CHAPTER 2 System Administration (Part 1)
Overview
As we stated in Chapter 1, the goal of information security is to protect information and information systems by ensuring confidentiality, integrity, and availability of information. You have seen some examples of how security can be breached and the consequences of such a breach. Evidently, businesses would like to defend themselves and their customers. So, how can they do that? The rest of this book is devoted to answering just this question. This chapter introduces you to system administration, one of the core components of an organization's response to information security concerns. At the end of this chapter, you should know:
- What is system administration
- Why system administration is important to information security
- What are the general system administration facilities provided by enterprise software systems
Introduction
The overall information security response by an organization has many components including standard procedures, user training, and managerial accountability. All of these will be addressed in the appropriate sequence in this text. However, the first line of defense is the effort undertaken by system administrators to secure critical information systems. The system administrator is the person who is responsible for the day-to-day operation of a technology system.1 Given the importance of information security for day-to-day technology operations, system administrators often also perform the role of system security officer. The system security officer is the person who is responsible for writing, enforcing, and reviewing security-operating procedures. System administrators are some of the most important IT personnel in an organization.
This chapter introduces you to system administration and describes why it is vitally important to information security. We then introduce you to some of the standard system administration facilities provided by common enterprise software using the major operating systems currently in use as examples. The hands-on activity in this chapter gives you the opportunity to download, install, and configure your own copy of a customized version of the Linux operating system. This operating system has been customized by the authors of this book and includes tested versions of the most common information security utilities used by system administrators. These utilities will be used in the hands-on activities in later chapters. The operating system also includes a mini-simulation of Sunshine State University, which you may find useful in the threaded design case on Sunshine State University used in the book.
Why introduce system administration so early in the text? And why emphasize hands-on system administration?
Effective system administration requires a good amount of discipline and technical skill. It takes time to develop these skills. It is tempting to relegate system administration to an appendix or to direct students to online resources to develop these skills. However, we believe that system administration is also a foundational skill for an aspiring information security professional. We therefore introduce the topic early in the text. We will use the hands-on activities after every chapter to help you refine your system administration and technical skills. Many students find this to be the most valuable component of this course. Most employers also value these skills for entry-level positions.
What is system administration?
System administration is a set of functions that provides support services, ensures reliable operations, promotes efficient use of the system, and ensures that prescribed service-quality objectives are met. System administration includes the installation, configuration, and maintenance of network equipment (switches, routers, DHCP, DNS servers, etc.) and computer systems (database systems, email systems, ERP systems, etc.). Depending on the size and complexity of the systems involved, the time required to provide these services could range from just a small portion of one IT person's time per week to an entire dedicated team of administrators, programmers. and support personnel. If you have ever installed new software or replaced faulty hardware in your PC, you have done the job of a system administrator, albeit on a small scale. At the other extreme, companies like Google employ thousands of system administrators and other personnel to support hundreds of thousands of computers.2 Every minute that a critical business system is off-line could mean thousands, even millions, of dollars of lost revenue. Therefore, skilled system administrators are highly sought-after in the industry.
Related trends – Cloud Computing
In response to the complexities of system administration, two major technology trends have emerged in recent years. Both of these trends fall under the category of cloud computing. Cloud computing is the delivery of software and other computer resources as a service, rather than a product and provided over the Internet.3 The first trend is Software as a Service (SaaS). Software as a Service is a software delivery mechanism in which an application and all of the associated resources are provided to organizations by the SaaS vendor, typically through a web browser. The SaaS provider provides all hardware and software and takes on the responsibility for all aspects of system administration. Pricing is typically as a subscription, with a per-user cost paid on a monthly or annual basis. Some SaaS applications are provided free of charge and provide revenue through displaying advertisements. If you have used any of the web-based applications such as Google Docs or used an online storage service such as DropBox, you have used a SaaS application.
The second major trend is Infrastructure as a Service (IaaS). Infrastructure as a Service is a business model in which an organization uses hardware equipment such as processors, storage, and routers from the IaaS provider. IaaS is also considered a form of cloud computing. Unlike SaaS, the IaaS provider provides only the hardware and takes responsibility for just the hardware installation and maintenance. All operating system and application administration must be performed by the organization's system administrators. Pricing is typically on a subscription basis and is based on usage (e.g., per GB of storage, per million CPU cycles). Amazon4 and Rackspace5 are some of the better known IaaS providers.
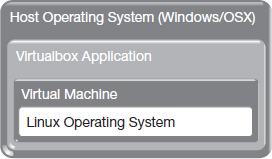
In recent years, system administrators have begun to deploy a technology called virtual machines to increase the efficiency of utilization of their computer hardware. A virtual machine is a software container into which an operating system and applications can be installed. Virtual machines function exactly like their physical counterparts but without the possibility of hardware failure. Virtual machines can be started and stopped on demand, so during times of business' peak load, such as the holiday season for an online merchant, new virtual machines can be started to run as web servers. Once the holidays are over and load returns to normal, the extra virtual servers can be removed. As an example of the utility of virtual machines, in the hands-on activity at the end of this chapter, you will create your own virtual machine and use the virtual machine for most hands-on activities in the rest of this book. When an organization hires an IaaS provider, they are buying access to a virtual machine.
Combining IaaS and virtual machines, instead of buying and maintaining enough physical servers to handle peak load, organizations can pay only for the exact number of servers they need, when they need them.
System administration and information security
At this point, you may be asking yourself “what does system administration have to do with information security?” In fact, system administration is the first line of defense for all the three dimensions of information security – confidentiality, integrity, and availability. Consider availability. If critical information, such as your grades, is not available because the server that it is stored on has failed and there is no way to recover it, you would be directly impacted by a system administration failure. It was the responsibility of the system administrator to anticipate this issue and use appropriate methods to prevent the hardware failure from affecting end users. For most system administrators, the majority of their time is spent planning for, repairing, and recovering from hardware failures. As another example, consider confidentiality. What if critical information, such as your transcript, was stolen from your university systems and put up on the web for anyone to see? This too would be a system administration failure. It was the responsibility of the concerned system administrator to anticipate this issue and use the appropriate file permissions to ensure that unauthorized people could not read or copy your transcript.
As you see, virtually everything that system administrators do is related to information security and most technical aspects of information security are addressed by system administrators. The next section describes some of the common tasks performed by system administrators and the section after that describes some of the common tools provided by enterprise software systems to help system administrators perform these tasks.
Common system administration tasks6
Every stage of using a technology involves system administration tasks. These tasks include installation and configuration of the system so it can be used, access control and user management so users can find what they need without inadvertently causing damage to the system, ongoing monitoring of the system to ensure all components are operating as expected, applying updates when monitoring reveals performance or security-related issues
Peter Bos, an engineer at MIT, is credited with using his privileges as a system administrator to send the world's first spam message in 1971. The message was addressed to about a thousand fellow engineers, including at the Pentagon. The intent of that first spam message was to:
| A | Sell used computers |
| B | Oppose the Vietnam war |
| C | Find a job |
| D | Recruit students to his lab |
(Answer on page 31)
Installation and configuration
Installation is the act of writing the necessary data in the appropriate locations on a computer's hard drive for running a software program. The first task when setting up a new computer is installing the operating system. If you have ever installed a version of Microsoft Windows or a Linux distribution, you are familiar with the process; you start the computer up with an installation disk, answer a few configuration questions, select which hard drive to install on, select which programs to install, then wait while the files are transferred. The steps are very similar no matter which OS you are installing. While the installation and configuration of software on one computer is quite straightforward, the challenge for system administrators is to streamline this process across hundreds or thousands of computers in the organization. In the next section, we provide an overview of some utilities commonly used for these tasks.
Configuration is the act of selecting one among many possible combinations of features of a system. Configuration has several information security implications. Complex configurations can create vulnerabilities due to the interactions among components and the inability of system administrators to fully comprehend the implications of these interactions. Many desirable software components are not maintained, creating information security hazards. For these reasons, whereas the general rule of thumb among consumers regarding configuration may be “when in doubt, install or update,” among professional system administrators it is “when in doubt, do not install.”
Access control and user management
Access control is the act of limiting access to information system resources only to authorized users, programs, processes, or other systems. Access controls establish what users can do on a system. Typically, this refers to which files or directories a user can read, modify, or delete, but in some operating systems, access to network ports and other OS-level structures can also be limited. Access controls can also be applied at the application level, limiting which rows and/or columns a user can see in a database or which screens are available in a business application.
A key component of access control is user management. User management refers to defining the rights of organizational members to information in the organization. Creating and removing user accounts are probably the first thing that people think of when they hear the term user management. However, user management also includes updating records appropriately when users change roles. To manage large numbers of users, it is common to organize users with similar privileges into groups. For instance, all faculty members in the Computer Science department can be made members of the Compsci-Faculty group. This group could then be used for granting access to certain resources on the department's website or as mailing list for email discussions.
The relationship between access control, user management, and the first two component portions of the CIA triad – confidentiality and integrity – is straightforward. A system administrator establishes access controls on pieces of information to ensure that only the authorized users are allowed to view (confidentiality) or modify (integrity) them. This process can be simple, but as the size of the organization and amount of data grows, the complexity and chance for error increases dramatically. We will look at these issues in depth in Chapter 7.
Monitoring and testing
Once installed, configured, and running, a system needs to be continuously monitored to ensure desired performance and security. Monitoring is the act of listening and/or recording the activities of a system to maintain performance and security. The system administration tasks in this category come in two varieties: reactive monitoring and proactive testing. Reactive monitoring is the act of detecting and analyzing failures after they have occurred. For example, administrators can use automated monitoring tools such as Nagios7 to get an overall view of the “health” of their network and instant notifications when problems occur. Similarly, log management tools collect and analyze the system logs from all of the servers across a network and correlate events between servers. Monitoring tools such as these assist system administrators in detecting unusual patterns or events, which may indicate a security compromise and, once a compromise is detected, how many systems are potentially affected.
Proactive testing is the act of testing a system for specific issues before they occur. One common practice is to use vulnerability scanners to access systems and look for potential vulnerabilities. These vulnerabilities can then be prioritized and resolved. Usually carried out by a professional security firm, penetration testing takes this one step further, actively exploiting vulnerabilities found and assessing the level of access that is gained.
Software updates
Ongoing use and monitoring of software usually reveal vulnerabilities or feature requirements. Software updates are used to fix these issues. A software update is the act of replacing defective software components with components in which the identified defects have been removed. Software updates can be broken into two categories: operating system updates and application updates. Operating system updates are software updates that fix issues with the low-level components of the system software and are developed and released by the operating system vendor directly. All modern operating systems include software for automatically checking for and installing required updates without system administrator intervention. Application updates fix problems in individual applications. These typically involve much more work on the system administrator's part because applications are often customized with plugins from other vendors and sometimes even by in-house developers. Many of these customizations are not well documented or well tested. It is not easy to predict the impact of an application update on these customizations. Therefore, manual updates are often necessary to deploy application updates.
Peter Bos
Answer: (B). The text of the message was: “There is no way to peace. Peace is the way.”
Keeping systems updated is extremely challenging in organizations because of the unpredictable behaviors of installed applications on updated systems. For this reason, system administrators typically install the update on a development server and test all applications on the development system before deploying the update to production systems.
Facebook, email discovery, system administration, and the law
Mark Zuckerberg started thefacebook.com on February 4, 2004, while still a student at Harvard. Over time, this site grew to become the well-known company – Facebook. About 9 months before launching the Facebook, while still a Harvard student, Mark had signed a contract with Paul Ceglia, an upstate New York serial entrepreneur to create a website called StreetFax. In 2010, Paul Ceglia filed a lawsuit in Buffalo New York, claiming that the StreetFax contract was in fact the contract for Facebook. According to the terms of the contract, Paul was entitled to a 50% stake in Facebook. At the time of the lawsuit, it was estimated that this stake could be worth as much as $50 billion. In support of his claim, Paul produced a copy of his contract with Mark.
Ok. So what does this have to do with information security in general and system administration in particular? Before you read further, pause to think for a moment what Facebook might be able to do to demonstrate that Paul's claim is false (Figure 2.1).
In its motion to dismiss the claim, Facebook produced the results of its search of Harvard's email server. Facebook's motion for dismissal states, “… [we reviewed] all of Zuckerberg's emails contained in the email account he used while a student at Harvard. That account contains emails from the 2003 to 2004 time period. The emails Ceglia quotes in his Amended Complaint do not exist in the account. They are complete fabrications…. [we ran searches] on all emails in the account using search terms containing the words and phrases taken from the purported emails excerpted in Ceglia's Amended Complaint…. the purported emails were not in Zuckerberg's email account…. not a single one exists on the Harvard server. What does exist in the Harvard account are numerous emails between Zuckerberg, Ceglia, and StreetFax employees concerning Ceglia's failure to pay Zuckerberg for his StreetFax work – and Ceglia's repeated pleas for forgiveness and his promises to scrape together the money he owed Zuckerberg. The real emails in Zuckerberg's account show that Zuckerberg never discussed Facebook or any social networking website with Ceglia or his colleagues, and that Ceglia's story of a purported “partnership” with Zuckerberg to launch Facebook is a complete fiction.
The article in Wired Magazine is quite detailed and worth a read for those interested in the matter.
References
- Paul D. Ceglia vs. Mark Elliott Zuckerberg, “Memorandum of law in support of defendant's motion to dismiss,” March 26, 2012.
- Raice, S. “A Facebook founder fight,” Wall Street Journal, March 27, 2012, B7.
- Kravets, D. “How forensics claims Facebook ownership contract is ‘forged’,” Wired Magazine, March 27, 2012, http://www.wired.com/threatlevel/2012/03/facebook-ownership-forensics/ (accessed 07/23/2013).
Single points of failure
The above are the standard system administration activities related to software that have information security implications. There is also one important system administration activity related to hardware with information security implications. A part of a system whose failure will stop the entire system from working is a single point of failure.8 Single points of failure have availability implications. For example, a common single point of failure in desktop computers is the power supply. If the power supply fails, the computer cannot function until a replacement is installed. The standard solution to deal with single points of failure is redundancy. Redundancy is surplus capability, which is maintained to improve the reliability of a system. For example, to minimize downtime, you could have a spare power supply ready to install right away. Extra parts like this are known as cold spares and are useful for minimizing downtime, but there is still some amount of time that the system would be unavailable. Most large computer servers utilize hot spares. Hot spares are redundant components that are actually housed inside the server and can replace the failed component with no downtime. Redundant components even allow system administrators to handle external failures as well. For instance, battery backups allow system administrators to deal with power failures (Figure 2.2).
What is the oldest email in any of your email accounts?
What is the subject matter of that email?
System administration utilities
Given the important role of system administration in an organization and the very high value of a system administrator's time, specialized system administration utilities have evolved over time for enterprise-grade hardware and software. In this section, we provide an overview of the common utilities available for the administration of common operating systems – Windows and Linux/UNIX. Similar system administration utilities are available for other enterprise systems as well – e.g., databases, routers, and hardware.
We first take a look at the general features of the two operating systems and then look at some popular system administration utilities for these two systems.
Microsoft Windows
With 92% of the desktop computer market as of April 2013,9 if you use a computer, it is most likely running Microsoft Windows. Since the mid-1990s when Windows 95 and Windows NT were released,10 Microsoft has released versions of Windows in two lines: desktop and server. The desktop line includes the familiar version numbers (Windows 95, 98, ME, XP, Vista, 7, 8) and includes support for the wide range of computer hardware and peripherals used on home computers. You have most likely used one or more of these versions. The server line (NT, 2000, 2003, 2008, 2008 R2, 2012) in contrast supports a much smaller set of hardware and peripherals and is focused on business desktops and the server market. The most important differentiator, however, is that the server line includes a number of services for access control and user management that are not available for the desktop line. The most important of these services are the Active Directory Domain Services.
Active Directory is a collection of technologies that provide centralized user management and access control across all computers that are “members” of the domain. Once domain memberships are defined, Group Policies can be applied to domain users and computers to control user access to features on specific computers in the organization. Microsoft defines group policy as an infrastructure that allows you to implement specific configurations for users and computers.11 Group Policies are often used to restrict certain actions that may pose potential security risks, e.g., to disable the downloading of executable files or to deny access to certain programs. The server that implements the active directory rules within a domain is called the Domain Controller for the domain. The Domain Controller maintains information on user accounts, authenticates users on the domain based on this information, and authorizes these users to access resources on the domain based on the group policy. Each domain requires at least one Domain Controller, but more can be added for redundancy.
System administration utility – System Center
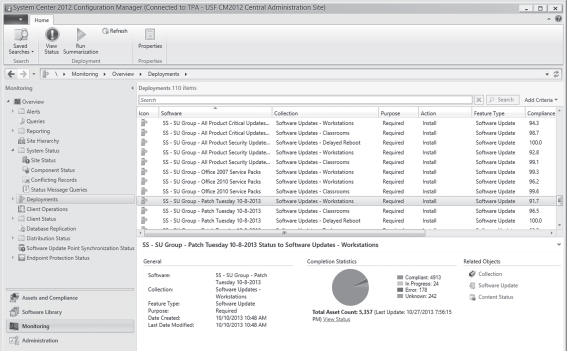
Microsoft provides several tools for securely installing and configuring Windows under the name System Center.12 The System Center Configuration Manager (SCCM) allows system administrators to manage the Windows installation process on hundreds of servers and desktops from one console, including the services and software to be installed. In addition to operating system installation, SCCM also automates the update process, both for Windows and other software packages that have been installed. The tools provided by System Center give a system administrator the ability to deploy new software or changes in a repeatable manner that can be easily automated and, more importantly for information security, audited.
System Center also includes a monitoring system called System Center Operations Manager (Figure 2.3), which can alert system administrators to hardware failures or other issues affecting the availability of data. Recognizing the developments of IaaS and virtual machines, SCCM can create or remove virtual servers to maintain the level of availability set by the system administrator.
Windows SysInternals
For personal use, you may like to use a set of utilities provided by Microsoft called System Internals, better known in the industry as SysInternals. They are available from Microsoft's website.13 These tools were first created by Mark Russinovich in 1996, and the company he founded, Winternals Software, was later acquired by Microsoft. SysInternals provides excellent visibility into the ongoing activities such as file and registry changes on a running computer. Many screenshots in this book use information from Sysinternals.
Unix/Linux
The Unix operating system was first developed under the name UNICS in 1969 by a group at AT&T's Bell Labs led by Ken Thompson and Dennis Ritchie.
Trivia
We can credit an early video game, Space Travel, for the development of UNIX – Thompson had originally written the game for an operating system (Multics) and hardware that the group no longer had access to. During the process of rewriting the game for new hardware, he wrote the basis of what would become Unix.14
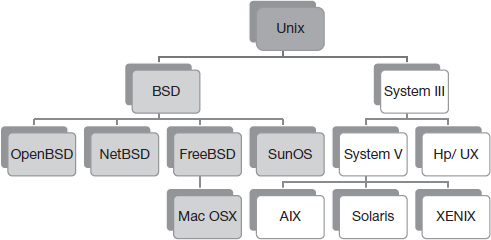
In 1975, AT&T licensed Unix to several educational and research institutions. Because the source code was provided with Unix, many of these institutions modified and extended Unix to meet their needs. The University of California, Berkley, released the Berkley Software Distribution (BSD) Unix in 1978, which introduced many enhancements that are still present in modern Unix systems.15 Dozens of Unix “flavors” have been released – each based on either the BSD or AT&T code-bases, but adding their own particular enhancements. The final AT&T version of Unix, System V, was released in 1988, but versions of Unix based on their code (referred to as SysV-based Unix) are still in development today.16 A family tree showing the most popular releases is shown in Figure 2.4.
Linux
In 1991, Linus Torvalds, a Computer Science graduate student at the University of Helsinki, released the first version of a new Unix-like operating system: Linux. Linux is referred to as Unix-like because it does not contain any source code from earlier Unix operating systems, but it provides an environment that includes virtually all of the tools and features provided by a BSD or SysV-based Unix. Linux was released as Open Source Software. Open source software is a software in which anyone is able to modify the source code and distribute his or her changes to the world. The motivation behind developing an independent code base and adopting the unique licensing model was to allow developers an opportunity to distribute their own innovations to the world, without being obstructed by the restrictions imposed by commercial operating systems. This free exchange of ideas in software was greatly enhanced by the rise in Internet-connectivity beginning in the mid-1990s. Instead of just one or two students at a university or a few dozen developers at a commercial software vendor, Linux soon had thousands of developers from around the world working to improve it.17 In the two decades since it was first released, Linux has been modified to run on everything from supercomputers to cell phones. With many GPS devices, home wireless routers, Android devices, and the Amazon Kindle using Linux for their operating system, chances are you have used a device running the Linux operating system. Also, as of November 2012, all of the world's 10 fastest supercomputers use Linux as the operating system.18
An interesting result of the open nature and flexibility of Linux is the number of different Linux versions that have been created. Everyone is free to create their own Linux “distribution,” and there are literally hundreds in active development.19 Unlike Microsoft Windows and the commercial Unix operating systems, there is not an “official” version of the Linux operating system, but there are several major distributions. By far, the most common Linux distribution in a business setting is Red Hat Enterprise Linux (RHEL). RHEL is a commercial Linux distribution, but Red Hat also freely provides the source code for the entire operating system. The developers of the CentOS project20 have compiled this source code and built a free Linux operating system that is nearly identical to RHEL. All of the hands-on activities in this text, beginning with the one at the end of this chapter, will utilize a customized version of CentOS.
System administration utilities
Automated operating system installation and configuration tools have many names in the Unix and Linux world (Jumpstart on Oracle Solaris, Kickstart on RHEL, and Network Installation Manager on IBM AIX to name just a few), but they all work in a very similar fashion. The system administrator creates a file that contains instructions on how to configure network devices, hard drives and any other common hardware, and a list of software packages that should be installed. Finally, it includes any post-install programs that need to be run to finish the configuration process.
Several applications provide cross-platform support for configuring software after operating system installation.21 The most popular of these packages is Puppet,22 which is used heavily by major Internet companies such as Google and Twitter. A system administrator creates a “puppet manifest” which lists the software to be installed and the desired configuration, the manifest can then be sent to one or more remote servers, and the software is installed, regardless of the underlying operating system.
SUMMARY
This chapter sets the groundwork for the technical component of this course. System administrators perform most of the technical activities related to information security. This chapter therefore defined system administration and introduced the role played by system administrators in organizations. It also introduced the common information security tasks performed by system administrators. Finally, it provided an overview of the common utilities used to simplify these tasks in large organizations.
The hands-on activity in this chapter will lay the stage for the hands-on activities you will perform in all the remaining chapters of this book.
EXAMPLE CASE–T.J. MAXX
Corporate interest in information security was dramatically raised in 2007 following the revelations of embarrassing information security breaches at several well-known companies. Hackers had complete access to credit-card databases at many of the leading retailers in the country including T.J. Maxx, Barnes and Noble, and Office Max (Figure 2.5).
Hackers know that it is safe to be outside the target country to avoid prosecution. It was therefore initially believed that the attacks were caused by hackers outside the country. However, investigations revealed that the attacks were mostly from domestic sources and led to the prosecution of 11 men in 5 countries, including the United States. Most interestingly, the ringleader turned out to have been an informer for the US Secret Service.
Outcome
On August 5, 2008, the US government charged 11 individuals with wire fraud, damage to computer systems, conspiracy, criminal forfeiture, and other related charges for stealing credit-card information from prominent retailers such as T.J. Maxx, BJ's Wholesale Club, Office Max, and Barnes and Noble.
In August 2009, many members of the same gang were again charged with compromising Heartland Payment Systems, a credit-card processing company, and stealing approximately 130 million credit-card numbers. With approximately 100 million families in the United States, this translates to almost 1 credit card stolen from every American family. 5 members of the gang were indicted on July 25, 2013.23,24
Background
The gang involved in all these incidents had been in operation since 2003. Between 2003 and 2007, the gang used simple methods to exploit weaknesses in wireless security at retail stores. At T.J. Maxx, they had found that many stores did not use any security measures in their store wireless networks. As a result, obtaining employee user names and passwords was as simple as waiting outside the stores in the morning with laptops and listening to the network traffic as employees and managers logged into their accounts.
Worse, these user accounts had access to the corporate IT systems at T.J. Maxx, including those that stored credit-card information. Using this information, the hackers had a free run of the company's credit-card information. For almost a year, the gang members extracted the data, stored it on the company's own servers, and retrieved it at their own convenience. Their goal was to use this information to sell fake credit cards at pennies on the dollar.
This was the method used by the gang in the attacks that formed the basis of the 2008 indictment. Beginning in August 2007, the gang refined its skill set and began to use SQL injection attacks to place malware on web applications and gain access to corporate databases. The gang used this method in the attacks for which it was indicted in 2009.
The ring leader and his activities
Albert Gonzalez, the ringleader of the gang, was a resident of Miami, Florida. Beginning around 2003, he is believed to have driven around Miami, using his laptop computer to locate insecure wireless access points at retail stores. Stores typically use these networks to transfer credit-card information from cash registers to store servers. When an open network was located, the gang would use a custom-written “sniffer” program to collect credit-card account numbers (one of the most popular sniffers is Wireshark, an easy to use program that is available for free use25). Fake cards using these numbers were then sold in the gray market. The biggest victim was T.J. Maxx, which lost information on over 40 million credit cards.
Later, when the gang graduated to SQL injection attacks, it would visit stores to identify the transaction processing systems these companies used. The gang used this information to determine suitable attack strategies to target the specific systems used by these companies. The gang also studied the companies' websites to identify their web applications and to develop appropriate attack strategies for these websites.
The ringleader, Albert Gonzalez, earned over $1 million in profits by selling this card information. Apparently, at one time, his counting machine broke and he had to manually count $340,000 in $20 bills. In August 2009, Albert Gonzalez agreed to plead guilty to charges in the T.J. Maxx case, which had been filed in 2008.
Gonzalez became an informant for the Secret Service in 2003 after being arrested for various crimes. As an informant for the Secret Service, in October 2004, he helped the Secret Service indict 28 members of a website Shadowcrew.com. Shadowcrew stole credit-card information and sold it for profit. While in operation, Shadowcrew members stole tens of thousands of credit-card numbers. After the Shadowcrew operation was completed, however, Albert began his own exploits.
Impact
The direct damage from the attacks in terms of fraudulent charges on customer credit cards was limited. In March 2007, one gang in Florida was caught using cards stolen from T.J. Maxx (TJX) to buy approximately $8 million in goods at various Wal-Marts and Sam's Club stores in Florida. However, the collateral damage from the incident has been colossal. TJX Companies, Inc. (TJX) (T.J. Maxx Stores is one of the companies owned by the group, Marshalls is another) settled with Visa for $40 million in November 2007 and with MasterCard in April 2008 for $24 million.
The impact was nationwide. Tens of millions of customers had to be reissued credit cards. Customers who had set up automated payments on the stolen cards received collection notices from service providers when charges did not go through because the cards had been canceled and new ones had been issued in their place.
Surprisingly, sales at T.J. Maxx do not seem to have been significantly affected by the intrusion (Figure 2.6). Fraudulent expenses were refunded to customers by the credit-card companies through the automatic protection programs offered by credit cards. Customers do not seem to mind their cards information stolen so long as they are not held liable for fraudulent transactions.
Significance
The T.J. Maxx case is significant for the study of information security and its relationship with other professions because the case has been extensively documented in the press. In addition, details are also available from the indictments made in the case. These readings provide a rich account of the actors involved in information security, their motivations. and the legal processes that follow major information security incidents.
REFERENCES
Pereira, J. “How credit-card data went out wireless door,” Wall Street Journal, May 4, 2007.
Pereira, J., Levitz, J. and Singer-Vine, J. “U.S. indicts 11 in global credit-card scheme,” Wall Street Journal, August 6, 2008: A1.
United States of America vs. Albert Gonzalez, Criminal indictment in US District Court, Massachusetts, August 5, 2008 (the T.J. Maxxcase).
United States of America vs. Albert Gonzalez, Criminal indictment in US District Court, New Jersey, August 17, 2009 (the Heartland case).
Zetter, K. “TJX Hacker was awash in cash; his penniless coder faces prison,” Wired, June 18, 2009.
Gorman, S. “Arrest in Epic Cyber Swindle,” Wall Street Journal, August 18, 2009.
Gorman, S. “Hacker sentenced to 20 years in massive data theft,” Wall Street Journal, 2010: A1.
“Albert Gonzalez,” Wikipedia, http://en.wikipedia.org/wiki/Albert_Gonzalez.
T.J. Maxx, 10-K reports, 2006–2010.
T.J. Maxx, 8-K filing, January 18, 2007; April 2, 2008; November 30, 2007.
CHAPTER REVIEW QUESTIONS
- What is system administration?
- Why is system administration important?
- Who is a system administrator?
- What are some of the important day-to-day activities performed by system administrators?
- Define Infrastructure as a Service (IaaS).
- What are some of the benefits of using an IaaS provider?
- What is a virtual server?
- What are some benefits of virtualization?
- What is the role of a system administrator in maintaining information security in an organization?
- What is software configuration?
- How does software configuration impact information security?
- Define access control. How can weak access controls impact information security?
- Define user management. How does user management impact information security?
- What is monitoring? How does it help information security?
- What is reactive monitoring? What are some common reactive monitoring methods?
- What is proactive testing? What are some common proactive testing methods?
- What is a system update? What are the challenges in keeping systems updated? Why is it important for information security?
- What is a single point of failure? How do system administrators typically deal with single points of failure?
- What is the difference between cold spares and hot spares?
- What is Active Directory? What role does it play in maintaining information security on Windows computers?
- What are group policies? How do group policies assist system administrators in maintaining information security?
- What is a domain controller?
- Provide a brief description (two to three sentences maximum) of the information security features of the latest version of Microsoft's System Center or comparable product.
- What is Linux? Why is it popular? What are some of the most popular distributions of Linux?
- Provide a brief overview (two to three sentences maximum) of the capabilities of Puppet, the IT automation software used by many system administrators.
EXAMPLE CASE QUESTIONS
- Based on the information provided above, list as many example of violation of confidentiality, integrity, and availability identified in the case.
- Based on the case, identify the failures in execution of the common system administration tasks at T.J. Maxx at the time of the case.
- If you were responsible for system administration at T.J. Maxx, what are the things you would have done to prevent the occurrence of the incidents reported in the case?
HANDS-ON ACTIVITY–LINUX SYSTEM INSTALLATION
Disclaimer
The activities you are about to perform can harm your computer if not done correctly. While every effort has been made to prevent mishaps, please note that it is ultimately your responsibility to protect the data on your computer and your computer itself.
In order to get practical hands-on experience on essential information security and system administration skills, the book includes a series of hands-on activities, which use the Linux operating system. You will create the required environment as the hands-on activities in this chapter. When you complete the activity, you will have your own working copy of CentOS Linux (http://centos.org) that we have configured for use with this course. In our experience, at the end of the course, students find these hands-on activities to be the most useful component of this course, and in fact, one of the most interesting activities in their college studies. The specific configuration used here has been chosen because it allows you to create the required infrastructure on almost any computer you may own. We have taken considerable effort to make this resource available for you because these are skills that are highly sought after by employers and which differentiate you from competitors in the marketplace. We hope you find these activities as exciting as we are excited about creating them (Figure 2.7).
The activity for this chapter is completed in two steps. In the first step, you will install VirtualBox, a virtualization environment. In the second step, you will use VirtualBox to create a virtual machine containing a preconfigured Linux operating system.
Step 1 – Installing VirtualBox
Before you begin, note the minimum system requirements:
- Windows XP, Windows 7, Windows Server 2003, or Windows Server 2008
- Macintosh OSX 10.5 or greater
- 2 GB of RAM
- 10 GB free hard drive space
VirtualBox is an open source computer application that can be installed on any computer running an Intel or AMD processor to create virtual machines on the computer. Guest operating systems can be installed on these virtual machines so that a Windows computer with adequate storage and processing power can run multiple operating systems. Follow these steps to install VirtualBox on your personal computer. At the time of this writing, the product is being updated very rapidly, so your version numbers may differ from those shown here. It should be safe to follow the configuration management rule for consumers, “when in doubt, install the latest version.” For more details on VirtualBox, check the VirtualBox manual,26 particularly Chapter 1 of the manual.
- Visit the VirtualBox download page (Figure 2.8) to obtain the installer. This URL changes often; it is best to search for “Download VirtualBox” to locate this link. The page looks as below. Download the appropriate installer for your system. The instructions below are for Windows. The procedure for other systems will be similar.
- Double-click the downloaded file to start the installation. Click “Next” on the welcome screen (Figure 2.9) to begin the installation.
- You are now asked to select the location where you would like to install VirtualBox. The default location is your Program Files folder. Click “next” if the default install location is OK (Figure 2.10).
- The installation now proceeds like any normal application. You may receive an alert from the UAC (user acceptance control). Allow the installation and proceed through the screens by clicking “Next.”
- You may receive a warning that your network connections will be restarted. If you have any network traffic (file downloads, music streaming, etc), you may want to wait until those transfers are complete before proceeding.
- If you are asked whether you would like to install USB support, it is recommended that you elect to do so.
- Click “Finish” to complete the installation. When installation is complete, you will see the confirmation (Figure 2.11). If you enable the checkbox to start VirtualBox, you will see the VirtualBox manager (Figure 2.12). It is currently empty. You will populate it with your own customized Linux operating system in the next step of this exercise.
Step 2 – Install the OS
As you may have read in the VirtualBox documentation, you can install almost any modern desktop operating system as a guest OS. For this book, we have customized a distribution of Linux. Using Linux in allows us to circumvent commercial licensing limitations. Fortunately, most security concepts are generalizable across operating systems and most of the general concepts you will learn here also apply to Windows. Follow the instructions below to install the customized Linux distribution in a new virtual machine on your computer:
- Download the CentOS Linux virtual image from the companion website for the text. The .ova file extension stands for “Open Virtual Appliance,” an industry standard for operating systems packaged for installation into a virtual machine.27 The format was created by VMWare, a leading firm in the virtualization industry. Note that this is a VERY large (over 2.5 GB) file and can take several hours to download, even over broadband.
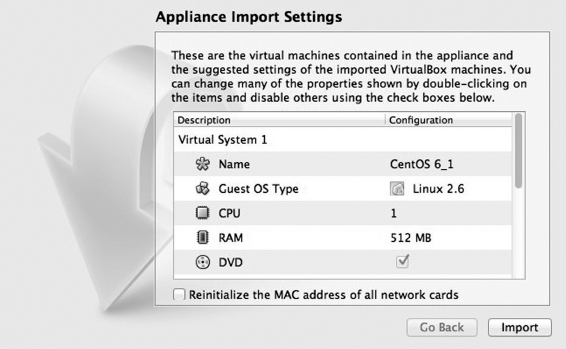
- Double-click on the CentOS_6.ova file, the “Appliance Import Wizard” will start. The default values should be fine, and you can start the process of creating your virtual machine by clicking “import,” as shown in Figure 2.13. The import may take 10–20 minutes depending upon the speed of the computer and the location of the installation.
- When the installation is complete, the VirtualBox manager shows the new VM in the list of VMs (Figure 2.14). You can now start VirtualBox at any time, select the VM and click on “start” to start up the VM. When the VM is running, you can click on “stop” to terminate the VM.
- At this point, you are probably eager to see what all this leads to. After the virtual machine has been imported, click on “Start.” The Linux operating system will start. Common issues and their solutions are listed below. After any such issues are resolved, you will see the CentOS Linux login screen.
Known issues
- You may get a warning suggesting that you download and install the expansion pack since your computer had USB 2.0 enabled. You may ignore this message, or if you feel comfortable, you may download and install the extension pack available on the VirtualBox website.
- You may get warning messages regarding mouse movements, window size, etc. These may be ignored.
- If you get an error message that says that indicates a problem with the CPU, please select the VM, select “Settings” in the VM manager, then System →Processor and select the “enable PAE checkbox (Figures 2.15 and 2.16).”
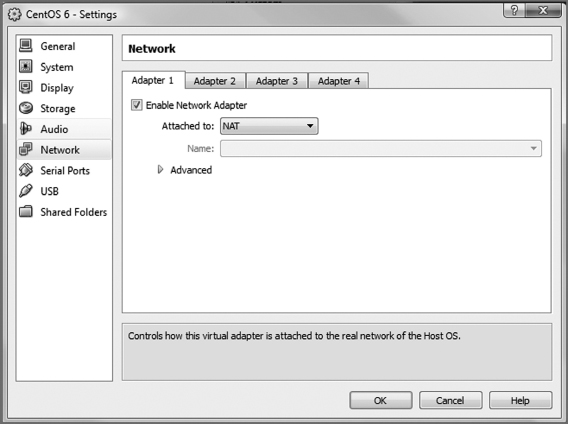
- If you are unable to connect to the network, go to settings → network and attach the network adapter 1 to the NAT as shown in Figure 2.17. You may also be able to just scroll down on the front page and select “Network.”
Starting the virtual machine
- When the virtual machine boots up, you will see the login screen as shown in Figure 2.18.
- At the Login prompt enter the username alice and use the password aisforapple. This will bring up the CentOS desktop as shown in Figure 2.19.
- To stop the virtual machine, select Machine → Close (Virtual Box → Quit on OS X) from the running CentOS VM window.
- To start the machine again, use Start → Programs → Oracle VM VirtualBox → Oracle VM VirtualBox (Applications → Virtual Box in OS X).
- In the next chapter, you will learn some basic UNIX/Linux system administration, including folder navigation, using the vi editor, and creating user accounts.
Hands-on activity questions
- Provide a brief description of VirtualBox and its uses.
- Provide a brief description of the OVA file format.
To demonstrate that you have successfully installed the VM, submit the following:
- A screenshot of the CentOS desktop.
- Start the browser using Applications → Internet → Firefox web browser. Submit a screenshot of the browser window showing the default home page of the browser.
- Start the system monitor using Applications → System tools → System monitor. Submit a screenshot of the System monitor.
- Start the terminal by selecting Applications → System Tools → Terminal. At the prompt, type in the command “whoami.” Submit a screenshot of the terminal window showing the command and its output. (Most of the hands-on activities in the book will make extensive use of this terminal window.)
- Stop the VM by selecting Machine → Close → Poweroff the machine.
CRITICAL THINKING EXERCISE–GOOGLE EXECUTIVES SENTENCED TO PRISON OVER VIDEO
In September 2006, four classmates bullied a boy suffering from autism at their school in Turin, Italy, and uploaded the clip to Google video (the predecessor to YouTube). The video became popular and was viewed over 5,500 times over the next 2 months and even reached the top of the list of “most entertaining” videos at Google's Italian site.
When Google was notified about it by Italian Police, Google removed the video. However, the boy's father and Vivi Down, an organization representing people with Down's syndrome, sued four Google executives for defamation and illegal personal data handling. Google claims it was swift in removing the video upon being alerted.
On February 24, 2010, the Court of Milan acquitted all executives of the defamation charge, but held three executives guilty of illegal personal data handling and being slow to remove the video upon being informed about it by the police. They were senior vice president and chief legal officer David Drummond, former Google Italy board member George De Los Reyes, and global privacy counsel Peter Fleischer. Personal liability was assigned because corporate officers are held legally liable for a company's actions in Italian law. None of the executives was present in Italy for the hearing and since the sentence was suspended pending appeal, none were under immediate threat of imprisonment.
Google's stand, articulated by its communications manager, was that “They didn't upload it, they didn't film it, they didn't review it and yet they have been found guilty.” In his 111-page judgment, the judge Oscar Magi wrote “the Internet [is] not an unlimited prairie where everything is permitted and nothing can be prohibited…. Instead, there were laws regulating behavior and if those laws were not respected, ‘penal consequences’ could ensue.” According to Italian law, not stopping a fact is equivalent to causing it. The data protection law requires prior authorization before handling personal data and the posted video was personal data. Therefore, Google was responsible for ensuring that the user who posted the video had the consent of everyone involved in the video.
On December 21, 2012, an Italian appeals court overturned the conviction and acquitted the executives.
REFERENCES
Manuela D’ Alessandro, “Google executives convicted for Italy autism video,” 02/24/2010, http://www.reuters.com/article/2010/02/24/us-italy-google-conviction-idUSTRE61N2G520100224 (accessed 07/16/2013).
Hooper, J. “Google executives convicted in Italy over abuse video,” The Guardian, 02/24/2010, http://www.guardian.co.uk/technology/2010/feb/24/google-video-italy-privacy-convictions (accessed 07/16/2013)
Povoledo, E. “Italian judge cites profit as justifying a Google conviction,” New York Times, April 12, 2010.
EDRi-gram, “First decision in the Italian criminal case against Google executives,” 02/24/2010, http://www.edri.org/edrigram/number8.4/decision-italy-vs-google-executives (accessed 07/16/2013).
Pfanner, E. “Italian appeals court acquits 3 Google executives in privacy case,” New York Times, December 21, 2012.
CRITICAL THINKING QUESTIONS
- What is your opinion about the incident?
- Should system administrators and companies be responsible for the content posted by users of a website?
- Say you are the system administrator of a website and you receive a request from a user to delete a picture uploaded by a friend at a party that includes the user. Would you consider the request reasonable?
- How would you respond to such a request?
DESIGN CASE
For this design case, we will use the Sunshine State University used on the first chapter. Like many other IT-related services at the University, email support is divided into two major systems:
- Information technology, which reports to the VP of Business and Finance, supports email for all administrative personnel. For historical reasons, the Provost Office pays IT for support of faculty email as well.
- Student email is supported by the technical staff reporting to the Dean of Students.
The current Student Email system runs on a single server purchased 6 years ago. The server has two internal drives. The internal drives contain the operating system and applications and an external JBOD holds all the data. The server has a single power supply and a single network port. The server runs Linux and the open source SMTP program Sendmail for email delivery.
A recent hardware issue brought the Student Email Servers crashing. The first time this happened, there was an outage of 13 hours. Unfortunately, the root cause of the initial outage was not determined and problem happened again but this time things were a bit more serious: a critical storage failure caused all of the emails to be lost. The System Administrator in charge of the server could not handle the pressure and resigned. You were the Student Assistant to the Sys Admin. The Dean of Students is in a bit of a bind and offers you a job with great pay, benefits, and tuition waiver program to help you finish your degree.28
Two weeks later the server is back online and all email has been recovered from tape. The failure happened at 1:00 p.m. on a Wednesday. The last backup ran at 2:00 a.m. on Tuesday. Email delivered between those times was irrevocably lost.
The student population is up in arms and the Provost gets involved. Together with the Dean of Students, you are asked to recommend a choice for email service among the following options, along with your reasons for the same:
- Maintain email services locally
- Replace the entire email infrastructure with a SaaS email solution
- GoogleApps for Education (http://www.google.com/apps/intl/en/edu).
SECURITY DESIGN CASE QUESTIONS
- What is a JBOD anyway?
- As you research your options for Sunshine State University, you are advised to start with a common procedure – looking at what your closest peers are doing. Businesses call this benchmarking. In your context, this means what peer universities are doing in terms of email systems.
- List three universities or colleges in your area that you would consider the closest peers to Sunshine State. (Keep this list handy. You will find yourself returning to this list often to research what these schools are doing to address the challenges you face in this and later chapters.)
- Which of these options has each of the institutions selected for email service? Why did they select this choice? (You may find information regarding this on their websites. You can also call their technical support help line).
- If your own institution is not on the list in (a), what is your own institution doing for email service? Why?
- What problems can you anticipate from Sunshine State's current system as shown in Figure 2.20? What are the single points of failure? What would have to happen for the local system to be able to safely handle email service if any of these single points of failure were to fail?
- What features (if any) do the cloud service models (IaaS and SaaS) offer that could not be currently provided locally?
- During your research you find that one of the common queries fielded by technical support is restoration of accidentally deleted email. What facilities (if any) does each alternative provide in the restoration of accidentally deleted emails?
- Another important feature request from the student body is email access from a wide variety of devices, especially non-web clients such as smart phones and traditional email clients such as Thunderbird and Eudora. What support does each of the choices provide for email access from these devices. What advantages or disadvantages does each system have for such access?
1ATIS Telecom glossary: http://www.atis.org/glossary/default.aspx
2http://www.datacenterknowledge.com/archives/2011/08/01/report-google-uses-about-900000-servers/
3http://en.wikipedia.org/wiki/Cloud_computing
5http://www.rackspace.com/cloud/
1. · Morozov, E. “The common enemy,” WSJ Book Review, May 9, 2013.
2. Brunton, F. “Spam: a shadow history of the Internet (infrastructures),” MIT Press, ISBN 026201887X.
8http://en.wikipedia.org/wiki/Single_point_of_failure
10http://windows.microsoft.com/en-US/windows/history
11http://technet.microsoft.com/en-us/library/cc779838(v=ws.10).aspx
12http://www.microsoft.com/en-us/server-cloud/system-center
13At the time of writing (April 2012, the URL was http://technet.microsoft.com/en-us/sysinternals/bb545021
14http://www.livinginternet.com/i/iw_unix_dev.htm
15http://en.wikipedia.org/wiki/Berkeley_Software_Distribution
16http://www.levenez.com/unix/
17http://www.ragibhasan.com/linux
18http://www.top500.org/lists/2012/11
19http://distrowatch.com/search.php?ostype=Linux&category=All
21http://en.wikipedia.org/wiki/Comparison_of_open_source_configuration_management_software
22http://projects.puppetlabs.com/projects/puppet
23http://www.justice.gov/opa/pr/2013/July/13-crm-842.html (accessed 10/11/13)
24http://www.justice.gov/iso/opa/resources/5182013725111217608630.pdf
26https://www.virtualbox.org/manual/
27For more details, see http://www.fileinfo.com/extension/ova
28While there is some dramatization, the scenario is based on an actual incident.