CHAPTER 1 Introduction
Overview
This chapter motivates the topic of information security and lays out the structure for the rest of the text. At the outset, we describe why information security is a useful area of study with the hope of getting you excited in the topic. We then provide a brief history of the subject, highlighting important developments that have led to the current state of the industry. Finally, we outline the procedures adopted by the industry to maintain information security. These procedures will be examined in detail in the rest of the book. At the end of this chapter, you should know:
- Why information security is an important topic for everyone today
- The important developments that led to the current state of the information security industry
- Key terms used in information security
- Broad outlines of the procedures used in the industry to maintain information security
Professional utility of information security knowledge
If you are reading this book as part of a college course, it is probably offered by a professional school – business, information, or engineering for example. These schools are expected to graduate students who can hit the ground running when they join the work force. Naturally, we expect that the question foremost on the minds of students in these college is – where are the jobs? What is the professional relevance of this subject? What is the demand for professionals in this subject? What drives organizations to hire graduates with skills in this subject? When hired, what are graduates in this subject typically expected to do? What competencies will help graduates meet or exceed these expectations of employers? Before you decide to spend any more time with this book or the subject of information security, we would like to take this topic head-on and address these issues.
Demand estimates
The standard source for employment estimates is the Bureau of Labor Statistics1 (BLS), a government agency that gathers employment statistics from extensive surveys of employers. BLS has created a taxonomy called the “standard occupational classification (SOC)” for all the major occupational categories. Information security analysts are given the SOC identifier 15-1122 (Figure 1.1). They fall under the major group of “Computer and mathematical occupations (15-0000).” Statistics for information security analysts is aggregated along with those for web developers and computer network architects and may be obtained from the BLS website.2 The total employment for this group in May 2010 was estimated to be 243,330, with a mean annual wage of $79,370.
Other sources for obtaining estimates of the demand for information security professionals are the professional certificate action organizations involved in the industry. One of the leading organizations is (ISC).2 Based on a survey of over 10,000 information security professionals around the globe, this organization estimated that there were approximately 2.28 million information security professionals worldwide in 2010, of who over 900,000 were in the Americas. This number was also estimated to be growing at over 13%.3 The average annual compensation was estimated at over $78,000. The wide difference in estimated employment between the two surveys could be attributed to a difference in the characteristics of the organizations sampled by the two surveys. It may however be noted that both surveys are quite consistent in their estimates of average annual compensation.
Demand drivers
A number of factors are driving the demand for information security professionals. Primary among these is the increasing criticality of information to individuals and organizations and the resulting increase in the amounts of information gathered by organizations and stored in computer systems for easy retrieval. Possession of a username and password combination could be more useful to a thief today than possession of a $100 bill. A successful attack at a bank or other commercial establishment could yield hundreds of thousands of vetted username and password combinations. The most motivated attackers are therefore increasingly targeting information stores rather than physical stores.
Even as information is becoming more valuable, unwittingly, users are also making it easier for attackers to obtain this valuable information. For example, most users use a small set of usernames and passwords wherever usernames and passwords are required. They also often prefer that their devices remember these usernames and passwords to save typing effort at websites. Now consider what happens if an attacker is able to lay their hands on a laptop, tablet, or other mobile device belonging to a user in possession of sensitive information. The attacker could easily get access to hundreds of thousands of records with minimal effort. With millions of knowledge workers leaving their workplaces with billions of mobile devices every day, organizations are compelled to act proactively to ensure that they do not appear on the front pages of newspapers and TV channels for losing customer information or other sensitive data.
The value of information described above is just one of the demand drivers for information security professionals. Other factors include dealing with application vulnerabilities, the constant stream of viruses and worms reaching organizations, regulations, customer expectations of privacy, and disgruntled employees.
The demand drivers for information security professionals have also been changing very rapidly. For example, until as recently as 2008, mobile devices such as smart phones and tablets were not common in companies. Having a company-issued phone was a matter of pride for executives. Then by 2010, most employees preferred to use their personal smart phones and tablets to do company work rather than the company-issued phones that did not have web browsers and other desirable features. Information security professionals had to scramble to deal with the far-reaching implications of this change. Whereas earlier they could issue phones such as Blackberries and impose the desired security policies on these devices, the security policies on personal devices were controlled by the users, not by the companies they worked for. As a result, information security professionals reported in 2010 that dealing with mobile device security was one of their top concerns. These concerns, and hence the demand for information security professionals, are only likely to increase in the near future, securing the professional prospects for information security professionals.
Professional activities
What do information security professionals do? The BLS website describes the role of information security analysts as:
Plan, implement, upgrade, or monitor security measures for the protection of computer networks and information. May ensure appropriate security controls are in place that will safeguard digital files and vital electronic infrastructure. May respond to computer security breaches and viruses.
Illustrative examples: Computer Security Specialist, Network Security Analyst, Internet Security Specialist
This is a fairly technical set of activities. However, a lot of the work done by information security professionals is non-technical in nature. Figure 1.2 shows the distribution of the top four most time-consuming activities reported by respondents to the (ISC)2 survey.4 It is seen that regulatory issues, policy development, and managerial issues constitute the bulk of information security work.
Desired competencies
The primary responsibilities of information security professionals are to anticipate information-related problems and to minimize their impact. Responses to the ISC2 survey highlighted the eight areas with the greatest need for training, as shown in Figure 1.3. These are very good indicators of the competencies expected of information security professionals. It can be seen that successful information security professionals are expected to have expertise in systems analysis and design to identify possible vulnerabilities entering homegrown applications, system administration skills to examine systems and identify traces left behind by hackers (forensics), and risk management. In addition, the business continuity and disaster recovery expectations require that information security professionals also have a very good understanding of the business as well as the IT infrastructure to be able to identify the most mission-critical applications in the organization so that these can be quickly brought up online in the event of a natural or man-made disaster.
The intent of this section was to satisfy you that information security is a viable profession. Hopefully, it has also conveyed that information security is a very exciting profession. Further, since information security lapses attract a lot of public scrutiny, the activities of information security professionals are of great interest to top management of organizations, probably more so than those of many other parts of an organization's IT infrastructure. In fact, according to the ISC2 survey, the information security group reports to executive management, i.e., the CEO, CIO, or equivalent, in almost 25% of the organizations.
Brief history
From this point on, we assume that you are interested in learning about information security from a professional perspective. That is, you are interested in learning about the subject for use in your career. Almost everything we do today regarding information security is the result of famous lapses that have occurred over the years and the responses by industry to these experiences. Many of these incidents are now part of the professional folklore. It is useful for you to know about these incidents in order to better appreciate regulatory requirements, the concerns of managers as well as to build your vocabulary in the profession. The list below is not intended to be comprehensive;5 it only captures the major incidents that led to regulatory or industry actions or serve as a barometer for information security concerns at the time.
1981 – Development of the core Internet technologies (TCP and IP): The core technologies of the Internet were finalized in 1981. There was no mention of security in these technologies, indicating that at that time the technology world was not concerned about information security. Since TCP and IP were available for free, they became the preferred networking technology for UNIX systems, widely used at universities and various intensive organizations such as hospitals and banks.
1982–1983 – Gang of 414's: Computer intrusions began soon after TCP and IP were integrated into industrial equipment. The most highly publicized incident of this time was the gang of 414's, a group of six teenagers from Milwaukee, who got their name from the telephone area code for Milwaukee. These teenagers found it exciting to get into systems that were supposed to be out of their reach. Using home computers, phone lines, and default passwords, this group was able to break into approximately 60 high-profile computer systems, including those at the Los Alamos Laboratories and the Memorial Sloan-Kettering Cancer Center in New York. The incident received wide coverage, including a Newsweek cover story titled “Beware: Hackers at play.” This is believed to be first use of the term “hacker” in the mainstream media in the context of computer security. While the teenagers themselves did no harm, it was easy for the industry to see that the simple techniques used by the kids could easily be replicated by others. As a result, the US Congress held hearings on computer security. After more such incidents, Congress passed the Computer Fraud and Abuse Act of 1986, which made it a crime to break into federal or commercial computer systems.
1988 – Morris worm: Robert Morris, then a graduate student at Cornell, and now a Professor of Computer Science and Artificial Intelligence at MIT, released a 99-line self-replicating program on November 2, 1988, to measure the size of the then nascent Internet. As a result of a design feature of the program, it brought down many systems it infected, and achieved several landmarks in the process. It is considered the first Internet worm. In percentage terms, it is estimated to have brought down the largest fraction of the Internet ever (10%). It also resulted in the first conviction under the 1986 Computer Fraud and Abuse Act. Robert Morris was sentenced to probation, community service and a fine. The Morris worm prompted the US Government to establish the CERT/CC (CERT coordination center)6 at Carnegie Mellon University as a single point to coordinate industry–government response to Internet emergencies. Prof. Morris was also a co-founder of Viaweb, an e-commerce firm bought by Yahoo!, and renamed it as Yahoo! Store.
As an interesting anecdote, Robert Morris' father, Bob Morris, designed the password encryption system for the UNIX operating system that is used even today. Even more interestingly, at the time of this incident, the senior Bob Morris was the chief scientist for the National Computer Security Center (NCSC) of the National Security Agency (NSA),7,8 the federal agency responsible for designing secure computers.
1995–1998 – Windows 95/98: Microsoft released Windows 95 on August 24, 1995. The operating system had a graphical interface and was designed to run on relatively inexpensive computers). The release was supported with a heavy marketing push, and within a very short time, it became the most successful operating system ever produced, and drove most other operating systems out of the market. Windows 95 was designed primarily as a stand-alone single-user desktop operating system and therefore had almost no security precautions. Most users ran Windows 95 without passwords and most applications ran on Windows 95 with administrative privileges for convenience. However, Windows 95 supported TCP/IP, thereby bringing TCP/IP into mainstream businesses. This combination of a security-agnostic networking technology (TCP/IP) combined with an equally security-agnostic business desktop created a fertile environment for information security compromises to flourish. In talks, security experts sometimes refer to this environment as the source of the information security profession.9 Even the introduction of Windows 98 on June 25, 1998, made no change to the basic security design of Windows desktops.
1996 – Health Insurance Portability and Accountability Act (HIPAA): This Act which primarily focused on protecting health insurance for US workers when they change or lose jobs also had important information security implications. Many government leaders believed at the time that electronic health records (EHR) were an important instrument to lower rising healthcare costs in America. The Act therefore also pushed for electronic health records. Since information security was getting recognized as an important concern, the law had provisions to make organizations responsible for maintaining the confidentiality of patient records in the healthcare industry. At the current time, the healthcare industry has until 2014 to move over completely to EHR. This is a major driver of demand for information security at the time of writing this edition (2012–2013).
2000 – ILOVEYOU virus: On May 5, 2000, this virus was released by a student in the Philippines (Figure 1.4). The virus deleted images on infected computers and automatically sent itself as an email attachment to the Outlook contacts list of infected computers. The virus infected millions of computers worldwide, and caused billions of dollars in damage. The creators of the virus, Reomel Ramores and Onel de Guzman, were traced within hours of the release of the virus. However, investigators realized very quickly that Philippines had no law against writing computer viruses, and had to drop all charges against the students.10 This incident led to the realization that information security was a global phenomenon and led to a push from developed countries for developing countries to revamp their information security laws. However, even today there are significant differences between countries regarding information security laws. For example, while writing a virus can lead to fines of up to $250,000 and 10 years of imprisonment in the United States, the punishment in the Philippines can range from 100,000 Pesos (about $2,500) and up to an amount commensurate to the damage and up to 3 years in prison.11
2002 – Sarbanes–Oxley Act: During 2000–2002, America witnessed many unpleasant incidents of corporate fraud involving such legendary companies as Enron, Tyco, and WorldCom. For example, Enron claimed revenues of over $100 billion in 2000 and declared bankruptcy the next year. MCI-WorldCom revealed in 2002 that it had overstated its earnings by over $72 billion in the past five quarters. These frauds were enabled by fraudulent manipulation of accounting systems, believed to be at the behest of firm leadership. However during trials, the CEOs consistently tried to escape blame by pleading ignorance of accounting procedures, and blind trust in their highly paid and well-educated lieutenants. Since the retirements of most Americans are invested in large publicly traded firms, their downfall affects most American families. Compelled to act and ensure correctness in financial reporting, Congress enacted the Sarbanes–Oxley Act in 2002. The Act focused on making the key executives personally accountable for the correctness of financial reports filed by publicly traded companies. The Act had three major provisions. Section 302 of the Act requires the CEO and CFO of firms to sign a declaration of personal knowledge of all the information in annual filings. Section 906 of the Act imposes criminal penalties including imprisonment of up to 20 years for incorrect certification. Section 404 of the Act has had a major impact on the information security profession because it requires that the certification in Section 302 be based on formal internal controls. This has led to significant investments in internal controls over financial reporting in publicly traded firms.
2005–2007 – Retailer attacks: In December 2006, T.J. Maxx reported that its computer systems, which processed credit card payments, had been breached (Figure 1.5). On investigation, it was found that the breach had started a year and a half ago in July 2005 and over 45 million credit card and debit card numbers had been stolen. It turned out that the leader of the group involved in the breach was Albert Gonzalez, an informer for the US Secret Service and in fact Albert was cooperating with the Secret Service in connection with another case at the time of these attacks. Investigations also revealed that the group had also hacked into the systems at other retailers such as BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, and Sports Authority. The modus operandi of the group was to drive along US Route 1 in Miami and seek out an insecure store with wireless networks to enter the corporate networks. Later the group improved its methodology and used SQL injection attacks to enter the networks at Hannaford Brothers and Heartland Payment Systems, a credit card payments processing company. Over 125 million credit card numbers were estimated to have been stolen from Heartland, and the company estimated damages at over $12 million. In March 2010, Albert Gonzalez was sentenced to 20 years in prison. He also forfeited over $1.65 million that he had earned from selling fake credit cards based on the stolen information. These incidents highlighted that even large firms had glaring information security weaknesses, which could lead to serious embarrassment and losses. The SQL injection attacks in particular created an awareness of the need to pay attention to information security during software development, and introduced the term “secure SDLC” to the IT lexicon.
2008 – Denial of service attacks in Georgia: Coinciding with the military war between Georgia and Russia in 2008, Georgia was the victim of massive distributed denial of service attacks. The attacks defaced the websites of many media and government organizations, limiting their ability to communicate their viewpoints about the war to their citizens (Figure 1.6). The circumstances of the incident led many people to believe that the cyber-attacks12 were caused by Russia as part of a war strategy. If so, these were the first known incidents of cyber-war being used as an instrument of warfare.
June 2009 – Establishment of the US Cyber Command: In April 2009, the Wall Street Journal reported that intruders had broken into the computer networks of defense contractors developing the Joint Strike Fighter, also called the F-35 Lightning II.13 The $300 billion project was the Defense Department's costliest weapons program ever, and used 7.5 million lines of computer code. Intruders had stolen terabytes of data related to the aircraft's design and electronics. It was believed that the theft would help enemies plan their defenses against the fighter. The contractors involved in the project include Lockheed Martin, Northrop Grumman, and BAE Systems. Also in April, the Wall Street Journal reported that the US electricity grid had been penetrated by spies from China, Russia, and other countries. The spies also inserted computer software in the grid, which could be used to cause damage by remote control.14
Soon thereafter, on June 23, 2009, the US Cyber Command was created to defend US military computer networks against attacks from adversaries and also to respond in cyberspace as necessary). At the time of creation of the new command, there were concerns that the initiative might impose undue restrictions on the civilian Internet under the pretext of defense.
2010 – Operation Aurora and Google-China: On January 12, 2010, a blog post by Google's Chief Legal Officer reported that the company had detected an attempt to steal its intellectual property originating from China (Figure 1.7). The attacks were also aimed at accessing emails of Chinese human-rights activists. The US Government soon escalated the incident with Congress announcing its intention to investigate the allegations and the Secretary of State labeling the Chinese censorship of the Internet to an information-age Berlin Wall. Further investigations traced the attacks to two educational institutions in China – Shanghai Jiaotong University and the Lanxiang Vocational School. Jiaotong is home to one of China's elite computer science programs, and Lanxiang is involved in training computer scientists for the Chinese military.15 China has however denied formal government involvement and called the attacks simply an attempt by students to refine their computer skills.
April 17, 2011 – Sony PlayStation Network (PSN): Sony announced that an external intrusion had compromised its PlayStation Network and Qriocity service), and that hackers had obtained personal information on the 70 million subscribers of the network. The company could not rule out the possibility that credit card numbers may also have been stolen. In response, the company took the network offline while it tried to ensure that all traces of the offending software had been removed from the network. During the time, millions of kids all over the world who had planned their summer breaks around catching up with online gaming on PSN had to find alternate ways to pass their time. For this reason, while the intrusion affected a relatively innocuous network, the impact on families around the world was huge and almost every family with kids followed the daily developments around the attacks.
This brief chronology highlights how information security attacks have evolved from technical proofs-of-concept to commercially driven attacks to steal credit card information. Of late even governments are being suspected of pursuing their agendas through cybercrime. In Europe, a remote Romanian town, Râmnicu Vâlcea, has emerged as the focal point in global cyber money laundering. In the middle of nowhere, this town has car dealerships selling Mercedes-Benz and other expensive cars.16 Social response has evolved as well, from judges merely warning intruders and laws making specific exceptions for juveniles in spite of their known involvement in cyber-attacks (414's) to governments establishing entire military commands to deal with cyber security.
Definition of information security
That is the background which has defined organizations' concerns about information security. If you were observant, you may have noted that the incidents had different impacts on information security. In the case of the 414's, the primary concern was loss of privacy. In the Enron case, it was accuracy of information, and in the case of Georgia, it was the ability of citizens to access relevant information. Information security can mean different things to different people.
Information security is now defined as protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide integrity, confidentiality and availability.
While the above definition is based on the code of law of the United States (section 3542, Chapter 35, title 44),17 the definition is remarkably consistent across the industry. For example, RFC 219618,19 on information security states that the basic goals of security are availability, confidentiality, and integrity.
The CIA triad
The law writes the dimensions of information security in the sequence – integrity, confidentiality, and availability. However, these three dimensions are better remembered in a slightly different sequence as the CIA triad, where C stands for confidentiality, I for integrity, and A for availability. To maintain symmetry with this popular phrase, we will henceforth discuss the information security dimensions in the sequence of this triad – confidentiality, integrity, and availability.
Confidentiality
According to section 3542 of the US code, Confidentiality means preserving authorized restrictions on access and disclosure, including means for protecting personal privacy and proprietary information.
The law recognizes the right of individuals to privacy, and such right extends to information which, if made public, could cause harm or embarrassment to the person. Confidentiality is the responsibility of custodians of information to provide that privacy to the individuals whose information they have in their possession. All the examples of credit card theft discussed in this chapter relate to the failure of organizations to maintain confidentiality of the information in their possession.
If you ask most people to define information security, they typically will respond with some variant of “information security means not losing credit card information.” Most people associate information security with confidentiality.
Integrity
Integrity means guarding against improper information modification or destruction, and includes ensuring information non-repudiation and authenticity.
When you pull information from an information system, for example, your grades from the university, or the monthly statement from your bank account, you trust that the information provided is reliable and actionable. For example, when the bank reports the balance in your checking account, you do not think it necessary to tally the totals of credits, debits, and interest income yourself to verify the amount. Rather, you trust that the bank has made the right calculations. Imagine how complex life would be if the information you received from IT systems could not be trusted to be accurate. Integrity is the aspect of information security that prevents that from happening.
In the examples above, the inability of IT systems to prevent senior executives at Enron and WorldCom from manipulating company records to serve their personal interests were examples of failure of integrity.
Availability
Availability means ensuring timely and reliable access to and use of information.
When you log into your course site online, you expect it to be online. That in essence is availability. The relevance of availability to information security is self-explanatory. An information system that is unavailable is an information system that is not useful. In the example above, the response of the Sony PSN was an example of failure of availability. Most viruses also have the same impact – they typically delete important files, causing a loss of availability. Even if the files can ultimately be recovered from backup systems or other sources, the time lost in recovering those files represents time not spent doing useful work, i.e., lack of availability.
The right to privacy
Of the three dimensions of information security, confidentiality is probably the most difficult to define precisely. This is because the social expectations of privacy are very dynamic. What one person considers private, photographs for example, another may consider public. What was once considered private may now be considered public. While organizations may fiercely protect the privacy of their employees, the same employees may willingly share much of the same information voluntarily on social networks and other websites.
In fact, the right to privacy is fairly recent in US law. The first modern reference came in an 1890 article in the Harvard Law Review, where Louis Brandeis (who later became a Supreme Court Justice) and his law partner Samuel Warren wrote:20
Recent inventions and business methods call attention to the next step which must be taken for the protection of the person, and for securing to the individual what Judge Cooley calls the right “to be let alone.” Instantaneous photographs and newspaper enterprise have invaded the sacred precincts of private and domestic life; and numerous mechanical devices threaten to make good the prediction that “what is whispered in the closet shall be proclaimed from the house-tops.” For years there has been a feeling that the law must afford some remedy for the unauthorized circulation of portraits of private persons; … The press is overstepping in every direction the obvious bounds of propriety and of decency. Gossip is no longer the resource of the idle and of the vicious, but has become a trade, which is pursued with industry as well as effrontery … modern enterprise and invention have, through invasions upon his privacy, subjected him to mental pain and distress, far greater than could be inflicted by mere bodily injury.
The article was an outburst by Samuel Warren in response to media coverage of high society events of the time, including events in the Warren family which following the social conventions of the time, greatly embarrassed the Warren family.21 Readers may find an eerie similarity between these thoughts from the 19th century and the privacy debates of the 21st century surrounding Facebook and other social media websites.22
In recent years, as organizational concerns over information security have intensified, many experts have proposed expanding the definition to include aspects of information security such as non-deniability (if a company charges a service ordered by phone to your credit card and you deny ordering for the service, how do you prove that you did indeed place the order?). However, for the purposes of this text, we will focus on the traditional definition of information security of integrity, confidentiality, and availability.
Personal guide to maintaining information security
If you are studying information security, perhaps it is a good idea to develop a 2-minute elevator speech on information security that answers the question, “how can I best maintain my information security.” You may get this question from friends and family members who are concerned about their own information security. Every professional will give you a different answer, based on their own experiences. Here is ours.
If you wish to maintain your information security, you will get the best returns for your efforts from the following:
Antivirus: Make sure that you are using antivirus software and that its subscription is current. Many people can get the software and subscription for free as part of their ISP subscription or from their employers or school.
Automating software updates: Wherever possible, configure your operating system and application software to apply updates automatically.
Passwords: If possible, use a different password at each site that requires a password. If this is difficult, at the very least, use two passwords – one for the “fun” sites such as newsletters, email etc and another for financial organizations such as banks and brokerages. Never share the financial password anywhere or with anyone.23 For an easy way to add security, pad your chosen password with characters, e.g., pass – word is not very difficult to remember, but it is vastly more secure than password.
SUMMARY
This chapter provided an overview of information security. We started by looking at why companies have found it necessary to invest in information security and what activities information security professionals spend their time on. There was a quick review of the important information security incidents in the last quarter century. We saw how based on these experiences, the industry has defined information security as the CIA triad – confidentiality, integrity, and availability.
In the rest of this book, we will focus on developing skills to implement information security. We start with essential system administration and scripting so that students can experiment with technology throughout the semester. We do this because in our opinion, system administration and scripting skills are extremely important differentiators in the workplace, particularly for entry-level positions. We then move on to more conceptual issues in Part 2. To implement information security, we present the framework composed of assets, vulnerabilities, threats, and controls and show how assets are determined, threats are identified, and incidents are handled. Finally, in Part 3, we examine the managerial and regulatory context.
EXAMPLE CASE–WIKILEAKS, CABLEGATE, AND FREE REIGN OVER CLASSIFIED NETWORKS
In February 2010, the then relatively unknown WikiLeaks began releasing classified memos from the archives of the US State Department. In summer 2010, Wikileaks reached an agreement with leading newspapers around the world, including the New York Times in the United States and Der Spiegel in Germany, to publish selected cables from the archives in redacted form, i.e., after removing identifying information. The first of these were published in November 2010. By September 2011, the security on the files at Wikileaks had been compromised and all memos were visible online in full text form to anyone. About half the leaked memos were classified as “unconfidential,” 45% were “confidential,” and the remaining were marked “secret.” None of the leaked memos was classified as “top secret.” The incident had acquired the moniker “Cablegate.”
Wikileaks is a non-profit organization launched in 2007. The leading force behind Wikileaks is Julian Assange, an exceptionally competent computer programmer from Australia, who has a strong zeal for reform using the freedom of the press. Accordingly, the mission of Wikileaks is to help whistleblowers reach journalists anonymously by providing a secure and anonymous electronic drop box. It is motivated by the principles of freedom of speech and media publishing. It is proud of its record of defending its journalists and anonymous sources against legal and political attacks aimed at obtaining the identities of these sources.
The memos leaked by Wikileaks were the result of decades of information collection effort by US diplomatic offices from around the world. The earliest memo dates back to 1966 and the leak was a source of considerable embarrassment to the US State Department. The leaked memos summarized analysis by world leaders and US diplomats. Reflecting geopolitical realities, often these analyses were at odds with the leaders' public positions. The leaders shared their analyses based primarily upon complete trust in the ability of the US State Department to maintain the confidentiality of the information and their identities. With no known information leaks in the past, US diplomats around the world had a high degree of credibility in the diplomatic community. This gave them unparalleled access to sensitive and privileged information.
In fact, once the memos were leaked, leading newspapers in many countries published excerpts from memos that related to their country to satisfy their readers' curiosity about what the United States knew about their country.
The source – Pfc Bradley Manning
Private First Class (Pfc) Bradley Manning is a US army soldier, 23 years of age at the time of Cablegate. He enlisted in the Army in 2007 and trained as an Intelligence analyst. Around this time, through friends, he also came in touch with the programmer-enthusiast community at Brandeis University near Boston. In 2008, when he was deployed to Iraq, his job gave him access to two information networks – SIPRNet and the Joint Worldwide Intelligence Communication System (JWICS). More than 3 million US Government personnel and soldiers have access to these networks. The wide access to these networks was the result of the 9/11 attacks where it was believed that gaps in information-sharing within the government was responsible at least in part for the failure of the US Government to prevent the attacks.
Through these networks, Pfc Manning obtained access to the leaked memos. Sometime in 2009–2010, he decided to pass these confidential memos on to Wikileaks. In May 2010 Adrian Lamo, a former hacker and information source about the hacker community was profiled in Wired magazine. Probably as a result of the article, Pfc Manning contacted Lamo and chatted with him on AOL Instant Messenger (IM). During the chat, Manning revealed that he had leaked the memos and suggested his motivations for doing so. Lamo decided to report this to the authorities, which led to Pfc Manning's arrest and the revelation of the identity of the Wikileaks source. Wired magazine published the transcripts of the chats between Pfc Manning and Adrian Lamo.24 One of the most memorable lines in the transcript is (12:15:11 PM): hypothetical question: if you had free reign over classified networks for long periods of time … say, 8–9 months … and you saw incredible things, awful things … things that belonged in the public domain, and not on some server stored in a dark room in Washington DC … what would you do?
Pfc Manning was charged before a military court on February 23, 2012, with offenses including aiding the enemy. Though aiding the enemy is a capital offense (i.e., can lead to the death penalty), prosecutors did not seek the death penalty in this case.
REFERENCES
http://en.wikipedia.org/wiki/United_States_diplomatic_cables_leak
http://en.wikipedia.org/wiki/Bradley_Manning
http://www.bbc.co.uk/news/world-11047811
http://www.wired.com/threatlevel/2011/07/manning-lamo-logs/
http://www.cablegatesearch.net/
CHAPTER REVIEW QUESTIONS
- What are some of the strengths of information security as a career choice?
- What are some of the ways in which stolen information can be used for profit?
- What are some of the most common ways in which the carelessness of end users can lead to a loss of sensitive information?
- What are some of the common professional responsibilities of information security professionals?
- Provide a brief description of the activities on which information security professionals spend most of their time.
- Briefly describe the most important skills that information security professionals are expected to possess to succeed in their job.
- How did the development of inexpensive computer networking technology (TCP/IP) affect information security?
- Briefly describe the activities of the gang of 414's.
- Briefly describe the impact of the gang of 414's on information security.
- Briefly describe the Morris worm. What are some of the factors that make it a landmark in the evolution of information security?
- What was the impact of Windows 95/98 on information security?
- How does HIPAA (the Health Insurance Portability and Accountability Act) affect the profession of information security?
- What are the provisions in the Sarbanes–Oxley act that are related to information security?
- What were some of the immediate factors that led to the creation of the US Cyber Command?
- Provide a brief description of the US Cyber Command and its activities.
- What was operation Aurora?
- Briefly describe the outage that affected the Sony PlayStation Network in 2011.
- What is information security?
- What is confidentiality?
- What is integrity?
- What is availability?
- Provide an example of a violation of confidentiality.
- Provide an example of a violation of integrity.
- Provide an example of a violation of availability.
- Which in your opinion is the most important of the three components of information security? Why?
EXAMPLE CASE QUESTIONS
- Of the three dimensions of information security, which was/were affected by Cablegate?
- What do you think motivated Pfc Bradley Manning to release the memos to Wikileaks, and then discuss his actions with Adrian Lamo, well aware of the risks of these actions?
- Based on publicly available information, what were some of the measures taken by the US Government to secure the memos?
- To what extent were these measures effective?
- If you were responsible for the information security of these memos, what would you have done to prevent an incident such as Cablegate from happening?
- Why do you think the recommended actions above were not taken by the experts responsible for the information security of these memos?
HANDS-ON ACTIVITY–SOFTWARE INSPECTOR, STEGANOGRAPHY
The hands-on activities in every chapter are designed to help you become familiar with the common tools used by information security professionals. These activities also help you apply the material covered in the chapter within the context of real systems.
Secunia Online Software Inspector
As the first hands-on activity, you will use a simple, free resource to identify the most important security problems in the computers you use for daily work. This process is called an audit, and PC audit tools are available from many software companies and ISPs. While this exercise uses the tool provided by one such firm – Secunia, you are free to use similar tools from a provider of your choice.
The Secunia Online Software Inspector is available from the firm's website.25 The product's webpage appears as in Figure 1.8.
Using the software is straightforward. Clicking on the “Start Scanner” button on the page starts the scan with default options and the scan takes a few minutes to complete. When it is done, the report appears at the bottom of the page. A sample report is shown in Figure 1.9.
The report shows that the scanned computer had many software applications that needed to be updated to their latest versions. We have seen in this chapter how older versions of software typically have known vulnerabilities that can be exploited by viruses and hackers. It is a good idea to periodically run an audit tool such as this and update or remove outdated software.
PC audit questions
- Run a PC audit tool such as Secunia's Online Software Inspector on one of your home computers. Submit a screenshot such as the one shown in Figure 1.9.
- What are some actions you are considering after viewing the results of your PC audit?
Steganography26
This exercise gives you the opportunity to take a look at the “dark side” of information security. You will act as a revolutionary trying to secretly send a message to a friend. You are trying to fix the time and place of a meeting with a group of friends. You believe that all your emails are being scanned.
While there a numerous ways of doing this, in this exercise you will use a particularly easy and interesting method – you will hide the text with the relevant information inside an image (say your university's logo) and send it to your friends. If your friends know where to look for, they can easily get the information.
The goal of the exercise is to demonstrate how easy it is to create information security challenges and therefore how challenging it can be to eliminate information security problems.
To do the exercise, you will need the following:
- An image file. While almost any image will do, it is most convenient to take a small .jpg or .gif file. Usually your school's logo will work fine. Save the file on your computer. In this exercise, we will assume that all files are saved in the Downloads folder. It is a particularly convenient location on Windows and Mac computers. For this example, the file is called logo.gif (if gif image) or logo. jpg (if jpg image).
- A text file containing the date, place, and time of the meeting. Save the file in the same folder as the image above (an easy way to create this file is to open Notepad, type in the contents and save the file in the Downloads folder). For this example, the file is called msg.txt.
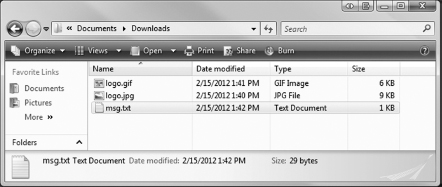
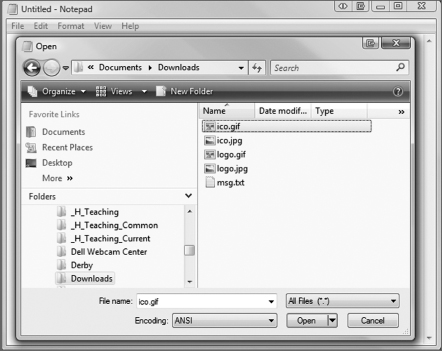
When you complete the above, your Downloads folder will look as in Figure 1.10.
We are now ready to hide the text file inside the image files. You will need to open the Command prompt for this. In Windows, this is accessed from All programs → Accessories → Command Prompt. On Mac, this is accessed from Applications → Utilities → Terminal. To reach the Downloads folder, type in the command:
Cd DocumentsDownloads
On Windows, the following command will append file2 at the end of file1 and save the results as file3:
Copy /B file1+file2 file3
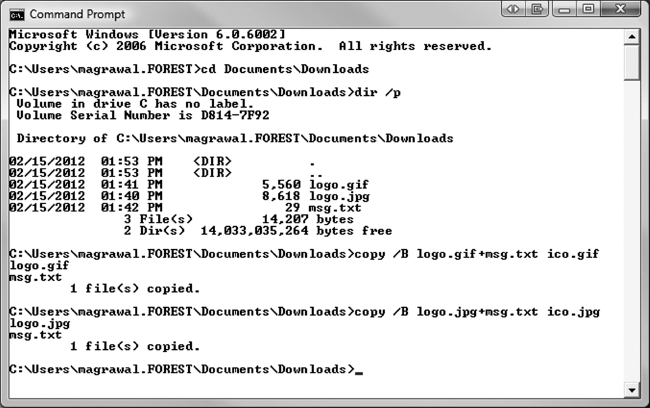
To use this command to hide our text file in the image file, we can use the following commands:
Copy /B logo.jpg+msg.txt ico.jpg (for the jpg image) Copy /B logo.gif+msg.txt ico.gif (for the gif image)
The sequence of commands is shown in Figure 1.11.
After you run these commands, the contents of your Downloads folder appear as shown in Figure 1.15 (to preview the images, you can select Views → Large icons).
You may notice that the manipulated images (ico.gif and ico.jpg) are indistinguishable from the original images (logo.gif and logo.jpg respectively). A person without knowledge of your activities would not find anything amiss in the manipulated images. You can verify that these images can be opened in browsers and other applications and be used anywhere images can be used.
But how can your friends recover the information hiding in the images?
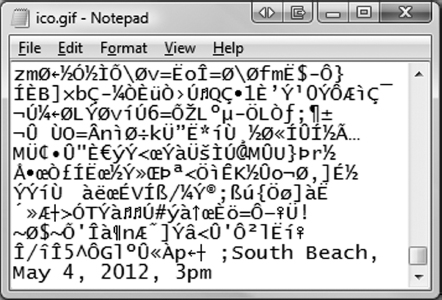
Turns out, it is quite easy; they just need to use the right application – Notepad in this case. Start Notepad, select File → Open and navigate to the Downloads folder. Change the file type to All files (*.*) as in Figure 1.13 and select either the ico.gif or ico.jpg file. Ignore the unreadable text and scroll to the end of the file. You will see something like what you see in Figure 1.14. You see that it is possible to create interesting information security challenges using simple, every day IT tools available to everybody. You may also appreciate why these possibilities create nightmares for information security professionals.
What you did in this exercise is called Steganography – hiding information in a way such that no one suspects the existence of the message.
Steganography questions
- Create one steganographic image following the directions in this section.
- Submit printouts of the original image, the modified image, and a screenshot of the text embedded in the image as in Figure 1.14.
CRITICAL THINKING EXERCISE: IDENTIFYING CIA AREA(S) AFFECTED BY SAMPLE REAL-LIFE HACKING INCIDENTS
This chapter introduced some of the most damaging (and hence well-known) information security incidents. These are listed in Table 1.1 for your convenience. For each incident, identify the information security area (confidentiality, integrity, or availability) that was most affected. While we have not yet discussed measures organizations take to defend themselves against these kinds of incidents, make an initial attempt to identify some actions organizations can take to ensure that these incidents do not happen to them.
DESIGN CASE
To give students the opportunity to walk through the process of developing the information security architecture for an organization, we will use a threaded design case that runs throughout the book. In each chapter, you will use the concepts covered in the chapter to build the information security architecture for the organization. To help in the exercise, the chapters in the book are arranged in approximately the sequence in which the issues relevant to information security are addressed in practice. Therefore, your activities in earlier chapters will help you build up your solution in later chapters.
The organization we consider in the case is a typical state university. We call it the Sunshine State University. Modern universities such as the Sunshine State University share most characteristics of medium-to-large businesses. They serve upwards of 20,000 demanding users, have thousands of employees, have budgets in excess of a billion dollars, and comply with various regulations. To meet the needs of all these constituencies, universities have all the business processes and IT systems found in a typical corporation such as HR, payroll, finance, and travel in addition to typical services such as email and calendar. Also, many research centers at universities act as custodians of sensitive personal data associated with research projects, creating information security needs comparable to the needs of most large businesses. In fact, it is not surprising to find state universities being some of the largest deployments of leading information technologies.
From the perspective of students and faculty, one of the greatest advantages of using the university as the context for the threaded design case is that it is very familiar to everyone. If necessary, faculty can customize the context to suit any special needs of their institution. In most cases, students will have encountered some of the issues discussed in the case, which greatly facilitates learning.
The organization
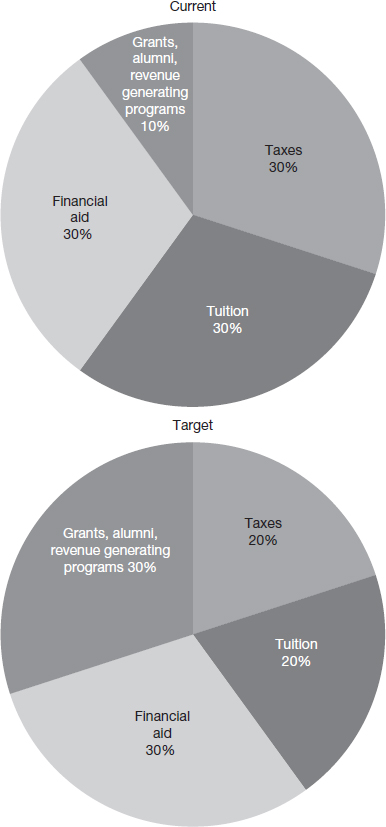
Sunshine State University is a State University. Like many state universities, about 30% of its funding comes from state taxes; another 30% comes from student tuition, and 30% from student financial aid (Figure 1.15). The remaining 10% comes from an assortment of sources including research grants, alumni contributions, and revenue-generating academic programs such as executive education. The university is trying to move towards a more elite profile by reducing its dependence on state taxes and tuition to about 20% each. The difference would be made up by increasing revenues from other sources to about 30% of the total budget from the current 10%. The current enrolment at Sunshine State University is about 20,000 students. To serve these students, the university has about 700 faculty members (leading to a student–faculty ratio of about 29). There are also about 1,500 administrative support personnel performing functions such as academic counseling, scholarships, IT, finance, payroll, office managers, and so on.
To improve the student educational experience, Sunshine State University has begun to increase its focus on research opportunities for graduate and undergraduate students. At the current time, this emphasis is led by the colleges of Engineering and Medicine. Recently hired faculty members in both these colleges have strong records of attracting research funding from sources such as the National Science Foundation and the National Institutes of Health. While these projects create great opportunities for students to earn scholarships while working on research projects, university administrators have been advised by their colleagues that the university should upgrade its systems for handling the data created by these projects. Universities have been taken to court for violating the privacy of research subjects and students.27
Organization structure
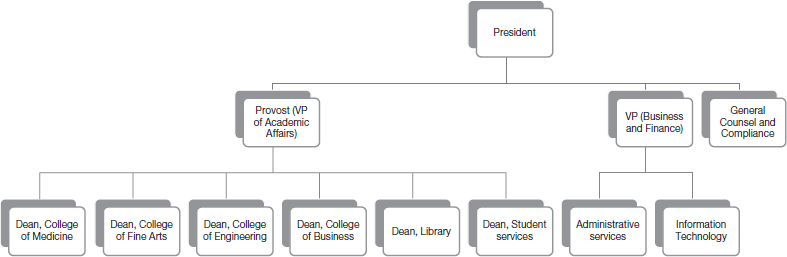
An extract from the organization structure of the university is shown in Figure 1.16. The discussion in the book will be limited to these units of the university. Provost is responsible for all Academic Affairs on the campus. The Chief Operating Officer is responsible for all business and finance activities on campus. The General Counsel manages legal affairs and compliance.
Students in the College of Medicine do their residency in the local Downtown Hospital. The hospital itself is part of a larger conglomerate and has its own IT support personnel. A major research project initiated by college faculty has enrolled 4,000 newborn children to study the medical impacts of interactions between environmental factors and genetic structures. The study will follow these children for up to 15 years. The college maintains its own IT services that primarily consist of providing email services and shared document storage.
The College of Fine Arts is known for its School of Art, graduating several well-known graphic artists. While the location of the university is not home to a major movie studio, some of its recent graduates have leveraged the video capabilities of DSLR cameras to gain success as movie directors in the indie movie circuit.28
The School of Engineering is beginning to gain traction with funding agencies, attracting some seed funding from the US Department of Defense for developing sensors and associated applications for battlefield deployment.
In addition to its regular teaching and research activities, the College of Business supports local minority businesses in the community by providing a business incubator, where small disadvantaged business (SDBs) can utilize IT resources and mentoring from local faculty on writing business proposals, marketing, distribution, etc.29
The Library is small but very active. In addition to the traditional library services, the library offers undergraduate and graduate degrees in library sciences. The library is actively looking for partnerships with vendors and publishers in order to migrate to an e-textbook model. They are also leading an effort to combine collections with other state and local government libraries and improve their interlibrary loan systems.
Student Services supports students by attending to their non-course-related needs such as student loans, housing, code of ethics, student government, and other student organizations.
The business and finance services on campus are largely centralized. The administrative services component handles purchasing, physical plant, grounds maintenance, and University Police. They also deal with payroll, hiring procedures, and benefits. Information Technology deals with all enterprise-wide IT efforts, including the Enterprise Business Systems. The Student Information System, HR systems, and payroll and financial systems are operated centrally by IT.
Some ancillary IT services are operated as a mix of centralized services and local support. These services include desktop support and management, file share management, print management, account provisioning, and server management. To save costs, the management of some of these services is led by non-tenured faculty members whose primary responsibility is to teach classes. Generally speaking, technical staff is over-worked, under paid, but is well-trained and qualified. They do their best to meet student expectations on a limited budget. The information security department is part of IT.
Security design case questions
Answer the following questions with regard to Sunshine State University:
- What are some of the ways in which weaknesses in information security can potentially cause embarrassment or financial losses to the university?
- List three items of information stored in the university's information systems for which the university is expected to maintain confidentiality. What are some of the ways in which the confidentiality of each of these items may be compromised?
- List three items of information stored in the university's information systems for which the university is expected to maintain integrity? What are some of the ways in which the integrity of these items may be compromised?
- List three items of information stored in the university's information systems for which the university is expected to maintain availability? What are some of the ways in which the availability of these items may be compromised?
2http://www.bls.gov/oes/current/oes151179.htm
3https://www.isc2.org/uploadedFiles/Landing_Pages/NO_form/2011GISWS.pdf
4https://www.isc2.org/uploadedFiles/Landing_Pages/NO_form/2011GISWS.pdf
5A more comprehensive source is Wikipedia: http://en.wikipedia.org/wiki/Timeline_of_computer_security_hacker_history
6While CERT typically stands for Computer Emergency Response Team, CMU has registered the name as a service mark with the US Patents and Trademark Office
7http://cm.bell-labs.com/cm/cs/who/dmr/crypt.html
8For another very interesting account of Bob Morris, read the amazingly humorous book by Cliff Stoll, “The Cuckoo's Egg,” ISBN 0671726889
9For example, Dan Geer (chief information security officer for In-Q-Tel, the venture capital arm of CIA) referred to this in his talk at the ISSA meeting in Tampa, December 2011.
10Arnold, W. “TECHNOLOGY: Philippines to drop charges on e-mail virus,” New York Times, August 22, 2000.
11http://www.chanrobles.com/ecommerceimplementingrules.htm (accessed 02/28/2012)
12Cyber is a prefix that refers to anything related to computers or networking
13Gorman, S., Cole, A. and Draezen, Y. “Computer spies breach fighter-jet project,” Wall Street Journal, April 21, 2009.
14Gorman, S. “Electricity grid in US penetrated by spies,” Wall Street Journal, April 8, 2009.
15Markoff, J. and Barboza, D. “2 China schools said to be tied to online attacks,” New York Times, February 18, 2010, http://www.nytimes.com/2010/02/19/technology/19china.html (accessed January 8, 2012).
16Bhattacharjee, Y. “How a remote town in Romania has become cybercrime central,” Wired Magazine, January 31, 2011, http://www.wired.com/magazine/2011/01/ff_hackerville_romania/all/1 (accessed January 8, 2012).
17The US code is available online from many sources, though the publishers frequently change the URLs to their sites. It is best to simply Google for “US code 3542” to find a site. As of January 8, 2012, the top result was the Cornell University Law School at http://www.law.cornell.edu/uscode/usc_sec_44_00003542----000-.html
18RFCs or requests for comments are the documents published by the Internet Engineering Task Force, the group that defines Internet standards including TCP and IP.
19Fraser, B. RFC 2196 site security handbook, September 1997, http://www.ietf.org/rfc/rfc2196.txt
20Brandeis, L.D. and Warren, S.S. “The right to privacy,” Harvard Law Review, December 15, 1890, 4(5): http://groups.csail.mit.edu/mac/classes/6.805/articles/privacy/Privacy_brand_warr2.html (accessed 1/12/2012)
21Gordon Crovitz, L. “The right to privacy from Brandeis to Flickr,” Wall Street Journal, 7/25/11.
22Facebook has a very well-written “Guide to Facebook security,” at https://www.facebook.com/notes/facebook-security/ownyourspace-a-guide-to-facebook-security/10150261846610766
23This recommendation comes from the fact that many compromises occur when websites store passwords without encryption. If the website is compromised, the hacker will get access to your password and will definitely use it at all bank and brokerage sites. For an interesting, but lengthy account, read the article by James Fallows, “Hacked!,” The Atlantic, November 2011, http://www.theatlantic.com/magazine/archive/2011/11/hacked/8673/ (accessed 01/13/12)
24http://www.wired.com/threatlevel/2011/07/manning-lamo-logs/
25URLs are very volatile. As of 02/12/12, the URL was http://secunia.com/vulnerability_scanning/online/. The most reliable method of course is to use a search engine to find “Secunia Online Software Inspector.”
26Source: http://lifehacker.com/230915/geek-to-live--hide-data-in-files-with-easy-steganography-tools
27See http://blog.alertsec.com/2012/01/univ-of-hawaii-settles-data-breach-lawsuit/ for an example
28“Indie” refers to independent movies. Indie films are typically produced and marketed on a shoestring budget without the assistance of major film studios. Many leading movie directors first attracted attention on the indie movie circuit.
29From Wikipedia: A small disadvantaged business (SDB) is a small business that is at least 51% owned by one or more individuals who are both socially and economically disadvantaged. SDB status makes a company eligible for bidding and contracting benefit programs involved with federal procurement.