The design and implementation of a corporate security policy is site specific. After you have identified the critical assets and analyzed the risks, it is time to design the policy by defining the guidelines and procedures to be followed by corporate personnel.
To be effective, the procedures should be concise and to the point. Don't write a large cumbersome document few people will actually read. A short document of fewer than 10 pages should suffice as a start. Technical implementation details should not be included because they can change over time. If a corporate network infrastructure is already in place, you might have to modify the existing ad-hoc security procedures to align more closely with the newly created policy. The design of the policy takes careful planning to ensure that all security-related issues are adequately addressed.
This chapter discusses the following areas that you must consider before you can design a security policy for the corporate networking environment:
Defining the physical security controls
Defining the logical security controls
Ensuring system and data integrity
Ensuring data confidentiality
Defining mechanisms to verify and monitor security controls
Developing policies and procedures for the staff that is responsible for the corporate network
Developing appropriate security awareness training for users of the corporate network
Some implementation details are given as examples of how to carry out part of the policy. Most of the implementation details are found in Chapter 9, “Securing the Corporate Network Infrastructure,” Chapter 10, “Securing Internet Access,” and Chapter 11, “Securing Remote Dial-in Access,” which detail specific features and considerations.
NOTE
Incidence response handling is also part of the planning and implementation phase, but, because of its importance and breadth, it is detailed separately in Chapter 8, “Incident Handling.”
Physical security controls are those controls pertaining to the physical infrastructure, physical device security, and physical access. Do you expect intruders to tap into your infrastructure to eavesdrop on transmitting data? How easy or difficult is it for intruders to gain physical access to the important network infrastructure devices? If the corporate network has not yet been created at an existing site, you should consider the physical security controls available in its planning phase.
For existing networks, if a security policy is being created or modified to accommodate changing environments, it might be necessary to change the physical infrastructure or the locations of some critical pieces of equipment to ensure an easier security policy implementation. After you have incorporated the physical security controls into the policy, as the corporation grows and new sites are added, you should consider the network physical security controls as the site is constructed.
The physical network infrastructure encompasses both the selection of the appropriate media type and the path of the physical cabling (the network topography). You want to ensure that no intruder is able to eavesdrop on the data traversing the network and that all critical systems have a high degree of availability. For wireless networks, it is clear that eavesdropping must always be a consideration because anyone with a wireless networking card has potential access to any existing wireless network. Wireless networks require specific security considerations, which are described in subsequent appropriate sections.
From a security point of view, the type of cable chosen for various parts of the network can depend on the sensitivity of the information traveling over that cable. The three most common cable types used in networking infrastructures are twisted pair, coax, and optical fiber. Optical fiber is most often used in high-bandwidth and long-haul environments. Unlike either twisted pair or coax, optical fiber does not radiate any energy and, therefore, provides a very high degree of security against eavesdropping. Optical fiber is also much more difficult to tap into than either twisted pair or coax cable.
Wiretaps can sometimes be detected by using tools to measure physical attenuation of cable. Typically, a time domain reflectometer (TDR) tool is used to check coax cable, and an optical time domain reflectometer (OTDR) tool is used for optical fiber cable. These devices are used mainly to measure signal attenuation and the length of an installed cable base; sometimes, however, they can also detect illegal wiretaps.
Let's take a look at how you can detect taps in fiber-optic cable using an OTDR. One of the things an eavesdropper needs when tapping into an optical cable is an optical splitter. The insertion of an optical splitter into an optical cable allows the tap to be made, but it also affects the signal level in the media. This level can be measured. If a benchmark optical signal level is observed at several points along the topology of an optical media network, any conventional optical tap inserted into the network should be observable. Figure 7-1 shows an initial OTDR fiber-optic cable trace between two buildings.
Figure 7-2 shows the fiber-optic trace taken after an optical splitter was inserted into the length of the fiber cable.
Although these types of traces can be an indication that an illegal tap might be in place, they are most useful in detecting cable degradation problems.
NOTE
An expert can insert a tap in a way that isn't easily detectable by a TDR or OTDR. However, it is good practice to initially take a baseline signal level of the physical cable infrastructure and periodically verify the integrity of the physical cable plant. Even if it doesn't detect unauthorized media taps, the measurement will provide you with some confidence in the integrity of the cable infrastructure.
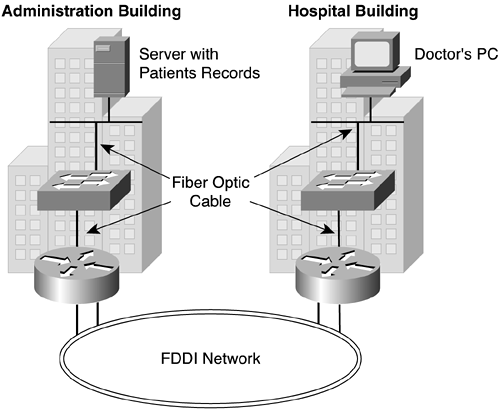
When choosing the transmission media to install for various segments of the network infrastructure, it is important to ensure that eavesdropping on the physical wire is proportionally more difficult as the data on that wire becomes more sensitive. In addition, if it is important that the transmission media be secure, the entire data path must be secure. (See Figure 7-3.)
Figure 7-3 shows a large medical facility with two buildings connected by an FDDI ring. Because the server holding the patient records is located in the administrative building, and the doctor retrieving the information is located in the hospital building, both the backbone segment and the LAN segments of the network use optical fiber. It is very difficult for someone to gain access to patient information by tapping into optical fiber.
NOTE
Although it is useful to keep the possibility of tapping in mind, in today's typical corporate network, there is very little need to use an “unauthorized” tap. Why bother with all the cloak-and-dagger stuff when there are all these PCs and workstations already attached to the network? All the thief has to do is run a program on any authorized workstation/PC to put its network controller into promiscuous mode; then the thief can “sniff” the network at his or her leisure.
Several shareware programs can do this now; they are available for Windows, Linux, Solaris, and others. There is no need for a thief to set up an actual sniffer on the network anymore. Because there is no way to prevent anyone from running such a program on a Macintosh or a PC running Windows 98/2000/XP, there isn't much point in actually worrying about restricting the ability to sniff. Even a policy stating that anyone caught sniffing the corporate network will be fired probably won't be very helpful because this is very hard to detect, although having the policy is still a good idea because it reinforces to the users that this is unacceptable behavior.
The issue therefore is reversed: The question you ask now is, “How do we prevent people who are sniffing the network from reading the contents of the packets they've sniffed?” The answer is obviously some form of encryption.
The physical path of the media, also known as the network topography, is a concern for the availability of the network and its attached devices. It touches on the reliability and security of the infrastructure. It is important to have a structured cabling system that minimizes the risk of downtime.
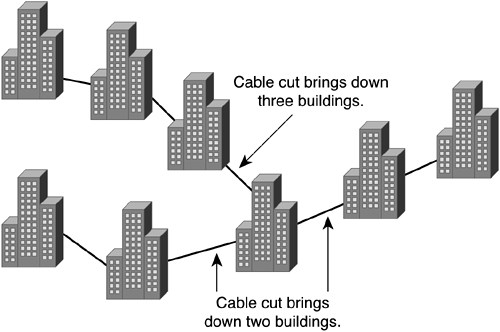
Imagine a large campus environment with multiple buildings. If the topography of the backbone network infrastructure is not a true starred network with common conduits at the base of the star, a construction worker with a backhoe could bring down large portions of the network. (See Figure 7-4.) If alternative physical paths are made available (that is, if you create a true starred network), however, only small portions of the network might become inaccessible if the physical cable fails. (See Figure 7-5.)
The cable infrastructure should also be well secured to prevent access to any part of it. If cables installed between buildings are buried underground, they must be buried a minimum of 40 inches, although local regulations might dictate other guidelines. Sometimes, cables can be encased in concrete to provide maximum protection. The International Telecommunication Union has a number of recommendations (the Series L Recommendations) that cover the construction, installation, and protection of cable plants. You can access these guidelines at http://online.vsi.ru/library/ITU-T/.
Physical device security is sometimes understated. Intruders with enough incentive will think of anything to get at what they want. Physical device security includes identifying the location of the devices, limiting physical access, and having appropriate environmental safeguards in place.
The location of critical network resources is extremely important. All network infrastructure equipment should be physically located in restricted-access areas to eliminate the possibility of unauthorized access by physical proximity. Facility issues can be a horrific nightmare, but when it comes to creating space for wiring closets that house critical infrastructure equipment, such as switches, firewalls, modems, and routers, it is imperative that you fight for whatever autonomous space there is. Don't overlook any aspect of the physical facility. Having a secure lock on a wiring closet does not provide much protection if you can go through the ceiling panels to get into the room.
The infrastructure equipment includes more than just the networks and the routers, firewalls, switches, and network access servers that interconnect the networks. Infrastructure equipment also includes the servers that provide the various network services:
Network management (SNMP)
Domain Name Service (DNS)
Network Time (NTP)
Network File System (NFS)
Hypertext Transfer Protocol (HTTP)
User authentication and authorization (TACACS+, RADIUS, Kerberos)
Network audit and intrusion detection
Multimedia conferencing server (NetMeeting)
Voice over IP gateway
Most of these servers can be segmented into a common area to provide easier access control measures. However, you must also be sure that adequate redundancy needs are met to ensure the availability of these critical services, especially when a single LAN may get segmented from the rest of the network.
NOTE
Whenever possible, incorporate security controls for cases in which physical access might be compromised. Protect console access using authentication mechanisms, for example, and use screen savers with authentication mechanisms for critical servers.
Here is another area of concern that is sometimes overlooked. When printing confidential configuration files or faxing configurations, there is the possibility that the printouts from printers or fax machines might fall into the wrong hands. You might want to make it a requirement to put all sensitive printers and fax machines on a LAN segment that is physically located in a room with controlled access. Also, you must have a way to dispose of the printouts and documents securely. Shredding is not out of the question.
Who has access to the wiring closets and restricted locations? The physical access requirements of controlled areas are determined largely by the results of the risk analysis or a physical security survey. It is good practice to restrict physical access to wiring closets and locations of critical network infrastructure equipment. Access to these areas should not be permitted unless the person is specifically authorized or requires access to perform his or her job.
Wireless access servers require special consideration because the nature of the technology requires that they be deployed in open spaces. A possible solution could be to put wireless access servers under video surveillance to deter physical tampering.
NOTE
Not all physical security tampering is malicious, but it can have the same effect of causing network resources to be unavailable. The following incident is a true story and although it might represent a rare occurrence, it is nevertheless something to keep in mind. After countless hours of troubleshooting an unavailable network connection, analyzing all potential switch and routing problems, the equipment closet was inspected. It turned out that the cable connecting the LAN to the router had been disconnected. A maintenance worker had been working in another part of the closet, found the wire to be in the way, and disconnected it. When his work was finished, he forgot to reconnect it. Needless to say, this incident caused any subsequent maintenance work to be more closely supervised.
Part of the physical security policy should be to have contract maintenance personnel or others who are not authorized with unrestricted access, but who are required to be in the controlled area, to be escorted by an authorized person or to sign in before accessing the controlled area.
To ensure an enforceable physical security policy, it is essential to ensure that people's work areas mesh well with access restrictions. If these conditions are not met, well-meaning employees will find ways to circumvent your physical security. (For example, they will jam doors open rather than lock and unlock them 15 times per hour.)
If your facility is providing temporary network access for visitors to connect back to their home networks (for example, to read e-mail), plan the service carefully. Define precisely where you will provide it so that you can ensure the necessary physical access security. A typical example is at large industry meetings; if these meetings are hosted at a corporate facility, the host corporation usually has a separate network solely for guest privileges. This network should reside in a single area and access should be given only to conference attendees.
Adequate environmental safeguards must be installed and implemented to protect critical networked resources. The sensitivity or criticality of the system determines whether security is “adequate.” The more critical a system, the more safeguards must be put in place to ensure that the resource is available at all costs. At a minimum, consider the following environmental safeguards:
The last item might seem a little extreme, but anyone who has worked with fiber-optic equipment knows that is has been prone to network degradation and downtime caused by dust particles and will recognize the usefulness of this seemingly inane point.
The following is a sample physical security control policy.
Construction and Location of Premises:
All university buildings must have network closets built in accordance with relevant fire and safety standards.
All network closets must be protected from potential sources of man-made or natural hazards, such as floods, earthquakes, and lightning.
Maintenance of Equipment:
All network infrastructure equipment must be connected to backup power supplies.
All network infrastructure equipment must be in locked cabinets with keys that only maintenance staff can access.
Physical Access:
Access to network closets and equipment racks is authorized only for people in the network infrastructure operations group.
Other personnel may access network closets only in the company of a member of the network infrastructure operations group.
Surveillance cameras must be installed in all network closets.
In the event of personnel changes, the locks to the network closets must be changed.
Logical security controls create boundaries between network segments. As such, they control the flow of traffic between different cable segments. When traffic is logically filtered between networks, logical access controls provide security.
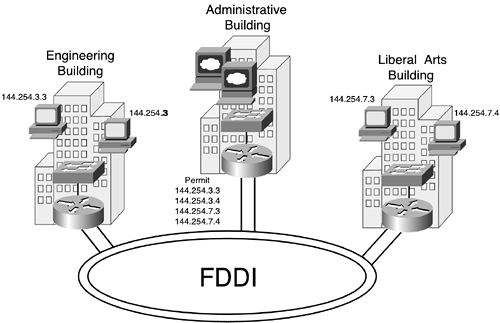
The example in Figure 7-6 shows three university buildings each connected by a router. The administration building has a LAN that allows only specific IP addresses from the engineering building (144.254.3.3 and 144.254.3.4) and the liberal arts building (144.254.7.3 and 144.254.7.4) to access the LAN. These addresses are permitted access because they are known to belong to hosts in the faculty room, to which only faculty members have access.
NOTE
Although traffic filtering provides some measure of security, it is easy to spoof IP addresses. Filtering should be used in conjunction with other security measures.
Because logical boundaries are not as secure as physical boundaries, you must fully understand the path the data is taking from one point to another. Although logical boundaries usually exist between separate subnets, routing policies and virtual local-area networks (VLANs) can obfuscate the logical traffic flow.
TIP
The only way to detect unauthorized traffic on the network is through the use of a packet analyzer or an intrusion detection system. It is prudent to place intrusion detection systems at critical network access points.
A characterization is sometimes made that traffic on different subnets is secure because the traffic is constrained to a single subnet domain. The thinking is that there is a logical separation between different groups of addresses that make up the different network access domains. You can provide filters to permit or deny traffic based on subnet addresses. As pointed out in the preceding section, however, IP addresses are easy to spoof; other security measures should always be used in conjunction with filtering mechanisms. (Readers not familiar with IP addressing and subnetting can refer to the following sidebar.)
Because subnets are under local administration, the outside world sees an organization as a single network and has no detailed knowledge of the organization's internal structure. However, internally, each subnet constitutes a separate LAN, possibly on a separate physical cable segment. (See Figure 7-9.)
The logical infrastructure of any network depends largely on how networks are logically separated into groups using subnets and how traffic is controlled between these subnets. Routing (also known as Layer 3 switching) is how traffic is controlled between subnets. Where routing information is distributed and accepted plays a large role in how you gain access to data on various networks. VLANs can also modify traditional subnet physical boundaries.
Routing involves two basic activities:
Determining optimal routing paths
Transporting packets through an internetwork
The latter activity is typically referred to as Layer 3 switching. Switching is relatively straightforward: It involves looking up the destination address in a table that specifies where to send the packet. The table is created as a result of determining the optimal path to a given destination. If the table entry for a given destination is not there, the optimal path must be computed. The computation of the optimal path depends on the routing protocol used and can be a very complex process.
NOTE
Routing fundamentals are beyond the scope of this book. Read Internet Routing Architectures, Second Edition (Cisco Press, 2000) for a more detailed discussion on routing.
A security policy can incorporate detailed routing policies, where routes for separate networks and subnets are announced and accepted on an as-needed basis. Most routers, regardless of the routing protocol used, have features that suppress the announcement of specified routes and can ignore certain received routes and not incorporate them into their tables. Usually, there are many ways to accomplish the same goal. It is best to first design the logical boundaries, decide how open or closed an environment you want, and then implement the policy accordingly.
Filtering routes is one way of exerting some control over who can source traffic and to what destination. Filtering does not protect you from spoofing attacks, but it can make spoofing attacks harder to carry out.
Figure 7-10 shows a common scenario of creating logical routing boundaries.
In this scenario, the corporate network is divided into three distinct components:
The campus network has a Class B address of 144.254.0.0, which is subnetted into 256 distinct networks using an 8-bit subnet mask of 255.255.255.0. The Internet access is provided by an unnumbered interface. An unnumbered interface refers to a point-to-point connection that is configured without using an IP address. The remote access for a branch office is provided by a subnetted Class C address of 192.150.42.0 with a 5-bit subnet mask of 255.255.255.248. This branch office is mainly used for taking orders via the web and carrying out the corporation's financial transactions. The web servers used to collect the order information are all located on the 192.150.42.32 network. The corporation's routing policy allows free access to all corporate campus servers but allows only the branch office web server network, 192.150.42.32, to access the Internet through the campus network. The policy can be implemented as follows:
Allow all 144.254.0.0 routes to be announced everywhere.
Announce all 192.150.42.0 networks to the main campus.
Announce the 192.150.42.32 network to the Internet.
Suppress all other 192.150.42.0 network announcements.
Static routing protocols offer the ultimate control of routes. However, the management of static routes in environments that exceed 10 or more entries can become an administrative nightmare. A dynamic routing protocol is much more flexible and can offer similar control for larger environments.
In some remote access scenarios, it may also be useful to further subdivide wireless network access, VPN network access, and dial-in access into separate subnets. If you have different authentication and access control policies for these remote access networks, these policies are easier to control and enforce using separate subnets.
NOTE
Routing can be a very complex subject; it is strongly recommended that you fully understand the routing protocols used in a given corporate environment and draw out the logical infrastructure before implementing any filtering commands. Where possible, use a modeling tool as a sanity check to verify the assumed logical path of network traffic.
A VLAN is a group of hosts or network devices—such as routers (running transparent bridging) and bridges—that form a single bridging domain. Layer 2 bridging protocols, such as IEEE 802.10 and Inter-Switch Link (ISL), allow a VLAN to exist across a variety of equipment, such as LAN switches.
VLANs are formed to group related users regardless of the physical locations of their hosts to the network. The users can be spread across a campus network or even across geographically dispersed locations. A variety of strategies can be used to group users. For example, the users can be grouped according to their department or functional team. In general, the goal is to group users into VLANs so that most of the user traffic stays within the VLAN. If you do not include a router in a VLAN, no users outside that VLAN can communicate with the users in the VLAN and vice versa.
Typically, although not necessarily, a VLAN corresponds to a particular subnet. Because a VLAN enables you to group end stations even if they are not located physically on the same LAN segment, you must ensure that the VLAN boundaries are properly understood and configured.
NOTE
Avoid using VLANs as the sole method of securing access between two subnets. The possibility for human error, combined with the understanding that VLANs and VLAN tagging protocols were not designed with security in mind, makes their use in sensitive environments inadvisable.
Within an existing VLAN, private VLANs provide some added security to specific network applications. Private VLANs work by limiting which ports within a VLAN can communicate with other ports in the same VLAN. Isolated ports within a VLAN can communicate only with promiscuous ports. Community ports can communicate only with other members of the same community and promiscuous ports. Promiscuous ports can communicate with any port. This is an effective way to mitigate the effects of a single compromised host.
Access to equipment and network segments should be restricted to individuals who require access. Two types of controls should be implemented:
Preventative controls, which are designed to uniquely identify every authorized user and to deny access to unauthorized users
Detective controls, which are designed to log and report the activities of authorized users and to log and report unauthorized access or attempted access to systems, programs, and data
Providing a policy for administrative access to the network devices depends directly on the size of the network and the number of administrators required to maintain it. Local authentication on the network infrastructure device can be performed, but may not be scalable. The use of network management tools can help in large networks; if local authentication is used on each device, however, the policy usually consists of a single login, which does not promote adequate device security. In these cases, an access control server should be considered, which allows for a centralized administrator database, and administrators can be added or deleted at one location.
The type of access is also an important consideration. It is usually prudent to consider using different administrative access levels to the network infrastructure device such that specific commands have specific privilege levels and that these privilege levels are defined for individual user logins.
The three most common types of users are as follows:
Administrators—. All levels of access privileges
Privileged—. Troubleshooting access privileges
Staff—. General monitoring access privileges
The correct technical solution is one that will be followed and not circumvented. You must strive to strike a balance between what authentication methods users will actually use and the methods that provide adequate security for a given system.
When providing access control, it never works to have a different password for every router, switch, firewall, and other network device. Probably the easiest approach is to use one password for console access and another for logical Telnet or Secure Shell (SSH) access to the devices. These passwords should be changed on a monthly basis (or whatever timetable is comfortable). The passwords should definitely change when a person leaves the group.
Better access control can be achieved by avoiding common group passwords and instead, having passwords per individual user needing access to a given device. Using a AAA protocol such as RADIUS or TACACS+, per-user authentication, authorization, and accounting can be achieved in a scalable manner. This is extremely important as networks become larger, because individual password management of network devices only scales in small installations. As the number of routers, switches, and so on grows, it may be time to consider using a specific set of hosts as jumphosts to access the network devices. An administrator would be required to strongly authenticate to the jumphost and then from the jumphost leverage an authentication service to access network devices. The authentication service can be accomplished using RADIUS, TACACS+, or Kerberos where there typically exists machine-level trust to the network elements.
Some organizations still base their authentication mechanisms on standard, reusable passwords. Any reusable password is subject to eavesdropping attacks from sniffer programs. It is recommended that, if possible, these environments change to a more robust authentication scheme, such as any of the one-time passwords described in Chapter 2, “Security Technologies.” If this is not possible, however, here are some recommendations for using traditional passwords:
Choose passwords that cannot be guessed easily. Many automated password-cracking programs use a very large dictionary and can crack passwords in a matter of seconds. Passwords should also be as long as the system supports and as users can tolerate.
Change default passwords immediately when you install new network infrastructure equipment. Don't forget to change the passwords for console access and passwords used for maintenance purposes. For any product you buy, find out from the manufacturer whether there are ways to recover passwords and whether there are any ways to access configurations using these passwords (usually through undocumented means).
Restrict access to the password when possible. Many vendors now have features that encrypt the password portion of configuration files. Use these features whenever they are available.
Provide guidelines for how often users should change their password. It is recommended that passwords be changed at least whenever a privileged account is compromised or when there is a critical change in personnel.
NOTE
Many authentication mechanisms have automated password protocol enforcement. For instance, an initial password is marked as expired in the account record, either forcing the user to change the password when he or she logs in, or disabling the account if the user doesn't change the password. Users can be forced to change their passwords at regular intervals. If your authentication mechanism has these provisions (many TACACS+ and RADIUS implementations do), use them.
Many systems offer the capability to configure a greeting or banner message when accessing the system. Never include location information or the type of system in greeting or login banner messages. The system announcement messages must not welcome the user or identify the company, neither must it identify the equipment vendor or the type of operating system in use. Savvy intruders can easily reference databases of vendor or system hacks and bugs that they then can exploit. Make intruders work to get into the system before they learn what type of system it is; this gives you an additional chance to detect them breaking in. In addition, governments are creating legislature requiring specific language to aid in prosecution of any network infiltrators. It is always best to discuss the use and language of a banner message with your corporate legal department to ensure that the message is appropriate for your environment.
Example 7-1 shows a sample of a good banner message.
Example 7-1. Sample Banner Message
**WARNING**WARNING**WARNING**WARNING**WARNING** YOU HAVE ACCESSED A RESTRICTED DEVICE. USE OF THIS DEVICE WITHOUT AUTHORIZATION OR FOR PURPOSES FOR WHICH AUTHORIZATION HAS NOT BEEN EXTENDED IS PROHIBITED. LOG OFF IMMEDIATELY. VIOLATORS WILL BE PROSECUTED TO THE FULL EXTENT OF THE LAW. **WARNING**WARNING**WARNING**WARNING**WARNING**
The following is an example of a logical security control policy for a university.
Logical Network Layout:
All connections to which students have easy access (student housing, classrooms, labs, and libraries) will be on VLANs.
The VLANs a student can access will be determined by the curriculum in which the student is enrolled.
The faculty rooms in each building will be connected to subnets specified solely for faculty use.
The administration building will be on its own subnet.
All infrastructure devices and critical services will be on their own subnets.
Access to Networks:
All VLAN traffic will be cross-routed to each other so that all students have access to all classroom, housing, and lab computing facilities.
Only faculty members will be allowed access to the faculty subnets.
Only faculty and administrative personnel will be allowed access to the administration building LAN.
Access to Infrastructure Devices:
Telnet, SSH, and modem access to network infrastructure equipment is allowed only for network infrastructure operations personnel. (This equipment includes routers, firewalls, switches, remote access servers, and critical application servers.)
SSH will be the primary mechanism to access network infrastructure equipment. Telnet will only be allowed if it is used from a specified set of hosts.
All infrastructure device access will be based on one-time password authentication technology.
All infrastructure devices will have a generic login prompt with no information pertaining to system type or vendor name.
All activity on infrastructure devices will be logged (such as configuration changes or new image loading).
On the network infrastructure, you want to ensure as best you can that any traffic on the network is valid traffic. Valid traffic can be categorized as expected network traffic, such as the following:
Supported services
Unspoofed traffic
Data that has not been altered
Firewalls control the flow of traffic between networks and are often used to control the flow of supported network services. Authenticating data in the network infrastructure gives reasonable security against altered packets. Putting safeguards in place to deploy methods to deter attacks might help deter spoofed traffic.
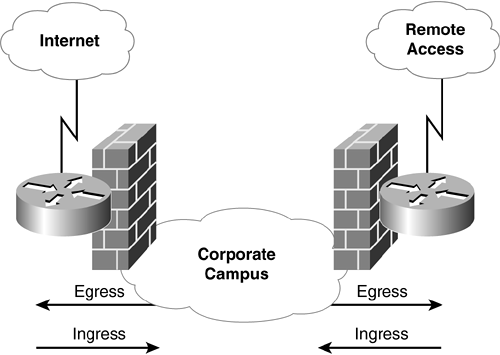
A common way to ensure infrastructure integrity is with firewalls. A firewall, in its most simplistic sense, controls the flow of traffic. Rules are created to permit or deny various types of traffic and parallel any routing decisions made. The permission or denial of traffic can include specific network services. Many books have been written on firewalls and firewall design; some are referenced at the end of this chapter. Typically, firewalls are deployed at critical ingress and egress points of the network infrastructure, as shown in Figure 7-11.
Currently, there are three classifications of firewalls that encompass different filtering characteristics:
Packet filtering—. These firewalls rely solely on the TCP, UDP, ICMP, and IP headers of individual packets to permit or deny traffic. The packet filter looks at a combination of traffic direction (inbound or outbound), IP source and destination address, and TCP or UDP source and destination port numbers.
Circuit filtering—. These firewalls control access by keeping state information and reconstructing the flow of data associated with the traffic. A circuit filter won't pass a packet from one side to the other unless it is part of an established connection.
Application gateway—. These firewalls process messages specific to particular IP applications. These gateways are tailored to specific protocols and cannot easily protect traffic using newer protocols.
Before determining which classifications best fit your environment, examine the traffic flow control you can exert in your environment. Most of the control is based on a combination of the following characteristics:
Traffic can be filtered in either the inbound or outbound direction. Generally, inbound traffic comes from an outside untrusted source to the inside trusted network. Outbound traffic comes from inside the trusted network to an outside untrusted network. (See Figure 7-12.)
Whether traffic was initiated from the inside (trusted) network or the outside (untrusted) can be a factor in managing traffic flow. For example, you might want to allow certain UDP packets to originate from inside the trusted network (DNS), but might not allow DNS requests to come in from the outside untrusted network. Alternatively, you might want to restrict TCP traffic to outside untrusted networks if the TCP session was initiated from the inside trusted network.
The source or destination address can be used to filter certain traffic. This approach is useful for implementing precursory controls to help avoid spoofing attacks. Specifically, inbound filters should be configured that block source addresses that should be internal and to block destinations that are not internal.
TCP and UDP source and destination port numbers are used to recognize and filter different types of services. Which services you support is a key question and is discussed in more detail in the “Network Services” section later in this chapter.
At all ingress points to trusted networks, you should authenticate users before they can access particular services, such as Telnet, FTP, or HTTP. Available authentication mechanisms vary, but they all aid in controlling use and auditing who is accessing which services. As an aside, authentication can also help service providers with billing and accounting information.
Choosing which services and protocols you support can be a daunting task. An easy approach is to permit all and deny as needed. This policy is easy to implement because all you have to do is turn on all services and allow all protocols to travel across network boundaries. As security holes become apparent, you restrict or patch those services at either the host or network level.
This approach is fairly simple, but it is also vulnerable to a multitude of attacks and not recommended. A more secure approach is to deny all and permit as needed. With this method, you turn off all services and selectively enable services on a case-by-case basis as they are needed. The deny-all model is generally more secure than the permit-all model, but it requires more work to successfully implement. It also requires a better understanding of the services. If you allow only known services, you provide for a better analysis of a particular service or protocol and you can design a security mechanism suited to the security level of the site.
NOTE
Security complexity can grow exponentially with the number of services provided. Evaluate all new services with a skeptical attitude to determine whether they are actually needed.
It is beyond the scope of this book to provide a detailed list of all the network services available. However, the books recommended in Appendix A, “Sources of Technical Information,” provide you with all the detail necessary to choose the services appropriate for your specific environment. To summarize, the services most commonly required in environments include SNMP, DNS, NTP, WWW, Telnet, FTP, NNTP, and SMTP. Additionally, a good way to understand what traffic exists (and thus what filters need to be defined) is just to snoop the network for traffic. A table can be constructed of common data flows based on these observations. That table can then be verified with the users of the resources being accessed to determine legitimacy of the data.
It can be a daunting task to figure out which services to filter. At a minimum, you should follow the CERT recommendations, which strongly suggest that you filter the services listed in Table 7-1. The Computer Emergency Response Team (CERT) from Carnegie Mellon University collects reports of computer crime, provides this information to vendors, and distributes information from vendors regarding vulnerabilities of their systems.
Table 7-1. CERT-Recommended Services to Filter
Protocol | Port Number | Description |
|---|---|---|
TCP | 53 | DNS Zone Transfer |
UDP | 69 | Tftpd |
TCP | 87 | Link (commonly used by intruders) |
TCP | 111 | SunRPC |
UDP | 111 | SunRPC |
TCP | 2049 | NFS |
UDP | 2049 | NFS |
TCP | 512 | BSD UNIX R-command |
TCP | 513 | BSD UNIX R-command |
TCP | 514 | BSD UNIX R-command |
TCP | 515 | lpd |
TCP | 540 | uucpd |
TCP | 2000 | OpenWindows |
UDP | 2000 | OpenWindows |
TCP | 6000+ | X Windows |
UDP | 6000+ | X Windows |
The services a site provides will, in most cases, have different levels of access needs and models of trust. Services essential to the security or smooth operation of a site are better off on a dedicated machine with very limited access.
Services provided on the same machine can interact in catastrophic ways. For example, allowing anonymous FTP on the same machine as the World Wide Web server might permit an intruder to place a file in the anonymous FTP area and cause the HTTP server to execute it. If possible, each service should run on a different machine. This arrangement helps isolate intruders and limit potential harm.
To ensure a reasonable amount of data integrity, you should authenticate most traffic traversing the network. For network infrastructure integrity, traffic specific to the operation of a secure infrastructure (such as routing updates) should also be authenticated.
If you do not authenticate routing updates, unauthorized or deliberately malicious routing updates can compromise the security of your network traffic. A security compromise can occur if an unfriendly party diverts or analyzes your network traffic. For example, an unauthorized router could send a fictitious routing update to convince your router to send traffic to an incorrect destination. This diverted traffic could be analyzed to learn confidential information about your organization, or merely to disrupt your organization's ability to effectively communicate using the network.
NOTE
The need to authenticate network traffic also applies to bridging spanning-tree and VLAN protocols. If you can spoof a routing update or bridge topology change, you can black-hole various portions of the network, causing denial-of-service (DoS) attacks that can be very, very difficult to detect because routing protocols don't keep much information about the device that sent them a routing packet. Bridges and switches keep even less information.
Checksums protect against the injection of spurious packets, even if the intruder has direct access to the physical network. Combined with a sequence number or other unique identifier, a checksum can also protect against replay attacks, wherein an old (but once valid) routing update is retransmitted by either an intruder or a misbehaving router. The most security is provided by complete encryption of sequenced, or uniquely identified, routing updates. This approach prevents an intruder from determining the topology of the network. The disadvantage to encryption is the overhead involved in processing the updates.
Most common networking attacks can be made more difficult with firewall-type products.
In many cases, attacks against random hosts behind the firewall can be completely prevented, depending on how you've configured the firewall. The most conservative configuration allows no traffic at all to reach internal hosts unless those hosts initiate an outgoing connection of some kind. If you're set up this way, a number of attacks can be deterred.
Web servers, mail servers, FTP servers, and so on behind the firewall are at the most risk because any host on the network can send at least some kinds of packets to them at any time. You are generally better off putting those exposed services on a demilitarized zone (DMZ) network, rather than on your internal network. You must also make sure that application server itself is protected. Firewalls do some things to protect exposed services, but that's still where the biggest risks lie.
If internal client hosts have formed outgoing connections, they are exposing themselves to some return traffic. In general, attacks against internal clients can be conducted only by the server to which the client has connected—which includes someone impersonating that server using IP spoofing. To impersonate the server, the attacker obviously has to know which server the client has connected to.
For any given attack, protection is generally complete for hosts that aren't actively talking to the net, partial for hosts that are actively talking to the net, and minimal for exposed services. However, security depends on how the system is configured.
No product, even if properly configured, can protect you completely against outside hosts assuming the addresses of your inside hosts. There is no way a firewall, or any other device, can determine whether the source address given in an unauthenticated IP packet is valid—other than to look at the interface on which that packet arrived. Therefore, no firewall can protect against the general case of one outside host spoofing another. If something has to rely on the address of an outside host, you must have control over the entire network path to that host, not just a single access point.
Any internetworking product can make spoofing attacks more difficult by making it harder for the attacker to guess which nodes it's profitable to spoof at any given moment. This protection is not complete; an attacker who can sniff the network at strategic points, or who can make good guesses based on knowledge of the traffic patterns, can get around the internetworking product.
The following is an example of the infrastructure and data integrity section of a sample university security policy.
Infrastructure Security:
Access to switch LAN ports and router interfaces will be disabled when not in use.
Firewall functionality will be used at egress points; egress points are defined as any connections that provide access anywhere outside the main university campus.
Only necessary network services will be supported. These services will be defined by the network operations steering group.
The infrastructure will be addressed from a well-defined block of IP addresses so that the edge filters at egress points may block inbound traffic to the infrastructure.
Data Integrity:
Software not related to work will not be used on any computer that is part of the network infrastructure and critical services.
All software images and operating systems should use a checksum verification scheme before installation to confirm their integrity.
All routing updates and VLAN updates must be authenticated between sending and receiving devices.
Data confidentiality pertains to encryption. The hardest aspect of this endeavor is deciding which data to encrypt and which to keep as cleartext. This decision should be made using the risk assessment procedure, in which data is classified according to various sensitivity levels. It is usually prudent to take a careful look at your data and to encrypt the data that would pose the greatest risk if it should ever be compromised.
The following is an example of the data confidentiality section of a university security policy.
Data Confidentiality:
All information regarding student grades and transcripts must be encrypted when transmitted across the network.
All information regarding student financial information must be encrypted when transmitted across the network.
All employee salary and benefits information must be encrypted when transmitted across the network.
To ensure that a security policy is being adhered to, proper controls need to be put in place to verify and monitor authentication, access controls, and the data traversing your network. Mainly this requires the use of vulnerability scanners, accounting procedures, secure management, and intrusion detection controls.
Vulnerability scanners provide mechanism to both check and validate system-level security controls. It is prudent to audit the network infrastructure on a recurring basis to ensure that the security policy is being enforced appropriately and that no irregularities have developed as the network has evolved. The following are some of the capabilities needed for a useful vulnerability scanner to help users stay appraised of their network security status:
Network mapping—. Compiles an electronic inventory of the systems and the services on your network
Security vulnerability assessment—. Identifies security holes by probing for and confirming vulnerabilities
Risk management—. Enables effective management of vulnerability data through innovative data browsing technology
Decision support—. Communicates results through comprehensive reports and charts and enables you to effective decisions to improve the organization's security posture
Security policies validation—. Defines and enforces valid security policies when used during security device installation and certification
Accounting provides the method for collecting and sending security server information used for billing, auditing, and reporting, such as user identities, start and stop times, executed commands (such as PPP), number of packets, and number of bytes. Accounting enables you to track the services users are accessing and the amount of network resources they are consuming.
Logging and reading accounting information from the numerous network infrastructure devices can prove to be a challenging proposition. Which accounting logs are most important? How do you separate important messages from mere notifications? How do you ensure that logs are not tampered with in transit? How do you ensure your time stamps match each other when multiple devices report the same event? What information is needed if log data is required for a criminal investigation? How do you deal with the volume of messages that can be generated by a large network? You must address all these questions when considering managing accounting files effectively.
From a device-management standpoint, a different set of questions needs to be asked: How do you securely manage a device? How can you track changes on devices to troubleshoot when attacks or network failures occur?
Many larger networks opt for an out-of-band (OOB) management system, which refers to a network on which no production traffic resides. Devices would have a direct local connection to the OOB network where possible. If geographic or system-related issues make such an OOB connection impossible, the device should connect in-band via a private encrypted tunnel over the production network. The private encrypted tunnel should be preconfigured to communicate only across the specific ports required for management and reporting and should only allow specific hosts to initiate and terminate tunnels.
An OOB management network can make dealing with logging and reporting much more straightforward. Most networking devices can send syslog data, which can be invaluable when troubleshooting network problems or security threats. Depending on the device involved, various logging levels can be chosen to ensure that the correct type and amount of data is sent to the logging devices. For many attacks, it is important to identify the order in which specific events occurred. Therefore, it is critical that clocks on hosts and network devices are in sync so that all log messages are time synchronized to one another. For devices that support it, Network Time Protocol (NTP) provides a way to ensure that accurate time is kept on all devices.
OOB management is not always the best solution and largely depends on the type of management application you are running and the protocols that are required. If you are using a management tool that periodically determines the reachability of all devices on the network, for example, an OOB management system may not detect a critical failure between core devices because all devices appear to be attached to a single network. With these types of management applications, in-band management through an encrypted private tunnel is preferred.
When deploying in-band management of a device, you should consider several factors. First, what security and/or management protocols does the device support? If IP Security (IPsec) is supported, devices can be managed by creating IPsec tunnels from the management network to the device and sending all the management traffic across this secure tunnel. When IPsec is not feasible because it is not supported on a device, you can use other alternatives such as SSH or Secure Socket Layer (SSL) to configure devices and access management data securely.
The use of SNMP should be carefully considered because the underlying protocol has its own set of security vulnerabilities. If required, consider providing read-only access to devices via SNMP and treat the SNMP community string with the same care you might treat a privileged (that is, enable or root) password on a critical router or UNIX host.
Configuration change management is another issue related to secure management. Sometimes routine checks on when the last configuration change occurred and what was modified can lead to detecting unwanted security vulnerabilities. In addition, when a network is under attack, it is important to know the state of critical network devices and when the last known modifications took place. This helps identify where compromises could have occurred and to later restore the network to its original state (of course fixing any newly discovered security vulnerabilities). Creating a plan for change management should be a part of any comprehensive security policy. At a minimum, configuration changes should be securely recorded and archived. Many devices support AAA functionality, which allows for RADIUS or TACACS+ to be used to authenticate, authorize, and keep accounting data for any configuration modifications.
An intrusion detection system (IDS) acts like an alarm system in the physical world. When an IDS detects something that it considers an attack, it can either take corrective action itself or notify a management system, which would alert a network administrator to take some action. A host-based IDS (HIDS) intercepts operating system and application calls on an individual host and can also operate by after-the-fact analysis of local log files. The former approach allows better attack prevention, whereas the latter approach dictates a more passive attack-response role. Because of the specificity of their role, a HIDS is often better at preventing specific attacks than a network IDS (NIDS), which usually issues an alert only upon discovery of an attack. However, that specificity causes a loss of perspective to the overall network.
When an IDS is deployed, you must tailor its implementation to your specific environment to increase its effectiveness and remove “false positives.” False positives are defined as alarms caused by legitimate traffic or activity. False negatives are attacks that the IDS fails to see. Many IDSs have the capability to learn the normal traffic patterns in a given environment and automate configuring the system to more specifically act in its threat-mitigation role. An effective strategy would be to use a combination of host and network IDSs. The NIDS would provide an overall perspective of your network and is useful for identifying distributed attacks, whereas the HIDS would stop most valid threats at the host level because it is well prepared to determine that certain activity is, indeed, a threat.
When deciding on automated attack-mitigation roles for a NIDS, you have two primary options:
Shun traffic through the use of access control filters on routers and firewalls.
Use TCP resets.
The first option—and potentially the most damaging if improperly deployed—is to shun traffic through the use of access control filters on routers and firewalls. When a NIDS detects an attack from a particular host over a particular protocol, it can block that host from coming into the network for a predetermined amount of time. Although on the surface this might seem like a great aid to a security administrator, in reality it must be very carefully implemented, if at all. The main problem is that of spoofed addresses. If traffic that matches an attack is seen by the NIDS, and that particular alarm triggers a shun situation, the NIDS will deploy an access list to the device to effectively lock out traffic from the troublesome address. If the attack that caused the alarm used a spoofed address, however, the NIDS has now locked out an address that never initiated an attack. If the spoofed IP address happens to be the IP address of a major ISP's outbound HTTP proxy server, a huge number of users could be locked out. This by itself could be an interesting DoS threat in the hands of a creative hacker.
To mitigate the risks of having a NIDS use automated filtering to shun traffic, you should generally use it only on TCP traffic, which is much more difficult to successfully spoof than UDP. Use it only in cases where the threat level is high and the chance that the attack is a false positive is very low. Also consider setting the shun length to a very short time interval. The automated filter should block the user long enough to allow the administrator to decide what permanent action (if any) he/she wants to take against that IP address.
The second option for automated attack mitigation using a NIDS is the use of TCP resets. As the name implies, TCP resets operate only on TCP traffic and terminate an active attack by sending TCP reset messages to the attacking and attacked host. Keep in mind that TCP resets in a switched environment are more challenging than when a standard hub is used, because all ports don't see all traffic without the use of a Switched Port Analyzer (SPAN) or mirror port. Make sure this mirror port supports bidirectional traffic flows and can have SPAN port MAC learning disabled.
IDSs are a critical piece of deploying secure network infrastructures. Understand the limitations of your system to effectively deploy and use it. Too often it becomes a device that loses its effectiveness due to improper setup, resulting in a flurry of false positives that are too hard to deal with. An IDS will not be effective in an asymmetric routing environment. Packets sent out from one set of routers and switches and returning through another will cause the IDS to see only half the traffic, causing false positives. Also, ensure that the performance capability of the NIDS is sufficient to meet the traffic requirements in your network.
The following is an example of the verification and monitoring section of a university security policy.
Security Policy Verification and Monitoring:
All Internet and remote-access activity must be logged. These logs are to include user identities, resources accessed, and the duration of the connection.
All activity logs must be stored in an encrypted fashion for at least 5 years.
All network infrastructure device access and configuration changes must be logged.
Network intrusion detection systems must be deployed at corporate network ingress points.
The network infrastructure must be audited every 6 months to ascertain adherence to the existing security policy.
The people responsible for maintaining and upgrading the network infrastructure should have specific guidelines to aid them in carrying out their tasks in accordance with the corporate security policies.
The procedure of creating backups is an integral part of running a computer environment. For the network infrastructure, backups of all network service servers, as well as backups of the configurations and images of networking infrastructure equipment, are critical. The following list should be included in your backup policy:
Ensure that your site is creating backups for all network infrastructure equipment configurations and software images.
Ensure that your site is creating backups for all servers that provide network services.
Ensure that your site is using offsite storage for backups. The storage site should be carefully selected for both its security and its availability.
Consider encrypting your backups to provide additional protection for when the information is offsite. However, be aware that you will need a good key management scheme so that you'll be able to recover data at any point in the future. Also, make sure that you will have access to the necessary decryption programs in the future when you might need to perform the decryption.
Don't always assume that your backups are good. There have been many instances of computer security incidents that have gone on for long periods of time before a site has noticed the incident. In such cases, backups of the affected systems are also tainted.
Periodically verify the correctness and completeness of your backups.
Keep original and backup copies of data and programs safe. Apart from keeping them in good condition for recovery purposes, you must protect the backups from theft. It is important to keep backups in a separate location from the originals, not only for damage considerations but also to guard against theft. Media used to record and store sensitive software or data should be externally identified, protected, controlled, and secured when not in actual use.
All new equipment to be added to the network infrastructure should adhere to specified security requirements. Each specific site must determine which security features and functionality are necessary to support its security policy. These features can be as simple as providing TACACS+ or RADIUS support and can progress to the more specific requirements of providing TACACS+ and RADIUS support with token-card authentication integration and time-of-day support.
Portable hosts pose some risk. Make sure that the theft of one of your staff's portable computers won't cause problems. Consider developing guidelines for the kinds of data allowed to reside on the hard disks of portable computers, as well as how the data should be protected (for example, whether encryption should be used) when it is on a portable computer.
Keeping logs of traffic patterns and noting any deviation from normal behavior can be your first clue to a security breach. Cliff Stoll relayed his experience in The Cuckoo's Egg, in which he helped catch some cyberspies by noting a 2-cent discrepancy in some accounting data.
The actual data you collect for your logs will differ for different sites and for different types of access changes within a site. In general, the information you want to collect includes the following:
Username
Host name
Source and destination IP address
Source and destination port numbers
Time stamp
Of course, you can gather much more information, depending on what the system makes available and how much space is available to store that information.
Depending on the importance of the data and the need to have it local in instances in which services are being denied, data could be kept local to the resource until needed or be transmitted to storage after each event. Consider how secure the path is between the device generating the log and the actual logging device (the file server, tape or CD-ROM drive, printer, and so on). If that path is compromised, logging can be stopped or spoofed or both.
In an ideal world, the logging device would be directly attached to the device generating the log by a single, simple, point-to-point cable. Because that is usually impractical, the data path should pass through the minimum number of networks and routers. Even if logs can be blocked, spoofing can be prevented with cryptographic checksums. (It probably isn't necessary to encrypt the logs because they should not contain sensitive information in the first place.)
The storage device should also be carefully selected. Consider write-once, read many (WORM) drives for storing audit data. With these drives, even if attackers can get to the data (with the exception of the physical media), they cannot change or destroy the data.
Because collecting audit data can result in a rapid accumulation of bytes, you must consider the availability of storage for this information in advance. By compressing data or keeping data for a short period of time, you can reduce the required storage space. It is useful to determine a time frame with which everyone is comfortable and for which you will keep detailed audit logs for incident response purposes.
Audit data should be some of the most carefully secured data at the site and in the backups. If an intruder were to gain access to audit logs, the systems themselves—in addition to the data—would be at risk. Audit data can also become the key to the investigation, apprehension, and prosecution of the perpetrator of an incident. For this reason, it is advisable to seek the advice of legal counsel when deciding how you will treat audit data. Get legal counsel before an incident occurs. If your data-handling plan is not adequately defined before an incident occurs, it might mean that there is no recourse in the aftermath of an event, and it might create a liability resulting from the improper treatment of the data.
Because of the nature of the content of audit data, a number of legal questions arise that you might want to bring to the attention of your legal counsel. These legal considerations often differ from country to country. If you collect and save audit data, be prepared for consequences resulting from both its existence and its content. One area of concern is the privacy of individuals. In certain instances, audit data might contain personal information. Searching through the data, even for a routine check of the system's security, might represent an invasion of privacy. If you collect sensitive data, you should probably encrypt the stored data.
A second area of concern involves your having knowledge of intrusive behavior originating from your site. If an organization keeps audit data, is it responsible for examining it to search for incidents? If a host in one organization is used as a launching point for an attack against another organization, can the second organization use the audit data of the first organization to prove negligence on the part of that organization?
The following is an example of the policies and procedures for the staff aspect of a university security policy.
Personnel Security Controls:
Key positions must be identified, and potential successors should always be identified.
Employee recruitment for positions in the implementation and operation of the network infrastructure must require a thorough background check.
All personnel involved with implementing and supporting the network infrastructure must attend a 2-day security seminar, which has been developed internally.
Equipment Acquisition and Maintenance:
All infrastructure equipment must pass the acquisition certification process before purchase.
All new images and configurations must be modeled in a test facility before deployment.
All major scheduled network outages and interruptions of services must be announced to those affected.
Backup Procedures:
All software images and configurations will be backed up in infrastructure devices when modified.
The previous image and configuration file will be kept until another change is made. Therefore, there should always be available the current and the previous image and configuration.
Users are typically not aware of security ramifications caused by certain actions. People who use computer networks as a tool to get their job done want to perform their job functions as efficiently as possible—and security measures often are more of a nuisance than a help. It is imperative for every corporation to provide employees with adequate training to educate them about the many problems and ramifications of security-related issues.
The security training should be provided to all personnel who design, implement, or maintain network systems. This training should include information regarding the types of security and internal control techniques that should be incorporated into the network system development, operations, and maintenance aspects.
Individuals assigned responsibilities for network security should be provided with in-depth training regarding the following issues:
Security techniques
Methodologies for evaluating threats and vulnerabilities
Selection criteria and implementation of controls
The importance of what is at risk if security is not maintained
For large corporate networks, it is good practice to have a LAN administrator for each LAN that connects to the corporate backbone. These LAN administrators can be the focal point for disseminating information regarding activities affecting the LAN.
Rules to abide by typically should exist before connecting a LAN to the corporate backbone. Some of these rules are as follows:
Provide documentation on network infrastructure layout.
Provide controlled software downloads.
Provide adequate user training.
Training is also necessary for personnel in charge of giving out passwords. This personnel should ensure that proper credentials are shown before reinstating a “forgotten” password. There have been many publicized incidents in which people received new passwords just by acting aggravated enough but without presenting adequate credentials. Giving out passwords in this fashion can have serious-enough ramifications that the person who bypasses known regulations should be terminated.
Many intruders are far more successful using social engineering than they are with a technical hack. A critical training requirement should be that employees and users are not to believe anyone who calls them on the phone and asks them to do something that might compromise security. Would you give any caller your personal financial information and accept a new PIN number over the phone? Hopefully not—you have not absolutely established the inquirer's identification. The same is true for passwords and any kind of confidential corporate information requested over the phone. Before divulging any kind of confidential information, you must positively identify the person to whom you are talking.
This chapter covered what is needed to create the guidelines and procedures that are part of a corporate security policy. To be effective, the procedures should be concise and to the point. They should encompass rules that define physical security controls—these pertain to the physical infrastructure, physical device security, and physical access. These security policy rules should also promote infrastructure and data integrity as well as data transmission confidentiality to ensure that data has not been altered in transit and is only understandable by the sender and intended receiver of information. In addition, a security policy should have clearly defined rules for security policy verification and monitoring to ensure that the security policy is being effectively implemented and enforced. It also is imperative for every corporation to provide employees with adequate training to educate them about the many problems and ramifications of security-related issues.
The following questions provide you with an opportunity to test your knowledge of the topics covered in this chapter. You can find the answers to these questions in Appendix E, “Answers to Review Questions.”