11
Behavioral Analysis of Violent Crime
“Outside of the killings, Washington has one of the lowest crime ratesin the country.”
Marion Shepilov Barry, Jr.
Although the above quote might seem humorous or absurd, it makes a good point. In many ways, the key to reducing the crime rate is preventing crime. To effectively prevent crime, it is important to characterize and understand it so that it can be anticipated and predicted. Therefore, the use of data mining and predictive analytics to characterize and predict crime represents the first steps in the preparation of a comprehensive, information-based approach to enhanced investigative efficacy and meaningful, targeted crime prevention.
For better or worse, people generally develop their impressions of crime in a community based on the number of murders or on the overall violent crime rate (Figure 11-1). The ability to reduce community violence can reap tremendous benefits in terms of quality of life; rampant violent crime can impact almost every aspect of life in a community. Aside from the immediate, direct impact on the victims and their families, the overall quality of life, including economic opportunities, decreases significantly in a crime-ridden community. As the cycle of violence spins out of control, those residents that can, leave; existing businesses relocate; and new opportunities for development are lost. Even the young people are affected.1 Those growing up in urban combat zones (Figure 11-2) acquire the short-term approach to life so frequently observed in people with diminished perceptions of their value to the community, reduced access to opportunity, and shortened overall life expectancy.

Figure 11-1 Homicide rates can alter perceptions of the relative safety and associated desirability of a community.
Several years ago, I began a conversation with some colleagues who possessed exceptional skills in the behavioral analysis of violent crime. The basic thesis of this discussion was that the behavioral analysis of violent crime or criminal “profiling” works because violent crime is relatively homogeneous and predictable.
Violence is a behavior, albeit an extreme behavior, when reduced to its fundamental form. Social and behavioral scientists have been studying and categorizing behavior for many years and have found that in many ways, nature is economical. Biologists frequently find the same common elements repeated within an organism and across species. In other words, one of nature’s rules seems to be, if it works, keep using it. Complexity often is achieved by unique combinations of simple common elements. This concept is explored further in the chapter on modeling.
Animal Models
“Innocence about Science is the worst crime today.”
Sir Charles Percy Snow
It may not be obvious, but animal research can help us understand violent crime and enhance data mining strategies. An understanding of the research on nonhuman animal behavior frequently holds some insight for students of human behavior that can be applied to criminal or violent behavior in some cases. While it is unlikely that there are any studies in scientific literature entitled “When Mice Go Bad,” some excellent comparison data can be identified with a creative approach to the literature. For example, the theory of species-specific defense reactions (SSDR), which was developed using animals models, provides a good explanation for situations in which people fail to react in life-threatening situations and perish as a result. Briefly, this theory suggests that there are certain behaviors that have been selected for during the evolutionary process that are preprogrammed, or hardwired into the brain, because they previously have been integral to survival. The fight or flight response falls into this category, as well as another behavior called “freezing,” in which an individual “freezes,” or otherwise is incapable of movement. Why is an understanding of animal models of behavior important to the analysis of human public safety data? First, it provides a general outline of existing behavioral categorization that can be adapted and used to describe and understand human behavior. For example, we know based on the literature that animal responses to threatening situations can be classified into three mutually exclusive and distinct categories: fight, flight, or freeze. Within a context of conservation of the behavioral mechanism, this same behavioral categorization can be applied to human responses to threatening situations.
Second, by identifying and linking common behavioral elements found in animal research literature to questions regarding human behavior, we often can enrich our understanding of the human behavior in question. There are some “experiments” that would be illegal or unethical to conduct on human subjects. Characterizing and reducing human behavior to common elements and themes, however, frequently can facilitate the identification of a similar animal model that might further illuminate other aspects or outcomes related to the behavior not considered previously. For example, models describing predator selection and acquisition of prey can be used to describe victim selection in some patterns of violent crime.
Returning to the example of SSDR, we know from animal studies that it can be extremely difficult to elicit a behavior other than the natural response in a threatening situation. By further reviewing the literature, specific examples can be identified and applied to human situations. For example, animal research information can be used to enhance escape planning in protective operations. If particular situations or scenarios are likely to elicit a freeze or fight response when escape would be the best choice, then operational planning can be modified to incorporate our understanding of the natural or likely response to this particular situation or combination of operational elements. Alternatively, an adaptive response can be taught in an effort to overcome the natural response in the scenario.
Why does this have value to data mining and predictive analytics? In many ways, the behavioral analysis of violent crime works because behavior is relatively homogeneous and predictable when reduced to its simplest form. Therefore, examination of the nonhuman behavioral literature provides two benefits. First, it forces the analyst to reduce behavior to common elements. That is, it forces the development of operational definitions for the behavior of interest. For example, overkill can be extremely upsetting for responders who encounter it but, operationally defined, it just means that the amount of force used was greater than that required to kill the victim. So overkill is either present or it is not, which reduces it to a yes/no question. It does not matter whether the victim was stabbed 50 times or 500 times—overkill is overkill. By reducing this question to a yes/no choice, a binary selection, the data and related questions have been categorized in a way that is appropriate for data mining and predictive analytics.
Behavioral literature often can provide a level of insight and understanding that can be used to structure and guide data mining analysis of criminal behavior while illuminating likely outcomes or responses to the behavior in question. For example, optimal foraging models and predatory behavior in animals can be used to describe the nature and function of some illegal drug markets. Therefore, by looking to these examples, drug enforcement also can be understood within a context of changing the behavioral cost of the criminal behavior, similar to the approach used in the very effective Project Exile.
This conservation mechanism also can be applied to behavior. In many ways, the behavioral analysis of violent crime involves describing, aggregating, and categorizing behavior, similar to the behavioral categories or taxonomies developed and employed in the laboratory setting. Many of the same behavioral concepts developed in pigeons or rats can be applied to humans. While this comment might prompt a few uncharitable comments from those who work with criminal behavior on a daily basis, the concept of behavioral reduction can have profound implications for the use of data mining and predictive analytics in the analysis and prediction of criminal behavior, particularly violent behavior, as well as victim selection, victim response, and victim-perpetrator interactions.
People tend to get into ruts with regard to their behavior, which is the basic foundation for the routine activities theory of crime.2 A systematic review of drug-related homicide data in Richmond, Virginia, revealed that the victims of drug-related homicides generally did not get killed on the opposite side of the river from where they lived. We have conducted similar analyses since that time and have found a relatively consistent pattern of results. People still tend to get killed over drugs on the same side of the river where they reside.
In some ways, this should not have been a particularly surprising finding. The Richmond metropolitan area is divided by the James River. While people frequently will cross the river for work and work-related functions, they generally tend to stay on the same side of the river as their residence for most of their other routine activities. Additional analysis of the illegal drug markets in the city revealed a similar pattern. At the time of the analysis, there were drug markets that had evolved to serve the population from each particular side of the river. They tended be in locations that were convenient for the particular market or clientele being served, but a quick review of vehicle identification stickers revealed very little crossover, particularly among users. Perhaps the one noteworthy exception to this finding was that dealers and other individuals involved with the illegal networks were killed on the other side of town, possibly because they did not belong in that area.
What does this mean? First, it has some implications for drug enforcement strategies. If people were not crossing the river and getting killed buying drugs, a logical assumption would be that they did not cross the river to buy drugs. These homicide data, in many ways, provided a snapshot into illegal drug buying habits in the city. Triangulating between the residence of the victims and the locations of the murders also provided some insight regarding normal traffic patterns and routes associated with the various drug markets. This information has considerable value for drug enforcement strategies.
What about folks working outside of the Richmond metropolitan area? What does this mean for them? Reducing this example to its common elements reveals three features that can be applied to other settings. First, it highlights the use of the discovery and modeling process embodied within data mining and predictive analytics. Although using very simple techniques, this example demonstrates that we can learn new things about violent crime through the process of characterization and categorization. By drilling down into the information, new trends and patterns can be revealed or discovered. Moreover, this information can be used to anticipate and predict future similar events, which opens the door to meaningful enforcement and prevention strategies.
Second, humans are creatures of habit. If I can buy milk, watch a movie, and get my car washed near my home, why should I cross the river to buy drugs? Drug markets can be extremely adaptable and fluid, particularly when responding to the preferences of the users. In fact, it is really amazing to see the differences between some of the inner-city open-air drug markets and those serving folks from the outlying areas. During various tours of the illegal markets, the differences in structure, setup, and function were noteworthy. At that time, the dealers associated with the inner-city markets tended to be savvier, able to quickly distinguish the unmarked vehicles—frequently after young children on bicycles called out, “Five-oh!,” heralding our impending arrival.3 The other markets, on the other hand, resembled a fast-food restaurant in terms of convenience and product availability, as well as setup and function.
The third benefit of this example is that it highlights the use of data mining and predictive analytics in the analysis of violent crime. If nothing else, this example should encourage other agencies to step outside the box in the analysis of violent crimes. Simply “counting crime” is not enough. To prevent crime, we need to be able to anticipate and predict it. This extremely low-tech yet powerful example highlights the value of creative analysis. It also further supports the use of spatial analysis or mapping. Mapping should not be confined to pin maps showing what happened. Maps should be used to convey additional details or information regarding crime trends and patterns of interest.
11.1 Case-Based Reasoning
In many ways, the process of criminal investigative analysis, or behavioral profiling of violent crime, truly is an amazing example of data mining and predictive analytics. At first, the process seems like magic. When confronted with a jumbled mass of clues, the investigator is able to identify a likely suspect, like a magician pulling a rabbit out of the hat. On further investigation, though, it becomes clear that are two important elements functioning in this investigative process. The first is good case management. By reviewing the case thoroughly, items that have been overlooked or lost can be identified and addressed. Similar to identifying where missing puzzle pieces belong, this process in and of itself can result in tremendous clarification in the direction of an investigation and significant progress toward closing the case. It allows the investigator to reveal the big picture and identify any readily apparent trends and patterns. In many ways, this is similar to the process of data cleaning and management. By thoroughly reviewing and organizing the case, missing details or data are identified and, if possible, addressed.
Similarly, using data mining and other automated methodologies can prompt consideration of evidence in a different light. By distilling the collected narrative information through a categorical filter, the information can be further characterized and categorized into smaller, readily identifiable groups that have value from an investigative perspective. How does this work in the field? Overkill, as discussed above, and many other factors considered during investigation can be broken down into “yes/no” or dichotomous decisions. Using this type of approach, decision trees can be developed that guide the investigative process, which ultimately can be used in automated motive determination algorithms and even strategic characterization models of likely suspect attributes. These and other data management techniques can add more structure and meaning to investigative information.
The second key piece in the behavioral analysis process is pattern recognition. While this might sound easy, any good investigator knows that it can be much more difficult than it sounds. Investigators who are particularly good at this task are those able to move beyond some of the obvious details and identify underlying themes and patterns. In addition, they will begin trying to match these elements in the current case to their internal database of previously solved cases in an effort to identify a common theme or pattern that might give them some insight. This process of comparing current evidence against historical memory to see what fits can be described as case-based reasoning. Case-based reasoning is a model of learning in which people comprehend new experiences within the context of previous ones,4 a process that can be modeled using expert systems or artificial intelligence.
In some ways, a good investigator can be thought of as a closet analyst. The process and approach associated with criminal investigations is one of the most analytical aspects of law enforcement. Attributes that are associated with a good patrol person or an excellent member of the SWAT team are very different from those factors that are associated with a good investigator. The comparison between the Hawaii Five-O and Columbo detective shows provides a nice parallel. McGarrett and Danno are out there in the thick of things, catching bad guys, while Detective Columbo seems to be stumbling around in a clumsy fashion. Yet the viewer can almost see Columbo’s wheels turning and watch him mentally chewing on the evidence as he chews on his cigars, trying to make the pieces fit in an effort to understand the puzzle. In addition, Columbo always was “bothered by” the pieces that did not fit, highlighting gaps in an alibi or oddities in the crime scene. In many ways, Columbo is a walking example of data mining, case-based reasoning, and anomaly detection rolled into one baggy trench coat. Again, not very elegant, but it works.
Cold case investigation can be seen as an extreme manifestation of the analytical side of the investigative process. These very special investigators and analysts are truly unique in their ability to move beyond the superficial nature of the evidence and look for the underlying form or commonalities with other solved cases in the investigator’s repertoire. While this may sound almost like a Zen-like approach to investigation, much of it comes back to excellent case management, anomaly detection, and some superb case-based reasoning.
Replicating this process through the use of computer programs or artificial intelligence algorithms certainly confers some benefits. First, a computerized database has the ability to store and quickly recover a large amount of information, with an associated capacity that extends well beyond the memory storage and retention abilities of a human. Expert systems have the ability to store, retain, and simultaneously consider information from more cases than any single investigator is likely to encounter in his or her career. In addition, the information is not subject to the same memorial decay and errors in interpretation over time that can occur with the human memory.
Second, an expert system theoretically has no bias—bias that can favor a particular scenario and color the course of future evidence collection and investigative process. It is not swayed by the suspicious boyfriend, or by the shifty looks and dubious alibi given by the jilted lover. Similarly, it is not likely to even subtlely discard or overlook evidence that is contrary to a favored hypothesis or outcome. This certainly is not to suggest any lack of professionalism or ethics on the part of sworn investigators. They are some of the most honor-bound, committed professionals in law enforcement. Rather, human investigators bring their internal norms, life experiences, and feelings to every case. While this can make them incredible champions for the victims and their families, it also shaves away some of their objectivity. It is almost impossible to look at the face of a dead child and remain objective; however, even a little compromise in objectivity can be associated with a concomitant decrease in efficacy. Computers, on the other hand, do not care.
Finally, expert systems are not bothered by crime scene details; they can get beyond the “yuck” factor that occasionally can catch even the most seasoned investigator. Certain victims and certain scenes affect investigators in different ways. Those that are affected by everything that they see are limited in their ability to effectively investigate violent crimes. On the other hand, those who do not respond to anything probably have been on the job too long and should consider a change of pace in an effort to remain effective and retain their humanity. In short, even the most staid investigators are likely to be bothered by something that they encounter. This limits their objectivity and can compromise their ability to reduce the crime to common elements that can be characterized and compared to previous cases. Artificial intelligence systems truly embody the philosophy of “just the facts, ma’am” because they have no capacity for anything else (at least at the time of this writing).
Does this mean that we should discard detectives in favor of computer modeling programs and expert systems? Absolutely not! Expert systems, no matter how “smart,” lack one element critical to effective and meaningful data mining: domain expertise. Without an “expert” in the field to evaluate the nature of the evidence and information collected and to evaluate critically the value and validity of any created models, the risk for significant errors in logic and interpretation would seriously limit our ability to use these tools. Moreover, it is absolutely essential that professionals within law enforcement and public safety minimally have significant involvement in the analytical process. The best scenario would be one in which analytical and investigative personnel work together in the data mining and modeling process, perhaps with some outside help and support from statistical experts. It bears repeating that it seems to be relatively easy to teach data mining and predictive analytics to law enforcement personnel. These folks know where the data come from and how the models will be used. They intuitively know what is available for models and when. As such, they are much less likely to make critical errors that result in the creation of a model based on circular logic, which essentially requires information that is dependent upon the output as an input or indicator variable. Many investigators are natural data miners, given the intuitive nature of their work, and seem to embrace the approach when given the opportunity. On the other hand, trying to convey the internal norms, historical knowledge, and accumulated domain expertise from an active investigative career to data mining experts has proven to be extremely difficult.
In sum, data mining and predictive analytics can enhance the investigative process, particularly through many of the automated pattern recognition programs and scoring algorithms. However, the use of expert systems alone has limited value and could significantly compromise the investigative process.
11.2 Homicide
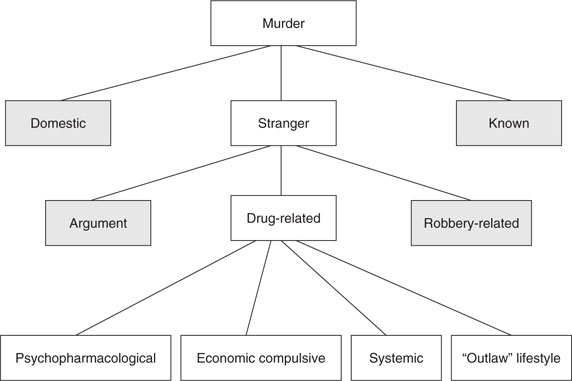
At its most basic, homicide as a crime can be categorized and divided in many ways, most frequently based on victim-perpetrator relationship and motive.5 Figure 11-3 depicts a possible decision tree for murder. The first branch of the tree is divided by three possible victim-perpetrator relationships: familial or domestic, acquaintance or known, and stranger. The second division in the branches includes possible motives associated with stranger murder. Finally, within the various motives, it is possible to characterize the motive even further. In this case, the drug-related homicides have been divided using the Tripartite Model of Drug-Related violence developed by Goldstein.6 Briefly, this model describes three types of drug-related violence: Psychopharmacological, economic compulsive, and systemic violence, which are related to the different role that drugs and/or the drug-related lifestyle may play in violent crime.
While the Goldstein model might be helpful for counting crime or determining the proper focus for needed crime prevention strategies, it frequently adds little value to the investigative process because the nature of the victim-perpetrator relationship and true motive generally are not confirmed until a suspect has been identified and apprehended.
Information collected during the investigative process can be subdivided and used to determine the nature of the crime and possible suspects. As can be seen in Figure 11-4, much of the information collected and considered in the investigative process can be reduced to simple binary choices or sets, reinforcing the fact that data preparation is one of the most important steps in the data mining process.
While startling to many, violent crime can be very homogeneous when viewed in the proper light. One feature of the behavioral analysis of violent crime is the characterization of an incident based on common elements. These include victim as well as scene characteristics, which ultimately are associated with common perpetrator characteristics. The goal is to develop a profile or model of the type of person likely to have committed the crime, based on the known characteristics of the crime. In many ways, the behavioral analysis of violent crimes is similar to algebra. Ultimately, the objective is to solve for “X,” the suspect’s identity, which is done by systematically revealing and examining the other elements of the equation.
Whether consciously or not, the death investigator goes through a series of “yes or no” questions, often as early as when the first call comes into the dispatch center. This information is used to begin characterization and categorization of the crime based on characteristics of the victim(s) and crime scene(s). These include, but are not limited to the following:
The list goes on, but a considerable amount of information can be described as binary in nature, meaning that it can be answered by a simple “yes” or “no.” Other information can be divided into categories or sets (e.g., race)—information ideal for data mining and predictive analytics.
These similarities can be used to link similar crimes perpetrated by the same individual or group of individuals. They also can be used to link similar crimes perpetrated by similar individuals or groups of individuals. In the former case, it is important to link crimes in a series because, like in a puzzle, individual elements present in one incident that were missing or overlooked in other incidents can contribute to a greater understanding of all crimes in the series. In other words, the whole often is greater than a sum of the parts. It also is important to identify all of the crimes associated with a particular individual for prosecutorial purposes. Presenting a linked series can be helpful in jogging the memory of a reluctant suspect.
Associating a crime or series of crimes to known suspects associated with solved cases can be helpful in at least two ways. First, it can provide guidance as to the type of individual likely to have perpetrated a particular crime or series. In contrast to television and movie portrayals of “profilers,” the behavioral analysis of violent crime does not identify a specific individual. Rather, it associates a crime or series with perpetrator characteristics that can be used to guide the investigation. By relating a current investigation to an earlier, solved case, additional elements can be highlighted (e.g., things that you might want to look for, why they did something, and investigative strategies, particularly interviewing).
11.3 Strategic Characterization
Where Do Murderers Come From?
The “nature versus nurture” question has swirled around in behavioral biology through several generations of scientists at this point, and the most reasonable answer seems to be that human development probably incorporates a little bit of both. One area where this question has some particular urgency, however, involves juvenile murderers. Many people look at a particularly heinous crime that has been committed by an individual who meets both the legal and chronological definitions of a child and wonder just where this individual came from to be able to commit such a heinous crime. In the course of my research, I have reviewed more than a few cases that fit these criteria and have been impressed again by the relative degree of behavioral homogeneity between the crimes committed by young people with relatively limited access to information regarding their chosen field of criminal expertise, and those committed by others who seem to have an abundant source of example and mentoring. Beyond the impulsive juvenile murderers who kill secondary to the commission of another felony, there lies another group that has taken murder to a level that seems to truly transcend their age and relative amount of life experience. As a result of this anecdotal experience, I have tended to informally subdivide juvenile murderers into two groups: those who learn how to kill, and those who seem to have an intuitive sense or need to kill.7
The first group generally uses violence or murder to achieve some sort of secondary objective. For this group, violence frequently is a means to an end, a way to achieve a particular goal. This type of juvenile murderer is especially prevalent in illegal drug markets. For example, in illegal drug markets, violence frequently is used to enforce rules and norms, particularly as there is limited access to legal enforcement mechanisms.8 In other words, if Bob sold Joe some bad dope, Joe generally could not expect to receive much help from the economic crimes unit at the local police department. It is not unusual for these offenders to commit multiple murders, and even use crime scene behavior and postmortem mutilation or positioning to send a message to the community, behaviors and practices frequently associated exclusively with serial killers. However, killing for these youthful offenders is a means to an end. Any additional behavior or manipulation of the victim’s remains often represents a punctuation mark to the underlying message sent.
This group seems to have acquired their skills through a process of social learning. These kids learn by watching others commit violent crimes and use violence to achieve secondary goals and objectives. This also relates to the idea that drug selling, like law enforcement, is a 24/7 profession. If one is to succeed in the extremely predatory world of illegal drug sales, then it is important to convey a sense of power and strength in every life domain. It would be extremely dangerous to be perceived as weak in a social setting, for example. This has been described previously as the “outlaw” lifestyle, and it can be linked to some murders involving those linked to illegal drug markets but not directly to a drug-selling transaction. Drug-involved violence, in particular, has been studied and characterized in some detail, which forms a great foundation and framework for the use of data mining and predictive analytics in the analysis of violent crime.
Consistent with the social learning model, Bennet, DiIulio, and Walters wrote a book titled Bodycount.9 At the time of its publication, their concept of a juvenile “superpredator” received a tremendous amount of press. At first, the concept of a superpredator seemed alien, almost offensive. He was almost like a “robocriminal,” relatively automatic, with slim prospects for rehabilitation. Over time, however, as I encountered more young killers like those involved in illegal drug markets, it became clear that there were some kids who had been changed significantly and perhaps irrevocably by their environments.10 Ongoing and repeated insults during critical periods of emotional and moral development had changed their cognitive set, to the point where they employed different rules of the road as they negotiated the twists and turns on their life path. That is why I am so sad to see young children in the arms of adults at crime scenes, because these events often represent the first steps in the social learning process that ultimately turns out juvenile murderers and victims in our urban combat zones.
The second group of juvenile murderers just seems to like to kill, whether to fulfill a need to attain the ultimate power over another human being or to gain the opportunity to engage in unlimited exploration of the human body. This group is particularly intriguing, given the intuitive sense that they seem to have for what they want or need to do. Their intuition frequently is associated with very little outside input, although this has been changing in recent years.
It is interesting to study historical cases of serial sexual homicide, many of which were used as the basis for the creation of criminal investigative analysis, and note the eerie similarities between many of the crimes. The relative degree of homogeneity between the crimes committed by these different individuals is uncanny, given the lack of contact between the individuals and the relatively limited public knowledge and understanding of this behavior even a few years ago. The fact that this behavior is so similar and predictable that it can be used to enhance the investigative process really begs the question, “Where does violence come from?”
Even more intriguing are the young people who go through a similar developmental process as they begin to explore violence. Recent increases in the prevalence and availability of reference materials regarding serial murder and other types of violence seem to have increased the sophistication of the methods and desires associated with this group. It is for this reason, perhaps, that this group can be a particular challenge in terms of the relative degree of sophistication associated with their pattern and methods. Through the use of educational materials or facilitators, their crimes can be almost indistinguishable from those committed by much older individuals, which presents a significant challenge to those charged with investigating their crimes. Frequently, the question is not, “Could a child do this?” The answer to that question is almost always, “Yes.” Rather, the question now has become, “Is the juvenile suspect that I am considering capable of committing this crime?”
Again, by using data mining and predictive analytics, it is possible to transcend human bias and opinion, particularly regarding juvenile suspects, in an effort to reveal the underlying elements of a crime, prepare a strategic characterization of the likely offender, and close cases that formerly challenged even the most seasoned investigators.
Frequently in an actual investigation, the nature of the victim-perpetrator relationship is unknown. It is the crime scene characteristics and victim lifestyle factors that suggest a possible motive, which then is used to identify possible suspects. In fact, it is this type of strategic characterization of likely suspects that is embodied in the behavioral analysis process.
Some of our earliest work using advanced statistics for characterizing violent crime involved the development of automated motive determination models.11 Again, this work arose out of some lively discussions regarding whether it is possible to accurately model violent crime using automated methods. The cases used for this study included 25 juvenile murderers incarcerated in the Commonwealth of Virginia Juvenile Correctional Centers from February 1992 to July 1996. Information pertaining to the victims, suspects, injury patterns, and the behavioral characteristics of the assault were identified and analyzed in an effort to determine whether it was possible to determine the motive using automated methods.
For the first analysis, all of the information that could possibly be obtained was put into the model. The analytical approach selected was discriminant analysis, which is a classification modeling algorithm. These tools are covered in greater detail in Chapter 7; in brief, discriminant analysis is a multivariate statistical approach that can be used to identify factors that are useful in determining group membership. Generally, one of the assumptions with the use of discriminant analysis is that the variables used to create the model are continuous. While some of the data available for this study were continuous (e.g., age), most of the relevant information was either binary or categorical. As a modeling tool, however, discriminant analysis is robust enough to accommodate a violation of this assumption. Basically, the type of error most likely to occur with a violation of this type is that a model will not emerge, even though there might be a relationship in the data.12 The issue of errors and how they should be evaluated is addressed in Chapter 4. In a motive determination model, any error that would misdirect an investigation could potentially be catastrophic, as it would waste investigative resources. Moreover, delay in the investigative process could seriously compromise the ultimate ability to solve the case. Therefore, failure to identify a model due to the violation of the data type assumption was determined to be acceptable after thoughtful consideration of the ultimate role for any potential models.
The initial results were extremely promising. Using information related to recent victim drug use and suspect substance use history, it was possible to accurately categorize 85% of the cases as drug-related or not drug-related. One interesting finding regarded the direct relationship between the suspects’ use of illegal drugs, particularly marijuana, and their involvement in a drug-related homicide. Our earlier work had confirmed conventional wisdom among narcotics detectives: Most successful drug dealers do not use the drugs that they sell.13 In fact, substance use has been associated with an increased risk for firearms assaults among drug sellers. Whether our finding was a cause or a consequence was not entirely clear, but substance use was not a healthy choice, particularly among those involved in the sale and distribution of illegal narcotics. Therefore, this result was somewhat surprising. Further examination revealed that the suspects’ substance use generally involved marijuana, while the recent victim use included cocaine and opiates (e.g., heroin). This finding was consistent with a model of drug-related violence that proposed different subtypes of drug-related violence associated with different types of suspect, similar to a division of labor within drug distribution networks.14 In particular, the suspects who emerged in this preliminary study were very similar to the “enforcers” described in this model.
The end result of this preliminary study was support for the notion that violent crime could be modeled using advanced statistics, as well as additional knowledge regarding our understanding of drug distribution networks and the proposed division of labor. From an investigative standpoint this was somewhat helpful, in that it offered additional information pertaining to the types of individuals likely to commit drug-related violence; however, it provided little more in the way of enhanced investigative efficacy. In other words, the results of this study indicated that recent victim use and suspect use were good indicators of drug-related violence. From an investigative standpoint, this creates circular logic: To identify the suspect, it is helpful to know the motive; to determine the motive, we need information regarding the suspect’s substance use; to know the suspect’s substance use habits, we need to know who the suspect is, which is the original question. Clearly, further work was needed.
11.4 Automated Motive Determination
More recent work in this area has been confined exclusively to the information that is available early on in an investigation. Again, drug-related violence represents a good area of study for several reasons. First, drug-related violence frequently drives the overall violent crime trends in many communities plagued by serious increases in violent crime;15 the homicide rate often rises and falls as a direct consequence of the drug-related homicide rate. Therefore, addressing drug-related violence can significantly reduce the violent crime rates in these communities.
Drug-related crimes, particularly violent crimes, can be difficult to solve in a timely fashion. Witnesses may be reluctant to come forward or may be unreliable. In some cases, drug-related violence is seen as “part of doing business,” reducing sympathy for the victim and making others less likely to get involved. The more time that elapses, however, the less likely it is that a murder will be solved. If significant progress is not made in the first few days of an investigation, it becomes increasingly unlikely that the case will be solved. Finally, and perhaps most importantly, drug-related violence appears to be relatively homogeneous and amenable to modeling, which makes it a good candidate to evaluate automated motive determination scoring algorithms.
Using automated classification techniques similar to those used earlier, drug-related homicides were analyzed in an effort to develop a model that could be used to automatically determine a motive using information available early in an investigation. The relevant variables that emerged were location, location, location. While this is an overly simplistic interpretation of the results, the most salient fact to emerge from this analysis was that certain areas were associated with an increased risk for drug-related violence (Figure 11-5).
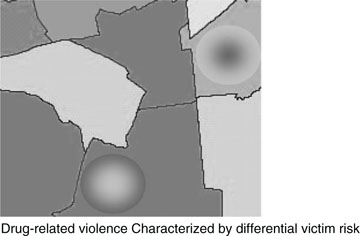
Figure 11-5 Drug-related violence models can be deployed through the use of mapping tools. These facilitate the development of proactive deployment strategies. This particular map highlights differences in victim characteristics, which might have additional value from an operational perspective.
The results were distilled and deployed through maps, which allowed for proactive, risk-based deployment specifically targeting drug-related violence. One interesting finding that emerged with the maps was that one particular area was associated with victims who were more likely to be employed. Further analysis of the location revealed a drug market frequented by users from the surrounding localities, which was consistent with employed victims. While this initially appeared to be nothing more than an interesting factoid, the operational implications quickly became apparent. Drug violence associated with employed victims was consistent with victims who were buyers. One way to reduce the violence in these areas was to reduce the number of potential victims. Demand reduction approaches offered the perfect solution to this finding, while different approaches could be used in other markets associated with different types of drug-related violence.
The opportunity to more fully characterize crime and tailor specific crime reduction approaches based on a thoughtful analysis of the problem is one powerful benefit of using data mining and predictive analytics in the development of operational strategies. Just as we cannot please all of the people all of the time, there is no universal “crime reduction” strategy that will work for every situation all of the time. While this seems entirely logical, it is very difficult to even begin to match an appropriate operational plan to a particular issue if the nature of the problem has not been characterized and defined. For those who would say, “Utilize, don’t analyze,” this approach offers a solution for evaluating operational approaches in a meaningful way—something that increasingly has become a requirement as resources are increasingly limited.
When the time of day, day of the week, and victims’ employment status were included in the analysis, the accuracy of the model increased concomitantly. Again, this model included only that information available early in an investigation; however, when the new information was added to the model, it became too opaque to have any value in the deployment process. Therefore, these results were deployed through a web-based package, which provides for 24/7 analytical capacity.16 As most homicide detectives can attest, people generally do not kill each other when it is convenient for us, particularly when drugs are involved. Most analytical teams, however, work normal business hours. By deploying algorithms through these web applications, operational personnel have the benefit of analytical help when they most need it: early in an investigation, when the case is progressing most rapidly.
11.5 Drug-Related Violence
Like homicide in general, drug-related violence can be categorized and divided further, based on the specific motive for the violence. When asking why this is relevant, it is important to remember that the more an investigator knows about what happened and why, the higher the likelihood that a suspect will be developed, effectively investigated, and prosecuted.
In his tripartite model of drug-related violence, Dr. Paul Goldstein17 has proposed three categories of drug-related violence. A fourth type of drug-related violence also should be considered that has been described as the “outlaw lifestyle.”18 Briefly, this type of drug-related violence is related to the fact that drug dealers, like police officers, generally are “on the job 24/7.” What this means is that to function effectively in an extremely predatory environment, the individual needs to always be “on.” A drug dealer involved in a violent drug market is going to have difficulty maintaining his safety when he is selling if he is perceived as being weak in other domains of his life.
A second benefit of analyzing violent crime in this fashion is that the outcomes can be used to guide the development of enforcement strategies. For example, a finding that in a certain area associated with open-air drug markets, most of the victims of drug-related homicides were employed is consistent with drug users being killed. A possible enforcement strategy in this situation could include aggressive demand reduction techniques in an effort to keep potential victims out of harm’s way. On the other hand, victim characteristics consistent with dealer rivalries or gang disputes over markets or territories would require a different approach.
11.6 Aggravated Assault
Many aggravated assaults can be viewed as incomplete or poorly planned homicides. Similarly, the line that separates a lethal from a nonlethal assault often reflects the quality of medical care or timeliness of response, rather than some specific intent on the part of the suspect. With that in mind, homicides and aggravated assaults can be viewed more as a continuum, rather than as two separate and distinct entities. When we explore this a little further, it makes sense based on what we know of violent crime. For example, the number of innocent victims associated with drive-by shootings supports the fact that drive-bys frequently do not go according to plan. Vehicle movement, unreliable weapons, and random bystanders all contribute to the variability associated with this type of violence. Similarly, it is not unusual for there to be several nonlethal assaults that precede a domestic homicide. Therefore, many of the same approaches to the analysis of murder can be applied to nonlethal assaults. One important difference from a data mining perspective, however, is that there usually are more nonlethal assaults than homicides. While this is a good thing for a community, it also is a very good thing for the analyst, as there generally are more incidents available for analysis and modeling.
11.7 Sexual Assault
Stranger rapists can be some the most disturbing predatory criminals a detective will encounter. Even the hint of a serial stranger rapist can create a climate of fear in a community. Several years ago, during a casual conversation, Dr. Paul Ferrara, the director of forensic scientists in Virginia, noted that a surprising number of the DNA “cold hits” for predatory sex crimes had come from criminals without prior histories of sex offending. At the time, Virginia was noteworthy for having created a very successful offender DNA database with broad inclusion criteria. While some states were confining their samples to convicted sex or violent criminals, the Commonwealth of Virginia obtained DNA samples from all convicted felons.
Dr. Ferrara noted that several of the offenders identified by cold hits were associated with prior property crimes, particularly burglaries. In some ways, this finding was not surprising, in light of what we know about sexual predators and some violent criminals. In reviewing violent crimes, it is not unusual to find a pattern of escalation that includes crimes that do not appear violent initially. For example, Timothy Spencer, the “Southside Strangler” and first person convicted with DNA evidence, had a history of burglaries in northern Virginia that preceded the homicides that he committed later. Similar cases have revealed a pattern of burglaries or trespassing that preceded escalation into more serious patterns of offending.
An initial review of the data revealed that approximately 40% of the cold hits were associated with offenders who had no documented history of either sex crimes or violent offending. Perhaps more importantly, had the database been confined to these patterns of offending, approximately 40% of the criminals might not have been caught and thus would have been allowed to continue to prey on their communities.19
Exploring this finding offered at least two benefits. First, the ability to characterize and identify patterns of offending that indicate an increased likelihood for escalation offers the promise of early detection, enhanced investigative efficacy, and increased community safety. This also creates increased opportunities for early detection and intervention for sex offenders, who have a pattern of offending that is noteworthy for its high recidivism rate and resistance to treatment. Second, an increased understanding of sex offenders, how they escalate, and how they prey on the community gives behavioral scientists an opportunity to better understand this particularly challenging form of criminal behavior. This greater understanding offers the promise for early intervention and the concomitant increase in public safety.
The initial study involved reviewing large correctional databases. Using discriminant analysis, models were created to determine which factors were predictive of subsequent stranger rapes. Not surprisingly, prior offense history reliably emerged as the most predictive variable. What was a shock, however, was that a prior property crime actually was a better predictor for a stranger rapist than a prior sex offense. It is important to note that discriminant analysis ideally is used with continuous variables, while offense history frequently is confined largely to categorical variables. Because discriminant analysis is such a robust statistical test,20 however, it was permissible to violate this assumption. The most likely error to occur when this assumption is violated would be a failure to identify a model, which was acceptable given the nature of the question.
Subsequent manual review of the paper files associated with these offenders revealed some differences in the nature of the property crimes they perpetrated. In several cases, these offenders appeared to specifically target occupied dwellings. When someone was home at the time of the break-in, it frequently was a female alone, or a female with small children. In addition, these offenders frequently took items of little or no value, if they removed anything at all from the residence. This behavior is inconsistent with a purely economic motive for the crime.
In many ways, these crimes differed qualitatively from traditional burglaries. Reduced to its simplest form, a burglary is an economic crime in which the offender tries to maximize the yield while managing the risk of being caught. The individuals associated with a subsequent stranger rape distinguished themselves from “normal” burglars in that they incurred a greater degree of risk in preferentially targeting occupied dwellings, and generally had little to show for their efforts other than a few items that could be viewed as souvenirs. In other words, their crimes were abnormal.
The discovery and confirmation processes associated with data mining expanded our understanding of stranger rapists. This new understanding was used to generate a brute force anomaly detection system for identifying crime patterns and trends determined to be at increased risk for escalation. Perhaps more importantly, it also resulted in the development of a general principle regarding “normal” crime. Since the original study, this concept has been applied successfully to other nonviolent crimes that deviate in some way from “normal.” In other words, anything that suggests some type of secondary gain beyond or instead of the economic motive generally associated with the crime is cause for concern because it frequently indicates potential for escalation or more serious patterns of offending. Similarly, any preferential behavior on the part of the offenders that increases their risk of detection or apprehension also is cause for concern.
In England, the West Midlands police have conducted very successful work using predictive analytics to characterize and apprehend sexual predators. Through the use of self-organizing maps or clustering algorithms, they were able to identify clusters or groups of crimes that were similar. These similarities were based on a variety of relevant dimensions, which included method of approach, verbal themes, precautions taken to prevent detection, and victim characteristics.21
This work is particularly encouraging because many of the category clusters identified in this study match classifications described previously in the United States.22 This similarity suggests commonalities in some patterns of offending that might transcend national and perhaps even cultural boundaries. Therefore, unlike some business, health care, and educational applications of data mining and predictive analytics, work in the public safety and intelligence arena promises to transcend national boundaries. This further increases the number of potential end users for predictive algorithms, while enhancing the opportunities for increased resource exploitation of criminal justice data resources and predictive algorithms.
11.8 Victimology
In some ways, victimology, or the study of the relationship between certain individual attributes and the risk for violent crime, can be seen as a logical extension of risk assessment. Examining victim characteristics can be used in two ways. First, it frequently has value from an investigative standpoint because identification of victim lifestyle issues or risk factors often can suggest a possible motive and, by extension, a likely suspect.
On the other hand, some insight regarding potential risk factors associated with violent crime opens the door to meaningful, specifically targeted prevention strategies. Many victims of violence suggest that their injury was the result of “bad luck” or that they were merely in the “wrong place at the wrong time.” If that was the case, there would be very little that we could do to reduce violent crime, other than identify the perpetrators and get them off the streets as quickly and for as long as possible in an effort to reduce crime. Crime prevention would rely almost exclusively on investigative efficacy.
We have come to realize that certain victim attributes can increase or even be related directly to an individual’s risk for violent victimization. For example, prostitutes are at increased risk for sexual assault and other violent crimes due to their involvement in that pattern of criminal activity. Similarly, substance users are at increased risk for violence related to their involvement with illegal drug markets. These frequently are referred to as “lifestyle” factors, meaning that some aspect of the victim’s lifestyle increased his or her risk for violence.
This is a very important point, because if violent victimization truly is related only to “bad luck,” we are limited in our ability to prevent violent crime. But if we can identify particular behaviors or activities that are linked to an increased risk for violent crime, then we have an opportunity to try and change those behaviors, which might concomitantly reduce the risk for violent crime. By reducing the risk associated with some of these individuals, the amount of lead flying through the air also will be reduced, which will reduce the “bad luck” associated with those individuals who truly were in the wrong place at the wrong time. By drilling down into the data, it is possible to identify certain groups that are at greater risk for violence than others.
Victim Risk Factors
While it certainly is true that different people get killed for different reasons, what factors increase someone’s risk for being the victim of a violent crime, and what does this have to do with data mining? Analysis of aggregate victim data generally reveals little, if anything, regarding specific victim risk factors. By drilling down into the data, researchers have found that one of the best predictors for violent victimization is involvement in criminal offending. However, this remains too broad a category to identify any specific risk factors. Therefore, it is necessary to parse the data even further in an effort to identify relatively homogenous groups that would be acceptable for modeling purposes.
By examining firearms injuries among juvenile offenders, certain patterns of associated risk could be identified and characterized. Certain attributes like promiscuity were noted among most of the categories, but others differed significantly. One attribute of particular interest was involvement with firearms. In particular, it was found that violent offenders who had been shot previously were more likely to admit to possessing a weapon, while juvenile drug sellers were much less likely to indicate that they carried a weapon. Additional information collected during this study ultimately had implications for officer safety in the field.
Analysis of aggregate statewide injury rates really did not reveal many differences among the different patterns of offending. When the data were categorized by community, however, differences began to emerge. In particular, juvenile drug sellers were much more likely to be shot in poorer communities than in those that were more affluent. Perhaps this was because there were more open-air drug markets in the impoverished communities, or perhaps robbery was the real motive. Regardless of the cause, this differential risk associated with specific community characteristics further illustrated the finding that victim risk represented a complex array of individual and community factors that interacted to determine the composite threat associated with a particular individual.
This finding was revisited several years later when it was noted that certain victim characteristics were related to geography in determining drug-related homicides associated with a particular drug market or area. During the development of the risk-based deployment strategies for drug-related violence, for example, it was noted that certain areas were associated with more victims who were employed, while other areas were associated with victims who were less likely to be employed. While correlation certainly does not imply causality, this particular finding had value in terms of creating meaningful enforcement strategies that could be targeted specifically to the likely victims.
Child Abduction
Another area in which the characterization of victim attributes can indicate the likely suspect and even probable outcome is child abduction. In a series of excellent papers, members of the Federal Bureau of Investigation’s National Center for the Analysis of Violent Crime have characterized this pattern of offending in great detail.23 Briefly, these researchers have identified a reliable association between victim age and gender and the likely offender, reason for the abduction, and probable outcome. Again, this type of victim characterization and modeling has tremendous implications for enhanced investigative efficacy in cases where investigative speed can be related directly to the likelihood of a good outcome.
11.9 Moving from Investigation to Prevention
Improving investigative efficacy is very important, but what if violent crime could be characterized, anticipated, and even predicted? If this were possible, then we would have an opportunity to engage in proactive strategies that would prevent crime before it happened. In death investigations, the act already has been committed, but what if it was possible to anticipate who was next? Minimally, the high rate of subsequent assaults and murders documented in victims of violent crimes24 identifies them as a group at extraordinarily high risk for violent assault and murder. It is unknown whether this increase is associated with the idea that each aggravated assault really represents an incomplete or poorly planned homicide, or because the same lifestyle factors that resulted in the first assault are still present. By identifying who is at risk, where, and why, traditional enforcement strategies can be matched and targeted to specific patterns of risk. Through the use of predictive analytics to create a rule set for drug-related homicides, for example, it could be determined that victims killed near a particular drug market were more likely to be employed. Additional information may indicate that this particular market was frequented by younger, relatively affluent, recreational drug users from neighboring communities. One possible approach in this situation would be a demand reduction strategy such as “reversals,” where police officers play the role of drug dealers in an effort to identify and arrest users, ultimately keeping the potential victims away from a dangerous activity or market. A different approach might be warranted for drug-related homicides involving individuals associated with other illegal drug markets. Identification, characterization, and modeling of victim risk factors represent another use for data mining and predictive analytics in our efforts to reduce violent crime.
11.10 Bibliography
1. McLaughlin, C.R., Yelon, J.A., Ivatury, R., and Sugerman, H.J. (2000). Youth violence: A tripartite examination of putative causes, consequences and correlates. Trauma, Violence & Abuse, 1, 115–127.
2. Cohen, L.E. and Felson, M. (1979). Social change and crime rate trends: A routine activity approach. American Sociological Review, 44, 588–608.
3. McLaughlin et al. (2000).
4. Casey, E. (2002). Using case-based reasoning and cognitive apprenticeship to teach criminal profiling and internet crime investigation. Knowledge Solutions; www.corpus-delicti.com/case_based.html
5. See Westveer, A.E., ed. (2002). Managing death investigation. Washington, D.C. U.S. Department of Justice, Federal Bureau of Investigation; or Geberth, V.J. (1996). Practical homicide investigation: Tactics, procedures, and forensic techniques, 3rd ed. CRC Press: New York.
6. Goldstein, P.J. (1985). The drugs/violence nexus: A tripartite conceptual framework. J Drug Issues, 15, 493–506.
7. McCue, C. (2002). Juvenile murderers. In Managing death investigation (Arthur E. Westveer, ed.), pp. 481–489. Washington, D.C., U.S. Department of Justice, Federal Bureau of Investigation.
8. Goldstein (1985).
9. Bennett, W.J., DiIulio, J.J., and Walters, J.P. (1996). Body count. Simon & Schuster, New York.
10. McLaughlin et al. (2000).
11. McLaughlin, C.R., Daniel, J., and Joost, T.F. (2000). The relationship between substance use, drug selling and lethal violence in 25 juvenile murderers. Journal of Forensic Sciences, 45, 349–353.
12. Klecka, W.R. (1980). Discriminant analysis, Sage: Beverly Hills.
13. McLaughlin, C.R., Reiner, S.M., Smith, B.W., Waite, D.E., Reams, P.N., Joost, T.F., and Gervin, A.S. (1996). Firearm injuries among Virginia juvenile drug traffickers, 1992 through 1994 (Letter). American Journal of Public Health, 86, 751–752.
McLaughlin, C.R., Smith, B.W., Reiner, S.M., Waite, D.E., and Glover, A.W. (1996). Juvenile drug traffickers: Characterization and substance use patterns. Free Inquiry in Creative Sociology, 24, 3–10.
McLaughlin, C.R., Reiner, S.M., Smith, B.W., Waite, D.E., Reams, P.N., Joost, T.F., and Gervin, A.S. (1996). Factors associated with a history of firearm injuries in juvenile drug traffickers and violent juvenile offenders. Free Inquiry in Creative Sociology, Special Issue: Gangs, Drugs and Violence, 24, 157–165.
14. Goldstein (1985).
15. McLaughlin, C.R., Robinson, D.W., and Faggiani, D. (1998). Declining homicide rates in the 1990s: Not everywhere! Academy of Criminal Justice Sciences.
16. McCue, C. and Parker, A. (2004). Web-based data mining and predictive analytics: 24/7 crime analysis. Law Enforcement Technology, 31, 92–99.
17. Goldstein (1985).
18. McCue (2002).
19. McCue, C., Smith, G.L., Diehl, R.L., Dabbs, D.F., McDonough, J.J., and Ferrara, P.B. (2001). Why DNA databases should include all felons. Police Chief, 68, 94–100.
20. Klecka (1980).
21. Adderly, R. and Musgrove, P.B. (2001). Data mining case study: Modeling the behavior of offenders who commit serious sexual assault. ACM Special Interest Group on Knowledge Discovery and Data Mining.
22. Ressler, R.K., Burgess, A.W., and Douglas, J.E. (1988). Sexual homicide: Patterns and motives. Lexington Books, New York.
23. Lord, W.D., Boudreaux, M.C., and Lanning, K.V. (2001). Investigation of potential child abduction cases: A developmental perspective. FBI Law Enforcement Bulletin, April.
24. Sims, D.W., Bivins, B.A., OBeid, F.N., Horst, H.M., Sorenson, V.J., and Fath, J.J. (1989). Urban trauma: A chronic recurring disease. Journal of Trauma, 29, 940–947.