EPS Key Hierarchy
Two requirements bound the EPS key hierarchy and derivation. The first is that the EPC and E-UTRAN shall allow for use of encryption and integrity protection algorithms for AS and NAS protection having keys of length 128 and for future use the network interfaces shall be prepared to support 256 bit keys. The second is that keys for the user plane, NAS and AS protection shall be dependent on the algorithm with which they are used.
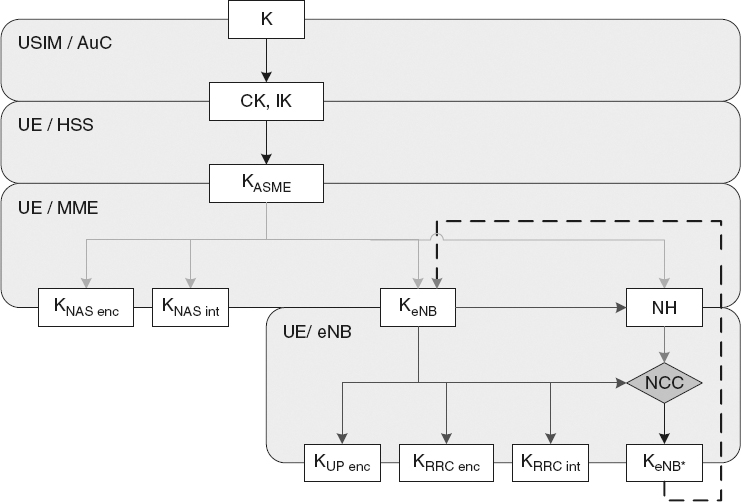
Figure 14.3 EPS Key Hierarchy and Derivation. Reproduced by permission of © 2010 3GPP. Further use is strictly prohibited.
The hierarchy, shown in Figure 14.3, includes the following keys: KeNB, KNASint, KNASenc, KUPenc, KRRCint and KRRCenc. A brief description of the different keys and how they are derived is provided below.
- KeNB is a key derived by UE and MME from KASME. KeNB may also be derived by the target eNB from NH at handover. KeNB shall be used for the derivation of KRRCint, KRRCenc and KUPenc, and for the derivation of KeNB* upon handover.
Keys for NAS traffic:
- KNASint is a key, which shall only be used for the protection of NAS traffic with a particular integrity algorithm. This key is derived by UE and MME from KASME, as well as an identifier for the integrity algorithm.
- KNASenc is a key, which shall only be used for the protection of NAS traffic with a particular encryption algorithm. This key is derived by UE and MME from KASME, as well as an identifier for the encryption algorithm.
- KUPenc is a key, which shall only be used for the protection of UP traffic with a particular encryption algorithm. This key is derived by UE and eNB from KeNB, as well as an identifier for the encryption algorithm.
Keys for RRC traffic:
- KRRCint is a key, which shall only be used for the protection of RRC traffic with a particular integrity algorithm. KRRCint is derived by UE and eNB from KeNB, as well as an identifier for the integrity algorithm.
- KRRCenc is a key, which shall only be used for the protection of RRC traffic with a particular encryption algorithm. KRRCenc is derived by UE and eNB from KeNB as well as an identifier for the encryption algorithm.
Intermediate Keys and Values:
- Next Hop (NH) is used by UE and eNB in the derivation of KeNB* for the provision of “forward security”. NH is derived by UE and MME from KASME and KeNB when the security context is established, or from KASME and previous NH, otherwise.
- Next Hop Chaining Count (NCC) is a counter related to NH (i.e., the amount of Key chaining that has been performed) which allow the UE to be synchronized with the eNB and to determine whether the next KeNB* needs to be based on the current KeNB or a fresh NH.
Forward security: In the context of KeNB key derivation, forward security refers to the property that, for an eNB with knowledge of a KeNB, shared with a UE, it shall be computationally infeasible to predict any future KeNB, that will be used between the same UE and another eNB. More specifically, n hop forward security refers to the property that an eNB is unable to compute keys that will be used between a UE and another eNB to which the UE is connected after n or more handovers (n = 1 or 2).
