115
make.co
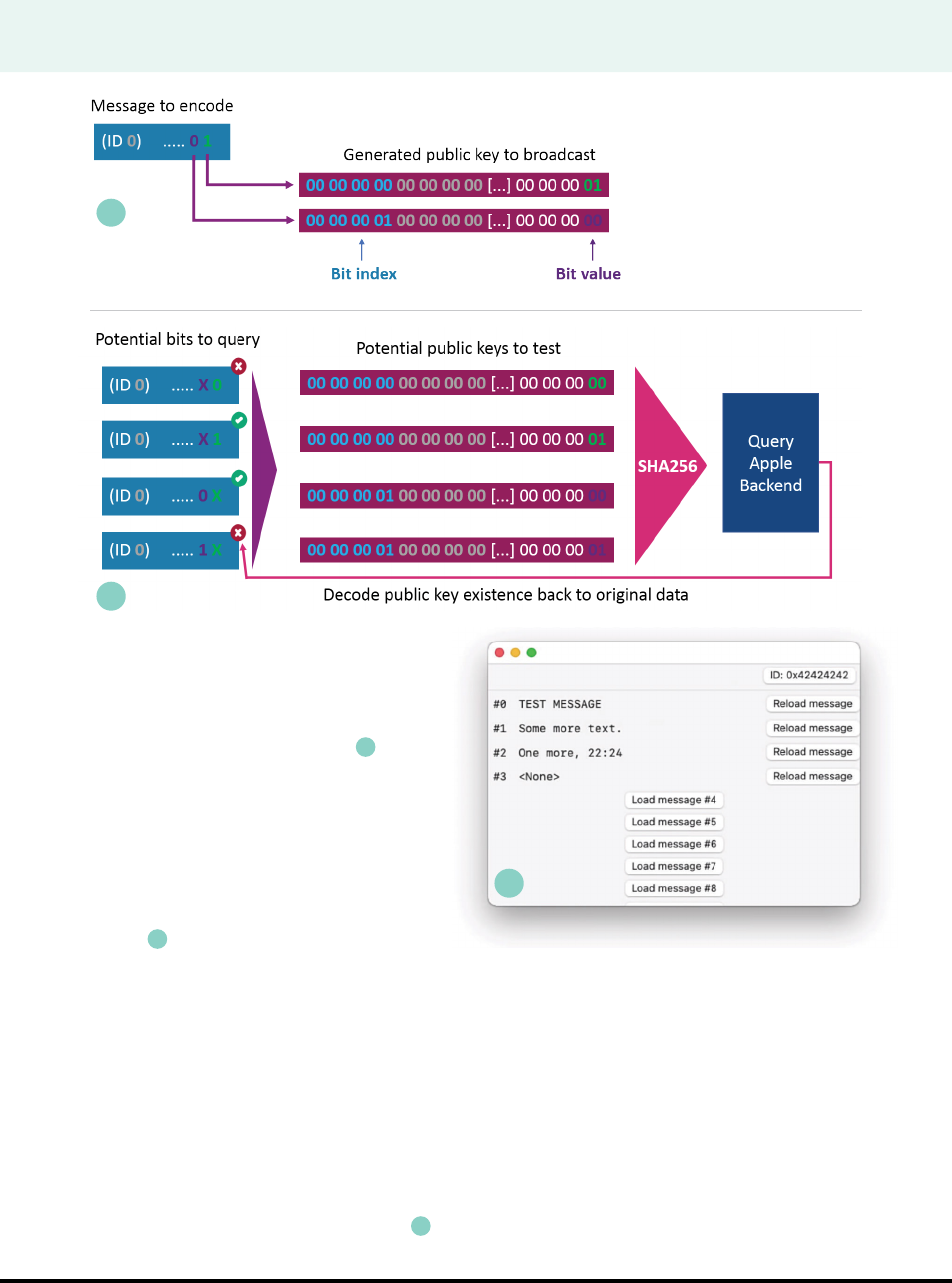
the information “bit 0 of message 0 is 1.”
To send a full message, the program
simply loops over its bits and sends out one
advertisement per bit with the public key that
encodes its index and value (Figure
G
).
When fetching data, the receiving application
will generate the same 28-byte arrays (two
per bit, for the possible bit values 0 and 1) and
query the Apple service with the hashes of those
“public keys.” There should be location reports
for only one of the two key IDs, which can then be
interpreted; for example, “bit at index 0 equals 1”
(Figure
H
).
Instead of only transferring one bit per
message, we could also send a full byte by
setting the last 8 bits of the public key. While this
increases the sending bandwidth, we now need
to request 255 different key IDs to fetch/”brute
force” one byte (compared to 16 when encoded
bit-by-bit).
I implemented this technique in Send My
(github.com/positive-security/send-my), a
modified version of OpenHaystack that turns an
ESP32 into a serial (upload only) modem and
includes a DataFetcher application (Figure
I
) to
retrieve sent messages for different modems.
Stealth Mode
Apple added a feature to iOS to detect unknown
AirTags traveling with the user and warn of them,
with the goal of preventing the tracking of other
people or their belongings. After numerous news
reports of AirTags being used to stalk women or
being placed in expensive cars to be stolen when
they arrived at the owner’s home, Apple also
issued an update for AirTags and iOS to reduce
the time until those warnings are triggered to
play a sound on the AirTag.
For Android, Apple released the TrackerDetect
app, though it does not run in the background and
G
H
I
Fabian Bräunlein
M83_110-17_SB_AirTags_F1.indd 115M83_110-17_SB_AirTags_F1.indd 115 10/11/22 12:08 PM10/11/22 12:08 PM
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
