|
|
Chapter 11 |
If the National Security Agency (NSA) needs a slogan, it should probably be ‘collect it all.’ But the fight over whether that’s an appropriate strategy for keeping order in a democratic society is one that stretches far beyond the NSA programs now being debated. We now have technologies that enable the creation of very detailed data on our activities. These technologies are only going to get more powerful and pervasive. We need to make a choice as a society about the extent to which we want to allow the government to store up that data so that it has the power to hit ‘rewind’ on everybody’s lives.189
National Security Agency (NSA)
There are clearly three groups of people who are giving thought to the NSA and its mass data collection. First, there are those who really don’t care because they rationalize they haven’t done anything wrong; if the government has data about them, it’s not a big deal. Second, there are those who think we must allow the government to have powerful surveillance techniques to protect against criminals and terrorists. And third, there are the people who are sure the Orwellian prophesy of 1984 is here and who are fighting to turn back the government’s spying powers.
The following graph shows the public’s attitude on NSA spying in just two areas. Surprisingly the majority thought that the NSA was justified in monitoring phones but were a little more mistrustful of E-mail monitoring.
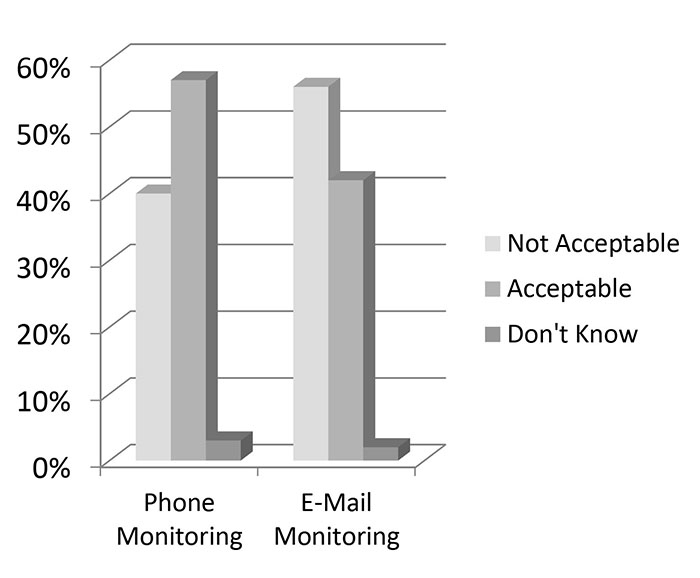
Public Attitudes toward NSA Spying—Pew Research190
Maybe the first group would care a little more if they realized the extent of the spying. Not only do the NSA and other government agencies collect phone and email records, they also collect financial transactions, hotel records, Google searches, images taken by street cameras, plane reservations, medical records, credit and debit card transactions—the list goes on and on. While most of the people in this group are focused on illegal hackers, they forget that their government is also collecting sensitive information about them, their families, their friends and the people they do business with.
…[M]ore revelations pointed to NSA efforts to decrypt or surveil data as it traveled between the data centers of companies like Yahoo! and Google. Yet another program siphoned users’ entire contact lists from services like Gmail, Yahoo! Mail, Hotmail and Facebook–NSA documents cited a single day when 82,857 contact lists were taken from Facebook users.191
Documents seen and published by the New York Times show that the NSA can harvest information such as a person’s age, location and sexual orientation from the data sent over the Internet by apps. Such personal details are contained in the data that apps send back to the companies that maintain and support them. This includes data sent to companies that serve and target ads in mobile apps. Google Maps was singled out as leaking particularly useful data for surveillance purposes. Documents from the NSA note how search queries intercepted from this app can reveal a person’s movements.192
But let’s move to the second group, who argue that we need to encourage the NSA in its data collection methods. One of those is Fareed Zakaria, noted author and host of GPS on CNN. He writes in Time Magazine that “The U.S.—its government, businesses and people—is under massive, sustained surveillance and infiltration by criminals, terrorists and foreign governments.”193 He points out that the theft of intellectual property and trade secrets from the U.S. networks is very prevalent, and utility companies have seen a tremendous rise in cyber-attacks. He states, “We all live, bank, work and play in a new parallel world of computer identities, data and transactions. But we do not seem to realize that this enormous freedom of activity in the cyberworld, as in the real world, has to be defended.”194
Michelle Van Cleave, head of U.S. counterintelligence under President George W. Bush, asks, “Is our privacy being violated when computers churn through billions of strings of digital data looking for signals of terrorist activity? Or is that something that we need the government to do to keep us safe? Don’t intrude but keep me safe. How to square such a circle? Today, when a personal video can ‘go viral’ in an instant, five hundred million people have a follow-me-right-this-second Twitter account, and some two billion people have access to the Internet, the digital records of U.S. citizens are comingled with the rest of the world in a maze of activity that is a fount of intelligence information.”195
And she voices my own opinion about the flurry over the NSA in asking about the thousands of data brokers who are collecting even more data than our government. Of that, Van Cleave says, “I find the loss of privacy in today’s digital world very troubling—but not because of the U.S. government. It’s the cookies that enable some Web merchant to track what I buy online and send me tailored ads to buy more. It’s the manner in which the Apple cloud insists on scooping up my entire personal calendar and contact information—and I can’t opt out if I want my cell phone to work. It’s the ever-vigilant, ever-ready Chinese microchip in my laptop computer, including the little extra that takes over the video camera and watches the room. Where is the public outrage about all of that?”196
Not a day goes by without several new articles about the NSA appearing in newspapers, magazines and blogs. Edward Snowden opened the door to heavy scrutiny of our intelligence gathering agencies—whether he should be considered a patriot or a traitor is still to be determined. Unfortunately, without massive surveillance, the government has no way of separating the “good” people from the “bad.” If they could not track certain phrases or anomalies in conversations and online communications, potential attacks against critical transportation, power, water, communication, financial and other infrastructures would be almost impossible to detect.
The final group of people are those who are actively fighting to turn back the government’s ability to collect and analyze any and all types of data about both its citizens and people in other countries. In the wake of the NSA revelations, there has been an avalanche of state bills requiring law enforcement to obtain a probable cause warrant before tracking an individual’s location in an investigation. Most state legislators know they can’t control the NSA—but they can control their state and local law enforcement agencies, which are engaging in some of the same invasive practices. The trend actually started in the wake of the ACLU’s nationwide public records requests on location tracking and the 2013 U.S. v. Jones decision.197
The U.S. v. Jones was a landmark case in which the government had placed a GPS device on a defendant’s car and tracked his movements for a month without a search warrant. It then justified its actions by arguing that the Fourth Amendment did not apply because the car was traveling on public streets. The court of appeals rejected that argument, stressing the intrusiveness of GPS technology and noting that tracking someone’s movements over an extended period reveals a great deal about a person beyond his/her mere location at any particular moment.198
Supreme Court Justice Sonia Sotomayor makes this point in her concurring opinion in U.S. v. Jones. Citing the Smith ruling, she wrote:
“It may be necessary to reconsider the premise that an individual has no reasonable expectation of privacy in information voluntarily disclosed to third parties. This approach is ill suited to the Digital Age, in which people reveal a great deal of information about themselves to third parties in the course of carrying out mundane tasks. People disclose the phone numbers that they dial or text to their cellular providers; the URLs that they visit and the e-mail addresses with which they correspond to their Internet service providers; and the books, groceries, and medications they purchase to online retailers. Perhaps, as Justice Alito notes, some people may find the ‘tradeoff’ of privacy for convenience ‘worthwhile,’ or come to accept this ‘diminution of privacy’ as ‘inevitable,’ and perhaps not. I for one doubt that people would accept without complaint the warrantless disclosure to the Government of a list of every Web site they had visited in the last week, or month, or year.”199
Justice Sotomayor also worries that citizens might choose not to attend certain political, cultural or religious events for fear of being publicly associated with a group or idea.
Exploiting Vulnerabilities
Heartbleed is a very far-reaching cyber-security scare, and experts say data will continue to be difficult to secure. By one estimate, as much as 66% of the Web is affected, including Yahoo! and OKCupid. “There are no secrets on the Internet,” says Ari Takanen, who works for the security firm that discovered Heartbleed. “Something bad can always happen.”200
The U.S. National Security Agency knew for at least two years about a flaw in the way that many websites send sensitive information, now dubbed the Heartbleed bug, and regularly used it to gather critical intelligence, people familiar with the matter said. The agency’s reported decision to keep the bug secret in pursuit of national security interests threatens to renew the rancorous debate over the role of the government’s top computer experts. The NSA, after declining to comment on the report, subsequently denied that it was aware of Heartbleed until the vulnerability was made public by a private security report earlier this month.201
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the Open SSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. It allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.202
Critics accuse the NSA of exploiting Heartbleed to obtain passwords and other basic data that are the building blocks of the sophisticated hacking operations at the core of its mission at a cost to millions of ordinary users who were left vulnerable to attack from criminal hackers. The NSA devotes millions of dollars and has over 1,000 experts devoted to hunting for common software flaws that are critical to stealing data from secure computers. Open-source protocols like OpenSSL, where the flaw was found, are primary targets. The agency found Heartbleed shortly after its introduction, according to one of the people familiar with the matter.203
The public may be placing too much trust in software and hardware developers to insure the security of our most sensitive transactions. Currently, the NSA has a trove of thousands of such vulnerabilities that can be used to breach some of the world’s most sensitive computers, according to a person briefed on the matter.204
Since 2010, the NSA has used data it gathered to map some Americans’ social connections to identify their associates, their locations, their travel companions and other personal information. The NSA was authorized to conduct “large-scale graph analysis on very large sets of communications metadata without having to check foreignness,” according to an NSA memorandum reported in the New York Times. The agency reportedly used material from GPS coordinates, along with Facebook and other social media profiles in their analysis.205
The “New” NSA
President Barack Obama, who initially defended the National Security Agency’s surveillance and data collection programs, branding them a “modest encroachment” on privacy for the good of national defense, has since endorsed a plan to change the NSA’s data collection.
The general idea is to end the government storage of phone metadata by transferring that storage to private phone companies. Under the administration’s proposal, the government must obtain a judge’s approval before accessing phone records, though exceptions could be made in cases of national security emergencies. The NSA’s database includes phone numbers that are called and the duration of those calls, but does not include the content of phone calls. NSA analysts will have to get a court order to obtain information from phone company databases except in cases where NSA officials can authorize searches on their own so long as they have a “reasonably articulated suspicion” that a particular number is involved in terrorist activities.206
The NSA will still have broad authority to intercept email and other Internet communications overseas, which often involve Americans who communicate with foreigners or are traveling overseas. When Americans’ communications are intercepted, the NSA is allowed to keep that information if it is relevant to a terrorism investigation or other foreign intelligence purpose, but is required to “minimize” how that information gets shared with other government agencies. 207
NSA opponents say that the new proposal is only designed to placate the American people and really doesn’t stop the NSA from collecting what they want. Just because phone records will now be stored “off site” doesn’t mean the NSA won’t have ready access to them when they feel a need to sift through conversations.
Reacting to reports that the NSA knew about encryption vulnerabilities like Heartbleed, President Barack Obama convened a panel to review surveillance activities and suggest reforms. Among the dozens of changes put forward was a recommendation that the NSA quickly move to fix software flaws rather than exploit them and that they be used only in “rare instances” and for short periods of time.208
What Can You Do?
To educate the public, the ACLU has launched a NSA Document website that lists all the documents made public since June 2013. They state, “We have made all of the documents text-searchable to allow users to investigate particular key words or phrases. Alternatively, the filter function allows users to sort based on the type of surveillance involved, the specific legal authorities implicated, the purpose of the surveillance, or the source of the disclosure. The fact is that most of the documents contained in this database should have never been secret in the first place. Now, with newfound access to these records, we can educate ourselves about the true nature and scope of government surveillance in its many forms. This database will serve as a critical tool with which we will hold our government accountable.”209
Responding to news reports that the National Security Agency may be monitoring more online activity than was previously believed, Microsoft launched what they are calling a comprehensive engineering effort to enhance encryption on communications via tools like its e-mail service Outlook, productivity suite Office 365, SkyDrive and Windows Azure. The company said it is rolling out three new features: 1) Expanded encryption across Microsoft services, 2) Reinforced legal protections for customer data and 3) Enhanced transparency designed to show customers that Microsoft products don’t have “back doors” that make government surveillance easier.210
Other software companies like Google and Yahoo! are also tightening up their encryption of users’ data. Mark Zuckenberg, CEO of Facebook, alleged that the National Security Agency went “way over the line” by hiding its surveillance programs from the American people.211
The debate goes on. The group of people who think the NSA are the “thought police” claim the government’s efforts to intensify its surveillance through backdoors, weak encryption and other intelligence-gathering tools are threats to Internet security. The group that defends the NSA, including the U.S. Intelligence chiefs, has said the country’s ability to spot terrorist threats and understand the intent of hostile leaders would be vastly diminished if the practice of monitoring emails and the exploitation of vulnerabilities were prohibited. And the group that doesn’t care because they feel they won’t be monitored still remains in the majority.
No matter which side ultimately prevails, it remains a fact that the NSA has contradictory roles: the defensive role to protect U.S. computer networks from any attack, and the offensive role of searching for and utilizing vulnerabilities to monitor terrorist and hacker activities throughout the world. As stated previously, the NSA remains firm in their belief that in order to protect America, its citizens must be willing to give up a certain amount of personal privacy.

