following Microsoft TechNet document:
All of the configurations for AD and IMFU are now complete. You can now authenticate users from both Windows and Linux clients after configuration. This AD server is also ready to be added into Storwize V7000 Unified, IBM Scale Out Network Attached Storage, and IBM SmartCloud Storage Access for the authentication and authorization of CIFS and NFS services.
4.3 Federated authentication with Active Directory
With FA in IBM SmartCloud Storage Access, users from different domains and ADs can access a common IBM SmartCloud Storage Access portal, and make use of the resources of that storage cloud. This enables the collaboration between organizations without the need of creating local authentication credentials for users for the IBM SmartCloud Storage Access environment, but instead using the native authentication information of their organization.
FA functionality in the storage cloud solution is provided by AD in the supported versions of Windows Server for IBM SmartCloud Storage Access, which is the reason why FA is not supported with LDAP as an authentication service. This FA with AD feature is also supported by Storwize V7000 Unified and IBM Scale Out Network Attached Storage file storage subsystems with no extra configuration in the storage resources required.
This section provides information about the following topics:
•Topology of the FA service in IBM SmartCloud Storage Access solution
•Configuration requirements in the AD for FA
4.3.1 Topology of the Federated Authentication service in the IBM SmartCloud Storage Access solution
FA for IBM SmartCloud Storage Access is based on the trust relationship between ADs from different domains. This trust relationship can be established among multiple forests or multiple domains in the same forest.
Figure 4-26 shows the components of a FA environment with IBM SmartCloud Storage Access, and the relationship between those elements.

Figure 4-26 Federated Authentication topology in an IBM SmartCloud Storage Access solution
The basic FA topology includes the following components:
•The local domain (domain1.com) where IBM SmartCloud Storage Access is deployed.
•An external domain (doman2.com), which can be either another AD forest or one child domain in the domain1.com forest.
•A local IBM SmartCloud Storage Access infrastructure in domain1.com, which contains the IBM SmartCloud Storage Access server and the storage services (Tivoli Storage Productivity Center and storage subsystems).
•An internal AD that contains users and groups from domain1.com. This AD is directly configured to the IBM SmartCloud Storage Access server and file storage subsystems.
•An external AD that contains users and groups from domain2.com.
•A DNS server that has information about all of the elements in the network.
•A trust relationship between ADs must be established to allow users from domain2.com to access the cloud resources in domain1.com.
•A firewall for information security purposes is common practice in an organization. A proxy service can be configured to allow connection between trusted domains.
•Internal and external users that can authenticate into the IBM SmartCloud Storage Access environment and provision using their native credentials from the domain that they
belong to.
belong to.
This is a basic FA scenario. However, IBM SmartCloud Storage Access supports integration with multiple AD domains if they are trusted ADs between each other.
For more information regarding forest and domains, see the following link:
4.3.2 Configuration of Active Directory for Federated Authentication
As mentioned previously, IBM SmartCloud Storage Access requires the trust relationship between ADs to enable FA for the cloud solution. This section describes the considerations and steps for this configuration. Table 4-10 shows the FA environment used for this publication, and used as an example in the following sections.
Table 4-10 Publication environment for FA configuration
|
Component
|
Setting
|
|
Local Domain
|
scsa.ibm.com
|
|
Internal Active Directory
|
9.111.67.200
|
|
Local User
|
clouduser01.scsa.ibm.com
|
|
External Domain
|
otherdomain.com
|
|
External Active Directory
|
9.111.67.201
|
|
External user
|
otherdomainuser1.otherdomain.com
|
|
DNS
|
9.111.67.190
|
Requirements and considerations
Before beginning the configuration of FA for IBM SmartCloud Storage Access, make sure that you have all of the following requirements in your environment:
•FA can be configured in the storage cloud with the AD in Windows server versions supported by IBM SmartCloud Storage Access.
•The local AD and global DNS must be connected to IBM SmartCloud Storage Access and file storage subsystems.
•The IBM SmartCloud Storage Access server and AD host name must be added in the Forward and Backward Lookup Zones in the DNS.
•The global DNS server knows every element in the network.
•The difference between the time configured in all of the AD servers must not exceed five minutes.
Enable Global Catalog
Before beginning with the configuration for Federated Authentication, it is important to be sure that the Global Catalog service is enabled in the AD server. Follow these steps:
1. Right-click Administrative Tools and select Active Directory Sites and Services, as shown in Figure 4-27.
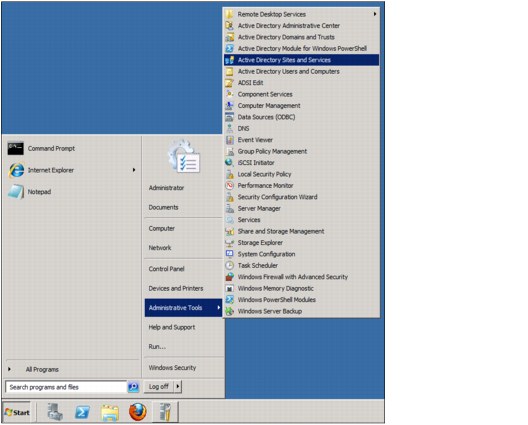
Figure 4-27 Select Active Directory Sites and Services
2. Select the AD server that you are going to use for FA (in this case, AD-SCSA), right-click NTDS Settings, and select Properties, as shown in Figure 4-28.

Figure 4-28 AD NTDS Settings Properties
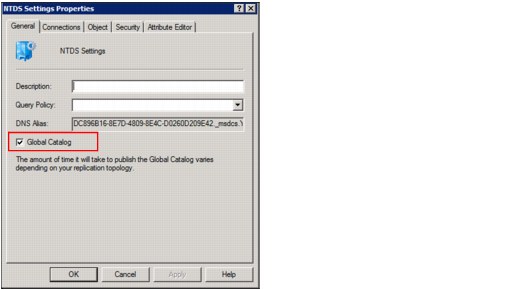
Figure 4-29 Global Catalog enabled
Configuring Active Directory trust
To enable FA for IBM SmartCloud Storage Access, there must be a trust relationship between ADs that want to have access to the storage cloud. The following steps show the configuration for AD trust between the scsa.ibm.com AD and otherdomain.com in this publication environment:
1. On the scsa.ibm.com AD server, which is the local IBM SmartCloud Storage Access authentication server, right-click Administrative Tools and select Active Directory Domains and Trust, as shown in Figure 4-30.

Figure 4-30 Active Directory Domains and Trust in Administrative Tools

Figure 4-31 Properties of Active Directory Domains and Trust
3. Go to the Trust tab and click New Trust to add otherdomain.com as a trusted domain, as shown in Figure 4-32.

Figure 4-32 Trusted domains for scsa.ibm.com
4. The New Trust Wizard starts. click Next.
5. In the domain name, enter otherdomain.com, which is the domain that you want to establish a trust relationship with. See Figure 4-33.

Figure 4-33 External domain name

Figure 4-34 Trust Type
7. The direction of the trust must be set to Two-way, as shown in Figure 4-35. This is required by IBM SmartCloud Storage Access.

Figure 4-35 Direction of Trust
8. Choose to create the trust in both of the domains, as shown in Figure 4-36.

Figure 4-36 Sides of Trust

Figure 4-37 Otherdomain.com administrative credentials
10. Select Forest-wide Authentication in the Outgoing Trust Authentication level, for both local and specified Forest.
11. Confirm that the settings are correct and click Next to complete the trust.
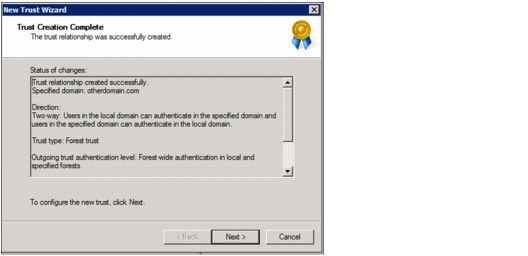
Figure 4-38 Confirm setting for trust creation
13. Select Yes for Confirm outgoing and incoming trust.
14. See the confirmation from the New Trust Wizard and click Finish to close it, as shown in Figure 4-39.

Figure 4-39 Close the New Trust Wizard

Figure 4-40 New trusted domain for scsa.ibm.com
For more information about domain and forest trusts, see the following website:
As a final configuration, the external domain othderdomain.com must be added in the Reverse Lookup Zone of the DNS server.
The following steps show how to add the new trusted domain manually into the Reverse Lookup Zone:
1. From the global DNS server, right-click the Reverse Lookup Zone where the AD and IBM SmartCloud Storage Access server are located, then select Create New Pointer, as shown in Figure 4-41.
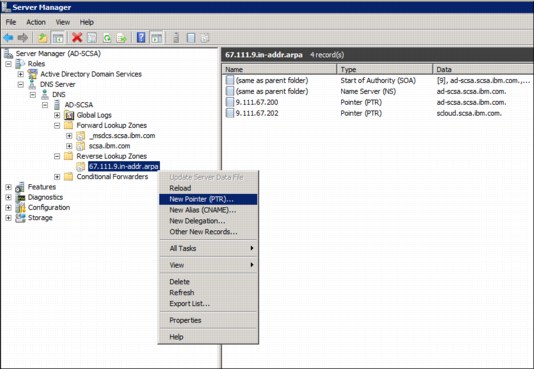
Figure 4-41 New pointer in the Reverse Lookup Zone
2. Enter the IP address and host name of the external domain AD server and click OK, as shown in Figure 4-42.

Figure 4-42 Host name and IP for othderdomain.com AD server
3. The otherdomain.com AD server record is now listed in the Reverse Lookup Zone as shown in Figure 4-43.

Figure 4-43 Othderdomain.com AD server record in Reverse Lookup Zone
This previous configuration will now allow the enablement of FA on the IBM SmartCloud Storage Access cloud solution. Users from the external domain can now log in to the IBM SmartCloud Storage Access environment using their native credentials.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
