37
Cognitive Radio Networks
Kwang-Cheng Chen
37.2 Cooperative Cognitive Radio Networks and Modeling
37.3 Spectrum Sensing and Tomography for CRN
37.4 Spectrum Sharing and Dynamic Spectrum Management
37.5 Routing, Power and Interference Control, and QoS Guarantees
37.1 Introduction
Since J. Mitola III proposed the concept of cognitive radio (CR) [1], cognitive radio technology with federal communication commission (FCC) endorsement has been widely considered as an emerging solution of crowded spectrum for future wireless communications. Haykins’ classic paper in 2005 [2] summarized important tasks to facilitate CRs. Particularly, the CR-transmitter (CR-Tx) shall identify the spectrum hole or white space in the spectrum for primary system (PS), such that CR-Tx can take this opportunity to transmit its message or packet(s) to the CR-receiver (CR-Rx). We may name such a link-level transportation of packets between CR-Tx and CR-Rx as a sort of opportunistic transmission. However, another major challenge arises to deal with multiuser opportunistic transmissions and to network CRs through opportunistic transmissions into the multihop cognitive radio network (CRN). This chapter therefore summarizes state-of-the-art CRN technology and its research opportunities at the horizon.
37.2 Cooperative Cognitive Radio Networks and Modeling
Once CR-Rx successfully receives the packet (or a message) from CR-Tx; an immediate challenge would be to transport such a packet from source (node) to destination (node). Multihop ad hoc network of CRs obviously serves the general purpose of CRN. Similar concepts were developed independently in earlier days around the birth of CR to demonstrate more networking efficiency [3,4]. However, we can leverage cooperative networking among coexisting multiradio networks that can be heterogeneous PSs and heterogeneous CR ad hoc networks, to form the most general CRN. In other words, as shown in Figure 37.1, cooperative relays among nodes in PSs and heterogeneous CR ad hoc networks can be used to realize a general-sense multihop CRN, say in Reference 5.
As a matter of fact, multihop CRN via cooperative relay forms heterogeneous wireless networks. We still wish to know whether CR can improve network efficiency or not, which is the ultimate purpose of CRN. A simple exploration was conducted in Reference 6, by considering a CR source node to send a packet to the CR destination node via cooperative and opportunistic relay through a primary system/network, without the interfering PS operating. The networking coding concept is used to develop the principles of routing algorithm. By generating random network topology to simulate such a scenario, without extra bandwidth (i.e., just using transmission opportunities from PS), 130% networking throughput gain is observed in average, with 92% chances to have gain (i.e., no gain due to prohibition to interfere PS in some cases). This experiment supports a critical fact that multihop CRN can indeed greatly enhance networking throughput without increasing frequency spectrum, much more than increasing at the physical layer due to transmission opportunities.

FIGURE 37.1 Cooperative multihop cognitive radio network.
CRN can be categorized into three types to reuse spectrum opportunities: interweave, overlay, and underlay [7]. The interweave paradigm is the original idea of cognitive radio to create the opportunistic communications (or transmission opportunities) if the primary system is not transmitting. The overall spectrum utilization is enhanced by opportunistic reuse when spectrum holes (or white spaces) exist. The overlay paradigm proceeds under the assumption that cognitive radios know the channel gains, codebooks, and messages from noncognitive radios. CRs can transmit simultaneously with noncognitive radios, and appropriate using of a part of the CR's power to relay the message can offset CR's interference to noncognitive radios. Overlay may be close to information theoretic limit. A more practical paradigm of CRN targeting higher spectrum utilization (than interweave) is underlay to allow CRs transmitting simultaneously with non-CRs as long as the invoked interference is below the acceptable limit, and typically through spatial reuse to achieve this goal. In this chapter, we treat interweave paradigm as the link-level CR and underlay as the new paradigm of CRN consisting of multiple CR links.
To realize general-sense multihop CRN, we have to first understand the nature of opportunistic links and appropriate model(s) to develop technologies of CRN. Note that CR can transmit only when PS is not transmitting, for any single link. Assuming that a primary communication system (or pair(s) of transmitter and receiver) is functioning, a cognitive radio that is the secondary user for the spectrum explores channel status and seeks an opportunity to utilize such a spectrum for communication. The channel can be commonly modeled as an Elliot–Gilbert channel with two possible states: existence of primary user's activity (i.e., CR transmission opportunity not available) and nonexistence of primary user's activity (i.e., CR's transmission opportunity available). Stefan Geirhofer, Lang Tong, and Brian M. Sadler have measured WLAN systems to statistically model the “white space” for cognitive radio transmission by the semi-Markov model [8]. Considering the practical operation of CRs, Figure 37.2 summarizes CR opportunistic operation using an embedded continuous-time Markov chain model, which may serve a basis to study more functions of CRN. Of course, there are more detailed studies of CR modeling, such as References 9 and 10. However, Figure 37.2 offers an opportunity to initiate useful explorations on the networking functions of CRN.
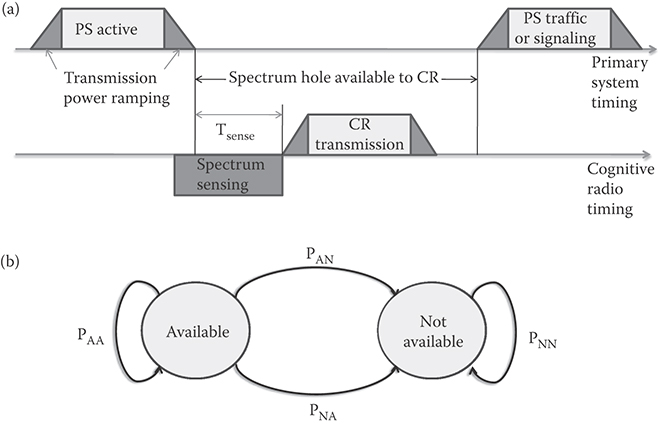
FIGURE 37.2 A model of CR link availability. (a) CR transmission opportunity window and (b) State transition of embedded markov chain for link availability.
37.3 Spectrum Sensing and Tomography for CRN
Conventional spectrum sensing to detect or to sense spectrum hole(s) or white space(s) at the link level (i.e., for an opportunistic transmission between a CR-Tx and CR-Rx pair) targets at a single primary system and is used to decide between the two hypotheses in discrete-time statistical signal processing [11], namely
where y[n] represent observation samples, s[n] and w[n] are contributed from PS signal and noise, respectively, and h is the channel gain observed at the CR. Numerous techniques to achieve the goal of spectrum sensing have been proposed, while details can be found in References 11 and 12. Generally speaking, among extensive literatures, the basic principles include
Energy detection
Matched filtering
Cyclostationary detection
Wavelet detection
Covariance-based detection
Multiple antenna
However, local detection at the CR might not be enough. Figure 37.3 delineates the well-known hidden terminal problem to reveal insufficiency of local sensing at CR due to either blocking or fading. A helpful approach is through cooperation, which is known as cooperative sensing [13–15] by placing multiple sensors/detectors in different locations. To implement cooperative spectrum sensing, CRs first send the raw data they collect to a combining user or fusion center. Alternatively, each node may independently perform local spectrum sensing, then reports either binary decision or test statistics to a combining node. Finally, the combining node makes a decision on the presence or absence of the licensed signal based on its received information.
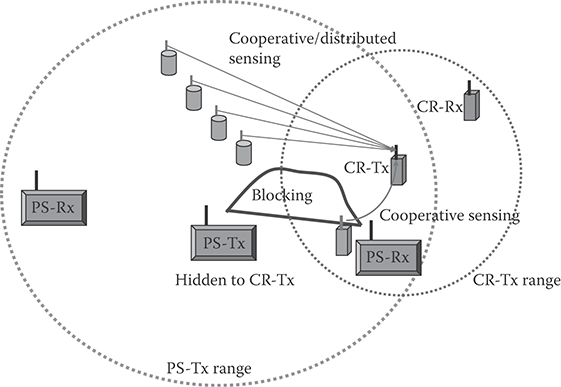
FIGURE 37.3 Hidden terminal problem and cooperative spectrum sensing.
A straightforward form of cooperative spectrum sensing is to transmit and to combine the samples received by all CR nodes/sensors in the local spectrum sensing phase [12]. Using random matrix theory, combining to process all the samples can be developed. Considering total K CRs and each taking N samples, we denote yk(n) as the sample received by the kth CR/sensor at the nth time instant, to construct the observation matrix
Although multiple CRs are involved, opportunistic link establishment is still the only concern in cooperative sensing. CRN must transport packets under multiple opportunistic links, and thus spectrum sensing must be able to support networking function such as medium access control (MAC) and routing for multiple CRs in the CRN, which creates a new scenario of spectrum sensing beyond traditional detection and estimation for a specific radio link. A possible approach is to use statistical inference [16] or even learning to learn radio resource availability of portion or entire radio resource of CRN. A simple, but useful, example to leverage statistical inference into such scenario can be illustrated. Suppose that a CR-Tx can observe link behaviors of a PS transmitter–receiver pair, which can be represented as “1” for active transmission and “0” for inactive in a given time slot. We may model such behavior as a Bernoulli process (i.e., each observation following an i.i.d. Bernoulli random variable). The key question is “can we predict the availability of the next time slot based on an earlier observation of L time slots?” Actually, this can be achieved by the well-known Laplace formula [16]. Let nL be inactive (radio resource available) time slots among these L observations. The probability of the next slot available for CR utilization (radio resource available) is
Generalizing this concept with well-known tomography, CRN tomography has been developed [17] to know a lot more information than traditional sensing over a single radio link, in CRN operation. Consequently, spectrum sensing of CRN can be treated into four categories on the following bases: (i) active probing or passive detection and (ii) to acquire link-level information or to acquire network-level information. Passive detection on link availability as traditional CR spectrum sensing falls into one of these four categories. With realizing network-level information such as radio resource, readers can easily tell the difference between sensing for CR's transmission opportunity and sensing for CRN, under this framework. Another statistical technique, information fusion, is useful in spectrum sensing. To obtain the observation matrix, some extra transmissions from cooperative sensors are needed, which wastes a lot of communication bandwidth that is targeted to save in cognitive radio. In [54], heterogeneous information fusion is introduced to observe different types of information at the CR-transmitter. Appropriate fusion can infer spectrum availability as good as cooperative sensing, without cooperative sensors. Currently, significant amount of research efforts are taken toward reliable spectrum sensing as its key role in dynamic spectrum access.
37.4 Spectrum Sharing and Dynamic Spectrum Management
As a matter of fact, multiuser CR communications have been discussed extensively in Haykins’ classic paper [2], including coordination of transmissions (widely known as MAC), transmission power control, and the associated game theory treatment.
MAC of cognitive radios when spectrum opportunities are available has been discussed in various ways. A straightforward thinking is to treat MAC of these CRs as the classical multiple access. As CRs are usually distributed and centralized control may not exist unless a common control channel is available in those systems such as IEEE 802.22, distributed random access mechanisms are usually considered, such as ALOHA and CSMA (carrier sense multiple access), while Reference 18 summarizes a review of several interesting explorations.
Another interesting approach is to study the MAC design as a mathematical optimization. Let us consider a set of frequency bands to represent the general case, although more dimensional radio resource can be considered. Suppose the frequency bands that we are interested in (typically PS operating) are a set of numbered bands, . At time tn, the CRN operation allows an update of spectrum utilization. The nth observation (or allocation) time interval is [tn,tn+1). Due to the opportunistic nature of each link (thus frequency band) modeled as a Markov chain, the ith frequency band is available following a Bernoulli process with probability πi available, and is invariant to time.
We define the following indicator function:
For perfect spectrum sensing, we can determine (37.1) in a reliable way. However, any spectrum sensing has some vulnerable situations, and thus we need to consider more to decide MAC. Following (37.1), the probability mass function (pmf) of Bernoulli random variable at the ith frequency band is
It is reasonable to assume independent, n = 1, …, L, where L implies the observation interval depth. Denote
For reliable CR operation, spectrum sensing is necessary, so that CR-Tx can have information about the availability of each frequency band. However, for network operations on top of CR links, the strategy would be highly related to π.
Case 1: π is known.
Case 2: π is unknown.
Case 3: π can be detected or estimated via some CRN sensing or tomography methods.
Traditional CR functions as follows: At time tn, CR learns the availability of a selected frequency band sn (typically via spectrum sensing). If , information amount B can be successfully transmitted. For L time durations, the overall throughput is
In case π is known, the spectrum sensing strategy for a CR is simply to select channel to sense. Then, access decision is therefore optimally or suboptimally made based on certain decision criterion and conditions, such as formation as a partially observed Makovian decision process [19]. More in-depth explorations can be found in Reference 20, and some detailed reviews in References 12 and 21. The authors in Reference 22 consequently suggest a framework for CRN functions, one step closer to realistic CRN.
Keen readers may note that effective access and thus throughput really relies on effective sensing. The relationship between throughput and sensing is therefore important. In a CRN, the secondary users are allowed to utilize the frequency bands of primary users when these bands are not currently being used. To support this spectrum reuse functionality achieving spectrum efficiency, the secondary users shall sense the radio frequency environments for transmission opportunities. This can be viewed from two parameters associated with spectrum sensing: probability of detection and probability of false alarm. The higher the probability of detection, the better the primary users are protected. However, from the secondary users’ perspective, the lower the probability of false alarm, the more chances the channel can be reused when it is available, thus the higher the achievable throughput for the secondary network. In Reference 23, authors study the problem of designing the sensing duration to maximize the achievable throughput for the secondary network under the constraint that the primary users are sufficiently protected. Sensing-throughput is thus a trade-off mathematically. Using an energy detection sensing scheme, the existence of optimal sensing time is proved, which yields the highest throughput for the secondary network [23]. This optimal sensing time decreases when distributed spectrum sensing is applied. An optimal joint design has been proposed [24]. However, almost all existing research efforts assume synchronous operation of CRs and PS, which is obviously far away from the true situation, as it takes a huge amount of communication overhead to reach this status, or is nearly impossible due to the nature of CRs’ operation. An ice-breaking study in Reference 25 considers asynchronous dynamic channel access with only prior knowledge about the frame length. Under the new operating philosophy facilitated by game theory, asynchronous dynamic spectrum access achieves surprising performance better than that of synchronous operation, which opens a new door toward practical CRN design in a distributed way as the most recent state of the art.
On the other hand, the above optimization of channel utilization leads to a new research subject of spectrum sharing or spectrum management, that is, how to utilize a collection of frequency bands, , for homogeneous or heterogeneous CRN(s). To fully exploit spectrum management, we have to consider a more general situation related to networking technology and networking economy. What is the reason for PS to allow CR operation? The reasons might be that (i) PS users can gain some incentives from such a way of operation and (ii) the CR concept can indeed enhance entire spectrum utilization so that the regulator would enforce CR as a policy. As the spectrum access or utilization actually involves more than technical concerns and also economic incentives, it brings spectrum management under CRN to a new wide-open interdisciplinary study. Game theory (auction could be considered as a game) has been introduced to model such behaviors [26,27], which set up the ground for possible commercial operation of CRN. Spectrum sharing has been studied not only in centralized infrastructure wireless networks but also in multihop ad hoc networks [28]. There exist some good follow-up explorations. To be practically feasible, we have to ensure satisfaction from four parties in the CRN operation:
Primary system users
Cognitive radios (secondary) users
Service provider(s)
Regulator wishing to optimize total spectrum utilization
A spectrum-management policy framework based on the Vickrey auction has been proposed [29] such that CR mobile stations can compete for utilization of the primary user network spectrum bands available for opportunistic transmissions. It is shown that CRN can indeed satisfy the above four different parties to achieve a win–win situation, as a practical technoeconomic foundation of CRN.
37.5 Routing, Power and Interference Control, and QoS Guarantees
The fundamental task of networking functions might be routing in multihop CRN. As a matter of fact, routing for mobile ad hoc networks has been extensively studied in the literature and we do not repeat it here. Due to the opportunistic and dynamic nature of CRN, routing appears to be a great intellectual challenge in multihop CRN. Reference 11 gives a summary of some initial thinking to completely deal with such challenges, namely, opportunistic links, sensing reliability and overhead, dynamic topology, likely unidirectional links, heterogeneous wireless networks, calerability, and so on which suggests a wide-open research opportunity, particularly for multihop ad hoc CRN.
Since the basic CR operation must not interfere with the transmissions of the licensed or primary users (PUs), this generally incurs a trade-off in the CRN performance. In order to evaluate this trade-off, a distributed CR routing protocol for ad hoc networks (CRP) is proposed [30] to achieve (i) explicit protection for PU receivers that are generally not detected during spectrum sensing, (ii) allowing multiple classes of routes based on service differentiation in CR networks, and (iii) scalable, joint route-spectrum selection. A key novelty of CRP is the mapping of spectrum selection metrics and local PU interference observations to a packet forwarding delay over the control channel. This allows the route formation undertaken over a control channel to capture the environmental and spectrum information for all the intermediate nodes, thereby reducing the computational overhead at the destination. Further underlay ad hoc CRN routing is still subject to innovative breakthroughs.
As a matter of fact, another major challenge of CRN functions is its operating in the interference-limited environments, particular for underlay CRN that brings the benefits of spectrum efficiency as a major attraction of CRN. Consequently, good mathematical modeling of interference in wireless networks is greatly needed. The mathematical model of network interference has been well organized and demonstrated how to model CRs [31]. The interference in large wireless networks has remarkably been explored in Reference 32, which is useful to understand some fundamental behaviors in interference-limited wireless networks. As each link in such wireless link may suffer severe fading and potential outage, random graph model of wireless networks becomes an important analytical tool, while Reference 33 presents an award-winning review, based on stochastic geometry. There are generally three critical factors in such modeling:
Spatial distribution of the nodes
Wireless propagation characterization
Overall impact of interferers including mobility and session lifetime
We can always describe network topology via a graph , defined by the collection of vertices, V, and the collection of edges, E. A vertex represents a node in a wireless network and an edge represents a link between two nodes. Erdös and Rényi pioneered the random graph theory. Among a number of random graph methodologies, we usually model the spatial distribution of the nodes according to a homogeneous Poisson point process in the two-dimensional infinite plane. The probability of n nodes being inside a region (not necessarily connected) depends only on the total area AR of the region and is given by
where λ is the spatial density of (interfering) nodes.
Regarding propagation and fading effect, the received power, PRx, at a distance r from a transmitter with power PTx is
where d is the amplitude loss exponent depending on the environment with typical range from 0.8 (hallways) to 4 (dense urban), and 1 for free-space propagation from point source. {Zk} are independent random variables to account for propagation effects such as fading and shadowing. An earlier model of link availability can also serve the purpose of modeling session lifetime.
Based on such analytical methodology, some important issues can be derived for routing (and other network functions) of CRN. The first wanted might be connectivity for a node in CRN [34], and its resulting delay. Transmission capacity is also desirable to know but it is hard to calculate precisely, with bound being available in [35]. As the connectivity is critical for routing algorithm, connectivity of cooperative multihop ad hoc CRNs can be found [36]. We do expect a lot of fruitful results coming from global researchers. However, there are more network functions for CRN as new challenges, particularly under the random nature of opportunistic links in CRN. MIMO-empowered multihop CRN to optimize throughout was introduced [37]. While dealing with end-to-end control, Figure 37.4 suggests a view to form multiple paths between source and destination for multihop CRN. After reorganization, these paths are just like MIMO by a directed graph between source node and destination node. This concept was first applied to end-to-end error control [38]. With a hybrid ARQ on top of a multipath concept, we can achieve reliable communications, while any single path of multipath may fail, without feedback control that is particularly critical for opportunistic links. When we have to deal with quality of service (QoS) as the fundamental need of networking, we can again apply formation of multipath to reach statistical control of QoS [39], and further consider routing and QoS together [40] with help from the effective bandwidth.
There are more issues of concern in CRN networking, for example, QoS provisioning of heterogeneous services in CRN [41] and delay of real-time traffic over CRN [42]. Furthermore, for multimedia communications, in addition to typical QoS factors such as radio link reliability, maximum tolerable communication delay, and spectral efficiency, CR spectrum sensing frequency and packet-loading scheme have great impacts on multimedia QoS. The optimal spectrum-sensing frequency and packet-loading solutions for a multichannel can be obtained by using the combination of Hughes–Hartogs and discrete particle swarm optimization (DPSO) algorithms with experimental verifications [43]. Associated with QoS, call admission and capacity analysis are considered in Reference 44.
Researchers have started to note spectrum sensing associated with location for different purposes [45]. A different thinking may arise when implementing routing algorithms, to route based on the spectrum map. The spectrum map indicates radio resource versus location information, at a given time and a given frequency band. Such spectrum map was first constructed via synthetic aperture radar [46]. As CRN routing may not require precise information from the spectrum to save communication overhead, a compressed sensing-based approach has been proposed [47]. With the aid from spectrum map, routing for CRN can be facilitated through modifying well-known opportunistic routing over opportunistic links [48].

FIGURE 37.4 Multipath formation of multihop CRN. (a) Using cooperative relay. (b) Graph model of multipath relay.
37.6 Applications to Cellular Systems and Machine-to-Machine Communications and International Standards
Although it might take a while to really facilitate complete CRN technology for wide applications, we can still take advantage of the CRN concept into the immediate system application scenario. A possible application scenario is femto-cell technology in 3GPP so that 3G LTE (long-term evolution) and LTE-A can well extend network coverage and thus better networking throughput. However, femto-cell systems are not arranged in a perfectly controlled way as traditional 3G cellular systems, due to easy installation. This creates a lot of new challenges in system design such as synchronization, interference alignment, or radio resource management. Let us look at radio resource management of OFDMA, that is, to allocate radio block (RB, grid of frequency–time transmission bandwidth).
As a misalignment between femto-cells and Macrocell to greatly degrade system performance, we may propose that the cognitive radio resource management (CRRM) consists of the following steps [49]:
The femto-BS periodically senses the channel to identify which RB to be occupied by the Macrocell. The sensing period is Ts frames and each channel sensing persists for one frame, to align with RB on the cell boundary. Thus, for the femto-cell, a frame is referred to the “sensing frame” if the femto-BS performs channel sensing at that frame. On the other hand, a frame is referred to the “data frame” if the femto-BS does not perform channel sensing at that frame. The femto-BS cannot perform data transmission and reception within the sensing frame.
The femto-BS senses the received interference power on each RB within the sensing frame.
If the received interference power on an RB exceeds a certain threshold, the RB is identified as being occupied by the Macrocell.
Otherwise, the RB is unoccupied by the Macrocell.
In subsequent data frames, the femto-BS only allocates unoccupied RBs sensed in the sensing frame to its femto-MSs.
The femto-BS also extracts the following parameters from channel sensing:
The traffic load of the Macrocell
The RBs allocation correlation probability of the Macro cell
The fraction of correlated RBs allocation of the Macrocell through the effective bandwidth facilitation of radio resource allocation
This approach to leverage CR's sensing to greatly improve RB allocation is adopted in 3GPP and can be generalized into two-tier macro-femto heterogeneous wireless networks. Various ways are summarized to implement such a concept into different types of systems [50], as an immediate realization of CRN.
As a matter of fact, another promising application for CRN is machine-to-machine (M2M) communications, which has to deal with a tremendous number of wireless devices and likely has to transport traffic through spectrum sharing mechanism due to the scare spectrum. Figure 37.5 depicts such an application scenario, similar to Internet of Things (IoT) or cyber-physical systems (CPS). It is challenging to establish effective communication between cloud and data aggregators or even machines. 3GPP LTE-A is therefore considering machine-type communication (MTC), and access for such massive devices becomes an immediate challenge [55]. For the “swarm communications” at the edge of the Internet for tremendous amount of sensors and machines to data aggregators as local networks shown in Figure 37.5, spectrum-sharing networks, likely CRN, might be the only solution.
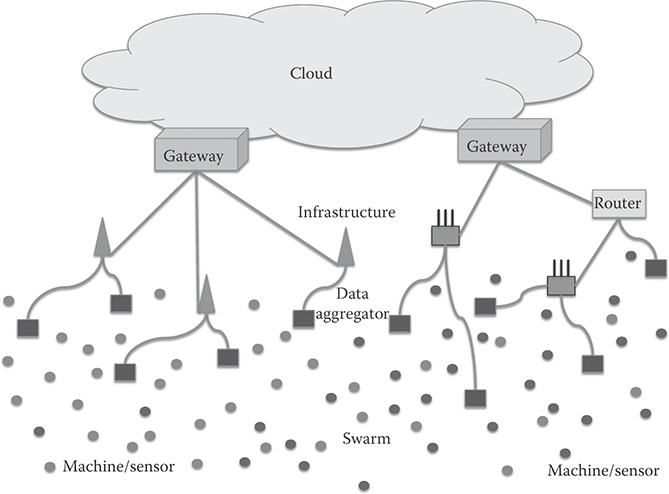
FIGURE 37.5 Scenario of M2M communications.
The concept of cognitive radio has been adopted in international communication standards for years. While dealing with the coexistence in Bluetooth 2.0 and IEEE 802.15.2 in the first couple of years of the twenty-first century (shortly after the birth of cognitive radio in 1999), adaptive frequency hopping (AFH) technology was applied by first conducting spectrum sensing at the 2.4 GHz ISM band, and then real-time adjusting hopping patterns to avoid interference from other systems for successful transmission, particularly for stream traffic. The later examples include sensing to avoid radar signals in 5 GHz wireless LANs, and Detect-And-Avoid (DAA) for ultra-wide-band communications. However, they are just examples of cognitive radio as a core technology in a standard. The very first international standard effort for cognitive radio should be IEEE 802.22 to allow transmission over TV white spaces. Actually, IEEE 802.19 is dealing with technical advisory to multiradio coexisting systems, while cognitive radio technology is definitely within the scope. The IEEE 802.22 Working Group was formed in November 2004 for Wireless Regional Area Networks (WRAN). This working group is dedicated to develop an air interface (i.e., MAC and PHY) based on CRs for unlicensed operations in the TV broadcast bands. This standard plays a key role in the evolution of CRs and goals at defining an international standard that may regulate in any regulatory regime.
The IEEE P1900 Standards Group was established in 2005 jointly by the IEEE Communications Society and the IEEE Electromagnetic Compatibility Society. The objective is to develop supporting standards dealing with new technologies and techniques for next-generation radio and advanced spectrum management. Note that this sponsor group was called SCC41—The Standards Coordination Committee 41. Currently, there is an ever-increasing number of international standards considering CRN technology due to the shortage of radio spectrum. Both ITU and ETSI are seriously considering CR into wireless communications and networks [51].
As a conclusion to this chapter, although facing tremendous technology challenges subject to more imaginative approaches such as biology-inspired thinking [52] or sociological thinking [53], CRNs are definitely the direction for future wireless communications and networks so that a large number of wireless devices can be connected to improve the quality of human life.
References
1. J. Mitola, III, G.Q. Maguire, Cognitive radio: Making software radios more personal, IEEE Pers. Commun., 6(4), 13–18, 1999.
2. S. Haykins, Cognitive radio: Brain-empowered wireless communications, IEEE J. Selected Areas Commun., 23(2), 201–220, 2005.
3. T.J. Shepard, Decentralized Channel Management in Scalable Multihop Spread-Spectrum Packet Radio Networks, PhD dissertation, MIT, Cambridge, MA, 1995.
4. P. Gupta and P.R. Kumar, The capacity of wireless networks, IEEE Trans. Inform. Theory, 46(2), 388–404, 2000.
5. K.-C. Chen, P.-Y. Chen, N. Prasad, Y.-C. Liang, and S. Sun, Trusted cognitive radio networking, Wireless Communications and Mobile Computing, Wiley, 2010.
6. C.-H. Huang, Y.-C. Lai, and K.-C. Chen, Network capacity of cognitive radio relay networks, Phys. Commun., 1(2), 112–120, 2008.
7. A. Goldsmith, S.A. Jafar, I. Maric, and S. Srinivasa, Breaking spectrum gridlock with cognitive radios: An information theoretic perspective, Proc. IEEE, 97(5), 894–914, 2009.
8. S. Geirhofer, L. Tong, and B. M. Sadler, Dynamic spectrum access in the time domain: Modeling and exploiting white space, IEEE Commun. Mag., pp. 66–72, May 2007.
9. V. Pla, J.R. Vidal, J. Martinez-Bauset, and L. Guijarro, Modeling and characterization of spectrum white spaces for underlay cognitive radio networks, Cape Town, IEEE International Conference on Communications, 2010.
10. B. Canberk, I.F. Akyildiz, and S. Oktug, Primary user activity modeling using first-difference filter clustering and correlation in cognitive radio networks, to appear IEEE/ACM Transactions on Networking, 19(1), 170–183, Feb. 2011.
11. K.-C. Chen, B.K. Cetin, Y.-C. Peng, N. Prasad, J. Wang, and S. Lee, Routing for cognitive radio networks consisting of opportunistic links, Wireless Communications and Mobile Computing, 10(4), 451–466, 2010.
12. Y.C. Liang, K.C. Chen, Y.J. Li, and P. Mähönen, Cognitive radio networking and communications: An overview, IEEE Trans. Vehicular Technol., 60(7), 3386–3407, 2011.
13. G. Ganesan and J. Li, Cooperative spectrum sensing in cognitive radio, Part I: Two-user networks, IEEE Trans. Wireless Commun., 6(6), 2204–2213, 2007.
14. G. Ganesan and J. Li, Cooperative spectrum sensing in cognitive radio, Part II: Multiuser networks, IEEE Trans. Wireless Commun., 6(6), 2214–2222, 2007.
15. J. Unnikrishnan and V. V. Veeravalli, Cooperative sensing for primary detection in cognitive radio, IEEE J. Selected Topics Signal Process., 2(1), 18–27, 2008.
16. K.C. Chen, S. Y. Tu, and C. K. Yu, Statistical inference in cognitive radio networks, IEEE ChinaCom, Xi-An, August 2009.
17. C.K. Yu, S. Cheng, and K. C. Chen, Cognitive radio network tomography, the special issue of achievements and road ahead: The first decade of cognitive radio. IEEE Trans. Vehicular Technol., 59(4), 1980–1997, 2010.
18. C. Cormio and K. R. Chowdhury, A survey on MAC protocols for cognitive radio networks, Ad Hoc Networks, 7, 1315–1329, 2009.
19. Q. Zhao, L. Tong, A. Awami, and Y. Chen, Decentralized cognitive MAC for opportunistic spectrum access in ad hoc networks: A POMDP framework, IEEE J. Selected Areas Commun., 25(3), 589–600, 2007.
20. L. Lai, H. El Gamal, H. Jiang, and H.V. Poor, Cognitive medium access: Exploration, exploitation, and competition, IEEE Trans. Mobile Comput., 10(2), 239–253, 2011.
21. K.C. Chen and R. Prasad, Cognitive Radio Networks, West Sussex, UK, Wiley, 2009.
22. W.-Y. Lee and I.F. Akyildiz, A spectrum decision framework for cognitive radio networks, IEEE Trans. Mobile Comput., 10(2), 161–174, 2011.
23. Y.-C. Liang, Y. Zeng, E.C.Y. Peh, and A.T. Hoang, Sensing-throughput tradeoff for cognitive radio networks, IEEE Trans. Wireless Commun., 7(4), 1326–1337, 2008.
24. A.A. El-Sherif and K.J.R. Liu, Joint design of spectrum sensing and channel access in cognitive radio networks, IEEE Trans. Wireless Commun., 10(6), 1743–1753, 2011.
25. Y.Y. Lin and K. C. Chen, Asynchronous dynamics spectrum access, IEEE Trans. Vehicular Technol., 61(1), 222–236, January 2012.
26. D. Niyato and E. Hossain, Competitive pricing for spectrum sharing in cognitive radio networks: Dynamic game, inefficiency of Nash equilibrium, and collusion, IEEE J. Selected Areas Commun., 26(1), 192–202, 2008.
27. D. Niyato and E. Hossain, Competitive spectrum sharing in cognitive radio networks: A dynamic game approach, IEEE Trans. Wireless Commun., 7, 2651–2660, 2008.
28. Y. Thomas Hou and Y. Shi, Spectrum sharing for multi-hop networking with cognitive radio, IEEE J. Selected Areas Commun., 26(1), 146–155, 2008.
29. H.B. Chang and K.C. Chen, Auction based spectrum management of cognitive radio networks, the special issue of achievements and road ahead: The first decade of cognitive radio, IEEE Trans. Vehicular Technol., 59(4), 1923–1935, 2010.
30. K.R. Chowdhury and I.F. Akyildiz, CRP: A routing protocol for cognitive radio ad hoc networks, IEEE J. Selected Areas Commun., 29(4), 794–804, 2011.
31. M.Z. Win, P.C. Pinto, and L.A. Sheep, A mathematical theory of network interference and its applications, Proc. IEEE, 97(2), 205–230, 2009.
32. M. Haenggi and R.K. Ganti, Interference in large wireless networks, Foundations Trends Networking, 3(2), 127–248, 2008.
33. M. Haenggi, J. Andrews, F. Baccelli, O. Dousse, and M. Franceschetti, Stochastic geometry and random graphs for the analysis and design of wireless networks, IEEE J. Selected Areas Commun., 27(7), 1029–1046, 2009.
34. W. Ren, Q. Zhao, and A. Swami, On the connectivity and multihop delay of ad hoc cognitive radio networks, IEEE J. Selected Areas Commun., 29(4), 805–818, 2011.
35. W.C. Ao and K.C. Chen, Upper bound on broadcast transmission capacity of heterogeneous wireless ad hoc networks, IEEE Commun. Lett., 15(11), pp. 1172–1174, 2011.
36. W.C. Ao, S.M. Cheng, and K.C. Chen, Connectivity of multiple cooperative cognitive radio ad hoc networks, IEEE J. Selected Areas Commun., 30(2), 263–270, February 2012.
37. C. Gao, Y. Shi, Y.T. Hou, and S. Kompella, On the throughput of MIMO-empowered multihop cognitive radio networks, IEEE Trans. Mobile Comput., 10(1), 1506–1519, 2011.
38. W.C. Ao and K.C. Chen, End-to-end HARQ in cognitive radio networks, IEEE Wireless Communications and Networking Conference, Sydney, 2010.
39. H.B. Chang, S.M. Cheng, S.Y. Lien, and K.C. Chen, Statistical delay control of opportunistic links in cognitive radio networks, IEEE International Symposium on Personal Indoor Mobile Radio Communications, Istanbul, 2010.
40. P.Y. Chen, S.M. Cheng, W.C. Ao, and K.C. Chen, Multi-path routing with end-to-end statistical QoS provisioning in underlay cognitive radio networks, IEEE INFOCOM Workshop, Shanghai, 2011.
41. A. Alshamrano, X.S. Shen, and L.-L. Xie, QoS provisioning for heterogeneous services in cooperative cognitive radio networks, IEEE J. Selected Areas Commun., 29(4), 819–820, 2011.
42. Z. Liang, S. Feng, D. Zhao, and X. Shen, Delay performance analysis for supporting real-time traffic in a cognitive radio sensor network, IEEE Trans. Wireless Commun., 10(1), 325–335, 2011.
43. X.-L. Huang, G. Wang, F. Hu, and S. Kumar, The impact of spectrum sensing frequency and packet-loading scheme on multimedia transmission over cognitive radio networks, IEEE Trans. Multimedia, 13(4), 748–761, 2011.
44. S. Gunawardena and W. Zhuang, Capacity analysis and call admission control in distributed cognitive radio networks, IEEE Trans. Wireless Commun., 10(9), 3110–3120, 2011.
45. T. Do and B.L. Mark, Joint spatial-temporal spectrum sensing for cognitive radio networks, IEEE Trans. Vehicular Technol., 59(7), 3480–3490, 2010.
46. T.W. Chiang and K.C. Chen, Synthetic aperture radar construction of spectrum map for cognitive radio networking, International Conference on Wireless Communications and Mobile Computing, Caen, France, 2010.
47. S.Y. Shih and K.C. Chen, Compressed sensing construction of spectrum map for routing in cognitive radio networks, IEEE Vehicular Technology Conference—Spring, Budapest, 2011.
48. S.C. Lin and K.C. Chen, Spectrum aware opportunistic routing in cognitive radio networks, IEEE GLOBECOM, Miami, 2010.
49. S.Y. Lien, Y.Y. Lin, and K.C. Chen, Cognitive and game-theoretical radio resource management for autonomous femtocells with QoS guarantees, 10(7), 2196–2206, IEEE Trans. Wireless Commun., 2011.
50. S.M. Cheng, S.Y. Lien, F.S. Chu, and K.C. Chen, On exploiting cognitive radio to mitigate interference in macro/femto heterogeneous networks, IEEE Wireless Commun., special issue on Heterogeneous Networks, 18(3), 40–47, 2011.
51. S. Filin, H. Harada, H. Murakami, and K. Ishizu, International standardization of cognitive radio systems, IEEE Commun. Mag., pp. 82–89, March 2011.
52. P. Di Lorenzo and S. Barbarossa, A bio-inspired swarming algorithm for decentralized access in cognitive radio, IEEE Trans. Signal Process., 59(1), 6160–6174, 2011.
53. H. Li and Z. Han, Socially optimal queuing control in cognitive radio networks subject to service interruptions: To queue or not to queue? IEEE Trans. Wireless Commun., 10(5), 1656–1666, 2011.
54. C.H. Huang, and K.C. Chen, Dual-observation time division spectrum sensing for cognitive radios, IEEE Trans. Vehicular Technol., 60(7), 3712–3725, 2011.
55. S.Y. Lien, K.C. Chen, and Y.H. Lin, Toward ubiquitous massive accesses in 3GPP machine-to-machine communications, IEEE Commun. Mag., 49(4), 66–74, 2011.
