13
Internet of Underwater Things: Challenges, Routing Protocols, and ML Algorithms
Monika Chaudhary, Nitin Goyal* and Aadil Mushtaq
Chitkara University Institute of Engineering and Technology, Chitkara University, Punjab, India
Abstract
The Internet of Underwater Things (IoUT) is the system of intelligent linked underwater things and a diverse kind of Internet of Things (IoT). IoUT is expected to permit different practicable requests, similar to ecological monitor, underwater examination, and calamity prohibition. With these uses, IoUT is considered unique of the likely technology around developed intelligent towns. To help the idea of IoUT, Underwater Wireless Sensor Networks (UWSNs) have appeared as an auspicious network system. UWSNs have various special characteristics, such a longer propagation delay, small bandwidth, and miserable reliability. This chapter presents challenges that can occur in IoUT. Also, the existing routing protocols for effective communication are discussed in great detail here. IoUT empowers a system of autonomous underwater vehicles (AUV) interconnecting with each other, detecting, collecting, and communicating data to sink node. Then, this data can be helpful in wide range of applications like ship wreckage detection, early discovery of tsunamis, marine health observing, as well as gathering real-time oceanic info. This chapter focuses on the complete terminology of IoUT including its basic concept, architectural requirements, challenges, routing protocols, and machine learning algorithms in IoUT.
Keywords: Challenges, machine learning, Underwater Wireless Sensor Network (UWSN), sensor
13.1 Introduction
Internet of Underwater Thing (IoUT) system of communication is the involvement of underwater objects that are interconnected with each other worldwide through a smart network [1]. Each device has its digital entity in this large network that provides uniqueness to each of the devices. These devices consist of a tracking system, sensors, and sequence of internet connectivity which helps these devices to react, sense, and tackle the environment [2]. Recently, smart cities have been growing with high speed. For that, one of the most significant technologies is the Internet of Things (IoT), precisely termed as “the infrastructure of the information society”. The concept of IoT was invented in 1985 and 2012; the IoUT was first discussed. IoUT helps to connect various terrestrial things like smartphones, IoT devices, and computers, with the underwater network [3]. Each object which is deployed underwater can be accessed virtually which helps to get information like physical properties and historical information about the object. Due to the ubiquitous nature of the information, it can be accessed or managed in real-time through many methods of communication like Human to Thing (H2T) and Thing to Thing (T2T). Around 70% of mother globe is shielded by water constituted of smaller seas and rivers [4]. Patterns of wind and various climatic changes are determined by the temperature of the ocean that affects the living life on the earth. The availability of freshwater/drinking water is at most around 1% on the earth. Contamination of this results in damaging the ecosystem. The IoUT helps to control or maintain various areas of water that are not [5] yet explored. Underwater Wireless Sensor Networks (UWSNs) work under very harsh conditions as compared to ground-based networks such as wireless sensor network [6–8].
IoT are a buzzword nowadays because of their popularity in daily life. The same is with IoUTs. It is the implementation of IoT under the water as shown in Figure 13.1. It is one of the most advanced and emerging techniques in underwater networks and communication. The IoUTs are termed as the internetwork of smart interrelated under the water things. The implementation of IoUTs is in many application areas of UWSN as described in Figure 13.2. These can be exploration of aquatic life, natural catastrophe preclusion, and also in the military applications as explained by Kao, C. et al. (2017) [9].
13.2 Internet of Underwater Things
IoT was invented by Kevin Ashton. IoT can be established by “adding RF-Identification and other sensors to everyday objects”. Over time, this field has attained higher extent and involves different entities, i.e., household utilizations, watches, and supplementary tools implanted using microelectronics, sensing devices, and connectors enabling data exchange. IoT is escalating at an overwhelming rate of 21%. The combination of IoT, underwater networks, and transmission techniques can take UWSN applications to higher extent. This combination has enabled the recent UWSN concept termed as IoUT. This word “IoUT” firstly discussed by Domigo in their research named as “An Overview of the Internet of Underwater Things” in 2012 [10].

Figure 13.1 Concept of IoUTs.

Figure 13.2 Concept and devices used in IoUT.
13.2.1 Challenges in IoUT
There are many issues and challenges that can slow down the current stride of research in IoUT due to distinctiveness in UWSNs [11]. Here, some of the challenges are discussed below:
- 1. Dissemination Speediness: The speed of propagation in UWSN is 200,000 slower than that of TWSN. In TWSN, propagation speed is 300,000,000 m/s, but, as compared to UWSN which is around 1500m/s, that is quite slow as compared to Terrestrial WSN. This raises a challenge which is called end-to-end delay.
- 2. Transmission Rate: Acoustic communication always uses narrow bandwidth which is not done in TWSN that uses radio communication, Due to the low level of narrow bandwidth, rate of transmission in UWSN is quite low around 10 kb/s. Hence, consumption of the bandwidth is main challenges for the IoUT.
- 3. Battery Problem: Underwater nodes that are deployed in designated region faces problem for recharge of their battery as these are deployed in underwater areas. As energy efficiency is one of the important concern for IoUT, so it is very critical challenge.
- 4. Mobility: As underwater networks are mobile in nature. Sensor nodes are mobile due to water currents and hence grieve with frequent network topology changes. It is also very perplexing job to pact with these dynamic and abrupt changes in IoUT.
- 5. Consistency: The consistency or reliability in UWSNs is usually unbalanced and less. It is related with the successful packet delivery ratio, means the number of packet received to total packet sent from source to destination. The packet delivery ratio is strictly disturbed by the transmission loss, i.e., the accumulated reduction in intensity of waveform energy. Transmission loss is severe problems in UWSNs as radio signals get absorbed in water. Furthermore, there are huge ecological noises in UWSNs, including marine creatures, turmoil, and shipment. Hence, the consistency problem is one of the utmost challenging concerns in IoUT.
13.3 Routing Protocols of IoUT
The routing protocol paves the way that how data packets will be sent from source to destination in the UWSN. In IoUT, these protocols plays a fundamental responsibility in achieving the suitable Quality of Service (QoS) [12]. Hence, it is essential to study different kinds of protocols that are used for routing in IoUT. The routing protocols can be classified into five various forms: (1) table-driven, (2) on-demand, (3) geographic, (4) opportunistic, and (5) multicast tree [13], as shown in Figure 13.3.
- 1. Table-Driven: The purpose of this approach is decreasing the waiting time caused by route searches before transmitting data packets from source to sink [14]. In this routing, information of targets and their routing data is kept by regularly updating routing tables using the transmission system to have up to date information and to decrease latency. Herewith, up-to-date routing details could be retained from each node to every other node in the network.
- 2. On-Demand: As the name suggests, the routes are discovers on demand. If there is requirement of data transmission to the destination node, then route detection process is started by a sensor node only [15]. For this, the route request packets are flooded throughout the network. Then, if any of the nodes accepts this route request packet, then that particular node will report the conforming route reply packet back to the source node.
- 3. Geographic: This protocol seems to be much appropriate elucidation for underwater IoT as compared to table-driven and on-demand routing. As in geographic routing, broadcast overhead is significantly reduced by tapping the geographical locality details of nodes [16]. A particular node select its next-hop node based on the position of its neigh-boring nodes and destination node itself. After confirming all these information, sender node forwards the packet in correct or functional direction.

Figure 13.3 Different routing protocols in IoUT.
- 4. Opportunistic: In this routing, sender node sends the data packet and all intermediate neighboring nodes when accepts the packet checks whether to transmit the packet according to the prospect or prearranged state [17]. The position may be the range between the sender and receiver. When the conditions have been satisfied, i.e., when target is nearer to the sink node from source node, then the target will decide to circulate the packet further in the network [20]. Thus, the receiver will identify whether or not the sender has to transmit the packet by itself to dispatch the packet, it can transmit the packet directly.
- 5. Multicast Tree: This protocol is an unconventional procedure for transmitting in UWSNs. Distinct from previous routing protocols. In this routing protocol, a tree topology is created for finding the optimized routes, different from other routing protocols [11]. The ultimate objective of this routing technique is to have reduced delay and less energy consumption. Instead of flooding packets, this protocols construct the corresponding specific shortest tree or minimum spanning tree. In this, multicasting of packets is done on the specific tree topology for finding routes in the network.
DSDV: The DSDV protocol requires each mobile station to advertise, to each of its current neighbors, its routing table (for instance, by broadcasting its entries). The entries in this list may change fairly dynamically over time, so the advertisement must be made often enough to ensure that every mobile computer can almost always locate every other mobile computer of the collection.
OLSR: This protocol is based on distributed concept without any central authority. OLSR protocol accomplishes hop-by-hop routing, where every node make use of its most recent or updated information to route a packet [18].
The concept of multipoint relays (MPRs), as shown in Figure 13.4, is to minimalize flooding or broadcasting of packets in the whole network by decreasing replica retransmissions. Every node chooses a set of nodes in its vicinity, which retransmits its packets in the network. These set of carefully chosen neighbor nodes is named as MPRs.

Figure 13.4 Multipoint relays in OLSR.
AODV: The Ad hoc On-Demand Distance Vector (AODV) is specifically designed for utilization of sensors that are moving in nature. These node works in a temporary system. It provides fast adjustment to lively connections, miserable handling, and identifies unicast routes to targets in the whole system. It is an enhancement over table driven routing protocol such as distance vector protocol. This message establishes an experimental protocol for the internet community.
DSR: The protocol adjusts rapidly to routing change when the host move is often, yet demands small or no overhead within periods in which hosts shift lower frequently. Dynamic source routing is a method where source transmit packet and decides full order of sensor over which to ahead the packet. It means next hop is decided by the source node. This protocols reduces bandwidth consumption, control overhead.
VBF: In Vector-Based Forwarding (VBF), every packet contains the locations of source, destination, and the node that forwards packet. These are represented by SP, DP, and FP, respectively. The furthering pathway is quantified by the Routing Vector (RV) from the source to destination. The routing pipe is well-defined by the vector from the source or SP to destination or DP and also RADIUS, which is radius of the pipe. VBF protocol reports the mobility of node in a scalable and energetic mode.
HH-VBF: Hop-by-Hop VBF is established using the idea of vector forwarding protocol. However, HH-VBF describes the separate virtual pipe that is near about hop-by-hop from every intermediate node to the sink node, as an alternative of using only single virtual pipe that occur around from sender to target. Each node can flexibly make packet forwarding decisions based on its current location.
GFGD: Greedy Geographic Forwarding based on Geospatial Division (GGFGD) and Geographic Forwarding based on Geospatial Division (GFGD) are described geo-spatially. The sender node S attempts to discover a next-hop node having distance smaller than its own SC. In this algorithm, every node directly communicates with every other node located in its surface neighboring SC, as shown in Figure 13.5.
EMGGR: This routing protocol has three core components. First component is the gateway election procedure which is accountable for selecting gateways mainly centered on nodes locations and their residual energy. Second is how gateway information is updated that allows sensor nodes to memorize gateways. The third component is the packet forwarding technique. Energy-efficient Multipath Grid-based Geographic Routing (EMGGR) observed whole network as logical 3D grids, as shown in Figure 13.6. In this, routing is performed by grid-by-grid manner with the help of gateways. It uses distinct routes to communicate data packets to the target node.
AHH-VBF: This protocol handle accelerating data packets and broadcast power in cross-layer manner. This is done to reduce energy consumption and increase consistency. One more advantage is also that it reduced delay using optimization of controlling period of data sent in the network.
LARP: Location-aided routing protocol belongs to geographical routing protocols, which can provide good reliability and validity of message transmission. Note that the exact location information of nodes is helpful for the transmission of the message in network. This is an efficient routing protocol that beats the existing routing protocols when packet delivery ratio and normalized routing control overhead is of great concern.

Figure 13.5 The relationship between S and L in GFGD.

Figure 13.6 A 3D logical grid view of EMGGR protocol.
WDFAD-DBR: This is a Weighting Depth and Forwarding Area Division Depth-based Routing protocol. It makes routing decisions based on the difference of weighting depth of two hop nodes. It improves the transmission reliability and also reduces void-holes chances. The prediction procedure about neighbor nodes based on the past information of neighbor nodes is one the major advantage of this routing protocol with the help of collision avoidance as shown in Figure 13.7.
DRP: This is a dynamic routing protocol in which route selection procedure considers broadcast space between source and destination. It uses the remaining energy for every node. An existing localization scheme works correctly in oceanic currents. Some variables naming is used for DRP. There are six sensor nodes (na, nb, nc, nd, ne, and nf) and one sink node (nsk). The EPR values are on the corresponding links. Getting HELLO packet, nodes va and vb calculate EPRva (nsk) and EPRvb (nsk), respectively. After applying the DRP algorithm, the associated Cmax(na)(Cmax(nb)), HC(na) (HC(nb)), and f(na)(f(nb)) are searched, depicted in Figures 13.8b and c.
The different existing algorithms are compared based on various quality parameters such as reliability, mobility of nodes, bandwidth consumption, energy consumption, and delay as described in Table 13.1.
13.4 Machine Learning in IoUT
Machine learning (ML) is novel paradigm that has remarkable prospective to endow various ocean applications smartly and efficiently. Conversely, due to punitive and active environment of marine scenario, the severe necessities of underwater solicitations and cost for management and maintenance of IoUT have restricted advancements in IoUTs [19].

Figure 13.7 The probability of ACK’s collision.

Figure 13.8 Operations in DRP.
Table 13.1 Comparison of various routing protocols for different quality parameters.
| Protocol | Reliability | Mobility | Bandwidth | Energy | Delay |
| LRP | High | Medium | Medium | High | Low |
| DRP | High | Medium | High | High | Low |
| LBRP | High | Low | High | High | Low |
| ERP2R | High | Low | High | High | Low |
| HydroCast | High | High | Low | Medium | High |
| OVAR | High | High | Medium | Medium | High |
| WDFAD-DBR | High | Medium | Low | Medium | High |
| GEDAR | Medium | High | Low | Low | High |
| VAPR | Low | High | Low | Low | High |
| DBR | High | Medium | Low | Low | High |
| LARP | Low | High | Medium | Medium | Medium |
| AHH-VBF | High | Medium | Medium | Medium | High |
| EMGGR | Low | Medium | High | High | Medium |
| MGGR | Low | Medium | High | Medium | Medium |
| GFGD | Low | Medium | High | High | Low |
| HH-VBF | High | Medium | Medium | Medium | High |
| VBF | High | Medium | Medium | Medium | High |
| DSR | Low | Medium | Medium | Medium | High |
| AODV | Low | High | Medium | Medium | High |
| OLSR | High | High | Low | Low | Low |
| DSDV | High | High | Low | Low | Low |
ML has been implemented comprehensively for extensive variety of tasks since the last decade. These task includes various applications areas like junk detection, fake recognition, and advertisements. ML procedures give incredible tractability advantages, when it is applied to numerous applications of UWSNs. Mostly, ML techniques fall in three classifications of supervised, unsupervised, and reinforcement learning (RL). The ML algorithms, when delivered a characterized set of values for training, lie in first category of supervised learning. Opposite to supervised, no set of values are available for training and learning in unsupervised learning.
ML in UWSN applications has been used for two issues: one of them is network-associated issue and the other is application-associated issue. First, in network-associated issue, learning techniques have been extensively implemented for the optimum distribution of sensors, safety, and power saving grouping. It is also used in QoS, allocation of resource in network, scheduling, and data aggregation and fusion. However, in application-associated issue, ML algorithms are mainly implemented in data processing, event cataloguing, and discovery of target class and its tracking.
13.4.1 Types of Machine Learning Algorithms
Here, different ML algorithms are used in various applications of UWSNs. One of the methods is Fuzzy Logic Systems (FLS), having three main methods that are fuzzification, interpretation engine, and defuzzification. Zohre and Arabi [22] suggested a fuzzy-based algorithm that implements fuzzy schemes for developing directed diffusion routing techniques for estimating the quality of routes. It also estimates the quantifiable value related with the quality of every route and supports the selection of numerous feasible routes in the routing protocol: FLS, sound appropriate in scheduling, clustering, energy-aware routing, and design and deployment.
The second method is Neural Network (NN), which is numerical prototypes using specific method on different values. Its initial encouragement originates by the concept of natural systems of neurons which comprise of neurons that are interrelated. The weights are given to each connections between the nodes in the network in which data is going from input. Wenhui Zhao et al. [23] suggest a self-managing NN optimizing route. Other methodology is recommended by dint of Veena K. N. et al. [24] for searching well-organized path from source to destination.
The third method is RL based, in which learning is what to do and how to do. It map the circumstances to movements for maximizing every ecological numerical signal. Opposite to other learning method, in this technique, learner is not communicated about the actions to be taken, as an alternative, learners attempt self-practicing and discerning act that produces return through trying and trying again. Nesrine Ouferhat and Abdelhamid Mellouk [25] recommended an Energy and Delay Efficient Routing (EDEAR) as flexible transmitting with an aim for searching finest optimal route based on power consumption and delay.
Fourth is Swarm Intelligence (SI) based on cooperative conduct using decentralization and self-managed networks. The basic idea of implementation comes from Mother Nature, particularly biological structures that communicate with each other in environment. The ordinary examples involves ant colony optimizations, animal shepherding, and fish training. Yi-ping Chen et al. [26] suggested a particle swarm optimization technique for investigation in inter-grouping for increasing the lifespan of networks. This scheme mainly works for efficiency of energy and prolonging network lifetime.
IoT performance played a very significant role in the advancements and developments of IoUT in many of the underwater applications [27, 28]. Security is also one of the main concerns when we work in UWSN with wide variety of other application area [29].
13.5 Performance Evaluation
Different algorithms have been proposed using ML-based models [21]. Park et al. [18] presented a model for the prediction of the ocean current in specific timelines using practical data learned with various ML techniques. Figure 13.9 shows the comparison for sending packets in the network which is better in DTC technique as compared to LGT using Laguerre-Gaussian presented by Trichili et al. [30].

Figure 13.9 Delivery ratio vs. number of nodes.
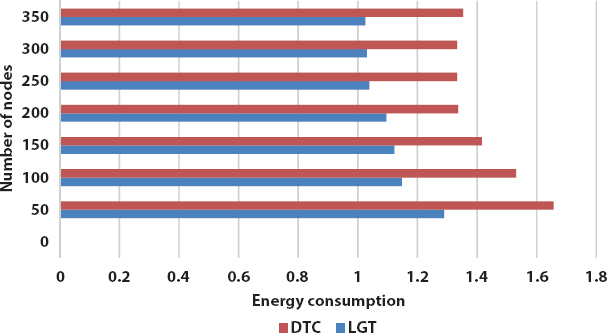
Figure 13.10 Energy consumption vs. number of nodes.
The energy efficiency is one of the main concerns in underwater environments. Figure 13.10 shows the comparison of energy consumption between DTC and LGT. The energy consumption in LGT is comparatively less as compared to DTC.
13.6 Conclusion
The IoT is a worldwide occurrence that has changed everyday life with the advancements in internet technology. With the advancements in IoT objects and appliances and satellite communication that can link devices in sea to shipments, one habitation left where IoT does not exist. That location is under the water. In this paper, we examine the modern kind of IoT, which is named as IoUT, i.e., the Internet of Underwater Things. This chapter offers beneficial knowledge about the IoUTs, its challenges, routing protocols, and implementation of ML algorithms in IoUT. Also, some of the existing protocols is evaluated to show their performance comparison.
References
1. Wang, H.H., Rock, S.M., Lee, M.J., OTTER: The design and development of an intelligent underwater robot. Auton. Robots, 3, 2–3, 297–320, 1996.
2. Sheng, Z., Yang, S., Yu, Y., Vasilakos, A.V., McCann, J.A., Leung, K.K., A survey on the ietf protocol suite for the internet of things: Standards, challenges, and opportunities. IEEE Wireless Commun., 20, 6, 91–98, 2013.
3. Vermesan, O., Friess, P., Guillemin, P., Gusmeroli, S., Sundmaeker, H., Bassi,
A., Doody, P., Internet of things strategic research roadmap, in: Internet of things-global technological and societal trends, vol. 1, pp. 9–52, 2011.
4. Gill, S.D., Mother earth: an American story, University of Chicago Press, USA, 1991.
5. Vitousek, P.M., Mooney, H.A., Lubchenco, J., Melillo, J.M., Human domination of Earth’s ecosystems. Science, 277, 5325, 494–499, 1997.
6. Nain, M. and Goyal, N., Localization Techniques in Underwater Wireless Sensor Network, in: 2021 International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), 2021, March, IEEE, pp. 747–751.
7. Choudhary, M. and Goyal, N., Node Deployment Strategies in Underwater Wireless Sensor Network, in: 2021 International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), 2021, March, IEEE, pp. 773–779.
8. Goyal, N., Architectural Analysis of Wireless Sensor Network and Underwater Wireless Sensor Network with Issues and Challenges. J. Comput. Theor. Nanosci., 17, 6, 2706–2712, 2020.
9. Kao, C.C., Lin, Y.S., Wu, G.D., Huang, C.J., A comprehensive study on the internet of underwater things: applications, challenges, and channel models. Sensors, 17, 7, 1477, 2017.
10. Domingo, M.C., An overview of the internet of underwater things. J. Netw. Comput. Appl., 35, 6, 1879–1890, 2012.
11. Liou, E.C., Kao, C.C., Chang, C.H., Lin, Y.S., Huang, C.J., Internet of under-water things: Challenges and routing protocols, in: 2018 IEEE International Conference on Applied System Invention (ICASI), 2018, April, IEEE, pp. 1171–1174.
12. Nayyar, A., Ba, C.H., Duc, N.P.C., Binh, H.D., Smart-IoUT 1.0: A smart aquatic monitoring network based on Internet of Underwater Things (IoUT), in: International Conference on Industrial Networks and Intelligent Systems, 2018, August, Springer, Cham, pp. 191–207.
13. Khalil, R., Babar, M., Jan, T., Saeed, N., Towards the Internet of underwater things: Recent developments and future challenges. IEEE Consum. Electron. Mag., 21, 16, 5398, 2020, https://doi.org/10.3390/s21165398.
14. Pantazis, N.A., Nikolidakis, S.A., Vergados, D.D., Energy-efficient routing protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutorials, 15, 2, 551–591, 2012.
15. Wang, W., Bhargava, B., Lu, Y., Wu, X., Defending against wormhole attacks in mobile ad hoc networks. Wireless Commun. Mobile Comput., 6, 4, 483–503, 2006.
16. Perkins, C.E., Royer, E.M., Das, S.R., Marina, M.K., Performance comparison of two on-demand routing protocols for ad hoc networks. IEEE Pers. Commun., 8, 1, 16–28, 2001.
17. Hu, Y.C., Perrig, A., Johnson, D.B., Ariadne: A secure on-demand routing protocol for ad hoc networks. Wirel. Netw., 11, 1–2, 21–38, 2005.
18. Baumann, R., Vehicular ad hoc networks (VANET):(engineering and simulation of mobile ad hoc routing protocols for VANET on highways and in cities, Master’s thesis, ETH, Swiss Federal Institute of Technology Zurich, Switzerland, Department of Computer Science, Computer Systems Institute, 2004.
19. Bangash, J.I., Abdullah, A.H., Anisi, M.H., Khan, A.W., A survey of routing protocols in wireless body sensor networks. Sensors, 14, 1, 1322–1357, 2014.
20. Abdollahi, M., Eshghi, F., Kelarestaghi, M., Bag-Mohammadi, M., Opportunistic routing metrics: A timely one-stop tutorial survey. J. Netw. Comput. Appl., 102802, 2020, arXiv:2012.00850.
21. Park, S., Byun, J., Shin, K.S., Jo, O., Ocean current prediction based on machine learning for deciding handover priority in underwater wireless sensor networks, in: 2020 International Conference on Artificial Intelligence in Information and Communication (ICAIIC), 2020, February, IEEE, pp. 505–509.
22. Arabi, Z., HERF: A hybrid energy efficient routing using a fuzzy method in wireless sensor networks, in: 2010 International Conference on Intelligent and Advanced Systems, 2010, June, IEEE, pp. 1–6.
23. Zhao, W., Liu, D., Jiang, Y., Distributed neural network routing algorithm based on global information of wireless sensor network, in: 2009 WRI International Conference on Communications and Mobile Computing, 2009, January, vol. 1, IEEE, pp. 552–555.
24. Veena, K.N. and Kumar, B.V., Convergecast in wireless sensor networks: a neural network approach, in: 2010 IEEE 4th International Conference on Internet Multimedia Services Architecture and Application, 2010, December, IEEE, pp. 1–6.
25. Ouferhat, N. and Mellouk, A., Energy and delay efficient state dependent routing algorithm in wireless sensor networks, in: 2009 IEEE 34th Conference on Local Computer Networks, 2009, October, IEEE, pp. 1069–1076.
26. Chen, Y.-p. and Chen, Y.-z., A novel energy efficient routing algorithm for wireless sensor networks. The 9th International Conference on Machine Learning and Cybernetics, Qingdao, July,2010, pp. 1031–1035, 11–14.
27. Datta, P. and Sharma, B., A survey on IoT architectures, protocols, security and smart city-based applications, in: 8th International Conference on Computing, Communication and Networking Technologies (ICCCNT), 2017, July, IEEE, pp. 1–5.
28. Badotra, S. and Panda, S.N., A review on software-defined networking enabled iot cloud computing. IIUM Eng. J., 20, 2, 105–126, 2019.
29. Goyal, N., Dave, M., Verma, A.K., Trust model for cluster head validation in underwater wireless sensor networks. Underw. Technol., 34, 3, 107–114, 2017.
30. Trichili, A., Issaid, C.B., Ooi, B.S., Alouini, M.S., A CNN-Based Structured Light Communication Scheme for Internet of Underwater Things Applications. IEEE Internet Things J., 7, 10, 10038–10047, 2020.
- *Corresponding author: [email protected]
