Security in IEEE 802.16m
Several changes and enhancements are introduced in the amendment for IEEE 802.16m. Figure 8.2 shows the counterpart for the security sublayer in .16m, called the Security Architecture.
Within the AMS and the ABS security architecture, there are two logical entites: the security management entity and the encryption and integrity entity.
The security management entity functions include:
- Overall security management and control;
- EAP encapsulation/decapsulation for authentication;
- Privacy Key Management (PKM) control (e.g., key generation/derviation/distribution, key state management);
- Authentication and Security Association (SA) control; and
- Location Privacy.
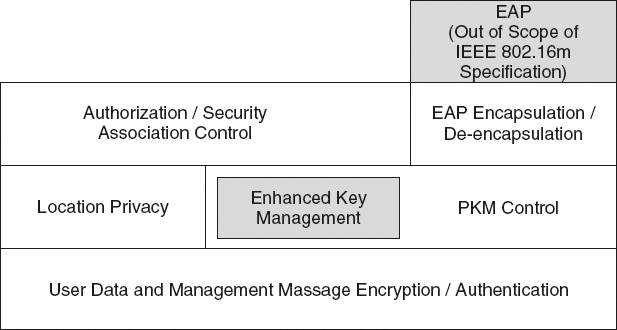
Figure 8.2 Security Architecture in 16m. Reproduced by permission of © 2009 IEEE.
The encryption and integrity protection entity functions include:
- Transport data encryption/authentication processing;
- Management message authentication processing; and
- Management message confidentiality protection.
However, certain noteworthy changes and enhancements are described below.
- All authentications between AMS and ABS take place in EAP;
- Only unicast static SAs are supported;
- Station IDs are introduced whereby a station's MAC can be made private;
- The introduction of Null SAIDs to accommodate mixed (secure/nonsecure) flow mixes;
- Mapping multiplexed payloads onto SAs;
- The possibility of encrypting MAC control message in three levels: no encryption, encrypted payload; encrypted payload and header.
Supported security modes for relaying include centralized and distributed.
For multicarrier communication, all security messaging is performed for the AMS's primary multicarrier.
Note that the draft does not detail how security is managed between Advanced and legacy systems.
