Keep Your Enemies Closer ◾ 235
e Verizon 2009 “Data Breach Investigation Report” shows that insider attacks have three times
the impact of external attacks, and the CERT 2009 “Common Sense Guide to Prevention and
Detection of Insider reats” details damages from sabotage and theft that extend into the mil-
lions of dollars range.
[A] hostile insider with access to vulnerable critical systems, potentially combined
with knowledge of that system has the potential to cause events that would far exceed
the consequences of an intrusion or attack.
e Insider reat to Critical Infrastructures
NIAC Report, April 2008
One other thing existing research underscores is just how poorly the industry is dealing with
the situation. Most companies do not actively manage their insider risks. Corporate culture, orga-
nization, and leadership are three big factors. Companies want to trust their employees (especially
long-timers), and they fi nd it distasteful to “spy” on them. e lack of convergence in security
management also hampers mitigation eff orts by limiting data exchanges between access con-
trol systems and IT identity management functions. A study group sponsored by the Computer
Security Institute in 2007 concluded, “Surveys have shown corporate leadership understands
that insider incidents occur, but it appears corporate leadership neither completely appreciates
the risk nor realizes the potential consequences.” e problem extends to supervisors as well.
Supervisors seldom have the time or the training needed to identify and mitigate employee issues
before they become malicious. is was another interesting fi nding in the research: Virtually
all inside attackers manifest the same behavior patterns leading up to their malicious actions
(e.g., stress, anger, disrespect, etc.), but, for the most part, their supervisors ignore these pat-
terns. Enforcement is another management problem. e enforcement of security policies and
standards at most organizations is inconsistent or lackadaisical at best, and security is seldom
granted the authority to enforce compliance. Another major challenge to insider threat mitigation
is technology. e technologies we need to hold people accountable for their actions are lacking,
including the ability to:
Manage and maintain employee identities across multiple platforms ◾
Create and preserve audit trails of employee actions ◾
Consolidate and collate data ◾
Detect patterns of malicious insider activities ◾
Nonetheless, accountability remains the best tactic for dealing with malicious insiders; fol-
lowed by competent supervision and comprehensive employee screening. (Accountability tactics
and control objectives are covered in detail in Chapter 10 and will not be repeated here.)
Competent Supervision
Supervision and supervisory controls have been in place in the banking industry for decades.
Separation of duties, forced vacations, job rotation, and other measures are all designed to
reduce the likelihood of fraud, theft, or other types of malfeasance in environments with sensi-
tive and high-value assets. Good supervisory controls in other environments are almost unheard
of. Unlike banking where real money is involved, managers in other industries tend to be
TAF-K11348-10-0301-C012.indd 235TAF-K11348-10-0301-C012.indd 235 8/18/10 3:11:56 PM8/18/10 3:11:56 PM
236 ◾ Security Strategy: From Requirements to Reality
complacent about insider threat; that is, they do not associate malicious insiders with high-value
losses. But a privileged user (one with root or admin access) can cause irreparable damage to
company-owned information assets and cause huge downstream damages to company employ-
ees, customers, and other innocent victims—not to mention the hit the company’s brand image
and reputation will take. One incident reported by CERT involved a terminated employee who
launched a logic bomb that deleted over 10 billion records from his former employer’s servers.
e restoration costs exceeded $3 million, and many records were permanently lost. It’s amazing
to think that in most companies, people with this level of access receive less supervision than a
bank teller.
ere are a number of contributing factors to this dilemma. Management complacency (or lack
of awareness) is one; lack of proper training is another. e move away from command and control
structures to empowered employees and self-directed teams is another. Cost cutting, work from
home, and geographic dispersions are others. When cost-cutting measures are in place, managers
end up supervising an increasingly larger number of employees. While government ratios remain
in the 7 to 1 range, private industry ratios are double that and climbing! It’s not unusual to have
a “distant” manager in today’s connected and geographically diverse work environments. When
Bill worked at Predictive Systems’ California offi ce, the boss’s offi ce was in Reston, Virginia. He
never actually met the boss in person: Meetings were by telephone, and he was even laid off by
phone when the dot-com bust hit in 2000. Given the realities of today’s business environment, it’s
unlikely these things are going to change, and for many job functions that’s okay. But for high-
privileged positions, that’s not only dangerous but just plain stupid. Virtually every malicious
insider attack we reviewed was discernible, but how do you discern bad behaviors when you don’t
actively engage with your workforce? e lack of direct (face-to-face) interaction can also be one of
the causes for illicit behavior. People require care; we believe that fully one-third of a leader’s time
should be devoted to the people working for him or her. When mangers are swamped with duties
and overloaded with people, people are the ones who suff er. Requests go unanswered, one-on-one
meetings get canceled, and the attention and recognition people need get lost. Is it any wonder
that employees get stressed out, dissatisfi ed, and disgruntled?
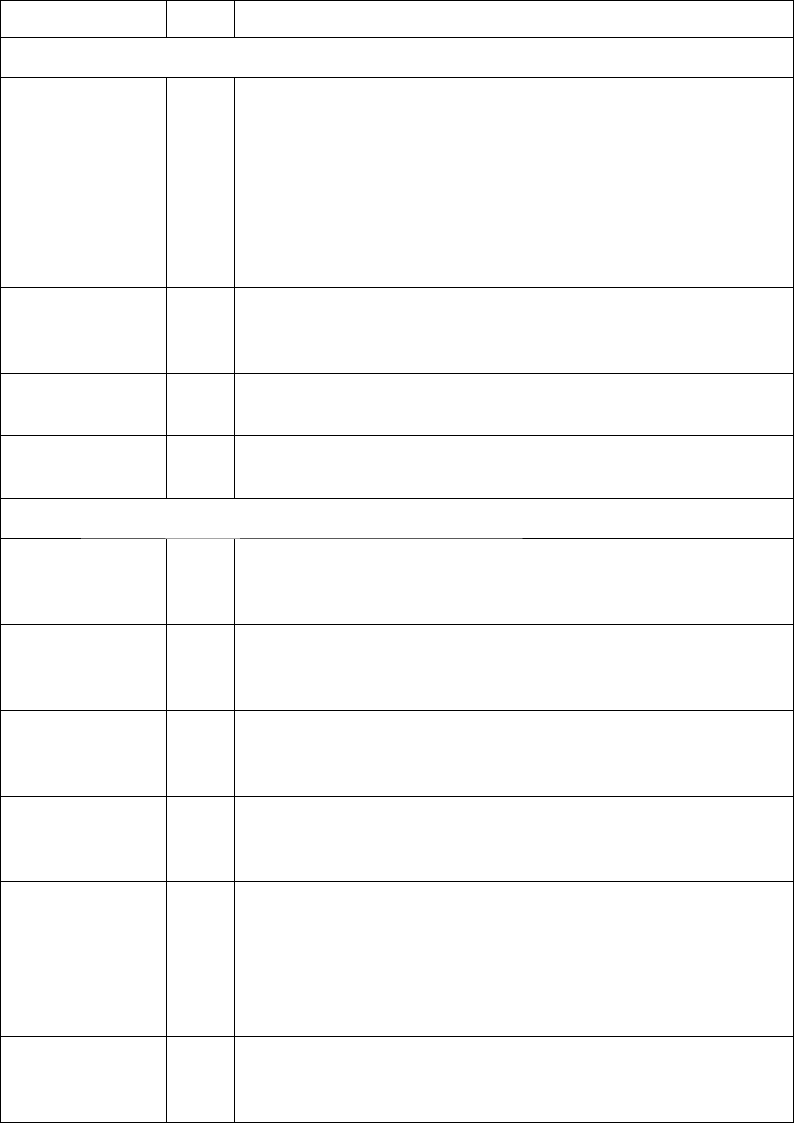
Competent supervision is a combination of supervisor and supervisory control objectives.
Table 12.1 maps the attributes of these control objectives to specifi c user threat baselines. e
type (hard or soft) is used to denote how evidence is collected for each control. Soft indicates a
procedure-based control, while hard denotes a technology-based (i.e., automated) control.
Supervisor Attributes
Supervisor attributes apply to the managers and other personnel charged with the oversight of
other workers, including employees, contractors, vendors, and partners working within their
sphere of responsibility. is combination of workers is generally considered to be the organiza-
tion’s staff .
Trained
e “trained” control objective ensures that the supervisor has the proper knowledge, skills, and
abilities (KSAs) to hire trustworthy individuals for security-sensitive positions and to properly
monitor the activities of their staff against company requirements. Supervisors, especially those
responsible for personnel with highly privileged access to company assets (i.e., servers, data ware-
houses, etc.) or access to high-value assets (i.e., bank accounts, payroll, etc.), need to be trained in
TAF-K11348-10-0301-C012.indd 236TAF-K11348-10-0301-C012.indd 236 8/18/10 3:11:56 PM8/18/10 3:11:56 PM
Keep Your Enemies Closer ◾ 237
Table 12.1 Control Objectives for Malicious Insider Threats
Attribute/Control Type Risk and Requirements
Supervisor
Trained Soft Supervisors of personnel with highly privileged access or access
to sensitive information must be trained in:
1. Employee monitoring techniques
2. The recognition of behaviors indicative of malicious or
potentially malicious acts
3. Proper response procedures for dealing with bad behaviors
4. Proper screening techniques for hiring
Observant Soft Supervisors of personnel with highly privileged access or access
to sensitive information must consistently observe employee
behaviors to detect illicit acts.
Enforcing Soft Supervisors must consistently enforce security policies and
controls, including applicable sanctions for illicit employee acts.
Cautious hirer Soft Supervisors must exercise “due care” when hiring people for
highly privileged or sensitive positions.
Supervisory
Separation of
duties
Soft High-value or highly privileged actions cannot be completed by
a single person; actions must require the participation of two
separate persons for completion.
Least privilege Hard Privileged and high-value accesses must be confi ned to the
specifi c assets the user requires to accomplish his or her
assigned tasks.
Isolated Hard Personnel with highly privileged access or access to sensitive
information must be physically and logically isolated from the
systems used to monitor and record their activities.
Rotated Soft Personnel may be periodically moved to different positions,
work locations, or shifts to reduce the likelihood of collusion
with others for actions requiring multiple actors.
Rescreened Soft
Soft
Personnel with highly privileged access or access to sensitive
information must be periodically rescreened to identify factors
related to their trustworthiness.
Internal transfers and temporary staff transitioning to permanent
positions must be rescreened to high-privilege/high-value
position standards.
Forced leave Soft Personnel with highly privileged access or access to sensitive
information may be required to take leave of a specifi c duration
each year to facilitate the detection of illicit behavior.
TAF-K11348-10-0301-C012.indd 237TAF-K11348-10-0301-C012.indd 237 8/18/10 3:11:57 PM8/18/10 3:11:57 PM
238 ◾ Security Strategy: From Requirements to Reality
proper staff -monitoring techniques, including technical and people-oriented sources of informa-
tion. Supervisors must be able to recognize and respond to behaviors that violate company ethics,
policy, or human resource standards. is includes internal and external behaviors that are com-
mon precursors to malicious acts such as co-worker abuse, repeated policy violations, and arrests.
Supervisors must also be trained in proper screening techniques when hiring or contracting for
positions with highly privileged access or access to high-value assets. Techniques may include addi-
tional background investigations, written assessments, and advanced interviewing procedures.
Observant
e “observant” control objective ensures that supervisors are doing “due diligence” in their man-
agement of staff security performance. As noted earlier, supervisors should devote one-third of
their schedule to the oversight of their staff . Oversight includes both personal interactions and the
review of technical control information (e.g., logs, alerts, video, etc.). Supervisors need to regularly
review staff activities to identify violations of company ethics, policy, or human resource stan-
dards. Supervisors may choose to solicit additional information from other staff members as well.
When personnel know that their activities are being observed (monitored), they are less likely to
commit an act of malfeasance. In addition, regular reviews help the leadership identify areas where
additional training or controls may be needed.
Enforcing
e “enforcing” control objective assures consistency in the application of policy requirements across
the enterprise. Supervisors must actively manage policy violations by their employees. Disciplinary
actions must be applied equally across the organization to avoid the appearance of favoritism.
Employees must understand the value the organization places on security. When employees are sub-
ject to disciplinary actions, they are more diligent in adhering to policy requirements. Conversely,
poorly enforced policies create an environment that is more susceptible to attack.
Cautious Hirer
e “cautious hirer” control objective ensures that supervisors have exercised “due care” when
hiring people for highly privileged or sensitive positions. Due care implies that all reasonable and
prudent measures were taken in the screening of a candidate for highly privileged or sensitive posi-
tions. Background checks should include fi ngerprint checks whenever possible to assure the positive
identifi cation of the applicant and a full-disclosure of criminal history. Other forms of evaluation
that are recommended include psychological assessment questionnaires and drug testing.
Supervisory Attributes
Supervisory attributes apply to the management or limitation of personnel activities, for example,
limiting their physical access to company facilities.
Separation of Duties
e “separation of duties” control objective ensures that high-value or high-impact actions can-
not be carried out by one person, thus reducing the likelihood of malicious high-impact events.
TAF-K11348-10-0301-C012.indd 238TAF-K11348-10-0301-C012.indd 238 8/18/10 3:11:57 PM8/18/10 3:11:57 PM
Keep Your Enemies Closer ◾ 239
Approvals are a simple example of this control, provided the approval is required before the trans-
action can be completed. is is a common source code control; new versions of the code cannot
be checked into the source safe without the review and approval of the change control manager.
More sophisticated versions of this control involve multiple parties to complete single tasks, for
example, requiring two parties to simultaneously turn the keys to arm an ICBM (Intercontinental
Ballistic Missile). is control object can be implemented as a procedure or a technical control.
When the control is procedural, supervisors must make sure that the persons involved in the
transaction are suffi ciently isolated from each other to prevent collusion. Separation of duties is
most commonly used for transactions involving money, intellectual property, source code, secu-
rity devices, and backup and restore operations.
Least Privilege
e “least privilege” control objective makes sure that users and processes do not have access to
assets that are not required for the proper execution of their assigned job or function. Least privi-
lege is a very old security principle. Inside a castle compound, people were restricted to the area
where they worked, and access to the lord’s chambers was controlled by armed guards. Least privi-
lege means you are explicitly allowed access to a specifi c set of assets and nothing else. However,
the practical application of least privilege using today’s general-purpose operating systems and
business applications is extraordinarily diffi cult. Poorly designed applications, inadequate tools,
and poor identity management practices all contribute to problems. e best compensation for
the lack of technical controls is supervision. Supervisors should regularly monitor the activities of
employees to ensure that they are not violating acceptable use guidelines by accessing information
they have no legitimate need for. Accountability controls that record user access are useful for
this purpose and often have confi gurable rules that can detect unauthorized activity. Today, least
privilege in general-purpose computing is really a trade-off between functionality and protection;
when protection cannot be achieved with technology, competent supervision is required.
Isolated
e “isolated” control objective ensures that personnel with highly privileged access or access to
sensitive information are physically and logically isolated from the systems and processes used
to monitor and record their activities. For example, access to system logs and logging services
is restricted. When dealing with privileged users, isolation can be diffi cult to achieve. System
administrators have the ability to disable audit/logging services and destroy or alter audit records.
ere is no practical way to prevent this, but it is possible to use a centralized monitoring and/
or log collection service to capture these events to an incorruptible system (e.g., confi guring sys-
tems to forward log entries to a Syslog server). While this tactic may not prevent a malicious user
from disabling log forwarding, it will record the disablement event for future investigation. When
technological controls are not in place, the best compensating control is competent supervision.
Supervisors should regularly monitor employee activities for events indicative of “hiding”—that is,
attempts to conceal their activities by deleting, falsifying, or altering audit records.
Rotated
e “rotated” control objective ensures that personnel with highly privileged access or access to
sensitive information are periodically assigned to diff erent positions, work locations, or shifts to
TAF-K11348-10-0301-C012.indd 239TAF-K11348-10-0301-C012.indd 239 8/18/10 3:11:57 PM8/18/10 3:11:57 PM
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
