Information Security Management
Another of the key warranty aspects of a service is security, and it is this aspect that we will discuss in this section. A service that is insecure will not deliver value to the customer and indeed may not be used by them at all.
ITIL defines information security as “the management process within the corporate governance framework, which provides the strategic direction for security activities and ensures objectives are achieved.”
Central to information security management (ISM) is the identification and mitigation of risks to the security of the organization’s information. The ISM process ensures that all security aspects are considered and managed throughout the service lifecycle.

Organizations operate under an overall corporate governance framework, and information security management forms part of this framework. As with wide governance, ISM provides guidance as to what is required, ensuring risks are managed and the objectives of the organization are achieved.
Purpose, Objectives, and Scope of Information Security Management
The purpose of the information security management process is to ensure that IT security meets the requirements of the overall business security. It is responsible for making sure that the information, data, and IT services used by the organization are protected to the appropriate level. Information must be kept confidential, that is, made available only to those with the appropriate access rights. The data must be protected from any corruption or unauthorized alteration so that its integrity is assured. Finally, the information must be available to authorized users when required through robust systems that are resistant to failure. By ensuring these aspects—confidentiality, integrity, and availability—ISM enables the business to meet its objectives.
Where information is transmitted between partner organizations, ISM must ensure that this exchange is protected so that the information can be trusted.
ITIL defines the objective of information security management (ISM) as “to protect the interests of those relying on information, and the systems and communications that deliver the information, from harm resulting from failures of confidentiality, integrity, and availability.”
The scope of ISM includes all aspects of information security that are important to the business. It is the responsibility of the business to define what requires protection and how strong this protection should be. Risks to security must be recognized, and appropriate countermeasures should be implemented. These may include physical (restricting access to secure areas through swipe cards) as well as technical aspects (password policies, use of biometrics, and so on). Information security is an integral part of corporate governance.
Producing an Information Security Policy
The information security management process is responsible for producing and maintaining an information security policy. This document should be made available to all IT staff, customers, and users. It is also part of ISM to ensure that the policy is being carried out, for example, by performing spot checks.
To produce such a policy, the IT security manager must have a thorough understanding of all security issues within the organization. This must include an understanding of the overall business security policy and requirements, its current and future plans, how these might impact security, and any risks to security (either business risks or IT risks), including how these risks are being managed). Any particular legal or regulatory requirements should also be included. For example, an organization that handles online credit-card payments will be subject to particular regulations to ensure that the transactions are adequately protected.
Information security management activities should be focused on and driven by an overall information security policy and a set of underpinning specific security policies. The information security policy should have the full support of top executive IT management and ideally the support and commitment of top executive business management. The policy should cover all areas of security and be appropriate to meet the needs of the business; specifically, it should include the following:
- Use and misuse of IT assets policy
- An access control policy
- A password control policy
- An email policy
- An Internet policy
- An antivirus policy
- An information classification policy
- A document classification policy
- A remote access policy
- A policy with regard to supplier access to IT service, information, and components
- A copyright infringement policy for electronic material
- An asset disposal policy
- A records retention policy
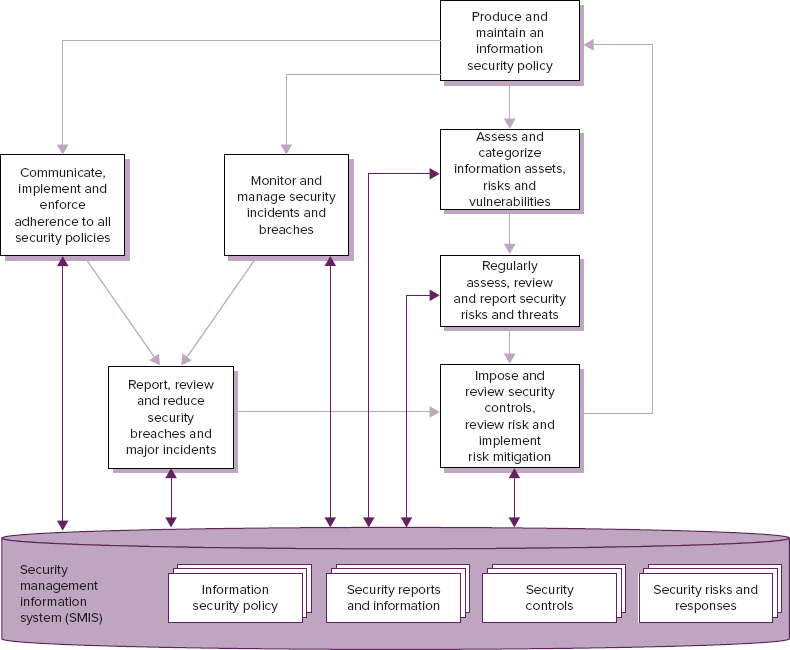
In most cases, these policies should be widely available to all customers and users, and their compliance should be referred to in all SLRs, SLAs, OLAs, underpinning contracts, and agreements. They are stored in the security management information system (SMIS), as shown in Figure 6.6. The SMIS forms part of the overall service knowledge management system (SKMS).
FIGURE 6.6 The information security management process
Based on Cabinet Office ITIL® material. Reproduced under license from the Cabinet Office.
Educating Staff About Security
The information security management process includes producing the information security policy and publicizing its contents. The process also involves working with the business to understand current and future needs in this area. Implementing appropriate protective measures and controls to manage the identified risks and ensuring that these measures are documented and maintained are ongoing aspects of this process.
The information security manager must ensure that controls are in place to manage the access to secure systems by third-party suppliers and ensure that faulty or obsolete hardware is not scrapped without removing the data held within it. Staff members must be made aware of their responsibilities with regard to protecting data (carrying data on unencrypted flash drives, sharing passwords, and so on); where a breach does occur, this should be used as an opportunity to reevaluate the existing policy for effectiveness.
For security to be effective, it must not be considered as an additional aspect but as integral to the design and operation of all services and across all ITSM processes. Security is an ongoing process; the information security manager should be constantly reviewing possible threats and taking the necessary steps to protect the organization’s data. More security breaches occur as a result of lack of awareness than by deliberate action. The information security manager must continually emphasize the importance of adhering to the policy and be proactively seeking to improve security and reduce risk.
The information security policies should be authorized by senior management as they form an important part of overall governance. These business managers should emphasize the importance of adhering to the policies and ensure that all staff members are aware of what the policies are. Publicizing the policies through presentations, notices, posters, and so on, will help get the message across. There should be no scope for a staff member to argue that they did not know what the policy was. Should deliberate flouting of the policies take place, it is essential that these are taken seriously, with appropriate disciplinary measures enacted.
The nature of security threats changes with new technology; many organizations now have policies on downloading music or access to Facebook that would not have been necessary a few years ago. It is essential that the security policies keep in step with the new threats. All security policies should therefore be formally reviewed—and when necessary revised—at least every 12 months.
