|
|
Introduction |
If you feel frustrated about your personal data being misused, hacked or compromised, you are in the majority of Americans. Hacking and the public’s concern about their privacy are becoming so commonplace that hacking events no longer warrant a headline in a newspaper but are buried in the Business section or on a blog that most people don’t see. Consider these stories, each concerning a different segment of the population, and how their data is being exploited:
EBay revealed that a cyber-attack carried out months ago has compromised customer data, and the company urged 145 million users of its online commerce platform to change their passwords after hackers stole email addresses, encrypted passwords, birth dates, mailing addresses and other information. 1
Schools routinely transfer large quantities of student personal data, including transcript information, homework essays, lunchroom purchases and even student weight, to third party providers. School boards are considering limiting access to yearbooks and student directories after revelations that data aggregators are using student data for marketing purposes.2
Farmers are serving notice in Washington that the federal government might need to become involved in yet another debate over electronic security and privacy issues because of the amount data sensors are collecting; sensors are being increasingly used to measure soil conditions, seeding rates, crop yields and many other variables that could be hacked or exploited by corporations or government agencies. Farmers worry that a hedge fund or large company with access to “real-time” yield big data from hundreds of combines at harvest time might be able to use that information to speculate in commodities markets long before the government issues crop-production estimates.3
Consider this, too: the vast majority of identities are not stolen intact but with sophisticated tools that can take a fact from one site, an online survey you took on another site and a purchase from third site, and little by little they can piece together your buying habits, your church and school affiliations, the names of your pets, the names of your family, your illnesses, your driving habits, the places you have vacationed and much, much more. This is not science fiction and this is not the future; this is what is happening to each and every one of us now—today. And although the vast majority of adults say they are concerned about providing personal information online, nearly a third say they have never used a privacy setting on their computer, never inquired about the charities to whom they donate their money, never worried about searching for medical information and never thought twice about giving their bank their social security number over the Internet.
How many of these online activities you have personally preformed?
- Posted your resume on LinkedIn?
- Opened an email from someone you didn’t know?
- Kept in touch with your friends on Twitter?
- Told a site to “Remember Me” so you didn’t have to use your password?
- Checked the Dow or other stock market reports?
- Posted your vacation destination on Facebook?
- Download an app on your Smartphone?
- Used a family member’s name as a password?
- Checked out an article in an online newspaper?
- Clicked on an ad that popped up while browsing another site?
Numbers 3, 5 and 9 are activities that are relatively harmless, but the rest are susceptible to online tracking and even fraud. Every time you go online, you need to ask yourself, “If someone is monitoring my activity, am I disclosing something I don’t want that person to know?”
Okay, you say you are extremely careful to the point where you change your password every two weeks, never pay bills online, don’t post on Facebook and won’t ever use an ATM. Think that will keep you safe? Don’t bet on it. Much of the information about you is in public records; here is some of the “sensitive” information accessible by anyone:
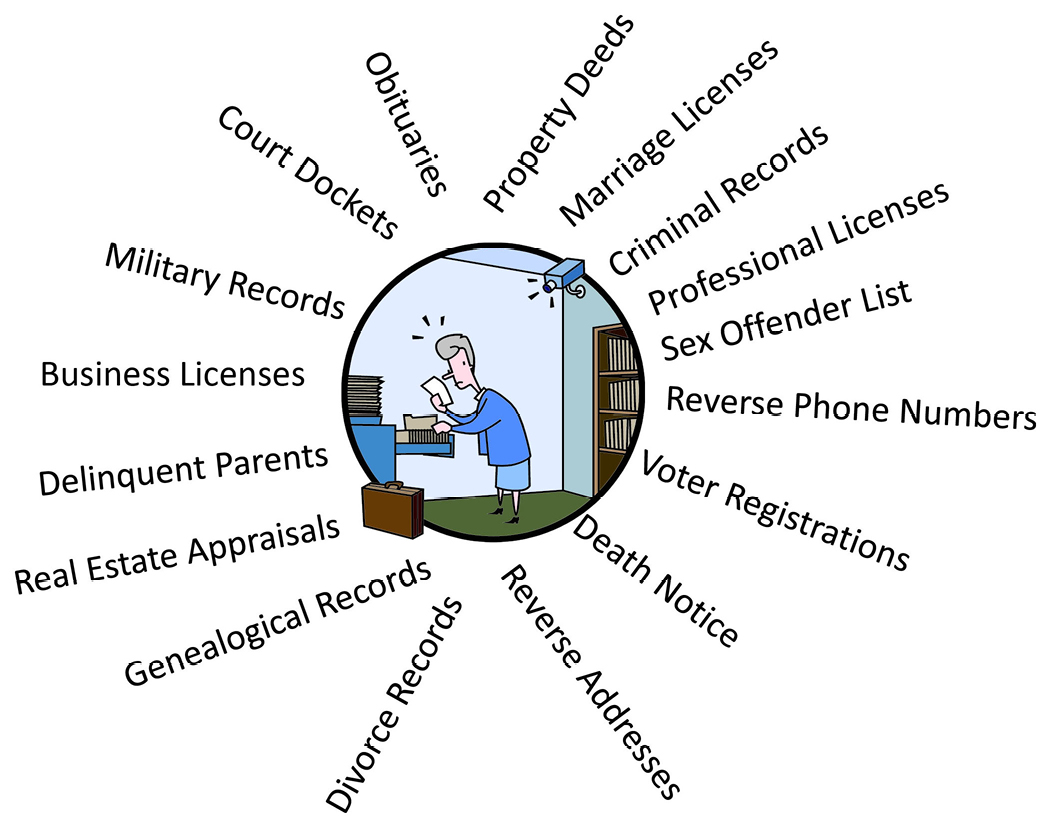
The Data Available in Public Records
As you see, a skilled data broker can amass a lot of information without even breaking into your computer, and a hacker can learn a lot more by accessing your personal online files. Companies are spending millions of dollars yearly to combat hackers and fight off cyber-attacks. JP Morgan Chase spends about $200 million a year to protect its data and expects that figure to climb 20 to 40 percent a year for the next several years.4 Don’t you think it’s about time you thought about protecting your own personal data?
This book reveals the ways in which your identity and personal data have been stolen by various sources. Rather than worrying about the NSA having your phone calls and emails, worry more about the insidious data brokers that are collecting information about you every time you log on to your laptop, use your cell phone, access an app or use your GPS.
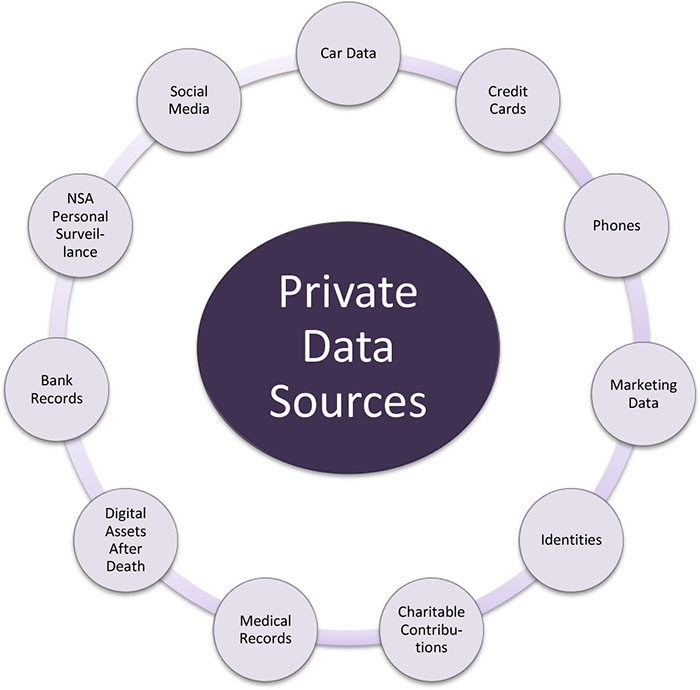
What Data Can Be Compromised?
But more than warning you, we give ways in which you can limit the amount of personal data that is being snatched and then divulged to whomever has a few dollars to buy it. Can you completely cut off the flow of information about yourself? The answer is no, not completely. There is too much data out there already and increasingly sophisticated ways to obtain bits and pieces. But knowing how it is collected gives you the power to limit the information on the sites over which you have control.
One last caveat: laws and regulations are changing rapidly as people become more aware of the assault on personal privacy. While we have used the latest information as of the writing of this book, we caution that you should check your local, state and federal regulations along with your service agreements to make sure you are kept up to date on changes to existing rules and policies.

