This chapter covers the following subjects:
Given that the title of this book is Routing TCP/IP, it is fitting to begin with a review of TCP/IP before getting into how to route it. Presumably, if you are preparing for a Cisco Certified Internetwork Expert (CCIE) examination, or have just bought this book as a routing reference, you already know most or all of the information in this chapter. But reviews never hurt and sometimes help, so here you have it.
The purpose of this chapter is to review the protocols that enable, control, or contribute to the routing of TCP/IP, not to do an in-depth study of the TCP/IP protocol suite. Several books on the recommended reading list at the end of the chapter cover the subject in depth. Read at least one.
Conceived in the early 1970s by Vint Cerf and Bob Kahn, TCP/IP and its layered protocol architecture predates the ISO’s Open System Interconnection (OSI) reference model. A brief review of TCP/IP’s layers will be useful in understanding how the various functions and services examined in this chapter interrelate.
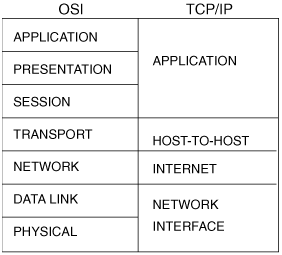
Figure 1-1 shows the TCP/IP protocol suite in relationship to the OSI reference model.[1] The network interface layer, which corresponds to the OSI physical and data link layers, is not actually part of the specification. However, it has become a de facto layer either as shown in Figure 1-1 or as separate physical and data link layers. It is described in this section in terms of the OSI physical and data link layers.
The physical layer contains the protocols relating to the physical medium on which TCP/IP will be communicating. Officially, the protocols of this layer fall within four categories that together describe all aspects of physical media:
Electrical/optical protocols describe signal characteristics such as voltage or photonic levels, bit timing, encoding, and signal shape.
Mechanical protocols are specifications such as the dimensions of a connector or the metallic makeup of a wire.
Functional protocols describe what something does. For example, “Request to Send” is the functional description of pin 4 of an EIA-232-D connector.
Procedural protocols describe how something is done. For example, a binary 1 is represented on an EIA-232-D lead as a voltage more negative than –3 volts.
The data link layer contains the protocols that control the physical layer: how the medium is accessed and shared, how devices on the medium are identified, and how data is framed before being transmitted on the medium. Examples of data-link protocols are IEEE 802.3/Ethernet, Frame Relay, ATM, and SONET.
The internet layer, corresponding to the OSI network layer, is primarily responsible for enabling the routing of data across logical network paths by defining a packet format and an addressing format. This layer is, of course, the one with which this book is most concerned.
The host-to-host layer, corresponding to the OSI transport layer, specifies the protocols that control the internet layer, much as the data link layer controls the physical layer. Both the host-to-host and data link layers can define such mechanisms as flow and error control. The difference is that while data-link protocols control traffic on the data link—the physical medium connecting two devices—the transport layer controls traffic on the logical link—the end-to-end connection of two devices whose logical connection traverses a series of data links.
The application layer corresponds to the OSI session, presentation, and application layers. Although some routing protocols such as Border Gateway Protocol (BGP) and routing Information Protocol (RIP) reside at this layer,[2] the most common services of the application layer provide the interfaces by which user applications access the network.
A function common to the protocol suite of Figure 1-1 and any other protocol suite is multiplexing between layers. Many applications might use a service at the host-to-host layer, and many services at the host-to-host layer might use the internet layer. Multiple protocol suites (IP, IPX, and AppleTalk, for example) can share a physical link via common data-link protocols.
Figure 1-2 shows the format of the IP packet header, specified in RFC 791. Most fields in this packet have some importance to routing.
Version identifies the IP version to which the packet belongs. This four-bit field is set to binary 0100 to indicate version 4 (IPv4) or binary 0110 to indicate version 6 (IPv6). This chapter is concerned primarily with IPv4, whereas Chapter 2, “IPv6 Overview,” focuses on IPv6. Table 1-1 shows all currently assigned version numbers, along with a few of the relevant RFCs. All versions other than 4 and 6 (built on an earlier proposal called Simple Internet Protocol, or SIP, which also carried a version number of 6) now exist only as “culture,” and it will be left to the curious to read their cited RFCs.
Table 1-1. IP version numbers.
Number | Version | RFC |
|---|---|---|
0 | Reserved | |
1–3 | Unassigned | |
4 | Internet Protocol version 4 (IPv4) | 791 |
5 | ST Datagram Mode | 1190 |
6 | Simple Internet Protocol (SIP) | |
6 | Internet Protocol version 6 (IPv6) | 1883 |
7 | TP/IX | 1475 |
8 | P Internet Protocol (PIP) | 1621 |
9 | TCP and UDP over Bigger Addresses (TUBA) | 1347 |
10–14 | Unassigned | |
15 | Reserved |
Header Length is a four-bit field that tells, as the name implies, the length of the IP header in 32-bit words. This field is included because the Options field (described later in this section) can vary in size. The minimum length of the IP header is 20 octets, and the options might increase this size up to a maximum of 60 octets—the maximum length in 32-bit words that can be described by this field.
Type of Service (TOS) is an eight-bit field that can be used for specifying special handling of the packet. This field actually can be broken down into two subfields: Precedence and TOS. Precedence sets a priority for the packet, the way a package might be sent overnight, two-day delivery, or general post. TOS allows the selection of a delivery service in terms of throughput, delay, reliability, and monetary cost. Although this field is not commonly used (all the bits will usually be set to zero), early specifications of the Open Shortest Path First (OSPF) protocol called for TOS routing. Also, the Precedence bits are occasionally used in quality of service (QoS) applications. Part (a) of Figure 1-3 summarizes the eight TOS bits; for more information, see RFC 1340 and RFC 1349.
In recent years, the ToS field has been redefined as a part of the Differentiated Services (DiffServ) framework.[3] This framework creates a much more flexible handling of IP packets than was allowed by the relatively rigid ToS definitions. With DiffServ, you can define service classes on a router and then sort packets into these classes. The router can then queue and forward packets with different levels of priority, according to their classification. Each queuing and forwarding treatment is called a Per-Hop Behavior (PHB). While DiffServ defines the framework or architecture, the mechanism itself is called Differentiated Class of Service or simply Class of Service (COS).
Part (b) of Figure 1-3 shows how the ToS field has been redefined, so that the first six bits now compose the DiffServ Code Point (DSCP). With these six bits you can define, either arbitrarily or according to service classes predefined in the DiffServ architecture, up to 64 different service classes that can then be sorted into PHBs. Note that the field in the IP header remains 8 bits; the DiffServ architecture just redefines how a router interprets the value in that field.
Explicit Congestion Notification (ECN), in part (b) of Figure 1-3, is used by some routers to signal support for Explicit Congestion Notification and, when it is supported, the bits can be used to signal congestion (ECN = 11).[4]
Total Length is a 16-bit field specifying the total length of the packet, including the header, in octets. By subtracting the header length, a receiver might determine the size of the packet’s data payload. Because the largest decimal number that can be described with 16 bits is 65,535, the maximum possible size of an IP packet is 65,535 octets.
Identifier is a 16-bit field used in conjunction with the Flags and Fragment Offset fields for fragmentation of a packet. Packets must be fragmented into smaller packets if the original length exceeds the Maximum Transmission Unit (MTU) of a data link through which they pass. For example, consider a 5000-byte packet traveling through a network. It encounters a data link with a 1500 byte MTU. That is, the frame can contain a maximum packet size of 1500 bytes. The router that places the packet onto this data link must first fragment the packet into chunks of no more than 1500 octets each. The router then marks each fragment with the same number in the Identifier field so that a receiving device can identify the fragments that go together.[5]
Flags is a three-bit field in which the first bit is unused. The second is the Don’t Fragment (DF) bit. When the DF bit is set to one, a router cannot fragment the packet. If the packet cannot be forwarded without fragmenting, the router drops the packet and sends an error message to the source. This function enables the testing of MTUs in a network. The DF bit can be set using the Extended Ping utility in IOS, as shown in Example 1-1.
Example 1-1. The IOS Extended Ping utility allows the setting of the DF bit to test MTUs across a network. In this ping Output, the largest MTU of the path to destination 172.16.113.17 is 1478 octets.
Handy#ping Protocol [ip]: Target IP address: 172.16.113.17 Repeat count [5]: 1 Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address: Type of service [0]: Set DF bit in IP header? [no]: y Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: r Number of hops [9]: Loose, Strict, Record, Timestamp, Verbose[RV]: Sweep range of sizes [n]: y Sweep min size [76]: 500 Sweep max size [18024]: 2000 Sweep interval [1]: 500 Type escape sequence to abort. Sending 4, [500..2000]-byte ICMP Echos to 172.16.113.17, timeout is 2 seconds: Packet has IP options: Total option bytes= 39, padded length=40 Record route: <*> 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 Reply to request 0 (16 ms) (size 500). Received packet has options Total option bytes= 40, padded length=40 Record route: 172.16.192.5 172.16.113.18 172.16.113.17 172.16.113.17 172.16.192.6 172.16.192.5 <*> 0.0.0.0 0.0.0.0 0.0.0.0 End of list Reply to request 1 (24 ms) (size 1000). Received packet has options Total option bytes= 40, padded length=40 Record route: 172.16.192.5 172.16.113.18 172.16.113.17 172.16.113.17 172.16.192.6 172.16.192.5 <*> 0.0.0.0 0.0.0.0 0.0.0.0 End of list Reply to request 2 (28 ms) (size 1500). Received packet has options Total option bytes= 40, padded length=40 Record route: 172.16.192.5 172.16.113.18 172.16.113.17 172.16.113.17 172.16.192.6 172.16.192.5 <*> 0.0.0.0 0.0.0.0 0.0.0.0 End of list Unreachable from 172.16.192.6, maximum MTU 1478 (size 2000). Received packet has options Total option bytes= 39, padded length=40 Record route: <*> 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 Success rate is 75 percent (3/4), round-trip min/avg/max = 16/22/28 ms Handy#
The third bit is the More Fragments (MF) bit. When a router fragments a packet, it sets the MF bit to one in all but the last fragment so that the receiver knows to keep expecting fragments until it encounters a fragment with MF = 0.
Fragment Offset is a 13-bit field that specifies the offset, in units of eight octets, from the beginning of the header to the beginning of the fragment.[6] Because fragments might not always arrive in sequence, the Fragment Offset field allows the pieces to be reassembled in the correct order.
Note that if a single fragment is lost during a transmission, the entire packet must be resent and refragmented at the same point in the network. Therefore, error-prone data links could cause a disproportionate delay. And if a fragment is lost because of congestion, the retransmission of the entire series of fragments might increase the congestion.
Time to Live (TTL) is an eight-bit field that will be set with a certain number when the packet is first generated. As the packet is passed from router to router, each router will decrement this number. If the number reaches zero, the packet will be discarded and an error message will be sent to the source. This process prevents “lost” packets from wandering endlessly through a network.
As originally conceived, the TTL was specified in seconds; if a packet was delayed more than a second in a router, the router would adjust the TTL accordingly. However, this approach is difficult to implement and has never been generally supported. Modern routers simply decrement the TTL by one, no matter what the actual delay, so the TTL is really a hop count.[7] The recommended default TTL is 64, although values such as 15 and 32 are not uncommon.
Some trace utilities, such as the IOS trace command, make use of the TTL field. If the router is told to trace the route to a host address such as 10.11.12.13, the router will send three packets with the TTL set to one; the first router will decrement it to zero, drop the packets, and send back error messages to the source. By reading the source address of the error messages, the first router on the path is now known. The next three packets will be sent with a TTL of two. The first router decrements to one, the second to zero, and an error message is received from the second router. The third set has a TTL of three, and so forth, until the destination is found. All routers along the network path will have identified themselves. Example 1-2 shows the output from an IOS trace.
Example 1-2. The trace utility uses the TTL field to identify routers along a route. Asterisks indicate timed-out packets.
Elvis#traceroute www.cisco.com
Type escape sequence to abort.
Tracing the route to cio-sys.Cisco.COM (192.31.7.130)
1 172.18.197.17 4 msec 4 msec 4 msec
2 ltlrichard-s1-13.hwy51.com (172.18.197.1) 36 msec 44 msec 2536 msec
3 cperkins-rtr-fr2.hwy51.com (10.168.204.3) 104 msec 64 msec *
4 cberry.hwy51.com (10.168.193.1) 92 msec *
5 jllewis-inner.hwy51.com (10.168.207.59) 44 msec * 44 msec
6 bholly-fw-outer-rt.hwy51.com (10.168.207.94) 44 msec * 48 msec
7 sl-stk-14-S10/0:6-512k.sprintlink.net (144.228.214.107) 92 msec *
8 sl-stk-2-F1/0/0.sprintlink.net (144.228.40.2) 52 msec 1156 msec *
9 sl-mae-w-H1/0-T3.sprintlink.net (144.228.10.46) 100 msec 124 msec 2340 msec
10 sanjose1-br1.bbnplanet.net (198.32.136.19) 2264 msec 164 msec *
11 paloalto-br2.bbnplanet.net (4.0.1.10) 64 msec 60 msec *
12 su-pr2.bbnplanet.net (131.119.0.218) 76 msec 76 msec 76 msec
13 cisco.bbnplanet.net (131.119.26.10) 2560 msec 76 msec 936 msec
14 sty.cisco.com (192.31.7.39) 84 msec 72 msec *
15 cio-sys.Cisco.COM (192.31.7.130) 60 msec * 64 msec
Elvis#Protocol is an eight-bit field that gives the “address,” or protocol number, of the host-to-host or transport layer protocol for which the information in the packet is destined. Table 1-2 shows a few of the more common of the 100 or so different protocol numbers currently assigned.
Table 1-2. A few well-known protocol numbers.
Protocol Number | Host-to-Host Layer Protocol |
|---|---|
1 | Internet Control Message Protocol (ICMP) |
2 | Internet Group Management Protocol (IGMP) |
4 | IP in IP (encapsulation) |
6 | Transmission Control Protocol (TCP) |
17 | User Datagram Protocol (UDP) |
45 | Inter-Domain Routing Protocol (IDRP) |
46 | Resource Reservation Protocol (RSVP) |
47 | Generic Routing Encapsulation (GRE) |
54 | NBMA Next Hop Resolution Protocol (NHRP) |
88 | Cisco Internet Gateway Routing Protocol (IGRP) |
89 | Open Shortest Path First (OSPF) |
Header Checksum is the error detection field for the IP header. The checksum is not calculated for the encapsulated data; UDP, TCP, and ICMP have their own checksums for doing this. The field contains a 16-bit one’s complement checksum, calculated by the originator of the packet. The receiver will again calculate a 16-bit one’s complement sum, including the original checksum. If no errors have occurred during the packet’s travels, the resulting checksum will be all ones. Remember that each router decrements the TTL; therefore, the checksum must be recalculated at each router. RFC 1141 discusses some strategies for simplifying this calculation.
Source and Destination Addresses are the 32-bit IP addresses of the originator of the packet and the destination of the packet. The format of IP addresses is covered in the next section, “IPv4 Addresses.”
Options is a variable-length field and, as the name says, is optional. Space is added to the packet header to contain either source-generated information or for other routers to enter information; the options are used primarily for testing. The most frequently used options are
Loose source routing, in which a series of IP addresses for router interfaces is listed. The packet must pass through each of these addresses, although multiple hops might be taken between the addresses.
Strict source routing, where again a series of router addresses is listed. Unlike loose source routing, the packet must follow the route exactly. If the next hop is not the next address on the list, an error occurs.
Record route provides room for each router to enter the address of its outgoing interface as the packet transits so that a record is kept of all routers the packet encounters. Record route provides a function similar to trace except that the outgoing interfaces, both on the path to the destination and on the return path, are recorded.
Timestamp is an option similar to record route except each router also enters a timestamp: the packet not only keeps track of where it has been but also records when it was there.
All these options might be invoked by using the Extended Ping on Cisco routers. Record route is used in Example 1-1, loose source routing and timestamp are used in Example 1-3, and strict source routing is used in Example 1-4.
Example 1-3. The Cisco Extended Ping can be used to set parameters in the Options field of the IP header. In this example, loose source routing and timestamp are used.
Handy#ping Protocol [ip]: Target IP address: 172.16.113.9 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address: Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: l Source route: 172.16.113.14 172.16.113.10 Loose, Strict, Record, Timestamp, Verbose[LV]: t Number of timestamps [ 6 ]: 2 Loose, Strict, Record, Timestamp, Verbose[LTV]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.113.9, timeout is 2 seconds: Packet has IP options: Total option bytes= 23, padded length=24 Loose source route: <*> 172.16.113.14 172.16.113.10 Timestamp: Type 0. Overflows: 0 length 12, ptr 5 >>Current pointer<< Time= 0 Time= 0 Request 0 timed out Reply to request 1 (76 ms). Received packet has options Total option bytes= 24, padded length=24 Loose source route: 172.16.113.13 172.16.192.6 <*> Timestamp: Type 0. Overflows: 6 length 12, ptr 13 Time= 80FF4798 Time= 80FF4750 >>Current pointer<< End of list Request 2 timed out Reply to request 3 (76 ms). Received packet has options Total option bytes= 24, padded length=24 Loose source route: 172.16.113.13 172.16.192.6 <*> Timestamp: Type 0. Overflows: 6 length 12, ptr 13 Time= 80FF4FC0 Time= 80FF4F78 >>Current pointer<< End of list Request 4 timed out Success rate is 40 percent (2/5), round-trip min/avg/max = 76/76/76 ms Handy#
Example 1-4. Extended Ping is used here to set strict source routing in the ping packets.
Handy#ping Protocol [ip]: Target IP address: 172.16.113.10 Repeat count [5]: 2 Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address: Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: s Source route: 172.16.192.6 172.16.113.17 172.16.113.10 Loose, Strict, Record, Timestamp, Verbose[SV]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 2, 100-byte ICMP Echos to 172.16.113.10, timeout is 2 seconds: Packet has IP options: Total option bytes= 15, padded length=16 Strict source route: <*> 172.16.192.6 172.16.113.17 172.16.113.10 Reply to request 0 (80 ms). Received packet has options Total option bytes= 16, padded length=16 Strict source route: 172.16.113.10 172.16.113.17 172.16.192.6 <*> End of list Reply to request 1 (76 ms). Received packet has options Total option bytes= 16, padded length=16 Strict source route: 172.16.113.10 172.16.113.17 172.16.192.6 <*> End of list Success rate is 100 percent (2/2), round-trip min/avg/max = 76/78/80 ms Handy#
Padding ensures that the header ends on a 32-bit boundary by adding zeros after the option field until a multiple of 32 is reached.
A protocol analyzer capture of an IP header is shown in Example 1-5. Compare the information shown with Figure 1-2.
Example 1-5. You can see the fields of an IP packet’s header and the values contained in each field in this protocol analyzer display.
Internet Protocol, Src Addr: 172.16.1.102 (172.16.1.102), Dst Addr: 224.0.0.5
(224.0.0.5)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0xc0 (DSCP 0x30: Class Selector 6; ECN: 0x00)
Total Length: 64
Identification: 0x6e61 (28257)
Flags: 0x00
Fragment offset: 0
Time to live: 1
Protocol: OSPF IGP (0x59)
Header checksum: 0xbcc8 (correct)
Source: 172.16.1.102 (172.16.1.102)
Destination: 224.0.0.5 (224.0.0.5)IPv4 addresses are 32 bits long; like all network-level addresses, they have a network portion and a host portion. The network portion uniquely identifies a physical or logical link and is common to all devices attached to that link. The host portion uniquely identifies a particular device attached to the link.
There are several ways to represent the 32 bits of an IP address. For instance, the 32-bit IP address
00001010110101100101011110000011
can be represented in decimal as
181,819,267.
The binary format is cumbersome, and a decimal format of the entire 32-bit number is time-consuming to calculate. Figure 1-4 shows a better format.
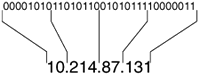
Figure 1-4. The dotted-decimal format is a convenient way to write IPv4 addresses, but it should not be confused with what the router (or host) sees: a 32-bit string.
The 32 bits of the address comprise four octets, each of which can be represented with a decimal number between 0 and 255, with dots between the decimal representations. In Figure 1-4, the 32-bit address is mapped into a dotted-decimal representation.[8]
An important distinction to remember when working with IPv4 addresses is that dotted decimal is just an easy way for humans to read and write IP addresses. Always remember that the router is not reading an address in terms of four octets; rather, the router sees a 32-bit binary string. Many pitfalls can be avoided by keeping this fact firmly in mind. If you have not worked with binary numbers—particularly converting between binary and decimal—you might want to read the tutorial in Appendix A, “Tutorial: Working with Binary and Hex,” before continuing on with this chapter.
Probably the most distinctive characteristic of IPv4 addresses is that unlike other network-level addresses, the network and host portions can vary in size within the 32-bit boundaries. That is, the network portion might take up most of the 32 bits, or the host portion might, or they might divide the bits equally. Protocols such as NetWare and AppleTalk were designed for use in relatively small networks, and as a result their network-level addresses have fixed-length network and host portions. This arrangement certainly makes life easier; a receiving device knows to read a certain number of bits into the address to find the network part, and the rest is host address.
TCP/IP, however, was designed from the first to be flexible enough to be used in any network, from the tiny to the colossal. This flexibility makes IP addresses more difficult to manage. The basics of administering IP addresses are presented in this section, and then some more advanced techniques are introduced in Chapter 6, “RIPv2, RIPng, and Classless Routing.”
Without putting too fine a point on it, it can be said that there are three sizes of networks as measured by the number of hosts: big, medium, and small:
Big networks, by definition, have a huge number of hosts. Relatively few big networks exist.
Small networks are just the opposite. Each one is small because it has a small number of hosts; a huge number of small networks exist.
Medium networks are just that: a medium number of them (in relation to big and small ones) and a medium number of hosts in each one.
This high level of addressing focus requires three types—classes—of network address for the three sizes of networks. Addresses for big networks need to be capable of addressing many hosts, but because so few big networks exist, only a few big-network addresses are required.
The situation is reversed for small networks. Because there are many small networks, a large number of small-network addresses are needed. But because a small network has a small number of hosts, each of the many network addresses only requires a few host addresses.
For medium-sized networks, a medium number of network addresses and a medium number of host addresses will be available for each network address.
Figure 1-5 shows how the network and host portions of IPv4 addresses are divided up for these three classes.
The big, medium, and small networks described thus far map to address classes as follows:
Class A IPv4 addresses are for big networks. The first octet is the network portion, and the last three octets are the host portion. Only 256 numbers are available in the eight-bit network part, but 224 or 16,777,216 numbers are available in the host part of each of those network addresses.
Class B addresses are for medium-size networks. The first two octets are the network portion, and the last two octets are the host portion. There are 216 or 65,536 available numbers in the network part and an equal number in the host part.
Class C addresses are just the opposite of Class A. The first three octets are the network portion, and the last octet is the host portion.
Because all IPv4 addresses are 32-bit binary strings, a way of distinguishing the class to which a particular address belongs is necessary. The first octet rule, demonstrated in Table 1-3, provides the means to make such a distinction and can be described as follows:
For Class A addresses, the first bit of the first octet—that is, the left-most bit of the entire 32-bit string—is always set to zero. Therefore, we can find the minimum and maximum numbers in the Class A range by setting all the remaining bits in the first octet to zero (for the minimum) and one (for the maximum). This action results in the decimal numbers 0 and 127 with a few exceptions: 0 is reserved as part of the default address (Chapter 12, “Default Routes and On-Demand Routing”), and 127 is reserved for internal loopback addresses.[9] That leaves 1 through 126; any IP address whose first octet is between 1 and 126 inclusive is a Class A address.
Class B addresses always have their left-most bit set to one and the second bit set to zero. Again, finding the minimum and maximum number of the first octet by setting all remaining bits to zero and then to one, you see in Figure 1-4 that any address whose first octet is in the decimal range 128 through 191 is a Class B address.
In Class C addresses, the first two bits are set to one, and the third bit is set to zero. The result is a first octet range of 192 through 223.[10]
So far IPv4 addressing doesn’t seem so difficult. A router or host could easily determine the network part of an IP address by using the first octet rule. If the first bit is 0, then read the first eight bits to find the network address. If the first two bits are 10, then read the first 16 bits; and if the first three bits are 110, then read 24 bits in to get the network address. Unfortunately, things are not that easy.
The address for an entire data link—a non-host-specific network address—is represented by the network portion of an IP address, with all host bits set to zero. For instance, an addressing authority[11] might assign to an applicant an address of 172.21.0.0.[12] This address is a Class B address because 172 is between 128 and 191, so the last two octets make up the host bits. Notice that they are all set to zero. The first 16 bits (172.21.) are assigned, but address owners are free to do whatever they please with the host bits.
Each device or interface will be assigned a unique, host-specific address such as 172.21.35.17. The device, whether a host or a router, obviously needs to know its own address, but it also needs to be able to determine the network to which it belongs—in this case, 172.21.0.0.
This task is accomplished by means of an address mask. The address mask is a 32-bit string, one bit for each bit of the IPv4 address. As a 32-bit string, the mask can be represented in dotted-decimal format just like an IPv4 address. This representation tends to be a stumbling block for some beginners: Although the address mask can be written in dotted decimal, it is not an address. Table 1-4 shows the standard address masks for the three classes of IPv4 address.
For each bit of the IPv4 address, the device performs a Boolean (logical) AND function with the corresponding bit of the address mask. The AND function can be stated as follows:
Compare two bits and derive a result. The result will be one, if and only if, both bits are one. If either or both bits are zero, the result will be zero.
Figure 1-6 shows how, for a given IPv4 address, the address mask is used to determine the network address. The mask has a one in every bit position corresponding to a network bit of the address and a zero in every bit position corresponding to a host bit. Because 172.21.35.17 is a Class B address, the mask must have the first two octets set to all ones and the last two octets, the host part, set to all zeros. As Table 1-4 shows, this mask can be represented in dotted decimal as 255.255.0.0.
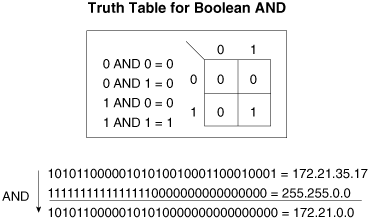
Figure 1-6. Each bit of this Class B address is ANDed with the corresponding bit of the address mask to derive the network address.
A logical AND is performed on the IPv4 address and its mask for every bit position; the result is shown in Figure 1-6. In the result, every network bit is repeated, and all the host bits become 0s. So by assigning an address of 172.21.35.17 and a mask of 255.255.0.0 to an interface, the device will know that the interface belongs to network 172.21.0.0. Applying the AND operator to an IPv4 address and its address mask always reveals the network address.
An address and mask are assigned to an interface of a Cisco router (in this example, the E0 interface) by means of the following commands:
Smokey(config)# interface ethernet 0 Smokey(config-if)# ip address 172.21.35.17 255.255.0.0
But why use address masks at all? So far, using the first octet rule seems much simpler.
Never lose sight of why network-level addresses are necessary in the first place. For routing to be accomplished, each and every data link (network) must have a unique address; in addition, each and every host on that data link must have an address that both identifies it as a member of the network and distinguishes it from any other host on that network.
As defined so far, a single Class A, B, or C address can be used only on a single data link. To build a network, separate addresses must be used for each data link so that those networks are uniquely identifiable. If a separate Class A, B, or C address were assigned to each data link, fewer than 17 million data links could be addressed before all IPv4 addresses were depleted. This approach is obviously impractical,[13] as is the fact that to make full use of the host address space in the previous example, more than 65,000 devices would have to reside on data link 172.21.0.0!
The only way to make Class A, B, or C addresses practical is by dividing each major address, such as 172.21.0.0, into subnetwork addresses. Recall two facts:
The host portion of an IPv4 address can be used as desired.
The network portion of an IPv4 address is determined by the address mask assigned to that interface.
Figure 1-7 shows a network to which the major Class B address 172.21.0.0 has been assigned. Five data links are interconnecting the hosts and routers, each one of which requires a network address. As it stands, 172.21.0.0 would have to be assigned to a single data link, and then four more addresses would have to be requested for the other four data links.
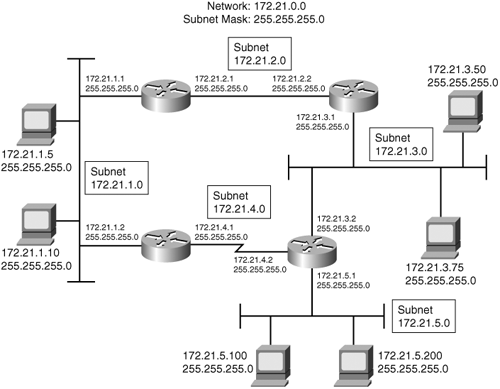
Figure 1-7. Subnet masks allow a single network address to be used on multiple data links by “borrowing” some of the host bits for use as subnet bits.
Notice what was done in Figure 1-7. The address mask is not a standard 16-bit mask for Class B addresses; the mask has been extended another eight bits so that the first 24 bits of the IP address are interpreted as network bits. In other words, the routers and hosts have been given a mask that causes them to read the first eight host bits as part of the network address. The result is that the major network address applies to the entire network, and each data link has become a subnetwork, or subnet. A subnet is a subset of a major Class A, B, or C address space.
The IPv4 address now has three parts: the network part, the subnet part, and the host part. The address mask is now a subnet mask, or a mask that is longer than the standard address mask. The first two octets of the address will always be 172.21, but the third octet—whose bits are now subnet bits instead of host bits—might range from 0 to 255. The network in Figure 1-6 has subnets 1, 2, 3, 4, and 5 (172.21.1.0 through 172.21.5.0). Up to 256 subnets might be assigned under the single Class B address, using the mask shown.
Two words of caution are in order. First, not all routing protocols can support subnet addresses in which the subnet bits are all zeros or all ones. The reason is that these protocols, called classful protocols, cannot differentiate between an all-zero subnet and the major network number. For instance, subnet 0 in Figure 1-7 would be 172.21.0.0; the major IP address is also 172.21.0.0. The two cannot be distinguished without further information.
Likewise, classful routing protocols cannot differentiate a broadcast on the all-ones subnet from an all-subnets broadcast address.[14] For example, the all-ones subnet in Figure 1-7 would be 172.21.255.0. For that subnet, the all-hosts broadcast address would be 172.21.255.255, but that is also the broadcast for all hosts on all subnets of major network 172.21.0.0. Again, the two addresses cannot be distinguished without further information. RIP version 1 and IGRP are both classful routing protocols; Chapter 7, “Enhanced Interior Gateway Routing Protocol (EIGRP),” introduces classless routing protocols, which can indeed use the all-zeros and all-ones subnets.
The second caution has to do with the verbal description of subnets and their masks. Subnetting the third octet of a Class B address, as is done is Figure 1-7, is very common; also common is hearing people describe such a subnet design as “using a Class C mask with a Class B address,” or “subnetting a Class B address into a Class C.” Both descriptions are wrong! Such descriptions frequently lead to misunderstandings about the subnet design or to a poor understanding of subnetting itself. The proper way to describe the subnetting scheme of Figure 1-6 is either as “a Class B address with 8 bits of subnetting,” or as “a Class B address with a 24-bit mask.”
The subnet mask might be represented in any of the following three formats:
Dotted decimal: 255.255.255.0
Bitcount: 172.21.0.0/24
Hexadecimal: 0xFFFFFF00
Dotted decimal is commonly used in software that has been around for a while, although the bitcount format is becoming increasingly preferred. Compared to dotted decimal, the bitcount format is easier to write. (The address is followed by a forward slash and the number of bits that are masked for the network part.) In addition, the bitcount format is more descriptive of what the mask is really doing and therefore avoids the type of semantic misunderstandings described in the previous paragraph. Some UNIX systems use the hexadecimal format.
Although the address mask must be specified to Cisco routers in dotted decimal, using the command shown previously, the mask might be displayed by various show commands in any of the three formats by using the command ip netmask-format [decimal| hexadecimal| bit-count] in line configuration mode. For example, to configure a router to display its masks in bitcount format, use
Gladys(config)# line vty 0 4 Gladys(config-line)# ip netmask-format bit-count
As established in the previous section, subnet bits cannot be all zeros or all ones in classful environments. Likewise, an IPv4 host address cannot have all its host bits set to zero—this setting is reserved for the address that routers use to represent the network or subnet itself. And the host bits cannot be set to all ones, as this setting is the broadcast address. These restrictions apply to the host bits with no exceptions and are starting points for designing subnets. Beyond these starting points, network designers need to choose the most appropriate subnetting scheme in terms of matching the address space to the particulars of a network.
When designing subnets and their masks, the number of available subnets under a major network address and the number of available hosts on each subnet are both calculated with the same formula: 2n – 2, where n is the number of bits in the subnet or host space and 2 is subtracted to account for the unavailable all-zeros and all-ones addresses. For example, given a Class A address of 10.0.0.0, a subnet mask of 10.0.0.0/16 (255.255.0.0) means that the 8-bit subnet space will yield 28 – 2 = 254 available subnets and 216 – 2 = 65,534 host addresses available on each of those subnets. On the other hand, a mask of 10.0.0.0/24 (255.255.255.0) means that a 16-bit subnet space is yielding 65,534 subnets and an 8-bit host space is yielding 254 host addresses for each subnet.
The following steps are used to subnet an IPv4 address:
Determine how many subnets are required and how many hosts per subnet are required.
Use the 2n – 2 formula to determine the number of subnet bits and the number of host bits that will satisfy the requirements established in Step 1. If multiple subnet masks can satisfy the requirements, choose the one that will best scale to future needs. For example, if the network is most likely to grow by adding subnets, choose more subnet bits; if the network is most likely to grow by adding hosts to existing subnets, choose more host bits. Avoid choosing a scheme in which either all subnets or all host addresses within the subnets will be used up immediately, leaving no room for future growth.
Working in binary, determine all available bit combinations in the subnet space; in each instance, set all the host bits to zero. Convert the resulting subnet addresses to dotted decimal. These are the subnet addresses.
For each subnet address, again working in binary, write all possible bit combinations for the host space without changing the subnet bits. Convert the results to dotted decimal; these are the host addresses available for each subnet.
The importance of doing the last two steps in binary cannot be overemphasized. The single greatest source of mistakes when working with subnets is trying to work with them in dotted decimal without understanding what is happening at the binary level. Again, dotted decimal is for convenience in reading and writing IPv4 addresses. Routers and hosts see the addresses as 32-bit binary strings; to successfully work with these addresses, they must be seen the way the routers and hosts see them.
The previous paragraph might seem a bit overzealous in light of the examples given so far; the patterns of subnet and host addresses have been quite apparent without having to see the addresses and masks in binary. The next section uses the four design steps to derive a subnet design in which the dotted-decimal representations are not so obvious.
In the examples given so far, the subnet spaces have fallen on octet boundaries. This arrangement is not always the most practical or efficient choice. What if, for instance, you need to subnet a Class B address across 500 data links, each with a maximum of 100 hosts? This requirement is easily met, but only by using nine bits in the subnet field: 29 – 2 = 510 available subnets, leaving seven bits for the host field, and 27 – 2 = 126 available hosts per subnet. No other bit combination will satisfy this requirement.
Notice, also, that there is no way to subnet a class C address on an octet boundary—doing so would use up all of the last byte, leaving no room for host bits. The subnet bits and host bits must share the last octet, as the following example shows.
Figure 1-8 shows the network of Figure 1-7 but with a Class C address of 192.168.100.0 assigned.
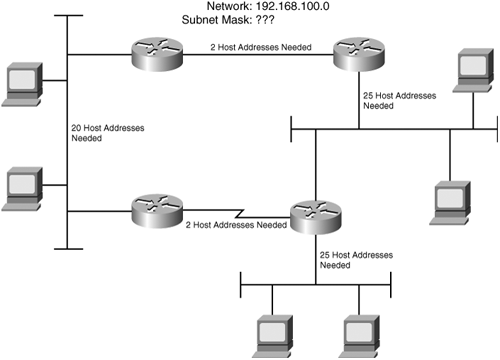
Figure 1-8. The network from Figure 1-7 but with a Class C prefix assigned. Subnetting an entire octet will not work here; there would be no space left for host bits.
There are five data links; therefore, the address must be subnetted to provide for at least five subnet addresses. The illustration also indicates the number of hosts (including router interfaces) that need to be addressed on each subnet. The maximum host address requirement is 25 for the two Ethernets. Therefore, the full subnetting requirements are at least five subnets and at least 25 host addresses per subnet.
Applying the 2n – 2 formula, three subnet bits and five host bits will satisfy the requirements: 23 – 2 = 6 and 25 – 2 = 30. A Class C mask with three bits of subnetting is represented as 255.255.255.224 in dotted decimal.
Figure 1-9 shows the derivation of the subnet bits. The subnet mask derived in Step 2 is written in binary, and the IP address is written below it. Vertical lines are drawn as markers for the subnet space, and within this space all possible bit combinations are written by counting up from zero in binary.

Figure 1-9. The subnet bits are derived by marking the masked subnet bit space and then writing all possible bit combinations in the space by counting up from zero in binary.
In Figure 1-10, the unchanged network bits are filled in to the left of the subnet space and the host bits, which are all zeros in the subnet addresses, are filled in to the right of the subnet space. The results are converted to dotted decimal, and these are the six subnet addresses (remembering that the first and last addresses, which have 000 and 111 in the subnet space, cannot be used).
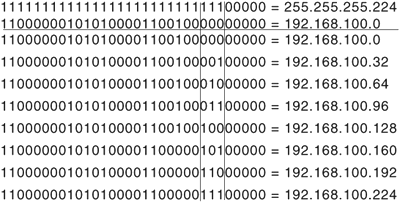
Figure 1-10. The subnet addresses are derived by filling in the network address to the left of the subnet space, setting all host bits to zero to the right of the subnet space, and converting the results to dotted decimal.
The last step is to calculate the host addresses available to each subnet. This step is done by choosing a subnet and, keeping the network and subnet bits unchanged, writing all bit combinations in the host space by counting up from zero in binary. Figure 1-11 shows this step for subnet 192.168.100.32.

Figure 1-11. The host addresses for a subnet are derived by writing all possible bit combinations in the host space. These are the host bits for subnet 192.168.100.32.
Notice the patterns in the results: The first address, in which the host bits are all zero, is the subnet address. The last address, in which the host bits are all one, is the broadcast address for subnet 192.168.100.32. The host addresses count up from the subnet address to the broadcast address, and if the sequence were to continue, the next address would be the second subnet, 192.168.100.64.
The importance of understanding subnetting at the binary level should now be clear. Presented with an address such as 192.168.100.160, you cannot be sure whether it is a host address, a subnet address, or a broadcast address. Even when the subnet mask is known, things are not always readily apparent.
Readers are encouraged to calculate all host addresses for all the remaining subnets in the example and to observe the patterns that result in the addresses. Understanding these patterns will help in situations such as the one presented in the next section.
The necessity frequently arises to “dissect” a given host address and mask, usually to identify the subnet to which it belongs. For instance, if an address is to be configured on an interface, a good practice is to first verify that the address is valid for the subnet to which the subnet is connected.
Use the following steps to reverse-engineer an IP address:
Write the given subnet mask in binary.
Write the IPv4 host address in binary.
Knowing the class of the host address, the subnet bits of the mask should be apparent. Using the mask bits as a guide, draw a line between the last network bit and the first subnet bit of the address. Draw another line between the last subnet bit and the first host bit.
Write the network and subnet bits of the address, setting all host bits to zero. The result is the address of the subnet to which the host address belongs.
Again write the network and subnet bits of the address, this time setting all host bits to one. The result is the broadcast address of the subnet.
Knowing that the subnet address is the first address in the sequence and that the broadcast address is the last address in the sequence, you also know that all addresses between these two are valid host addresses.
Figure 1-12 shows these steps applied to 172.30.0.141/25.

Figure 1-12. Given an IPv4 address and a subnet mask, follow these steps to find the subnet, the broadcast, and the host addresses.
The address is a Class B, so it is known that the first 16 bits are the network bits; therefore, the last nine bits of the 25-bit mask mark the subnet space. The subnet address is found to be 172.30.0.128, and the broadcast address is 172.30.0.255. Knowing that the valid host addresses for the subnet are bounded by these two addresses, it is determined that the host addresses for subnet 172.30.0.128 are 172.30.0.129 through 172.30.0.254.
Several things about this example tend to bother folks who are new to subnetting. Some are bothered by the third octet of the address, which is all zeros. Some are bothered by the single subnet bit in the last octet. Some think that the broadcast address looks suspiciously invalid. All of these uneasy feelings arise from reading the addresses in dotted decimal. When the addresses and the mask are seen in binary, these suspicions are assuaged and everything is seen to be legitimate; the mask sets a nine-bit subnet space—all of the third octet, and the first bit of the fourth octet. The moral of the story is that if everything is known to be correct in binary, don’t worry if the dotted-decimal representation looks funny.
Routers pass packets across a logical path, composed of multiple data links, by reading and acting on the network addresses in the packets. The packets are passed across the individual data links by encapsulating the packets in frames, which use data-link identifiers (MAC addresses, for example) to get the frame from source to destination on the link. One of the major topics of this book concerns the mechanisms by which routers discover and share information about network addresses so that routing might take place. Similarly, devices on a data link need a way to discover their neighbors’ data-link identifiers so that frames might be transmitted to the correct destination.
Several mechanisms can provide this information;[15] IPv4 uses the Address Resolution Protocol (ARP), described in RFC 826. Figure 1-13 shows how ARP works. A device needing to discover the data-link identifier of another device will create an ARP Request packet. This request will contain the IPv4 address of the device in question (the target) and the source IPv4 address and data-link identifier (MAC address) of the device making the request (the sender). The ARP Request packet is then encapsulated in a frame with the sender’s MAC address as the source and a broadcast address for the destination (see Example 1-6).[16]
Example 1-6. An analyzer capture of the ARP Request depicted in Figure 1-13, with its encapsulating frame.
Ethernet II, Src: 00:30:65:2c:09:a6, Dst: ff:ff:ff:ff:ff:ff
Destination: ff:ff:ff:ff:ff:ff (Broadcast)
Source: 00:30:65:2c:09:a6 (AppleCom_2c:09:a6)
Type: ARP (0x0806)
Address Resolution Protocol (request)
Hardware type: Ethernet (0x0001)
Protocol type: IP (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (0x0001)
Sender MAC address: 00:30:65:2c:09:a6 (AppleCom_2c:09:a6)
Sender IP address: 172.16.1.21 (172.16.1.21)
Target MAC address: 00:00:00:00:00:00 (00:00:00_00:00:00)
Target IP address: 172.16.1.33 (172.16.1.33)The broadcast address means that all devices on the data link will receive the frame and examine the encapsulated packet. All devices except the target will recognize that the packet is not for them and will drop the packet. The target will send an ARP Reply to the source address, supplying its MAC address (see Example 1-7).
Example 1-7. An analyzer capture of the ARP Reply depicted in Figure 1-13.
Ethernet II, Src: 00:10:5a:e5:0e:e3, Dst: 00:30:65:2c:09:a6
Destination: 00:30:65:2c:09:a6 (AppleCom_2c:09:a6)
Source: 00:10:5a:e5:0e:e3 (3com_e5:0e:e3)
Type: ARP (0x0806)
Trailer: 15151515151515151515151515151515...
Address Resolution Protocol (reply)
Hardware type: Ethernet (0x0001)
Protocol type: IP (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: reply (0x0002)
Sender MAC address: 00:10:5a:e5:0e:e3 (3com_e5:0e:e3)
Sender IP address: 172.16.1.33 (172.16.1.33)
Target MAC address: 00:30:65:2c:09:a6 (AppleCom_2c:09:a6)
Target IP address: 172.16.1.21 (172.16.1.21)Cisco routers will display ARP activity when the debug function debug arp is invoked, as shown in Example 1-8.
Example 1-8. Router Aretha (172.21.5.1) responds to an ARP request from host 172.19.35.2.
Aretha#debug arp
IP ARP: rcvd req src 172.19.35.2 0002.6779.0f4c, dst 172.21.5.1 Ethernet0
IP ARP: sent rep src 172.21.5.1 0000.0c0a.2aa9,
dst 172.19.35.2 0002.6779.0f4c Ethernet0
Aretha#Figure 1-14 shows the ARP packet format. As the fields are described, compare them with the ARP packets in Example 1-6 and Example 1-7.
Hardware Type specifies the type of hardware, as specified by the IETF.[17] Table 1-5 shows some examples of some of the more common type numbers.
Protocol Type specifies the type of network-level protocol the sender is mapping to the data link identifier; IPv4 is 0x0800.
Hardware Address Length specifies the length, in octets, of the data link identifiers. MAC addresses would be 6.
Protocol Address Length specifies the length, in octets, of the network-level address. IPv4 would be 4.
Operation specifies whether the packet is an ARP Request (1) or an ARP Reply (2). Other values might also be found here, indicating other uses for the ARP packet. Examples are Reverse ARP Request (3), Reverse ARP Reply (4), Inverse ARP Request (8), and Inverse ARP Reply (9).
The final 20 octets are the fields for the sender’s and target’s data-link identifiers and IPv4 addresses.
In the top screen in Example 1-9, the IOS command show arp is used to examine the ARP table in a Cisco router.
Example 1-9. The ARP table for three devices connected to the same network: a Cisco router, a Microsoft Windows host, and a Linux host.
Martha#show arp Protocol Address Age (min) Hardware Addr Type Interface Internet 10.158.43.34 2 0002.6779.0f4c ARPA Ethernet0 Internet 10.158.43.1 - 0000.0c0a.2aa9 ARPA Ethernet0 Internet 10.158.43.25 18 00a0.24a8.a1a5 ARPA Ethernet0 Internet 10.158.43.100 6 0000.0c0a.2c51 ARPA Ethernet0 Martha# ________________________________________________________________________ C:WINDOWS>arp -a Interface: 148.158.43.25 Internet Address Physical Address Type 10.158.43.1 00-00-0c-0a-2a-a9 dynamic 10.158.43.34 00-02-67-79-0f-4c dynamic 10.158.43.100 00-00-0c-0a-2c-51 dynamic _________________________________________________________________________ Linux:~# arp -a Address HW type HW address Flags Mask 10.158.43.1 10Mbps Ethernet 00:00:0C:0A:2A:A9 C * 10.158.43.100 10Mbps Ethernet 00:00:0C:0A:2C:51 C * 10.158.43.25 10Mbps Ethernet 00:A0:24:A8:A1:A5 C * Linux:~#
Notice the Age column. As this column would indicate, ARP information is removed from the table after a certain time to prevent the table from becoming congested with old information. Cisco routers hold ARP entries for four hours (14,400 seconds); this default can be changed. The following example changes the ARP timeout to 30 minutes (1800 seconds):
Martha(config)# interface ethernet 0 Martha(config-if)# arp timeout 1800
The middle screen of Example 1-9 shows the ARP table of a Microsoft Windows PC, and the bottom shows the ARP table from a Linux machine. Although the format is different from the IOS display, the essential information is the same in all three tables.
ARP entries might also be permanently placed in the table. To statically map 172.21.5.131 to hardware address 0000.00a4.b74c, with a SNAP (Subnetwork Access Protocol) encapsulation type, use the following:
Martha(config)# arp 172.21.5.131 0000.00a4.b74c snapThe command clear arp-cache forces a deletion of all dynamic entries from the ARP table. It also clears the fast-switching cache and the IP route cache.
Several variations of ARP exist; at least one, proxy ARP, is important to routing.
Sometimes called promiscuous ARP and described in RFCs 925 and 1027, proxy ARP is a method by which routers might make themselves available to hosts. For example, a host 192.168.12.5/24 needs to send a packet to 192.168.20.101/24, but it is not configured with default gateway information and therefore does not know how to reach a router. It might issue an ARP Request for 192.168.20.101; the local router, receiving the request and knowing how to reach network 192.168.20.0, will issue an ARP Reply with its own data link identifier in the hardware address field. In effect, the router has tricked the local host into thinking that the router’s interface is the interface of 192.168.20.101. All packets destined for that address are then sent to the router.
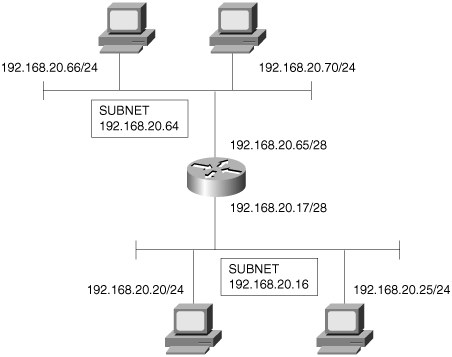
Figure 1-15 shows another use for proxy ARP. Of particular interest here are the address masks. The router is configured with a 28-bit mask (four bits of subnetting for the Class C address), but the hosts are all configured with 24-bit, default Class C mask. As a result, the hosts will not be aware that subnets exist. Host 192.168.20.66, wanting to send a packet to 192.168.20.25, will issue an ARP Request. The router, recognizing that the target address is on another subnet, will respond with its own hardware address. Proxy ARP makes the subnetted network topology transparent to the hosts.
The ARP cache in Example 1-10 gives a hint that proxy ARP is in use. Notice that multiple IPv4 addresses are mapped to a single MAC identifier; the addresses are for hosts, but the hardware MAC identifier belongs to the router interface.
Example 1-10. This ARP table from host 192.168.20.66 in Figure 1-15 shows multiple IPv4 addresses mapped to one MAC identifier, indicating that proxy ARP is in use.
C:WINDOWS>arp -a
Interface: 192.168.20.66
Internet Address Physical Address Type
192.168.20.17 00-00-0c-0a-2a-a9 dynamic
192.168.20.20 00-00-0c-0a-2a-a9 dynamic
192.168.20.25 00-00-0c-0a-2a-a9 dynamic
192.168.20.65 00-00-0c-0a-2c-51 dynamic
192.168.20.70 00-02-67-79-0f-4c dynamicProxy ARP is enabled by default in IOS and might be disabled on a per interface basis with the command no ip proxy-arp.
A host might occasionally issue an ARP Request with its own IPv4 address as the target address. These ARP Requests, known as gratuitous ARPs, have several uses:
A gratuitous ARP might be used for duplicate address checks. A device that issues an ARP Request with its own IPv4 address as the target and receives an ARP Reply from another device will know that the address is a duplicate.
A gratuitous ARP might be used to advertise a new data-link identifier. This use takes advantage of the fact that when a device receives an ARP Request for an IPv4 address that is already in its ARP cache, the cache will be updated with the sender’s new hardware address.
A router running Hot Standby Router Protocol (HSRP) that has just taken over as the active router from another router on a subnet issues a gratuitous ARP to update the ARP caches of the subnet’s hosts.
Many IP implementations do not use gratuitous ARP, but you should be aware of its existence. It is disabled by default in IOS but can be enabled with the command ip gratuitous-arps.
Instead of mapping a hardware address to a known IPv4 address, Reverse ARP (RARP) maps an IPv4 address to a known hardware address. Some devices, such as diskless workstations, might not know their IPv4 address at startup. RARP might be programmed into firmware on these devices, allowing them to issue an ARP Request that has their burned-in hardware address. The reply from a RARP server will supply the appropriate IPv4 address.
RARP has been largely supplanted by Dynamic Host Configuration Protocol (DHCP), an extension of the Bootstrap Protocol (BootP), both of which can provide more information than the IPv4 address, and which, unlike RARP, can be routed off the local data link.
The Internet Control Message Protocol, or ICMP, described in RFC 792, specifies a variety of messages whose common purpose is to manage the network. ICMP messages might be classified as either error messages or queries and responses. Figure 1-16 shows the general ICMP packet format. The packets are identified by type; many of the packet types have more specific types, and these are identified by the code field. Table 1-6 lists the various ICMP packet types and their codes, as described in RFC 1700.
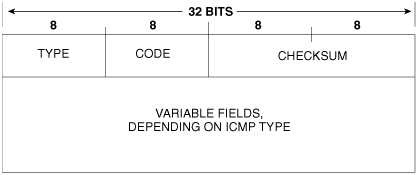
Figure 1-16. The ICMP packet header includes a type field, a code field that further identifies some types, and a checksum. The rest of the fields depend on the type and code.
Table 1-6. ICMP packet types and code fields.
Type | Code | Name |
|---|---|---|
0 | 0 | ECHO REPLY |
3 | DESTINATION UNREACHABLE | |
0 | Network Unreachable | |
1 | Host Unreachable | |
2 | Protocol Unreachable | |
3 | Port Unreachable | |
4 | Fragmentation Needed and Don’t Fragment Flag Set | |
5 | Source Route Failed | |
6 | Destination Network Unknown | |
7 | Destination Host Unknown | |
8 | Source Host Isolated | |
9 | Destination Network Administratively Prohibited | |
10 | Destination Host Administratively Prohibited | |
11 | Destination Network Unreachable for Type of Service | |
12 | Destination Host Unreachable for Type of Service | |
4 | 0 | SOURCE QUENCH (deprecated) |
5 | REDIRECT | |
0 | Redirect Datagram for the Network (or Subnet) | |
1 | Redirect Datagram for the Host | |
2 | Redirect Datagram for the Network and Type of Service | |
3 | Redirect Datagram for the Host and Type of Service | |
6 | 0 | ALTERNATE HOST ADDRESS |
8 | 0 | ECHO |
9 | 0 | ROUTER ADVERTISEMENT |
10 | 0 | ROUTER SELECTION |
11 | TIME EXCEEDED | |
0 | Time to Live Exceeded in Transit | |
1 | Fragment Reassembly Time Exceeded | |
12 | PARAMETER PROBLEM | |
0 | Pointer Indicates the Error | |
1 | Missing a Required Option | |
2 | Bad Length | |
13 | 0 | TIMESTAMP |
14 | 0 | TIMESTAMP REPLY |
15 | 0 | INFORMATION REQUEST (Obsolete) |
16 | 0 | INFORMATION REPLY (Obsolete) |
17 | 0 | ADDRESS MASK REQUEST (Near-obsolete) |
18 | 0 | ADDRESS MASK REPLY (Near-obsolete) |
30 | - | TRACEROUTE |
Example 1-11 and Example 1-12 show analyzer captures of two of the most well-known ICMP messages—Echo Request and Echo Reply, which are used by the ping function.
Example 1-11. ICMP Echo message, shown with its IPv4 header.
Internet Protocol, Src Addr: 172.16.1.21 (172.16.1.21),
Dst Addr: 198.133.219.25 (198.133.219.25)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
Total Length: 84
Identification: 0xabc3 (43971)
Flags: 0x00
Fragment offset: 0
Time to live: 64
Protocol: ICMP (0x01)
Header checksum: 0x8021 (correct)
Source: 172.16.1.21 (172.16.1.21)
Destination: 198.133.219.25 (198.133.219.25)
Internet Control Message Protocol
Type: 8 (Echo (ping) request)
Code: 0
Checksum: 0xa297 (correct)
Identifier: 0x0a40
Sequence number: 0x0000
Data (56 bytes)
0000 40 fd ab c2 00 0e 73 57 08 09 0a 0b 0c 0d 0e 0f @.....sW........
0010 10 11 12 13 14 15 16 17 18 19 1a 1b 1c 1d 1e 1f ................
0020 20 21 22 23 24 25 26 27 28 29 2a 2b 2c 2d 2e 2f !"#$%&'()*+,-./
0030 30 31 32 33 34 35 36 37 01234567Example 1-12. ICMP Echo Reply.
Internet Protocol, Src Addr: 198.133.219.25 (198.133.219.25),
Dst Addr: 172.16.1.21 (172.16.1.21)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
Total Length: 84
Identification: 0xabc3 (43971)
Flags: 0x00
Fragment offset: 0
Time to live: 242
Protocol: ICMP (0x01)
Header checksum: 0xce20 (correct)
Source: 198.133.219.25 (198.133.219.25)
Destination: 172.16.1.21 (172.16.1.21)
Internet Control Message Protocol
Type: 0 (Echo (ping) reply)
Code: 0
Checksum: 0xaa97 (correct)
Identifier: 0x0a40
Sequence number: 0x0000
Data (56 bytes)
0000 40 fd ab c2 00 0e 73 57 08 09 0a 0b 0c 0d 0e 0f @.....sW........
0010 10 11 12 13 14 15 16 17 18 19 1a 1b 1c 1d 1e 1f ................
0020 20 21 22 23 24 25 26 27 28 29 2a 2b 2c 2d 2e 2f !"#$%&'()*+,-./
0030 30 31 32 33 34 35 36 37 01234567Although most ICMP types have some bearing on routing functionality, three types are of particular importance:
Router Advertisement and Router Selection, types 9 and 10, respectively, are used by the ICMP Router Discovery Protocol (IRDP), a protocol used by some operating systems (such as most versions of Microsoft Windows) to discover local routers.
Redirect, ICMP type 5, is used by routers to notify hosts of another router on the data link that should be used for a particular destination. Suppose two routers, Router A and Router B, are connected to the same Ethernet. Host X, also on the Ethernet, is configured to use Router A as its default gateway; the host sends a packet to Router A, and A sees that the destination address of the packet is reachable via Router B (that is, Router A must forward the packet out the same interface on which it was received). Router A forwards the packet to B but also sends an ICMP redirect to host X informing it that in the future, to reach that particular destination, X should forward the packet to Router B. Example 1-13 shows a router sending a redirect.
Example 1-13. Using the debugging function debug ip icmp, this router can be seen sending a redirect to host 10.158.43.25, informing it that the correct router for reaching destination 10.158.40.1 is reachable via gateway (gw) 10.158.43.10.
Pip#debug ip icmp
ICMP packet debugging is on
ICMP: redirect sent to 10.158.43.25 for dest 10.158.40.1, use gw 10.158.43.10
0
Pip#An occasionally used trick to avoid redirects on data links with multiple attached gateways is to set each host’s default gateway as its own IPv4 address. The hosts will then ARP for any address, and if the address is not on the data link, the correct router should respond via proxy ARP. The benefits of using this tactic merely to avoid redirects are debatable; redirects are decreased or eliminated, but at the expense of increased ARP traffic.
Redirects are enabled by default in IOS and might be disabled on a per interface basis with the command no ip redirects.
The host-to-host layer of the TCP/IP protocol is aptly named. Whereas the internet layer is responsible for the logical paths between networks, the host-to-host layer is responsible for the full logical path between two hosts on disparate networks.[18] From another viewpoint, the host-to-host layer is an interface to the lower layers of the protocol suite, freeing applications from any concern about how their data is actually being delivered.
An analogy to this service is a corporate mailroom. A package might be given to the mailroom with requirements stated for its delivery (general delivery, overnight). The person making the delivery request does not need to know, and is probably not interested in, the actual mechanics of delivering the package. The mailroom people will arrange for the proper service (postal, FedEx, cross-town bicycle courier) to fulfill the delivery requirements.
The two primary services offered by the host-to-host layer are TCP and UDP.
The Transmission Control Protocol, or TCP, described in RFC 793, provides applications with a reliable, connection-oriented service. In other words, TCP provides the appearance of a point-to-point connection.
Point-to-point connections have two characteristics:
They have only one path to the destination. A packet entering one end of the connection cannot become lost, because the only place to go is the other end.
Packets arrive in the same order in which they are sent.
TCP provides the appearance of a point-to-point connection, although in reality there is no such connection. The internet layer TCP uses a connectionless, best-effort packet delivery service. The analogy of this is the Postal Service. If a stack of letters is given to the mail carrier for delivery, there is no guarantee that the letters will arrive stacked in the same order, that they will all arrive on the same day, or indeed that they will arrive at all. The Postal Service merely commits to making its best effort to deliver the letters.
Likewise, the internet layer does not guarantee that all packets will take the same route, and therefore there is no guarantee that they will arrive in the same sequence and time intervals as they were sent, or that they will arrive at all.
On the other hand, a telephone call is connection-oriented service. Data must arrive sequentially and reliably, or it is useless. Like a telephone call, TCP must first establish a connection, then transfer data, and then perform a disconnect when the data transfer is complete.
TCP uses three fundamental mechanisms to accomplish a connection-oriented service on top of a connectionless service:
Packets are labeled with sequence numbers so that the receiving TCP service can put out-of-sequence packets into the correct sequence before delivering them to the destination application.
TCP uses a system of acknowledgments, checksums, and timers to provide reliability. A receiver might notify a sender when it recognizes that a packet in a sequence has failed to arrive or has errors, or a sender might assume that a packet has not arrived if the receiver does not send an acknowledgment within a certain amount of time after transmission. In both cases, the sender will resend the packet in question.
TCP uses a mechanism called windowing to regulate the flow of packets; windowing decreases the chances of packets being dropped because of full buffers in the receiver.
TCP attaches a header to the application layer data; the header contains fields for the sequence numbers and other information necessary for these mechanisms, and fields for addresses called port numbers, which identify the source and destination applications of the data. The application data with its attached TCP header is then encapsulated within an IP packet for delivery. Figure 1-17 shows the fields of the TCP header, and Example 1-14 shows an analyzer capture of a TCP header.
Example 1-14. Analyzer display of a TCP header.
Ethernet II, Src: 00:0c:41:3c:2b:18, Dst: 00:30:65:2c:09:a6
Internet Protocol, Src Addr: 66.218.71.112 (66.218.71.112),
Dst Addr: 172.16.1.21 (172.16.1.21)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
Total Length: 52
Identification: 0xc0b7 (49335)
Flags: 0x04
Fragment offset: 0
Time to live: 50
Protocol: TCP (0x06)
Header checksum: 0x509d (correct)
Source: 66.218.71.112 (66.218.71.112)
Destination: 172.16.1.21 (172.16.1.21)
Transmission Control Protocol, Src Port: http (80),
Dst Port: 60190 (60190), Seq: 288, Ack: 811, Len: 0
Source port: http (80)
Destination port: 60190 (60190)
Sequence number: 288
Acknowledgement number: 811
Header length: 32 bytes
Flags: 0x0010 (ACK)
Window size: 66608
Checksum: 0xb32a (correct)
Options: (12 bytes)
NOP
NOP
Time stamp: tsval 587733966, tsecr 1425164062
SEQ/ACK analysis
This is an ACK to the segment in frame: 17
The RTT to ACK the segment was: 0.047504000 secondsSource and Destination Port are 16-bit fields that specify the source and destination applications for the encapsulated data. Like other numbers used by TCP/IP, RFC 1700 describes all port numbers in common and not-so-common use. A port number for an application, when coupled with the IP address of the host the application resides on, is called a socket. A socket uniquely identifies every application in a network.
Sequence Number is a 32-bit number that identifies where the encapsulated data fits within a data stream from the sender. For example, if the sequence number of a segment is 1343 and the segment contains 512 octets of data, the next segment should have a sequence number of 1343 + 512 + 1 = 1856.
Acknowledgment Number is a 32-bit field that identifies the sequence number the source next expects to receive from the destination. If a host receives an acknowledgment number that does not match the next sequence number it intends to send (or has sent), it knows that packets have been lost.
Header Length, sometimes called Data Offset, is a four-bit field indicating the length of the header in 32-bit words. This field is necessary to identify the beginning of the data because the length of the Options field is variable.
The Reserved field is four bits, which are always set to zero.
Flags are eight 1-bit flags that are used for data flow and connection control. The flags, from left to right, are Congestion Window Reduced (CWR), ECN-Echo (ECE), Urgent (URG), Acknowledgment (ACK), Push (PSH), Reset (RST), Synchronize (SYN), and Final (FIN).
Window Size is a 16-bit field used for flow control. It specifies the number of octets, starting with the octet indicated by the Acknowledgment Number, that the sender of the segment will accept from its peer at the other end of the connection before the peer must stop transmitting and wait for an acknowledgment.
Checksum is 16 bits, covering both the header and the encapsulated data, allowing error detection.
Urgent Pointer is used only when the URG flag is set. The 16-bit number is added to the Sequence Number to indicate the end of the urgent data.
Options, as the name implies, specifies options required by the sender’s TCP process. The most commonly used option is Maximum Segment Size, which informs the receiver of the largest segment the sender is willing to accept. The remainder of the field is padded with zeros to ensure that the header length is a multiple of 32 octets.
User Datagram Protocol, or UDP, described in RFC 768, provides a connectionless, best-effort packet delivery service. At first take, it might seem questionable that any application would prefer an unreliable delivery over the connection-oriented TCP. The advantage of UDP, however, is that no time is spent setting up a connection—the data is just sent. Applications that send short bursts of data will realize a performance advantage by using UDP instead of TCP.
Figure 1-18 shows another advantage of UDP: a much smaller header than TCP. The Source and Destination Port fields are the same as they are in the TCP header; the UDP length indicates the length of the entire segment in octets. The checksum covers the entire segment, but unlike TCP, the checksum here is optional; when no checksum is used, the field is set to all zeros. Example 1-15 shows an analyzer capture of a UDP header.
Example 1-15. Analyzer display of a UDP header.
Ethernet II, Src: 00:30:65:2c:09:a6, Dst: 00:0c:41:3c:2b:18
Internet Protocol, Src Addr: 172.16.1.21 (172.16.1.21),
Dst Addr: 198.133.219.25 (198.133.219.25)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
Total Length: 40
Identification: 0x8a4d (35405)
Flags: 0x00
Fragment offset: 0
Time to live: 1
Protocol: UDP (0x11)
Header checksum: 0xe0b3 (correct)
Source: 172.16.1.21 (172.16.1.21)
Destination: 198.133.219.25 (198.133.219.25)
User Datagram Protocol, Src Port: 35404 (35404), Dst Port: 33435 (33435)
Source port: 35404 (35404)
Destination port: 33435 (33435)
Length: 20
Checksum: 0x0000 (none)
Data (12 bytes)
0000 01 01 00 00 40 fd ac 74 00 00 d2 45 [email protected]The focus of this chapter has largely been on the mechanisms by which a device’s internet layer (or OSI network layer) identifies itself and how it maps to the network interface (or OSI data link) layer. Internet layer protocols such as ARP and ICMP, that are important to routing, were also examined. The following chapter examines a newer version of IP, IP version 6, how it differs from IPv4, and why a new version of IP is needed.
Command | Description |
|---|---|
arp ip-address hardware-address type [alias] | Statically maps an IP address to a hardware address |
arp timeout seconds | Sets the amount of time a Cisco router holds ARP entries |
clear arp-cache | Forces the deletion of all dynamic entries from the ARP table |
debug ip icmp | Displays ICMP events as they occur on the router |
ip address ip-address mask [secondary] | Assigns an IP address and mask to an interface |
ip gratuitous-arp | Enables gratuitous ARP |
ip netmask-format {bit-count|decimal|hexadecimal} | Configures a router to display IP (address, mask) pairs in bitcount, dotted-decimal, or hexadecimal format |
ip proxy-arp | Enables proxy ARP |
ip redirects | Enables ICMP redirects |
[1] The OSI protocol suite itself has become, with some rare exceptions, a relic of early Internet history. Its current contribution to networking technology seems to be mainly limited to the usefulness of its reference model in illustrating modular protocol suites to networking students—and, of course, the IS-IS routing protocol still widely used in large service provider and carrier networks.
[2] BGP is an application layer protocol because it uses TCP to transport its messages, and RIP because it uses UDP for the same purposes. Other routing protocols such as OSPF are said to operate at the internet layer because they encapsulate their messages directly into IP packets.
[3] K. Nichols, S. Blake, F. Baker, and D. Black, “Definition of the Differentiated Services Field (DS Field) in the IPv4 and IPv6 Headers,” RFC 2474, December 1998.
[4] K. Ramakrishnan, “The Addition of Explicit Congestion Notification (ECN) to IP,” RFC 3168, September 2001.
[5] A fragmented packet is not reassembled at the other end of the data link; the packet stays fragmented until it reaches its final destination.
[6] Units of eight octets are used so that a maximum-size packet of 65,535 bytes might be described with 13 bits.
[7] As you will read in Chapter 2, the equivalent field in the IPv6 header has been renamed Hop Limit to more accurately reflect its true usage.
[8] Dotted decimal is used only with IPv4 addresses. As you will read in Chapter 2, IPv6 addresses are represented entirely differently.
[9] Devices use loopback addresses (typically 127.0.0.1) to send traffic to themselves. Data might be sent to this address and returned to the transmitting process without ever leaving the device.
[10] Notice that 223 does not exhaust all available numbers in the first octet. See Configuration Exercise 1 at the end of this chapter.
[11] The high-level organizations responsible for managing and assigning IP addresses are APNIC in Asia, ARIN in North America, LACNIC in Central and South America, and RIPE in EMEA.
[12] Actually, this address would never be assigned. It is from a group of addresses reserved for private use; most of the addresses used in this book are from this reserved pool, described in RFC 1918. Reserved addresses are 10.0.0.0–10.255.255.255, 172.16.0.0–172.31.255.255, and 192.168.0.0–192.168.255.255.
[13] Seventeen million data links might seem like a lot until you consider that even a single moderate-size business might have dozens or hundreds of data links.
[14] The all-hosts IP broadcast address is all ones: 255.255.255.255. An all-hosts broadcast for a particular subnet would set all host bits to one; for instance, an all-hosts broadcast for subnet 172.21.1.0 would be 172.21.1.255. Finally, a broadcast for all hosts on all subnets sets the subnet bits and the host bits to all ones: 172.21.255.255.
[15] NetWare, for example, makes the MAC address of the device the host portion of the network-level address—a very sensible thing to do.
[16] Like an IP broadcast, the MAC broadcast is an address of all ones: ffff.ffff.ffff.
[17] All numbers in use in various fields throughout the TCP/IP protocol suite were originally listed in: J. Postel and J. Reynolds, “Assigned Numbers,” RFC 1700, October 1994. This large document (230 pages) is a valuable reference, but is now a bit outdated. A current list of assigned numbers can be found at www.iana.org.
[18] Similarly, it can be said that the equivalent functions of the OSI session layer, residing above the transport layer, provide a logical, end-to-end path between two applications across a network.