Amazon QuickSight servers need access to RDS instances and Redshift clusters that you want it to connect to. In the next few sections, we will see how to enable these connections to QuickSight.
It is a good practice to have a separate security group that can enable QuickSight to access RDS instances, Redshift, and EC2 instances. In this section we will look into the steps for creating this new security group.
Use the following steps to create a new security group with permissions to QuickSight:
- From the AWS services listing, select the VPC service, which can also be accessed by using this URL: https://console.aws.amazon.com/vpc/. From here, click on Security Groups and then on the Create Security Group button as shown here:

Figure 5.9: Create new security group
- This will result in a popup to create a new security group. Enter the Name tag as
QuickSightAccess, Group name asQuickSightAccess, and a Description as shown in the next figure. Ensure that the VPC identifier is same as that of the RDS instance it is associated with. Once you are done, click on Yes, Create:
Figure 5.10: New security group
- The new security group will have default settings with no inbound rules; click on Edit to configure this:

Figure 5.11: Inbound rules edit
- Next set the new rule with Type as Custom TCP Rule, Protocol as TCP (5), Port Range as appropriate for the RDS instances you want to be opened, and the source IP address range of the QuickSight servers
52.23.63.224/27. This is shown in the following screenshot. Once you have filled it, click on Save to retain these changes:
Figure 5.12: Inbound rules setup
This completes the setup of a separate security group for QuickSight.
For Amazon QuickSight to connect to RDS instances, you need to set the VPC that has inbound rule authorization access from the IP range of QuickSight servers created in the previous section Creating a new security group for QuickSight.
Use the following steps to enable QuickSight access to RDS instances:
- First navigate to the RDS service and select the RDS instance that you wish to grant access to. You can use the following URL to get the RDS service: https://console.aws.amazon.com/rds.
- Next, click on Instance Actions and select Modify as shown in this screenshot:

Figure 5.13: Modify RDS instance
- In the Network & Security section, select the newly created security group QuickSightAccess and then click on Continue to save the changes.
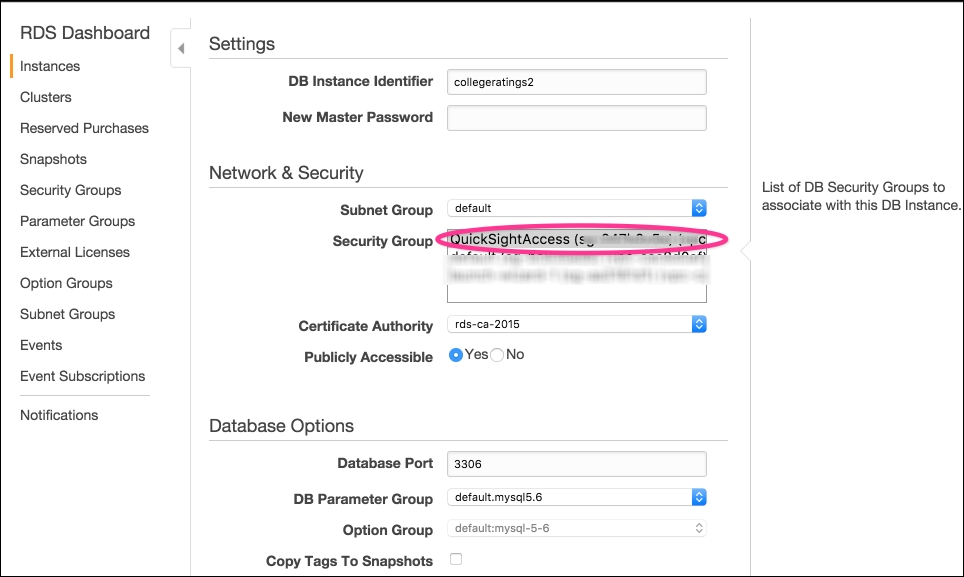
Figure 5.14: Associate QuickSight with RDS
- Now, your RDS instance is set up correctly so that QuickSight can access it. You can validate this by going to the QuickSight Manage data page; select the RDS instance, add the username and password, and click on the Validated button, as shown here:

Figure 5.15: Validate RDS connectivity
For Amazon QuickSight to connect to Redshift cluster, you need to set the VPC that has inbound rule authorization access from the IP range of QuickSight servers created in the previous section, Creating a new security group for QuickSight.
Use the following steps to enable QuickSight access to Redshift cluster:
- First navigate to the Redshift service page, which you can access using the URL:https://console.aws.amazon.com/redshift/.
- From here, select the Redshift cluster you wish to grant access to, as shown in this screenshot:

Figure 5.16: Redshift clusters
- Next, you need to modify the cluster and select the VPC security group that QuickSightAccess created in the Creating new security group for QuickSight section. Finally click on the Modify button to preserve the changes, as shown here:

Figure 5.17: Modify Redshift
- This completes the setup of the Redshift cluster for QuickSight; now let's verify that these changes are working by going to QuickSight home page and adding a new data source for this Redshift database:

Figure 5.18: Redshift verification
This completes the Redshift setup so that QuickSight has access to it.
For Amazon QuickSight to connect to EC2 instances, you need to set the VPC that has inbound rule authorization access from the IP range of QuickSight servers created in the previous section, Creating a new security group for QuickSight.
Use the following steps to enable QuickSight access to RDS instances:
- First navigate to the EC2 Service at the following URL:https://console.aws.amazon.com/ec2.
- Next, select the instance that you want to grant access to. Click on
Actionsand then Networking. Select Change Security Groups as shown in this screenshot:
Figure 5.19: Select EC2 instance
- Next, you will see a new page pop up with the various security groups; select QuickSightAccess, which we previously created, and click on Assign Security Groups as shown here:

Figure 5.20: Change security groups for EC2
This completes the EC2 setup so that QuickSight has access to this box.
