7
Using Advisor
In the previous chapter, we looked at securing the available storage services in Azure. We looked at how the shared responsibility model for public cloud platform providers requires the customer to have implemented the appropriate solutions and controls to ensure their storage is secure and protected.
This previous chapter concluded part one of this cookbook, where we looked at Azure’s security features and capabilities as a first-party solution. We covered recipes that provided security for identities, networks, remote access, VMs, databases, and storage.
This first chapter in Part 2 of the cookbook, which covers Azure Security Tools, looks at the first of these tools, Advisor.
In this chapter, you will learn how to secure and protect Azure environments using the security aspects of the Advisor recommendations engine. Advisor can also provide recommendations for reliability, performance, cost, and operational excellence, although these are beyond the scope of this book.
This section will break down the chapter into sections on security recommendations and secure scores, how to configure security recommendations, configure alerts, and perform remediation of recommendations.
By the end of this chapter, you will have gone through the following recipes and gained the skills to make the most effective use of Advisor:
- Reviewing the security recommendations
- Implementing the security recommendations
Technical requirements
For this chapter, it is already assumed that you have an Azure AD tenancy and an Azure subscription from completing the recipes in previous chapters of this cookbook. If you skipped straight to this section, the information to create a new Azure AD tenancy and an Azure subscription for these recipes is included in the following list of requirements.
For this chapter, the following are required:
- A device with a browser, such as Edge or Chrome, to access the Azure portal at https://portal.azure.com.
- An Azure AD tenancy and Azure subscription; you may use existing ones or sign up for free: https://azure.microsoft.com/en-us/free.
- An Owner role for the Azure subscription.
- The following access permissions: https://learn.microsoft.com/en-us/azure/advisor/permissions.
Reviewing the security recommendations
With the eagerness and excitement of moving workloads onto a cloud platform, unfortunately, things can get overlooked, and often governance and control can take a back seat. This can lead to less than optimal deployment, configuration, and operation practices and use of resources, resulting in a security breach and negatively impacting trust in adopting a cloud platform’s capabilities. We must not forget the shared responsibility we have, along with the cloud platform providers.
This recipe will teach you how to review the security recommendations provided by Advisor to improve your security posture and workload protection.
Getting ready
This recipe requires the following:
- A device with a browser, such as Edge or Chrome, to access the Azure portal at https://portal.azure.com
- Access to an Azure subscription, where you have access to the Owner role for the Azure subscription
How to do it…
This task consists of the following tasks:
- Accessing Advisor
- Reviewing Advisor’s recommendations
Task – accessing Advisor
- Sign in to the Azure portal at https://portal.azure.com.
- In the search bar, type advisor; click on Advisor from the list of services shown:

Figure 7.1 – Searching for Advisor
- When Advisor opens, it will load the Advisor score page.
This task of accessing Advisor in the Azure portal is complete. In the next task, we will review the security recommendations provided through Advisor.
Task – reviewing Advisor’s recommendations
- From the Advisor score page, you will see your Advisor score, reflecting Microsoft’s best practices. You will also see your Score by category information; the Security category is of interest for this recipe.
- There are several Advisor category tiles on the at-a-glance view of your Microsoft best practices posture; our focus is the Security tile here:
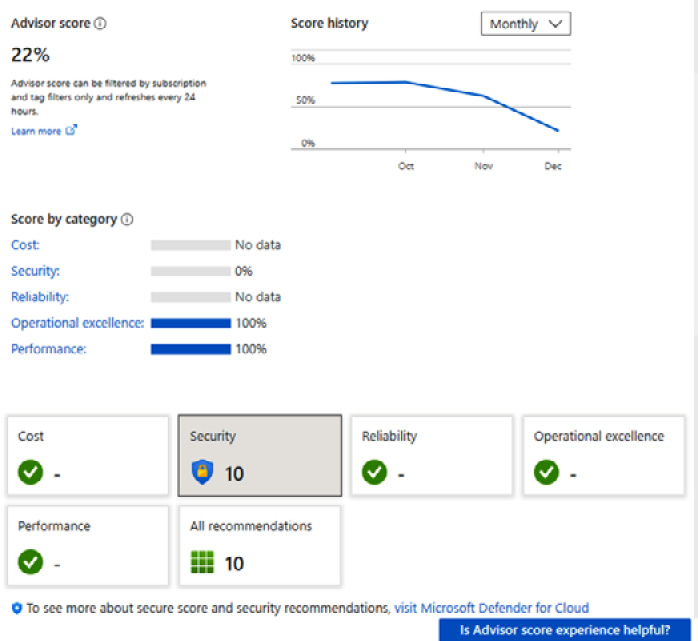
Figure 7.2 – Recommendations dashboard
In the preceding figure, a category score of 100% indicates that all Advisor-assessed resources follow Advisor’s best practices; a category score of 0% indicates that none of the Advisor-assessed resources follow the Advisor’s best practices. The Security category tile shows that there are 10 recommendations that we are not following.
- If you click on the Security tile, you will see that it lists these recommendations.
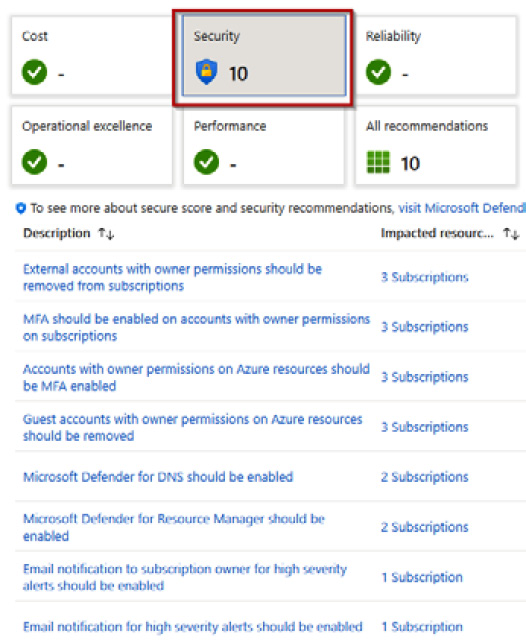
Figure 7.3 – Recommendations at a glance
- If we click on the first listed recommendation, we will be taken to a blade with further information.

Figure 7.4 – Recommendation detail
- You can also view the Security recommendations in the Recommendations section in the left-hand menu bar:
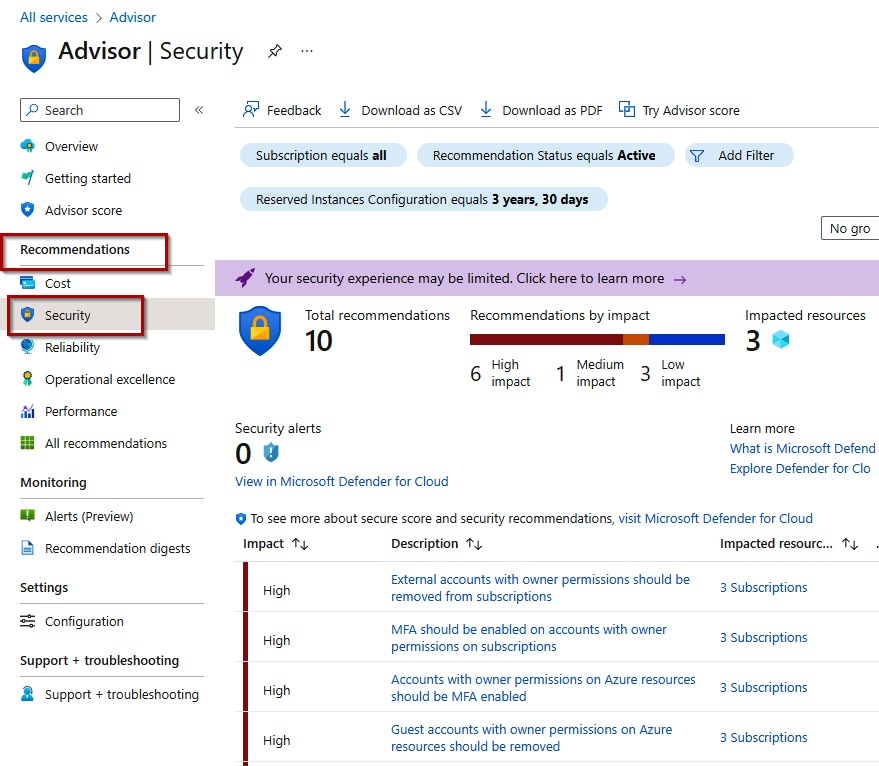
Figure 7.5 – Security blade
- In the Security blade, you can view Total recommendations, Recommendations by impact, Impacted resources, Security alerts, and the listed recommendations:

Figure 7.6 – The Security blade
This task of reviewing the security recommendations made available through Advisor is complete.
How it works…
For this recipe, look at how to access the security recommendations available through Advisor to improve your security posture and workload protection.
See also
Should you require further information, you can refer to the following Microsoft Learn articles:
- Advisor Microsoft landing page: https://azure.microsoft.com/en-us/products/advisor/
- Advisor documentation: https://learn.microsoft.com/en-gb/azure/advisor/
- Permissions in Azure Advisor: https://learn.microsoft.com/en-us/azure/advisor/permissions
- Microsoft Learn training – Get started with Advisor: https://learn.microsoft.com/en-us/training/modules/get-started-azure-advisor/
- Security recommendations - a reference guide: https://learn.microsoft.com/en-gb/azure/defender-for-cloud/recommendations-reference
Implementing the security recommendations
This recipe will teach you how to apply the security recommendations provided by Advisor to improve your security posture and workload protection.
Getting ready
This recipe requires the following:
- A device with a browser, such as Edge or Chrome, to access the Azure portal at https://portal.azure.com
- Access to an Azure subscription, where you have access to the Owner role for the Azure subscription
How to do it…
This task consists of the following tasks:
- Implementing Advisor’s recommendations
Task – implementing Advisor’s recommendations
- Sign in to the Azure portal at https://portal.azure.com.
- In the search bar, type advisor; click on Advisor from the list of services shown.

Figure 7.7 – Searching for Advisor
- When Advisor opens, it will load the Advisor score page.
- On the Advisor score page, click on the Security category tile; this will load the recommendations and present them in a list on this page.

Figure 7.8 – Selecting the Security category tile
- Select a recommendation from the list to remediate; in this scenario, we will select the Microsoft Defender for Resource Manager should be enabled recommendation, as represented by the following figure:

Figure 7.9 – Security recommendation
- On the Recommendations details page, you will see a description of the recommendation, so the recommended best practice. You will also see a Remediation steps section; this section can be clicked on and expanded so that you can read the full information on the remediation steps available for this recommendation:
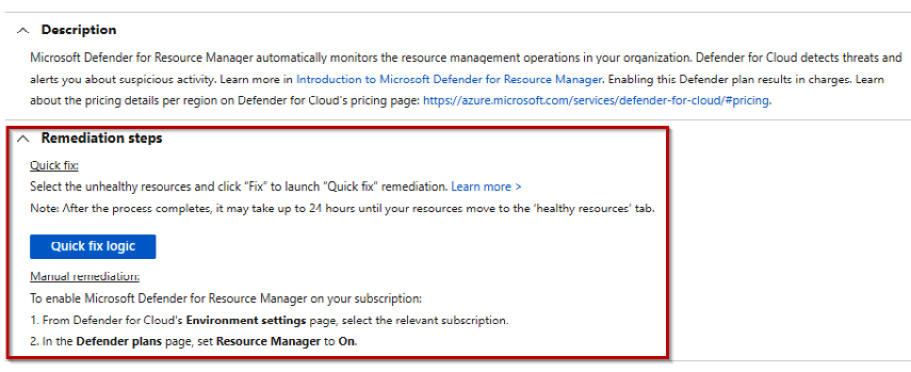
Figure 7.10 – Recommendation remediation steps
- If a quick fix is available, then a Quick fix logic button will be visible, which you can click to remediate the recommendation. The Manual remediation instructions to follow will also be provided.
- When you click on the Quick fix logic button, an Automatic remediation script content blade will pop up, showing the deployment template used to implement the recommendation.

Figure 7.11 – Recommendation script content
- In the Affected resources section, expand and check each Subscription item you would like to apply this recommendation to, and then click on Fix.
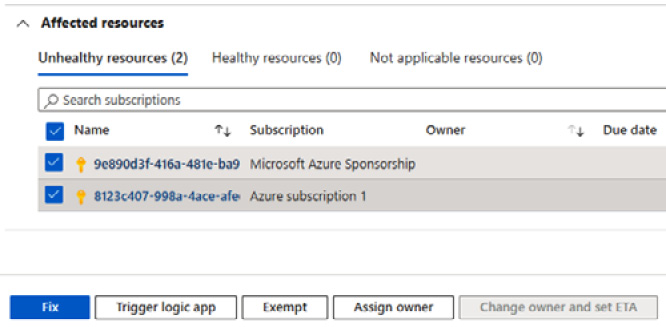
Figure 7.12 – Affected resources
- On the Fixing resources pop-up blade, review the information and then click on Fix 2 resources, as per our scenario, represented in the following figure:

Figure 7.13 – Fixing resources
- You will be notified that the remediation was successful.
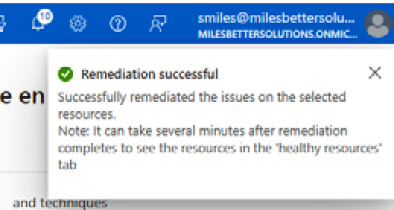
Figure 7.14 – Remediation successful
How it works…
For this recipe, we looked at remediation according to the security recommendations available through Advisor to improve your security posture and workload protection.
See also
- Advisor Microsoft landing page: https://azure.microsoft.com/en-us/products/advisor/
- Advisor documentation: https://learn.microsoft.com/en-gb/azure/advisor/
- Microsoft Learn training – Get started with Advisor: https://learn.microsoft.com/en-us/training/modules/get-started-azure-advisor/
