IN THIS CHAPTER
It’s an old story, but will remain true for the foreseeable future: The only method of keeping a computer 100% secure is to lock it in a room and never turn it on. The one thing computers do best is also the most dangerous thing about them—they collect, store, and display information. Your job as system administrator is to ensure to the best of your ability that particular bits of information are displayed only to people and machines you want those bits displayed to.
With its permission-based file system, Unix and Linux make a good start on protecting your data from the bad guys. But the more connections your computer makes to other computers, first to a local area network, then to a wide area network, and finally to the Internet, the more chances your data have to be compromised.
In today’s world of interconnected computers and “always-on” access to the Internet, the importance of maintaining a secure computer has never been greater. There may be some truly dangerous “cyber-terrorists” out there working at bringing down society as we know it, but these are not the people you have to protect your machine from. The ordinary computer user has to put up with the script kiddies (young folks who want to prove their alleged computer prowess by running prewritten programs that break into other people’s systems), disgruntled employees, and fast-spreading viruses and worms. Unfortunately, that’s more than enough to keep you busy for quite some time.
In earlier chapters, you’ve learned some basic skills for protecting your computer with permissions (Chapter 19, “Managing Users, Managing Security”), fighting viruses (Chapter 15, “Managing Email Servers”), and transferring files securely (Chapter 17, “Secure File Transfer”). In this chapter, the focus is on other tools to protect yourself and your information. You will also become prepared for the worst, having some idea of what to do when your carefully laid security strategy is somehow penetrated.
There are many ways to divide up the types of computer attacks, but perhaps the easiest to understand is the internal attack, where someone has access to a computer on the local area network, versus the external attack, which occurs over the Internet. The distinction is important because it clarifies the relative danger your system is in. Chances are excellent that your local network is protected quite well by the system of permissions, along with the trust you place in your users to not damage the system. Unless you are in the habit of hanging around with the bad guys and giving them access to your system, you shouldn’t have to spend a great deal of time protecting your system against your users.
It’s that outside world that you must worry about most. In a world—and Internet—filled with millions upon millions of people, some percentage (usually small) will be evil. The Internet makes it possible for machines to connect on a vast scale, and any single machine can be attacked by people located anywhere on the planet. Within minutes of making first contact with the Internet, some machines can be attacked, although usually not successfully. Don’t let your machines be counted among the victims.
This situation is not a result of malicious users lying in wait for your IP address to do something interesting. Instead, canny virus writers have created worms that exploit a vulnerability, take control of a machine, and then spread it to other machines around them. As a result, more attacks today are the result of these autohacking tools. There are really only a handful of the truly evil out there; however, as with most human endeavors, if you’re really the target of someone’s attack, you probably cannot prevent it without a massive effort.
Scripts come in another flavor as well: prewritten code that exploits a vulnerability and gives its users special privileges on the compromised machine. These scripts are rarely used by their creators. They get posted online for the aforementioned script kiddies, who use them to invade vulnerable systems and brag about it to their friends.
Your job as a system administrator is to keep your computers and local networks from being compromised by worms, script kiddies, and the more serious attacks conducted by more experienced criminals. Your users (even if it’s just you) want to use the computer to accomplish great things and not worry about the firefights outside. Wearing your sysadmin hat, you can accomplish this task.
Regardless of the source of the attack, you can follow a five-step checklist to secure your SUSE Linux box:
Assess your vulnerability. Decide what machines can be attacked, what services they are running, and who has access to them.
Configure the server for maximum security. Install only what you need, run only what you must, and configure a local firewall.
Secure physical access to the server.
Create worst-case–scenario policies.
Keep up to date with security issues.
You’ll learn more about each step in the following sections. You must implement all the steps.
It is a common mistake for people to assume that switching on a firewall makes them safe. Although there’s no question that switching on a firewall is an important step to take, it is not a solution and never has been. Each system has distinct security needs, and taking the time to customize its security layout will give you maximum protection and best performance.
Following are the most common security mistakes people make:
Installing every package—SUSE Linux 10 has 3 gigabytes of software included in the distribution. If a machine is not going to be an FTP server, you probably don’t need to have the server installed on it. YaST makes it easy to configure your installation so that you can remove unnecessary packages and get the ones you will use.
Enabling unused services—Do you really require the capability to access your system remotely? Do you want people to upload files to your machine? If not, don’t run SSH or FTP. Always think about what you use, whether that service is open to the Internet, and whether you need it.
Disabling the local firewall on the grounds that your server already has a firewall installed—When it comes to firewalls, more is better. Your computer is your castle. Put up a wide moat with a long drawbridge, followed by a thick wall, followed by another thick wall 10 feet away from the first one. Make it hard to access, and it won’t be worth the time it takes for your attacker to continue.
Letting your machine give out more information than it needs to—Earlier we talked about the unfortunate, if inevitable, demise of
fingeras a useful tool to find out about other users on the network. Now it’s just another way to hack into someone’s system.Keeping the door to the server room unlocked—Less common in IT shops these days, but still a bad idea. Even if your sysadmins live in the server room (and with Linux servers, that really shouldn’t be—they work best unattended), the room should be locked whenever no one is inside.
Being careless with your wireless network—Wireless networking is convenient and helpful, but the standards were not developed with security in mind. Someday, this is likely to improve. We’re not there yet.
After you have ruled out these common problems, you’re on to the real problem. How can the bad guys attack your machine? What can people access from the outside? This comes down to the question of what applications and services face the Internet, and what ports do they run on?
The best way to find answers to these questions is through the Nmap networking utility. This little tool will scan the ports of any machine on your network, or all of them, and tell you which ones are open at that moment. Any service you have installed that responds to Nmap’s query is pointed out, and you may, in turn, choose to lock down ports that should not be open.
SUSE Linux does not install Nmap by default, but you can install the command-line version and a GUI front-end called Nmap-gtk through YaST. Other GUIs are available at the Nmap website, http://www.insecure.org/nmap.
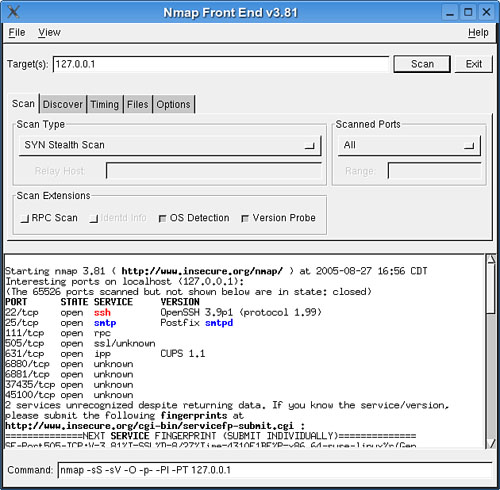
Although you can use the shell version, it is much easier to configure and see the results of Nmap’s work in the GUI (Figure 23.1). It is also better to run Nmap as the SuperUser, because you will get more information that way. To launch Nmap-gtk, log in as the SuperUser and type xnmap &.
The best way to run Nmap, especially the first time, is to use the SYN Stealth scan (on by default when you launch it as SuperUser) with OS Detection and Version Probe on. By default, Nmap scans the localhost (127.0.0.1), but you can add or change targets by typing the IP address(es) into the Target(s) edit box. The first time you run Nmap, you should click the Scanned Ports box to change the scan range from a few default ports; select All from the drop-down menu. This scan takes a little longer, but gives you a more complete picture of your status. As you adjust your options in the GUI, you’ll see the actual shell command being built at the bottom of the window. You could, if so inclined, copy this command to a text file and run it as a shell script later on.
When you have made your selections, click Scan. Nmap tests each port to determine whether it responds. If it does, Nmap asks the application at that port for version information and displays that to the Nmap screen. You then get results like those displayed in Figure 23.1. Ideally, there will be no surprises on the list. If there are surprises, or you decide that there are some unnecessary services on the list, you can take action.
You can log your Nmap scan by going to Save Log in the File menu and choosing a location from the menu. To view the log file later, go to Open Log from the File menu.
If you just have one or a few machines on the network, you probably need to run Nmap only once a year, or if you suspect your system is compromised. Sysadmins of larger networks should run Nmap regularly as part of their general maintenance regimen.
Caution
Peer-to-peer file sharing networks such as Gnutella and BitTorrent usually require you to open ports on your firewall to speed up, or even access, the network. Recognize that you may be compromising your security when you participate in these networks. Be wary when downloading files from these sources. although as of this writing, no significant worm has propagated itself through peer-to-peer networks, it could easily happen. Not every file with a certain name contains the content you may be expecting after you get it downloaded.
After you have disabled all the unnecessary services on your system, what remains is a core set of connections and programs that you want to keep. Don’t think you’re done, though. It’s time to consider what to do about your wireless network and the physical security of your servers.
Wireless networking under the 802.11 standards is not built with security in mind. The practice of wardriving, where folks drive around with wireless-equipped laptops looking for a hotspot, tells you most of what you need to know about the security of the average wireless network. It’s one thing to use random wireless hotspots to surf the web on the road, it’s quite another to intercept packets of data transferring across someone’s wireless network. This is potentially a serious problem that you need to be concerned about. Great progress has been made in the last few years, but this problem has not been solved yet. If an attacker is in your neighborhood and knows the frequency that your network uses, you have a nightmare on your hands. It should also be noted that the encryption standard of most wireless NICs is weaker than you need and should not be considered part of your security plan.
Tip
Whenever you are running on a wireless LAN, always run Open-SSH tools to protect yourself and your data. SSH passwords are not transmitted as plain text, and your sessions are encrypted.
This is especially true if you are accessing public WiFi access points. Many hosting providers don’t (or haven’t until recently) provided secure email, and your username/password combination is sent in plain text across the network every time you check your mail.
If you have your own network, it should be secured with the Wired Equivalent Privacy (WEP)algorithm. You not only want to protect your personal workstation/desktop/whatever information, but you also want to protect your credentials on any servers you connect to.
Whether or not your network is wired, the better the physical security of your computers, the more secure your network will be. Keep wireless transmitters (routers, switches, and the like) as close to the center of your building as possible. Do your own wardriving around the building to see if anyone just walking around can access your network, and shut things down tighter if you can.
It does not take much to hook up a wireless access point to a legitimate network hub, and then whoever sets up that point can compromise your entire network. Be wary and scan for them regularly.
This is one of those messages that it’s difficult to emphasize too much: Secure passwords and secure machines are the first line of defense against electronic break-ins. Follow the password rules outlined in Chapter 19, especially if you’re the Root user. Having access to the Root account is the holy grail for an attacker. Protect that account and that password with everything you have. Enforce the password standards mercilessly on your users as well.
If you are the sysadmin on a company SUSE Linux server, be aware that changes in people’s employment status can create problems for you. Former employees are often the source of attacks on servers. Have a policy in place for what happens to user accounts when someone leaves your company. That policy need not be draconian, but it should be fair to all concerned. Make sure everyone knows what it is, and enforce it consistently.
If you connect to the Internet, even with a modem and dial-up connection, you need a firewall to protect you from attack. Fortunately, SUSE Linux includes an excellent firewall to help you. Go to YaST Security and Users and click the Firewall module to start the process.
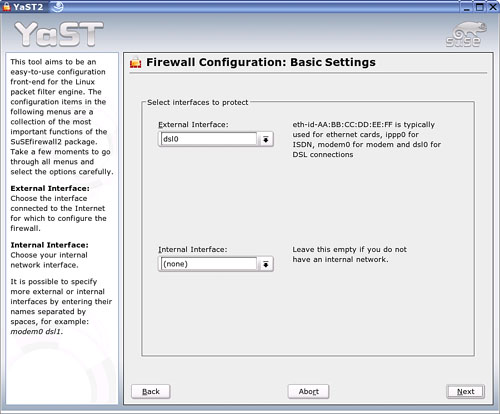
The first screen in this wizard (see Figure 23.2) asks for the interfaces you want to protect.
The External Interface is your Internet connection. The Internal Interface is your LAN card. Use the drop-down menu to select or change an interface from the default. Click Next to continue.
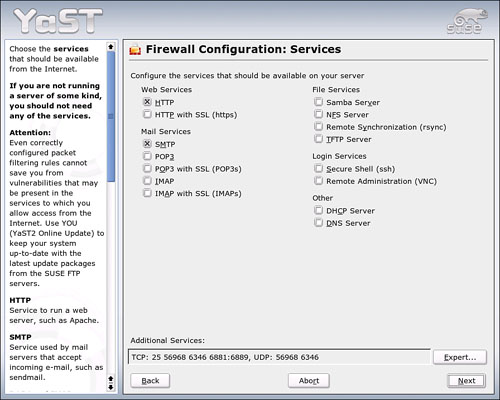
The second wizard page (see Figure 23.3) is used mainly for systems with active server components that need ports open to communicate with their clients. If you are using a web server (Apache or similar), a mail server, or any other server on the list, check the appropriate box.
Note
If you install a server package through YaST Network Services, the install wizard will always ask you to open the firewall so it can function properly.
If an Internet application needs a specific port opened, you can click the Expert button to open that port.
Caution
Anytime you open a port in your firewall, remember that every open port is a “hole” you are drilling that an attacker can breach. There are always good reasons for opening a port. Make sure you have a good reason before you drill the hole.
Click Next to continue.
The Features page comes up next. Going with the defaults here is usually best. If this machine is only going to be a router, check the Forward Traffic and Do Masquerading box. If you want other computers on your LAN to have only the same access to services on your computer that the rest of the Internet has, check Protect from Internal Network.
The last screen sets up what information the firewall logs contain. Unless you are trying to troubleshoot a specific problem, it’s a bad idea to log every packet, or even every dropped packet. Stick to the defaults here. Click Finish to activate the firewall.
The configuration file adds a script to the boot process so the firewall loads each time you boot. To turn off the firewall, reopen the module and select Stop Firewall and Remove from Boot Process.
In addition to the tools mentioned thus far, you should also consider adding some basic Linux security tools to your toolbox. These include the following:
Tripwire—This is one of the best file system monitoring tools around. It records information about important files (such as checksums) in a database. If anything changes in those files, Tripwire will catch the change when it runs (configure it as often as you like with cron) and will alert you. More information on Tripwire can be found at http://www.tripwire.org.
Snort—This is a sniffer that monitors network packets and can be used to alert you to suspicious activity. Acting as an intrusion detection system, it can offer you the first warning that a possible attack is underway. More information on Snort can be found at http://www.snort.org.
PortSentry—Like Snort, PortSentry acts as an intrusion-detection system by looking for suspicious activity. It differs from Snort in that it tries to find this activity by focusing on attempts aimed at the local computer and not on the network as a whole. It also offers the capability to block ports, and thus functions as a firewall as well. More information on PortSentry can be found at http://sourceforge.net/projects/sentrytools.
Humor books aside, it is never fun trying to come up with worst-case scenarios, and it’s even less fun trying to figure out how to survive them. Thinking about the day someone breaks into your carefully protected, what-seemed-secure network and compromises your system is harder still. Yet thinking about it ahead of time can ease the stress of that day and can also put that day further into the future.
You can take courses and even get certified in disaster recovery management, also called business continuity. So the suggestions offered here just scrape the surface, but following are some ideas to help you think out and plan for the day that no one wants to come—and how to survive and recover from it. The job you save may be your own.
Don’t just shut the network down. If the attack has ended, you let the attacker know you’re on to him by yanking the cord. Give the security team a chance to catch the perpetrator if he returns.
Not everyone needs to know you’ve been attacked. If the attack came from inside, it wouldn’t be a good idea to tell all the employees.
Head over to http://www.rootkit.nl/projects/rootkit_hunter.html and pick up a copy of the Rootkit Hunter. Rootkits are programs attackers leave behind so they can mess you up again. They are designed to hide themselves, but this application can help you find them. The bad news is that if a rootkit is found, you have to wipe the machine and start over.
After you’ve thought about it and decided the compromised machine is not really required on the network, take the machine offline. You may decide that the chances of your attacker coming back are slim, and so you don’t want to try luring him back.
Start reviewing your log files, and store them somewhere else. Because log files can be edited—they are just text files, after all—there may still be useful information in them that can help you track down the attacker.
Check
/etc/passwdfor unauthorized users. Although you should be usingshadowto store your genuine user passwords, invaders often create new users in/etc/passwdin hopes that some applications just check that file to confirm permissions. If you see a user you don’t recognize or can’t verify, remove it immediately.Run
lsofto obtain a list of open files. The–poption can be used to specify a process ID number (such as a suspected user’s shell) to limit the display to only those open files associated with them.Run
ps auxto check for unusual programs running on the system, and watch yourcronjob listing, too.Check on
/srv/wwwand make sure all your web pages are present, accounted for, and unchanged.Check the contents of
.bash_historyin each of your user’s home directories. Look for attempts to log in as the SuperUser or Root. If you find them, don’t put that user under suspicion automatically; that user may have just been the unlucky account the attacker reached.If you have a prior relationship with a security company, call them in right away. They can find things in the log files that an untrained observer won’t.
Bring those backup tapes back and start checking them. Just because you noticed this attack doesn’t necessarily mean it was the first time.
If you haven’t done so already, develop a more formal disaster recovery plan !
It’s no surprise that computer security is a hot topic on the Web. You can find a lot about it in the technology news sites and most Linux-oriented news sites as well. Two sites you should be familiar with are
LinuxSecurity.com—This is primarily a news service that scours the web for security-related information and commissions articles for its site as well. Every Monday morning, you can get the Linux Security Week newsletter in your inbox, with all the security warnings issued in the previous week so you can keep your system safe. The site also hosts Security HOWTOs, a glossary of security terms, and the comments and forums you expect on a PHP-driven website.
SecurityFocus.com—Possibly the best general site on computer security and the host of the famous BugTraq mailing list. This extremely high-traffic list is often the first place the public learns of newly exposed application vulnerabilities. They also host a Focus on Linux list and offer an RSS feed for its news content and vulnerability announcements.
To keep up with the latest security updates for SUSE Linux, keep your SUSEwatcher application in your desktop taskbar, too. This will help you keep your system as secure as the SUSE/Novell engineers can make it.
http://www.insecure.org/nmap—The
Nmaphome page. There is a lot of general information about network security here, as well as official and user-generated documentation.http://www.rootkit.nl/projects/rootkit_hunter.html—Analyze whether an attacker left behind tools to wreak more havoc on your system.
http://www.securityfocus.com—Keep up with security issues on all platforms.
http://www.linuxsecurity.com—Focus on Linux security problems and solutions.