Chapter 3
The Synergy of Knowledge Management and Competitive Intelligence1
3.1. Introduction
The capitalization of knowledge is an essential condition to ensure the growth of organizations and their continued viability. It cannot be separated from human agents. Knowledge of individuals or groups of individuals and of their actions constitutes a precious resource, a resource that should be preserved to optimize the realization of organizational aims. These aims are often manifested in the form of decision-making problems. Decision making starts with the adoption or construction of a decision strategy, followed by controlled progress until the decision is made. It is therefore essential for any organization, institution, or government to define and attain strategic means of reinforcing the decision process. This work aims to design and develop user-centered methods for knowledge management (KM) to assist in tactical and strategic decisions concerning processes in organizations.
Competitive intelligence (CI) emerged as a specialized domain offering tactical and strategic processes for decision making. In this context, the approach of facilitating decision making differs from the conception of shared decision support systems (DSS). Most DSS focus heavily on the technological dimension. Furthermore, CI aims to facilitate decision making by recognizing the fact that automated products can be used as a complement to human intervention. In the context of CI, an efficient decision process is the product of coordinated action between human actors. The process also concerns the activities involved in obtaining relevant and validated information to satisfy the needs of the organization. Precious resources, both human and material, are involved in the process of facilitating strategic decision making. For example, the competences of an actor responsible for the analysis and structuring of a decision-making problem, or of the person responsible for research, are human resources. Material resources may take the form of documents, information, and so on. These resources act as triggers in attaining organizational goals, and more specifically in obtaining an advantage over competitors. Consequently, material resources should be stored to capitalize and use them in resolving future problems. This requirement falls into the domain of KM.
Knowledge is defined as an indispensable resource in acquiring advantages in terms of competition and innovation. Publications in this domain [POH 00, MIL 02] distinguish between data and information. As information is essential to the operation of the organization, so knowledge is also an important economic asset for organizational productivity. This statement is justified by the use of information in research and development (R&D), in industry, and so on. Effective information use of this kind is made possible by applying KM methods. A system must be put into place for the organization, conservation, and transmission of existing knowledge, whether factual or implicit, and it is vital to anticipate needs in terms of new knowledge. Consequently, KM strategies are essential in the context of CI. These two notions are linked in the matter of processing information and knowledge.
3.2. Theoretical context
We will provide a brief overview of our field of research over the following sections.
3.2.1. Definitions of knowledge
Several definitions of knowledge may be found in published literature on the subject. From a philosophical viewpoint, knowledge is defined as a justified, true belief. However, belief is defined as a mental attitude or a state of mind, personal conviction, or acceptance of a particular fact or idea. Most contemporary philosophers instead use the term “propositional belief”. Belief may not be considered to be knowledge simply because it concerns a decision [EDW 06]. Moreover, Blackburn [BLA 99] suggests that no form of belief may be considered to be knowledge. Thus, in epistemology, it is defined as a perception or observation of an object or event, or as experience exercising a particular activity. Knowledge is seen as a form of capital that has an economic value and constitutes a resource of strategic importance in increasing productivity [MAT 02]. In [STA 89], Stata describes knowledge as the main source of wealth in industry and traditional sectors of the economy. We will conclude by noting that knowledge refers to the meaning transmitted when information is placed into context, with reference to the environment or associated events. Different types of knowledge exist, which have an impact on the method necessary for capitalization.
3.2.1.1. Types of knowledge
Knowledge can be broken down into classes, whether explicit or tacit or theoretical and practical [NON 95]. Explicit knowledge may be expressed in the form of a theoretical or practical experiment. It may be transmitted easily, formally, and systematically, via individuals. Tacit knowledge, on the other hand, is a form of personal competence and is difficult to formalize or share with other actors. Tacit knowledge needs to be transformed into explicit knowledge, rendering it representable and useable in a KM system.
3.2.2. Competitive intelligence
The decision-making process involves three kinds of images: values, aims, and plans. The image of value is a representation by decision makers (or DMs, economic actors who initiate decision problems (DPs)) of beliefs, values, and opinions on what is appropriate. The aim image is a representation of the DM’s vision of what should be attained. The plan image is a representation of actions and results [DAV 03]. CI provides a platform for the integration of these DM images to provide a basis for the resolution of DPs.
Information is required at different stages of a decision process in a company or community to develop and implement a coherent strategy and the tactics necessary to attain objectives set by the business, with the aim of improving the position of the company in relation to its competitors. CI emerged as a process to fulfill these needs. At single-company level, CI may be defined as the capacity of the DM to make good use of new knowledge and experiences, while reusing existing knowledge and experience, to resolve a DP as successfully as possible [KIS 02]. It is “the set of coordinated research actions, processing actions and the distribution of information to economic actors in the aim of using this information. These various actions are carried out legally, with all necessary guarantees to protect the capital of the company, within the best time and cost conditions” [MAR 94]. CI seeks to develop methods for the identification of relevant sources, analysis, collection, and use of information to respond to the needs of users in making decisions. There are four main types of actors involved in the process:
– The DM formulates an exact description of the DP.
– The watcher localizes, supervises, validates, and specifies the strategic information needed to solve the problem.
– The information systems analyst analyzes the information gathering process to understand its impact on company or institutional strategy.
– The project coordinator acts as a link between the DM(s) and other actors [KNA 07].
All actors cooperate to optimize the sharing of strategic knowledge. The CI process is a systematic approach in which seven steps are taken to solve a DP. [BOU 04a], following [BOU 04b], it includes the phases presented in Figure 3.1.
Figure 3.1. CI process
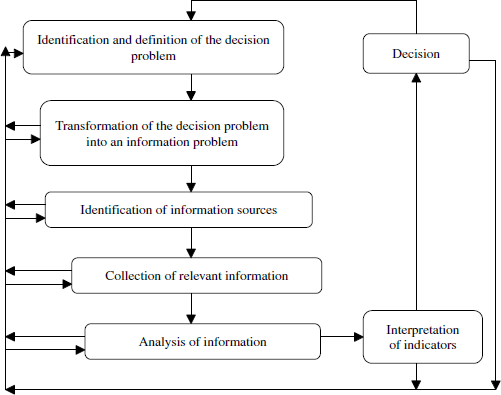
Each step in the process may be traced back to the validation phase. What follows is a list of some existing models for the representation of knowledge in relation to the CI process:
– the Model for Explicit Definition of Decision Problem (MEDP) [BOU 04b];
– the Watcher’s Information Search Problem (WISP) model [KIS 07];
– the Model for Information Retrieval query Annotations Based on Expression (MIRABEL) [GOR 06];
– the Model for Representation of Information Search Problem in Economic Intelligence (MORPRI2E) [AFO 07];
– the Annotation Model for Information Exchange (AMIE) [ROB 07];
– the Representation of User’s needs at the time of Interrogation of Information system (RUBICUBE) model [PEG 06];
– the Specification of the Competence of the Coordinator of Regional EI (CADRIE) model [KNA 07].
The first phase of the CI process involves the definition of a DP and the analysis of its context in terms of internal and external environmental factors that impact upon the organization. The DM (or manager) applies the MEDP model in defining the DP. Their profile and the internal and external environment of the organization are then analyzed. Consequently, stakes are expressed and hypotheses formulated, showing risks or threats (things that stand to be gained or lost) in relation to the DP. MIRABEL is applied to validate the activity so that the project coordinator, DM, and watcher can check concepts while connecting them to laws or theorems to clarify the supposed stakes. Hypotheses are examined to confirm the elements to which they correspond according to the context of the organization. This provides the watcher with a better understanding of the information needs of the DM (by applying the WISP model). The DP is transformed into a precise and sufficient information problem that assists in identifying the most relevant sources of information. The watcher, in collaboration with the information systems analyst, begins a process of research, collection, and analysis of information. The MORPRI2E assists in the acquisition of relevant information according to the context of the demand. The AMIE model facilitates traceability using annotations made by the actors (editors/commentators) linked to a piece of information. The project coordinator and the DM(s) validate results and information indicators in relation to the DP before any decision is made. Knowledge capitalization (KC) is required for all actors during all phases of the CI process.
Models for CI are proposed separately. To exploit the experiences and results gained from past DPs, we must integrate and represent these models. We will consider the KM approach in CI as being based on the roles of actors in the CI process.
3.2.3. KM in CI
The explicit and tacit knowledge present in an organization must be captured and stored to facilitate access, sharing, and reuse of this knowledge. KM involves all of these activities. Reference is occasionally made to KC, but the two phrases are often used interchangeably. In a subtle way, KC is the major service provided by KM, as stated by Dieng-Kuntz and Matta: “Knowledge Management is a global process in the enterprise, which includes all the processes that allow capitalization, sharing an evolution of the knowledge capital of the firm” [DIE 02].
KM allows us the knowledge present within an organization to be capitalized in a way which permits its reuse in connection with future problems. To be capitalized, knowledge must be stored in databases or repositories often known as “corporate memory” (CM) or “organizational memory”. CI requires the integration and reuse of knowledge from past and ongoing projects to help with the strategic decision-making process. The application of KM principles and techniques to CI, in this research, prevent the loss of individual or collectively acquired knowledge. Throughout all phases of the CI process, such knowledge, by its acquisition, organization, integration, and preservation, may be used, reused, and distributed to different economic actors, such as DMs, research specialists (watchers), or project coordinators.
KM has been applied in several domains of activity, of which we will consider a number of examples in the following section.
3.2.3.1. A generic model for CM: application to industrial systems
Admane suggests that industrial activities should be represented in the form of “cases”, producing reusable resources with roles dependent on the context, considered with assistance from models to allow KC within a context of systematic reuse. The aim of this project is to assist the designers of future industrial systems to transform tasks as quickly as possible to contribute to the design phase [ADM 05]. The system model takes into account two types of knowledge: knowledge linked to abilities and themes of knowledge. Knowledge linked to abilities refers simply to the basic capabilities of the company. Themes represent domains of knowledge. The component parts of a theme refer to specifications for product installation and are modeled from graphical and textual descriptions. The name of the CM model is ReCaRo (Resource Cases and Roles): it has a multiple-memory architecture containing sets of five memories. The model was validated by use in a renovation, maintenance, and extension project in a hydrocarbon transport network. All experiments carried out and all the knowledge acquired throughout the different phases of the project were capitalized.
Organizational memory is a set of models and resources, used in the form of a set of databases. The reuse principle is based on the collection (inventory) and classification of roles and resources. As mentioned above, KM deals with both tacit and explicit knowledge. We acknowledge that this work is limited as it only covers the acquisition of explicit knowledge, that is, knowledge concerning industrial products and processes. It does not take the tacit knowledge of employees of the organization involved in the project into account. However, the use of case-based reasoning (CBR) techniques facilitates the organization of saved solutions and simplifies access to the required knowledge.
3.2.3.2. KC in an equipment repair and diagnostics system
The aim of this system was to create a specialized CM for maintenance services [CHE 05]. A model was developed by Grundstein [GRU 94] to describe the KC cycle for a given application, as illustrated in Figure 3.2. The cycle shows the four phases applied for an e-maintenance system according to Brigitte et al.:
– Information detection: the practices of maintenance experts in repair and diagnosis in industrial zones were observed. Observation was combined with an analysis of the maintenance process presented in [RAS 04].
– Classification of knowledge: the design of a system of this kind demanded the application of appropriate tools for modeling knowledge.
– KC: capitalization was carried out based on a maintenance platform developed by project partners specializing in information technology. The platform was used as a medium for the diffusion of information. Web services were developed to take the acquisition of knowledge into account depending on the expertise considered.
– Knowledge update: this step was carried out using a CBR method. Access to the diagnostic service was opened up to all maintenance actors. Modifications that might be carried out on this knowledge were validated using the authority of experts, designated by theme.
Figure 3.2. KC cycle [GRU 94]

The system is modeled by a Web portal architecture, assisted by a CBR tool. The CBR module uses Belfort’s site ontology in addition to the generic maintenance ontology. A new problem was processed from saved cases, chosen following criteria of similarity with the problem considered. The solution suggested by these saved cases was adapted (or reused) based on the new situation and tested to increase its chance of success.
This approach is similar to our proposals as it also uses a CBR system in the context of a working memory destined for cooperative use. The evaluation and evolution of CM based on the reuse of knowledge were not included in this system.
3.2.3.3. Knowledge acquisition and modeling for CM: lessons learned
This project was put to use in the field of metallurgy, with a focus on characteristics of knowledge reuse from capitalization systems. This knowledge reuse supplied general methods, tools, and techniques [SIM 96]. It permitted storage and reuse of knowledge and abilities within the company concerning descriptions of steel production and metallurgical problems arising during this production. The technique chosen for use was CBR. The first phase of work involved the creation of common synthesis documents covering all geographical sites of the company. The uniform format used in these documents allowed the development of a communication medium for the group of experts involved. The second phase focused on the use and diffusion of the set of models of synthesis documents for the implementation of the CM of the information system. The author proposed a general system architecture that supports representations of CM to allow reuse of capitalized information based on the fact that the architecture establishes a set of general constraints induced by all capitalization systems according to [CAU 95].
3.2.3.4. Software engineering for KC using CBR: case structure
The main task carried out involved the capitalization of experience created by software engineering projects through the construction of CBR systems. The main case study used was named “intelligent computer-aided design for information systems” (Conception intelligente assistée par ordinateur de systèmes d’information) [NGA 04]. The authors specified two types of knowledge: knowledge of software artifacts and knowledge of the development process. The artifacts represent information and models generated during the development of a given program, including all steps of the software development project and knowledge relating to bridging activities. The knowledge considered was essentially explicit in nature. The case structure used to represent and store knowledge for a project was developed using a software life-cycle model [BOU 01]. The case structure was modeled in the form of a relational, hierarchical, and object-oriented database. The authors simply improved the representation of knowledge produced during different steps of the design process. Other knowledge concerning the exploitation and evaluation of software, also linked to the problem of KC, was not processed. Thus, the authors focused on the technological dimension alone; however, KM also involves social and cultural aspects linked to the final users of the product, the information system or the design system.
3.2.3.5. Information security systems and KM
Belsis et al. [BEL 05] focus on the identification of certain dimensions: types and sources of knowledge inherent to activities associated with an information security system as a basis for the development of a specialized KM system. The authors discuss factors of motivation affecting KM needs associated with the security of an information system. They propose a model for illustrating the knowledge structure of an information security system. This model describes explicit knowledge in the form of security policy and instructions. The developers of the model refer to the introduction of broad guidelines to assist staff in making decisions affecting the security system. In addition, steps taken later on indicate the security strategies of members of the organization. The third component of the model concerns “measures”, that is, specific actions required for the installation of the information system. The model also covers risk analysis for the implementation of the system. The knowledge identification and acquisition method is based on person-to-person contact or on expert opinions. The authors also propose a “knowledge-capture” function for the documentation and analysis of knowledge in case of incidents, but which does not disturb the work of security experts.
In conclusion, this model offers less improvement in terms of knowledge sharing and exploitation techniques among the employees considered. Moreover, the project only covers a very specific domain of KM, that of information security.
3.2.3.6. Business process modeling through KM
In this section, we will provide an overview of a research project considering the role of business process modeling (BPM) as a KM tool [KAL 06]. This project fits into the context of the broader issue of accounting for and understanding an increasingly complex environment, with mounting national and international competition, where the rapid development of technology often means that growth is proportional to the demands made by a company’s current and potential future clients.
Another important reason that justifies interest in BPM concerns the considerable potential advantages an organization stands to gain from the explanation and formalization of its knowledge and abilities to exploit, communicate, and/or locate this knowledge more effectively. BPM involves the description of business processes (all relevant processes involved in the creation of added value), which constitute a base of available and potentially exploitable knowledge throughout the production system of the business in question. Authors who have worked on this question affirm that BPM may be considered a KM tool, as it allows tacit knowledge to be identified and converted into explicit knowledge throughout the process. Their approach focuses on the creation of networks of concepts, in which BPM concepts are categorized and linked to other concepts relating to the life cycle of products and services associated with the Business Process (BP). BPM concepts are categorized by activity and “behavior models”.
These researchers developed a theoretical framework to illustrate how BPMs capture and allow sharing of knowledge associated with business processes. They propose a model for a KM process, which relates to the externalization and internalization of knowledge of two participants in a process (tacit knowledge); this is then transformed into artifacts (explicit knowledge). They also highlight the impact of culturally shared knowledge (e.g. knowledge shared by a community) for the understanding or interpretation of a formal process model. This research work recognizes the capitalization of technology knowledge concerning and takes account of social and cultural questions. However, the scope of the written work concerning this research is limited to business processes and the fact of making explicit knowledge available. For the moment, no evaluation of exploitation seems to have been taken into account.
3.2.3.7. KM: planning for the future
In this section, we will consider [RAN 06], which highlights the necessity of protecting knowledge in KM systems. The author of the work defends the idea that knowledge acquired in the KM system should include security measures and policies that allow access to and use of this knowledge to be controlled. He makes a distinction between the security of knowledge and data security and considers that knowledge is dynamic in nature and that a demand is non-deterministic.
Based on this idea, the author proposes an implementation of security levels for different identified types of organizational knowledge. The functions proposed for all secure KM systems are as follows:
– creation or reinforcement of trust among organization personnel, creating a culture of knowledge sharing;
– protection of main knowledge assets;
– monitoring knowledge transfer;
– eliminating risks of imitation by competitors.
This structure focuses on technical aspects (artifacts) to best identify the most appropriate knowledge and its source(s). For example, knowledge linked to the evolution and use of a document belonging to the organization may be protected by artifacts such as a secure connection, verification of the information involved, and so on.
In the case of moderators in discussion forums, these artifacts may take the form of time stamps and identification of authors of sources of annotations, and so on.
This research work focuses essentially on the security of KM systems rather than on their implementation.
3.2.3.8. KM in industry and government: security versus sharing
Zannes [ZAN 00] discusses the security requirements of an organization in relation to knowledge assets. The author picks up on the reluctance of government agencies and national laboratories to install KM systems, for fear of the risks involved in knowledge sharing. It highlights the following points associated with organizational security:
– use of copyrights in digital products or other documents in the industrial publication process;
– installation of KM systems for secure networks;
– use of secure ID cards for internet access and distance knowledge sharing;
– long-distance maintenance of Web sites and databases, that is, from outside the organization.
In the conclusion, Zannes [ZAN 00] recommends that trust in the tool and in individuals should be estimated when sharing knowledge. This work highlights a major demand concerning the installation of KM systems. However, it does not go into detail concerning the stages of planning and development of such a system.
3.2.3.9. KC in research and design projects: an integrated and diversified approach
Simon [SIM 03] is concerned with KC methodology and considers lessons learned from the observation of design projects in a multinational company to formulate a theory regarding the impact of social and organizational factors on KC in this context. The author looks at different dimensions of knowledge, such as its social, organizational, and cognitive aspects. The work includes an analysis of the diversification of dimensions of knowledge in KC practices.
To do this, the author took the general methodology for management of systematically assembled and analyzed data set out in [STR 94] as a base. The approach was based on the iterative analysis of data produced by case studies (supported by opinions from the research and study office) and may be used in conjunction with the theory of CBR described in [EIS 89].
This study aims to evaluate different KC methods used in R&D projects and the factors that affect KC practices.
3.2.3.10. Overview: classification of works
The publications described above may be split into three distinct categories: methodologies, applications, and principles of KM.
Methodologies refer to the structure and organization of knowledge and knowledge transmission during the different stages and tasks involved in KC.
KM principles concern characteristics (or functions) recommended for the development or implementation of KM systems.
Applications refer to KM systems developed for specific domains. Tables 3.1, 3.2, and 3.3 provide a synthetic presentation of these three categories.
Table 3.1. Evaluation of KM methodologies

3.2.3.11. Evaluation criteria for methodologies
– User oriented: this indicates whether or not the needs of users guide the main aims and operations of the KM system.
– Adaptability to different domains: criterion for flexibility of the structure of the KM system enabling application in other domains.
– Dating: this indicates whether or not the system attaches dates to knowledge, introducing temporal contextualization.
– Feedback on reused knowledge: indication concerning the evaluation of relevance of knowledge used, guaranteeing the evolution of the KM system.
3.2.3.12. Application evaluation criteria
The following list provides a summary of evaluation criteria for KM applications, as described in Table 3.2:
– Specificity of the domain: this represents the application object of the KM system as, for example, its adaptability to other domains.
– Type of knowledge: typology of knowledge identified for capitalization.
– Main technological focus: this shows the high dependence of the system on the technological infrastructure and on techniques involving little or no human intervention.
– Socioeconomic target: economic orientation of the KM system.
– Respecting and adapting to the culture of the domain: involvement of rules, languages, and standards present in an organization or group of individuals.
– Level of socialization: the weight of human interaction in the explanation, acquisition, and sharing of knowledge.
– Representation and exploitation of temporal attributes: integration of spatiotemporal data on knowledge managed by the system and reasoning concerning these attributes.
– Evaluation of reused knowledge: evaluation of the relevance of knowledge used while solving a new problem.
– Dynamism: continuous research and recording throughout the new problem and contextualization using a rate of relevance for knowledge used.
Table 3.2. Evaluation of KM systems

3.2.3.13. Evaluation criteria based on principles
The principles of KM are evaluated using the following criteria, as set out in Table 3.3: focus, the main slant chosen by authors; strength, the contribution made by the recommended principles; and limits, other, less developed constraints of the KM system.
Table 3.3. Summary of principle-based evaluation

3.2.3.14. Summary of evaluation of KM methodologies, principles, and systems
We note that three particular functions are less developed in existing work on the subject:
– orientation toward use,
– temporal attributes,
– integration of feedback.
These functions would provide the following benefits if used in a capitalization system:
– satisfaction of user needs,
– generation of procedural knowledge for a new problem,
– facilitation of knowledge development through the analysis of feedback from knowledge reuse.
There is a need to identify, acquire, and record all knowledge involved in a CI project and the capabilities of actors. This must be converted to explicit knowledge to allow representation for capitalization. CI models are used to represent the procedural knowledge of actors. These assist in the transformation of tacit knowledge into explicit knowledge. These models must be integrated to form a single model to capture and record knowledge in a decision-problem resolution project. We will apply the principles of KM to capitalize on and date knowledge, thus facilitating the decision-making process. The first stage in this process is to identify and acquire knowledge.
3.3. Knowledge acquisition strategy
Our methods for the acquisition of knowledge generated by a CI project may be classified as follows:
– Studies of CI models: these models represent knowledge concerning the activities of each actor.
– Rendering actor knowledge explicit: observation of activities and interactions of actors.
– Real-time identification of knowledge applied during different phases of the decision-problem resolution process (e.g. the definition of stakes of a DP, specification of a research problem, and information sources).
3.3.1. Action-based knowledge acquisition
In this case, the acquisition strategy takes users into account. A DM may, for example, initiate a DP by expressing a problem or an initial demand, its context, the time frame, and so on. Our approach aims to help actors to concentrate exclusively on what is relevant for them at a given moment. Consequently, the provision of information and knowledge suitable for the problem becomes their sole focus. Appendix A shows a process of knowledge acquisition based on the roles of actors, implemented using a prototype knowledge repertoire devoted to CI.
3.4. Formalization of knowledge
Our approach to the formalization of knowledge identified as resources in the context of CI is as follows:
– a structure for KC for CI projects;
– an architecture for the representation of CI knowledge;
– conceptual and relational modeling of knowledge.
3.4.1. KC structure for CI projects
Our approach consists of designing an adaptable structure (Figure 3.3) for the capitalization of CI projects. For example, problem domains that require the solution of various management problems may properly be taken into account. The structure acts as a platform for the development of a knowledge repertoire.
Figure 3.3. Model for KC in CI projects
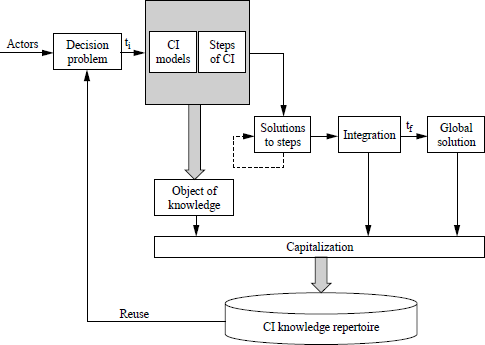
The heterogeneity of existing models is a factor, which must be taken into account and which poses major difficulties in this work. Currently, we must deal with models designed entirely independently, with the exception of the WISP model that includes part of the Model for Explicit Definition of Decision Problem (MEDP) model. However, all models include shared references to economic actors involved in a CI process. Consequently, we suggest that models should be harmonized to facilitate direct acquisition and use of knowledge from a system.
The general structure proposed shows the different components that feed into the capitalization system and the relationships that connect them. Actors present a DP at a given moment. Their problem-solving activities, based on models, are identified and recorded. The solutions produced are also recorded, with reference to the time frame, and integrated into a knowledge repertoire.
The knowledge repertoire, used to represent and organize knowledge, is modeled using a conceptual model that takes account of relationships.
3.4.2. Architecture for KM in CI projects
Figure 3.4 shows a possible architecture for the representation of knowledge in the context of CI. Our approach consists of modeling the above framework from the point of view of the user, to respond to the questions: “who” does “what”, “when”, “why”, and “how”. The architecture presents a platform for the presentation of knowledge with timestamps for decisions in a CI decision project. This facilitates the generation of implicit inferences in reasoning concerning temporal properties (marked t for timestamp, and i, l, and f, for the initial, later, and final phases, respectively) of knowledge resources. We will illustrate the application of the architecture to a decision-making problem scenario in Appendix B.
Figure 3.4. Architecture for a CI knowledge repertoire
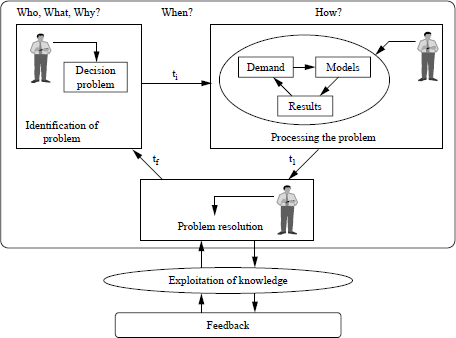
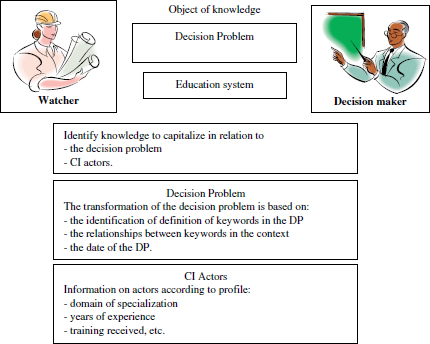
3.4.2.1. Case study of a DP: moral decadence among young people
This framework provides a model for KC for case studies. The objects of knowledge of actors in the CI process are identified and acquired using different models. The following scenario provides an example of knowledge objects in the first phase of the CI process.
3.4.2.1.1. Scenario
The DM presents the DP as concerning moral decadence among young people.
– the context of the DP is the education sector in Nigeria;
– understanding the DP: what does the DP mean?;
– the terms or concepts of the DP are defined by the DM as follows:
- morality refers to principles or rules of correct behavior;
- decadence is a state of moral decline;
- moral decadence implies a state of decline or deterioration in conformity to the principles or rules of correct behavior.
Thus, moral decadence among young people implies a state in which adolescents, or the general teaching college, present a decline (reduction) in the respect of rules (authorities) for correct behavior among individuals (of the population).
Definition of the interest of the DP:
– object: moral decadence;
– signals: unauthorized absences, violence, crime, and immorality;
– hypothesis: if moral decadence among young people is not restrained, then there will be:
- a high school dropout rate;
- bad signs for the future leadership of the country;
- a social threat.
The meanings of the DP are thus interpreted by the watcher. The two actors evaluate their individual points of view and finally agree on a specific definition of the DP. Appendix B shows the knowledge objects to harness in relation to the first phase of the CI process. Later, these knowledge objects may be reused in solving another DP.
3.4.2.2. Action-based knowledge use
The aggregation of knowledge objects in CI is carried out using a relationship-based modeling schema. This acts as a support for the classification of knowledge objects. Acquired knowledge is presented as elements in the knowledge repertoire. The architecture and the relationship model assist in organizing knowledge objects with the aim of enabling actor-centered exploration of the repertoire. An actor may explore the knowledge repertoire based on his/her role; for example, a DM may have access to stored knowledge on past projects to find knowledge and information on the identification, evolution, and definition of DPs, or on actors. We have developed a prototype, in the form of a knowledge portal, of the client—server environment to validate our research aims. The research mechanism for knowledge use is implemented using the CBR approach and Explore, Query, Analyze, Annotate (EQUA2TE). The appearance algorithm is oriented according to the role of the user. Case studies on solving DPs in the sectors of education, economy, and social issues were used to test the developed prototype.
3.5. Conclusion
The resolution of a DP using strategic CI processes, coupled with a KM model linked to the activities and capabilities of actors, should, in our opinion, render organizations more competitive. We have designed and developed KM models to assist the DM in the decision process, whether the decision is tactical or strategic. Our proposed model is user-centered and can be adapted for different types of knowledge resources within the CI process. The architecture is based on a knowledge repertoire, which harmonizes available knowledge linked to a decision project. We thus offer a basis for the acquisition and exploitation of knowledge linked to the CI process, contributing to knowledge reuse tools in terms of availability and accessibility with the aim of accelerating the decision process for economic actors.
3.6. Appendices
3.6.1. Appendix A: knowledge acquisition based on actor activities

3.6.2. Appendix B: capitalization scenario in decision making
3.7. Bibliography
[ADM 05] ADMANE L., “A generic model of corporate memory: application to the industrial systems”, IJCAI’2005: Workshop on Knowledge Management and Organizational Memories, pp. 55–66, 2005.
[AFO 07] AFOLABI B., La conception et l’adaptation de la structure d’un système d’intelligence économique par l’observation des comportements de l’utilisateur, Doctoral Thesis, University of Nancy 2, Nancy, 2007.
[ALA 97] ALAVI M., One Giant Brain, Harvard Business School, Boston, MA, 1997.
[BEL 05] BELSIS P., KOKOLAKIS S., KIOUNTOUZIS E., “Information systems security from a knowledge management perspective”, Information Management and Computer Society, vol. 13, no. 3, pp. 189–202, 2005.
[BLA 99] BLACKBURN S., Truth: A Guide, Oxford University Press, Oxford, 1999.
[BOU 01] BOURQUE P., DUPUIS R., ABRAN A., MOORE J., TRIPP L., “The emerging consensus on the software engineering body of knowledge”, SPIN-Ottawa, Ottawa, Ontario, Canada, p. 51, 18 October 2001.
[BOU 04a] BOUAKA N., DAVID A., “Proposal of a decision-maker problem model for a better understanding of information needs”, Proceedings of International Conference on Information and Communication Technologies: From Theory to Applications, pp. 551–552, 2004. IEEE, pp. 1–5, ISBN: 0-7803-8482-2.
[BOU 04b] BOUAKA N., Développement d’un modèle pour l’explicitation d’un problème décisionnel: un outil d’aide à la décision dans un contexte d’intelligence économique, Doctoral Thesis, University of Nancy 2, Nancy, 2004.
[CAU 95] CAULIER P., HOURIEZ B., “Apports de la modélisation des connaissances et du raisonnement à partir de cas à la capitalisation et la réutilisation de connaissances”, Actes des Journées Acquisition Validation Apprentissage, Grenoble, France, pp. 331–345, 1995.
[CHE 05] CHEBELMORELLO B., RASOVSKA I., ZERHOUNI N., “Knowledge capitalization in system of equipment diagnosis and repair help”, IJCAI’2005: Workshop on Knowledge Management and Organizational Memories, pp. 55–66, 2005.
[DAV 98] DAVENPORT T.H., PRUSAK L., Working Knowledge: How Organizations Manage What They Know, Harvard Business School Press, Boston, Cambridge, 1998.
[DAV 03] DAVID A., THIERY O., “L’architecture EQuA²te et son application à l’intelligence économique”, ISDM NO 11, Article No. 98, pp. 1–8, available online at www.isdm.org
[DIE 99] DIENG-KUNTZ R., CORBY O., GIBOIN A., RIBIERE M., “Methods and tools for corporate knowledge management”, International Journal of Human-Computer Studies, Vol. 51, No. 3, pp. 567–598, 1999. Also in http://ksi.cpsc.ucalgary.ca/KAW/KAW96/KAW98/dieng/
[DIE 02] DIENG-KUNTZ R., MATTA N., Knowledge Management and Organizational Memories, Kluwer Academic Publisher, Boston, 2002.
[EDW 06] EDWARD N.Z. (ed.), The Stanford Encyclopedia of Philosophy, 2006, available online at http://iplato.stanford.edu/entries/epistemology/.
[EIS 89] EISENHARDT K., “Building theories from case study research”, Academy of Management Review, vol. 14, no. 4, pp. 532–550, 1989.
[GOR 06] GORIA S., Proposition d’une démarche d’aide à l’expression des problèmes de recherche d’informations dans un contexte d’intelligence territoriale, Doctoral Thesis, University of Nancy 2, Nancy, 2006.
[GRU 94] GRUNDSTEIN M., Développer un Système à Base de Connaissances: un Effort de Coopération pour Construire en Commun un Objet Inconnu, CP2I, Paris, 1994.
[HOL 02] HOLSAPPLE C.W., JOSHI K.D., “A knowledge management ontology”, in Holsapple, C.W. (ed.), Handbook on Knowledge Management, Springer-Verlag, Berlin, vol. 1, pp. 89–128, 2002.
[KAL 06] KALPIC B., BERNUS P., “Business process modeling through the knowledge management perspective”, Journal of Knowledge Management, vol. 10, no. 3, pp. 40–56, 2006.
[KIS 02] KISLIN P., DAVID A., THIÉRY O., “A model of information retrieval problem in Economic Intelligence context”, SCI’2002, Orlando, Florida, USA, 14–18 July 2002.
[KIS 07] KISLIN P., Modélisation du probleme informationnel du veilleur, Doctoral Thesis, University of Nancy 2, Nancy, 2007.
[KNA 07] KNAUF A., Caractérisation des rôles du coordinateur — animateur: émergence d’un acteur nécessaire à la mise en pratique d’un dispositif régional d’intelligence économique, Doctoral Thesis, University of Nancy 2, Nancy, 2007.
[MAR 94] MARTRE H., Intelligence économique et stratégique des entreprises, Results of a workgroup led by Henri Martre, La Documentation Française, Paris, 1994.
[MAT 02] MATTA N., ERMINE J., AUBERTIN G., TRIVIN J., “Knowledge capitalization with a knowledge engineering approach: the MASK method”, in DIENG-KUNTZ R., MATTA N. (ed.), Knowledge Management and Organizational Memories, Kluwer Academic Publisher, Boston, pp. 17–28, 2002.
[MIL 02] MILLER F., “I = 0 (Information has no intrinsic meaning)”, Information Research, vol. 8, no. 1, pp. 1–13, 2002.
[NGA 04] NGANTCHAHA G., NKAMBOU R., BEVO V., “Software engineering knowledge capitalization using CBR: case structure”, Proceedings of the IASTED International Conference, Artificial Intelligence and Applications (AIA), Innsbruck, Austria, February 2004.
[NON 95] NONAKA I., TAKEUCHI H., The Knowledge-Creating Company: How Japanese Companies Create the Dynamics of Innovation, Oxford University Press, Oxford, 1995.
[PEG 06] PEGUIRON F., Application de l’intelligence économique dans un système d’Information stratégique universitaire: les apports de la modélisation des acteurs, Doctoral Thesis, University of Nancy 2, Nancy, 2006.
[POH 00] POHL J., “Transition from data to information”, Collaborative Agent Design Research Center (CADRC) Technical Paper, Cal Poly San Luis Obispo, CA, USA, pp. 1–8, November 2000. www.cadrc.calpoly.edu. www.cdmtech.com
[RAN 06] RANDEREE E., “Knowledge management: securing the future”, Journal of Knowledge Management, vol. 10, no. 4, pp. 145–156, 2006.
[RAS 04] RASOVSKA I., CHEBEL-MORELLO B., ZERHOUNI N., “A conceptual model of maintenance process in unified modelling language”, Proceedings of INCOM’2004 — 11th IFAC Symposium on Information Control Problems in Manufacturing, Salvador-Bahia, Brazil, 2004.
[ROB 07] ROBERT C., L’annotation pour la recherche d’informations dans le contexte d’intelligence économique, Doctoral Thesis, University of Nancy 2, Nancy, February 2007.
[SIM 96] SIMON G., “Knowledge acquisition and modeling for corporate memory: lessons learnt from experience”, in GAINES B., MUSEN M. (eds.), Proceedings of KAW’96, Banff, Canada, html page: http://ksi.cpsc.ucalgary.ca/KAW/KAW96/simon/KAW96US.htm
[SIM 03] SIMONI G., “Knowledge capitalization in research and design projects: an integrative and diversified approach”, 13th European Summer School in Technology Management, EIASM — European Institute for Advanced Studies in Management, WHU, Vallendar, Germany, 2003. Also in http://www.lest.cnrs.fr/lesdocumentsdetravail/simoni/knoledge.pdf
[STA 89] STATA R., “Organizational learning — the key to management innovation”, Sloan Management Review, vol. 30, pp. 63–73, 1989.
[STR 94] STRAUSS A., CORBIN J., “Grounded theory methodology”, in DENZIN N.K., Lincoln S.Y. (dir.), Handbook of Qualitative Research, Sage, Thousand Oaks, CA, 1994.
[ZAN 00] ZANNES E., “Knowledge management in industry and government: the conflict between security & knowledge sharing”, IEEE, 2000. Computer Security, Emerald Group Publishing Limited, vol. 13, pp. 160–169.
1 Chapter written by Bolanle OLADEJO and Adenike O. OSOFISAN.
