|
|
Chapter 4 |
Epsilon is the leading source of marketing data. We have information on more than 250 million consumers and 120 million business contacts, and we specialize in providing marketers with the clearest 360-degree view of their customer’s lifestyles, attitudes and behaviors. It’s this information that gives you the insight and the know-how you need for better campaign performance.60
Tracking Purchases
The Wall Street Journal conducted a study that found that the nation’s 50 top websites installed, on average, 64 pieces of tracking technology onto the computers of visitors, usually with no warning. A dozen sites each installed more than a hundred (the nonprofit Wikipedia installed none). Tracking isn’t new, but the technology is growing so powerful and ubiquitous that even some of America’s biggest sites say they were unaware, until informed by the Journal, that they were installing intrusive files on visitors’ computers. Tracking companies sometimes hide their files within free software offered to websites or hide them within other tracking files or advertisements. When this happens, websites aren’t always aware that they’re installing the files on visitors’ computers. Tracking technology is getting smarter and more intrusive; new tools scan in real time what people are doing on a Web page, then instantly assess location, income, shopping interests and even medical conditions. Some tools surreptitiously re-spawn themselves even after users try to delete them.61
United States businesses have more data stored per company than the U.S. Library of Congress. There is a lot of information out there about every one of us; it is sold on a daily basis to marketing firms so that big businesses can come up with relentless and targeted advertising campaigns. If you buy a bedspread from J.C. Penney with your credit card, you can probably expect a flood of mail order catalogs from places such as The Company Store, Sears and Bed Bath & Beyond in the next few months.
The typical information brokers sell to marketing agencies are names, addresses, contact information, age, race, occupation and education level. They also collect and sell lists of people who are experiencing life events such as getting married, having a baby, buying a home or getting divorced.
They also have data about many of the purchases you make or the hobbies you pursue, the places you travel (and how often) and the type of car you bought last year.
Where are they getting all this info? The stores where you shop sell it to them. Datalogix, for instance, which collects information from store loyalty cards, says it has information on more than $1 trillion in consumer spending “across 1400+ leading brands.” It doesn’t say which ones because data companies usually refuse to say exactly which companies sell them information, citing competitive reasons. And retailers also don’t make it easy for you to find out if they’re selling your information.62
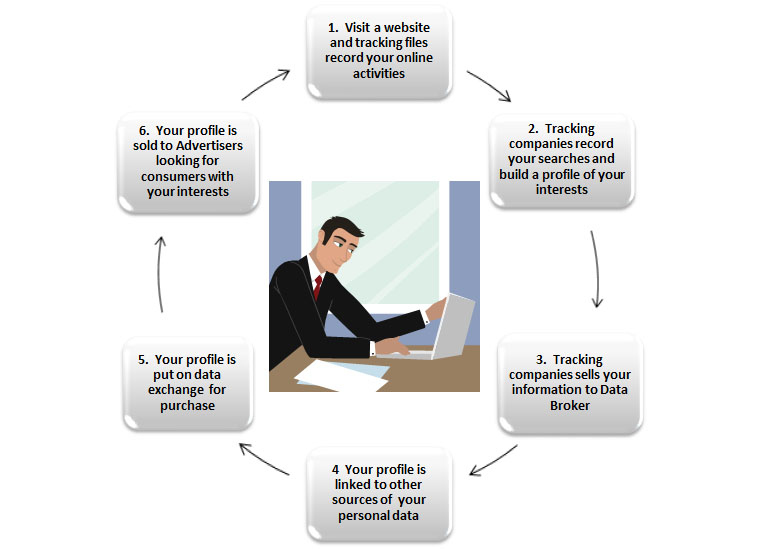
Stealing Your Online Data
By now, many people are used to the way advertisements follow them around the Web—how the chair they clicked on here keeps popping up there. Annoying, but advertisers have come to regard this technique, called retargeting, as a very effective way of reaching their target audience.
Online marketing companies are already focusing on the next generation of targeted advertising—one that collects and analyzes vast streams of data from social media, credit card histories and Web habits. That information helps to create ads that are increasingly personalized and nuanced. Often, these ads are shown to consumers in real time based on what they do moment to moment. The amount of information available to advertisers has increased exponentially, from credit card and telecommunications companies and even from brands.
Instead of using old retargeting methods, such as showing someone an ad for a car that they just viewed online, brands are using new technologies to help them decide, often in advance, whether a consumer should be shown an ad, for example, a luxury car or an inexpensive car, or any car at all. In milliseconds, fast technologies can determine whether a person is in the market for a new car or has bought a car recently, yielding different types of ads. One ad could focus on a new vehicle that a company is trying to promote to energy-conscious drivers, while another might focus on accessories for the car. 63
A value is assigned to a consumer, and how much the advertiser is willing to spend on that consumer can be based on myriad factors including whether and how that consumer uses social media, recent purchases and Web sites visited. If a consumer has a 20 percent chance of making a $100 purchase, that consumer could be valued at a certain level; conversely, if that person’s dollar value is lower than the cost of marketing, an advertiser may opt not to show an ad to that person.

How Retailers Can Use Your Personal Information to “Upsell”
Grouping users by type is not new, but with increasingly large sets of data, the process is increasing in precision and gives brands a “feedback loop” with consumers so they know which ads are most effective with which consumers. Social media companies work with advertisers to help segment users based on what they are posting. The information gathered from comments posted about a brand or product on online retailers’ websites, as well as comments gathered from social media, has created real-time focus groups and is an easy way for companies to compare their brand to those of their competitors.
The rewards for being in the data brokerage industry are too great. It’s obvious that companies are hungry to use data to inform their marketing campaigns. Data brokerage is booming. That’s why Facebook keeps tightening alliances with three of the largest data brokers in the U.S., Datalogix, Acxiom, and Epsilon. It’s more the fact that we aren’t told when and where our data is collected, and that most people don’t realize the extreme reach of these companies, that’s so troubling.64
For example, Proclivity Media developed a proprietary technology based on the premise that every person has a constantly changing economic value in relation to any item in the world which could be computed in real time to optimize sales for a broad array of industries such as commerce, travel, education, non-profit and politics. The Proclivity Media technology platform drives sales for companies by rapidly ingesting and scoring an ever-increasing volume of data about their products and consumers to predict what consumers are likely to buy, along with data on when and what they are willing to spend, to deliver the most relevant messages.65
How do consumers feel about the trend to more specific marketing? A December 2013 survey of US digital shoppers, conducted by Harris Interactive, found that the majority of recipients of emails containing personalization drawn from previous shopping behaviors and preferences would be more likely to increase their purchases as a result. In fact, 81 percent of respondents said they were at least somewhat likely to make additional purchases, either online or in store, as a result of targeted emails. Part of this willingness is likely due to the fact that email recipients have already agreed to opt in to receiving messages, making them more accepting of emails with increased relevancy.66
A Wall Street Journal investigation into online privacy has found that the analytical skill of data handlers is transforming the Internet into a place where people are becoming anonymous in name only. The findings offer an early glimpse of a new, personalized Internet where sites have the ability to adjust many things—look, content, prices—based on the kind of person they think you are.67
Personalized ads, which deliver sophisticated, individualized mobile messages based on a user’s exact location, have also arrived in a big way. In December 2013, Apple activated iBeacon, allowing it to track shoppers (with their permission) in all 254 of its retail locations in the U.S. and send them in-store notifications about upcoming deals and events.
The NFL is following Apple’s lead; the same technology (via transmitters) welcomed fans at both Times Square and the 2014 Super Bowl. Once users have downloaded the brand’s app and given permission to receive alerts, the NFL can send them location-based messages including directions to a stadium and nearby promotional offers. They can also use algorithms and regression models to figure out behaviors that indicate if a season ticket holder may not renew.68
Digital marketing has few boundaries, and encompasses devices such as Smartphones, tablets, laptops, game consoles, televisions, digital billboards, social media, search engines, videos and email. Companies are just scratching the surface on location-based marketing, which uses GPS technology to deliver content based on where a person is located. Are you in a store looking at shoes? Are you buying tickets for a play? Are you eating at your favorite restaurant? Advertisers will send you a message based on where you are and what you are doing at that moment. There are also users who are making their interests known on apps such as Flipboard, Pulse and Foodspotting, which then feed these preferences to merchants and businesses. Data is filtered and customized for each individual, rather than grouping like-minded individuals into segments of the population. Now you can be identified individually—talk about a lack of privacy!
If this seems like the future, then the future has arrived. Transmitters are being installed in several hundred stores and public areas in the next few months, including at two dozen Major League Baseball stadiums and a large number of Macy’s and American Eagle Outfitters stores.69
Popular sites are trying to cash in on your social connections to send advertisements to you. Technology firms like Google, Instagram, Facebook, Pinterest, Twitter and others are increasingly deploying user’s data to boost ads.
Pitching a product with a friend’s endorsement makes for powerful ads, and the research firm, eMarketer, estimated that the so-called social business advertisements were worth $9.5 billion in U.S. sales in 2013.
This can be a risky business, however. In August, 2013, a judge approved a settlement with Facebook on a class action suit over employing users in ads without their permission. Still, Facebook continues to use ‘Likes’ and photos in ads targeted to friends. It still is not known if this practice of using endorsements by friends may alienate users and open other companies to privacy lawsuits, but you can be sure a lot of them will try it to gain more advertising dollars.
Ninety-one percent of adult mobile phone owners have their devices within arm’s reach 24/7, and location-based marketing could massively exploit this fact. Furthermore, tools such as Google Wallet are being perfected, which enables people to buy with their credit card right from their Smartphone. The NFC (Near Field Communication) technology in Google Wallet, which allows users to make secure payments, is only set to get better and more popular. Businesses are sure to capitalize on this.70
Advertisers have found that videos can convey a more powerful message than text alone and can instantly alter a person’s behavior. Were you getting hungry and thinking about a Big Mac? Suppose at lunchtime you got a video message on your phone that Burger King was offering a Whopper for only $1 with a picture of the burger. Would you go there instead?
Do you feel manipulated yet?
Your Credit Score
Where have you shopped lately? Been looking at used cars and second-hand furniture? Have you been to several casinos or a bail-bond service? What you buy and where you shop may affect your credit score. As credit card companies continue to tighten their lending standards on card users, some are using purchased data—gleaned from millions of card transactions processed daily—to weed out those who may or may not be good credit risks. Congress and federal regulators will be probing the extent to which credit card issuers have used information about where a person shops or what they buy as reasons to lower credit limits or increase interest rates.71 Thankfully, some congressmen are arguing that what a person spends or where they shop has little bearing on whether they can afford to pay back their credit card so don’t abandon those consignment shops yet.
Behavioral modeling, data mining, and psychographic behavior analysis are all ways of searching internal credit card issuer databases for customer spending trends and other patterns. Banks and other financial institutions have been analyzing data and purchases since the beginning of credit cards for several reasons such as:
- Marketing. Issuers use past purchasing patterns as a basis for offering additional products. Someone purchasing camping supplies with a credit card may get offers from wilderness camping cabins, for example.
- Law enforcement. Law enforcement agencies can subpoena records from both the credit card issuer and the merchant to find out the time, date, and place of a credit card purchase—information that may be helpful in determining the last known location of a suspect or a crime victim. The Department of Homeland Security also tracks terrorist activity by monitoring certain purchases.
- Fraud detection. Credit card companies monitor cards to detect unusual buying, which might indicate a lost or stolen credit card. Did you spend $300 at Wal-Mart when you have never shopped there before? Did you buy gas in Georgia when you live in Illinois?
- Risk management. Banks know that card users who continually go over their credit limits, use credit card offers of cash or charge large amounts of merchandise on a card may be at greater risk of not paying their bills or filing for bankruptcy.
Thinking of signing up for a credit monitoring service? According to MSN Money, many of these companies tout “free” credit scores, and some even try to pretend they’re the official, federally mandated site that offers free credit reports (the real site is AnnualCreditReport.com). Liz Weston of MSN Money says, “way too many readers tell me they had no idea they were signing up for credit monitoring until the charges started appearing on their bills.”72 If a credit-monitoring company gives you free scores, here’s the scoop:
- They’re probably not the FICO scores that most lenders use, or you’re signing up for credit monitoring that isn’t free.
- You don’t have to spend money to monitor your credit score. You’d typically pay $240 a year for what you can get on your own for free. Use free access to your credit reports at AnnualCreditReport.com. You can get a report once a year from each of the three reporting systems: Experian, Equifax and Transunion. Look at a different one every four months to keep up with your credit score.
- Credit monitoring won’t stop bad guys from taking over your credit cards or establishing new accounts in your name. At best, it will give you an early warning that the damage has been done. The “insurance” policies many monitoring companies offer are essentially worthless since most people who are victimized face few, if any, out-of-pocket expenses.73
What Can You Do?
The things you can do are pretty much the same as we will be recommending for avoiding identity theft. You should be extremely careful of what you carry in your wallet and don’t carry your social security or Medicare card (which has your social security number on it). When disposing of financial documents, shred them. Don’t post too much personal information on social networking sites—especially your date of birth, children’s names, first school attended, or your mother’s maiden name since those are often used in the challenge questions employed to confirm your identity. Don’t answer questions about your financial status or other personal information over the phone, no matter who they say they are. When you receive your bank or credit card statement, review it for errors and charges you did not make.
If you are worried about your account being compromised, you can request a free 90-day fraud alert on your credit reports, which alerts a potential lender to the possibility that your account may have been hacked. Another option is a credit report freeze. This will lock your credit, and if someone applies for credit in your name, the lender won’t be able to see your data to approve the application. Credit report freezes may cost you $15 unless you are already a victim of identity theft, in which case you may be able to get one for free.
You can also submit a report about the situation directly to the FTC by completing an Identity Theft Affidavit. First, you will need to file a police report. Then, submit the police report along with the Identity Theft Affidavit to the FTC’s Complaint Assistant. After completing the report, you will be given a complaint reference number that you can use to update information at any time.
If your card is stolen or your account compromised, dealing with the problem is usually as simple as reporting it to the creditor. The fraudulent charges are erased and a new credit card with a new account number is issued. You are not held liable for any charges you did not personally make.
A critical thing to remember is that the credit card and other companies start sharing your data after 30 days, so it is up to you to notify them within that time period if you do not want them to share any non-essential data. Here is what you can do.
- For Capital One, MasterCard, Visa and other credit card companies, you can write or call them and tell them you want to limit sharing of your information. You may not be able to limit all your information based on the agreement you signed.
- For wireless companies such as Verizon or AT&T, you can notify them via their websites or by calling an 800 number they provide and following their recorded directions. However, if you have a family plan or a multi-line account, you must indicate your choice for each line. If you add a line, you will need to update your privacy choices.
- Even if you miss notifying a financial or service provider within 30 days, you can still notify them to stop sharing your data. But by then, it may be too late to prevent some of the information from going to other sites. Your providers are not sitting around waiting for you to make up your mind; they want to sell your data as soon as possible.
Identity thieves are sneaky, so you need to be sneaky, too. There are a few simple things you can do to protect your credit card in case it falls into the wrong hands. Sign your credit card with a Sharpie so your signature can’t be erased and written over. Some people don’t sign it at all but write “See ID” in the signature space. Consultant Sarah Browne of Carmel, California, had all but one credit card stolen from a hotel room. The card that was spared still had the “Please Activate” sticker on it. Though Browne had activated the card, she forgot to remove the sticker. “The thieves must have known that you have to activate a new card from the phone number listed with the credit card company, so they didn’t bother with it,” she said, and since then, she leaves the activation stickers on all of her cards. Indeed, when a thief struck a second time at a public function, Browne’s stickered cards were again left untouched.74
In-Store and Online Hacking
It is still unclear how criminals were able to break into many retailers’ systems. Target confirmed in December 2013 that criminals had access to its systems by using stolen credentials from a vendor but did not name the vendor. Target tried to minimize the damage by giving its customers free credit reports for a year and a discount of 10 percent over a pre-Christmas weekend, but there are reports that Target has lost many loyal customers. Others swore to only use cash when shopping there in the future.
In another hacking incident, Yahoo! said that criminals had gained access to Yahoo! Mail accounts using user names and passwords compromised in a third-party breach.
In the latest in a spate of online attacks affecting American businesses, White Lodging, which manages hotel franchises for chains like Marriott, Hilton and Starwood Hotels, is investigating a potential security breach involving customers’ payment information. A spokesman for the Secret Service could not immediately say whether the agency was investigating the breach of White Lodging data. The Secret Service is conducting separate inquiries into the breaches at Target, Neiman Marcus and Michaels.75
Before a transaction can be authorized, credit card data is momentarily decrypted and stored in memory. Thieves have been known to build RAM-scraping malware which scrapes that unencrypted data from memory and steal it. The thefts reignited the push for more secure credit and debit cards, similar to those used in Europe and elsewhere. The result is the EMV chips described in the previous chapter about credit cards. Congress is also calling for tougher consumer protections.
Verizon released their 2013 “Data Breach Investigations Report,” which analyzed where the largest threats originate and what cyber-thieves are after when they attack networks. According to the report, a large percentage of these attackers are simply looking for a way to turn a profit, using stolen information on their own or selling it to other parties.
The majority of the attacks originating in the U.S. are financially motivated. A much smaller percentage of the attacks analyzed in the report were state-affiliated or perpetrated as an act of espionage. The Verizon investigation found that the majority of cyber-espionage attacks originated in East Asia or China.76
Verizon said that 75 percent of cyber-attacks were not targeted; companies were hit because criminals saw an opportunity to hack into their systems. The report supports this by saying 78 percent of intrusions required little to no special skills or resources. While these attacks could be deemed simplistic, companies need to protect themselves from data breach or loss, which could have expensive consequences.77
What Can You Do?
Is there any way to stop companies from collecting and sharing information about you?
Yes, but it will require a lot of work on your part to stop companies from collecting and sharing your information. Many data brokers offer consumers the chance to “opt out” of being included in their databases or at least from receiving advertising enabled by that company. But to actually opt-out effectively, you need to know about all the different data brokers and where to find their opt-outs. Most consumers, of course, don’t have that information. In their annual privacy report, the FTC suggested that data brokers should create a centralized website that would make it easier for consumers to learn about the existence of these companies and their rights regarding the data they collect.78
As with many of the invasions of your privacy, there is little you can do except quit posting all that information about yourself and your family on social media sites. Not only malicious hackers, but “friendly” marketing people are downloading your data and using it in selected ways to manipulate you or your finances. Selling you a product you don’t need is not as bad as breaking into your bank account, but both cost you money, and did you really need another dog bed for Fido even if it was a cute tartan?
When you’re checking out at a store and a cashier asks you for your ZIP code, don’t give it to them. The store isn’t just getting that single piece of information. Acxiom and other data companies offer services that allow stores to use your ZIP code and the name on your credit card to pinpoint your home address — without asking you for it directly.79
The FTC has released a detailed report calling for Congress to act to give consumers control over the data that companies and data brokers gather and sell. Meanwhile there are online companies out there to help individuals delete these records—but none can guarantee that all data brokers will comply. Regulators and some Congressmen have been taking a closer look at this industry and are beginning to push the companies to give consumers more information and control over what happens to their data. Companies could voluntarily do this rather than have laws enacted which might be more stringent. The prominent data broker Acxiom recently launched aboutthedata.com, a site that allows you to review some of the information the company has connected to your name—and, potentially, edit and update it as well. For a lasting solution, we need legislation, so contact your state and federal representatives.
Don’t expect too much from Congress, however. Marketing companies will probably be excluded from any legislation aimed at financial and medical records. The thinking goes something like this: “What is the worst that could happen? You receive a piece of mail or an advertisement on your Smartphone and all you have to do is get rid of it. It’s not like someone stole your identification or your tax records.” Yes, congressmen, it’s not the end of the world, just another life-hassle for the consumer.

