LTE Security Architecture
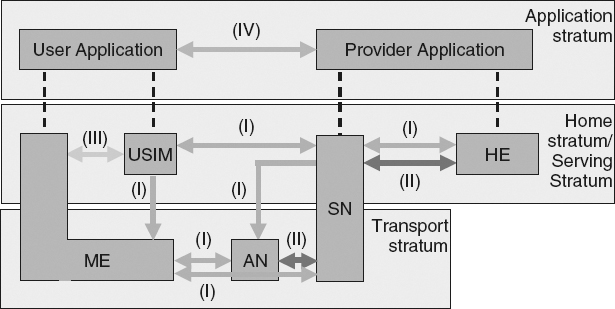
Figure 14.2 gives an overview of the complete security architecture for LTE. The stratums identified, each addressing a sufficiently isolated category of security threats, are the application, home, serving and transport stratum.
Figure 14.2 Overview of LTE Security Architecture. Reproduced by permission of © 2010 3GPP. Further use is strictly prohibited.
As can be noted in the figure, there are five sets of security features the 3GPP define:
- (I) Network access security: The set of security features that provide users with secure access to services, and which in particular protect against attacks on the (radio) access link.
- (II) Network domain security: The set of security features that enable nodes to securely exchange signaling data, user data (between the Access Network (AN) and the Serving Network (SN), and within the AN), and protect against attacks on the wireline network.
- (III) User domain security: The set of security features that secure access to mobile stations.
- (IV) Application domain security: The set of security features that enable applications in the user and in the provider domain to securely exchange messages.
- (V) Visibility and configurability of security: The set of features that enables the user to inform himself whether a security feature is in operation or not and whether the use and provision of services should depend on the security feature.
In what follows, we elaborate on some of these feature sets.
Network access security entails specific feature such as user identity confidentiality, entity authentication, general confidentiality of certain agreement and data exchanges, and data integrity. Identity confidentiality is normally achieved by assigning short-lived temporary identities to ensure confidentiality of both user identity and location, and user untraceability. Meanwhile, entity authentication applies to both user and network authentication. Realizing entity authentication is made possible through authentication at each connection set up between the network and the user. General confidentiality applies to cipher algorithm and key agreements, and user and signaling data. Finally, integrity algorithm and key agreements, in addition to data integrity and origin authentication of signaling data are all properties achieved various mechanisms.
Table 14.1 Security Termination Points. Reproduced by permission of © 2010 3GPP. Further use is strictly prohibited

Ciphering may be provided to RRC-signaling to prevent UE tracking on over-the-air RRC exchanges, for example, for measurements or handover. NAS signaling may also be confidentiality protected. Confidentiality of user plane exchanges should be made at the PDCP layer. This measure, however, is optional. Meanwhile, integrity shall be provided (i.e., is mandatory) for both NAS and RRC-signaling. These measures will be described below. Table 14.1 shows the termination points for the NAS signaling, U-plane, and the AS (RRC and MAC signaling)
Network domain security refers to general IP-relevant security measures that apply various IETF syndicated measures. These measures are detailed in further details in 33.210 and 33.10 (respectively describing security aspects for IP network layer and the network domain authentication framework).
User domain security involves user-to-USIM authentication, and authorization of the USIM-Terminal link. These are basic security measures to authenticate any user or terminal. Meanwhile, application security is enabled by the security features provided for the USIM Application Toolkit which enables authentication applications residing the USIM.
Note that a similar architecture is assumed when dealing with non-3GPP accesses, where the access and serving networks would be a non-3GPP access network.