This chapter examines how to secure Internet access to the corporate network. You can create such security by using some type of firewall functionality and securing the infrastructure devices, as discussed in the previous chapter, that interface with the Internet. Firewalls have become an integral component of perimeter network access, such as the boundary between the trusted corporate network and the less-trusted Internet. On this perimeter, traffic can be analyzed and controlled according to parameters such as specific applications, addresses, and users for both incoming traffic from remote users and outgoing traffic to the Internet.
NOTE
Constructing a firewall policy for your corporate environment was discussed in Chapter 7, “Design and Implementation of the Corporate Security Policy.” If you are new to firewalls, turn to Appendix A, “Sources of Technical Information,” and read the books listed under “Firewall Books” to get a good understanding of firewalls and their function.
A firewall device should be as impenetrable as possible; therefore, it should be one of the most secure devices in your infrastructure. This chapter contains sample firewall design implementations to control Internet access and refers to features specific to equipment provided by Cisco Systems. The chapter explains how to configure Cisco IOS devices and the Cisco (Private Internet Exchange [PIX]) firewall to provide necessary security controls for Internet access. You also can use many of the functions of other products mentioned in this chapter if they are available. You should use the controls described in Chapter 9, “Securing the Corporate Network Infrastructure,” in these devices to provide appropriate security controls.
When the decision is made to connect the corporate network to the Internet, it is important to recognize the additional security exposures. In most cases, you make a decision about how open an environment you can tolerate. In a very open environment, you may impose limited restrictions on access; in a more secure environment, you may impose more stringent access controls for traffic entering or leaving the main corporate network.
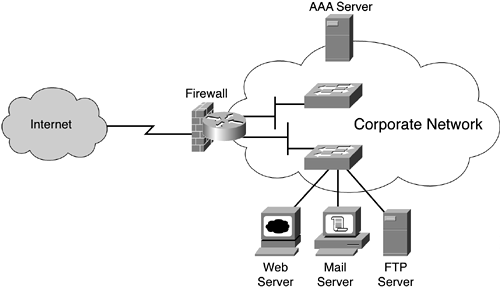
There are many variations on how to design access to the Internet. A common scenario is to construct a firewall between the internal corporate network and the external Internet connection, as shown in Figure 10-1.
The firewall can be a single device, such as a screening router with limited firewall capabilities. Often, the firewall has at least three interfaces. One of these interfaces is used as a perimeter network to isolate services (such as e-mail, FTP, Domain Name System [DNS], and HTTP) offered to Internet users. Internet connections may be restricted solely to these services, which reside on a single subnet. Restricting the services offered to Internet users to a single subnet, if possible, is a good strategy to use to simplify the administration of access control filter lists. The filter lists would typically be much shorter if you only have to worry about a single subnet. The single-firewall-device Internet access architecture may be a sufficient model for a small corporation. However, the downfall is that if this single device is compromised, the entire network is open to exposure.
Another scenario, used most often in high-traffic environments, uses an exterior screening router along with a more robust firewall, as shown in Figure 10-2.
This second model is much more secure because it offers multiple levels of security to the corporation. The exterior screening router acts as a first-level filter to permit or deny traffic coming in from the Internet to the internal campus. It validates most incoming traffic before passing it on to the firewall. The firewall then provides the more CPU-intensive function of packet-by-packet inspection. In this scenario, it is also effective to include an active audit device that includes network traffic monitoring and intrusion detection on the network segment connecting the firewall to the exterior router. This device can verify adherence to the corporate security policy and can pinpoint and isolate any attacks from the Internet to the corporate network—or any attacks instigated from your internal network out to the Internet.
NOTE
Intrusion detection and active audit capabilities should be incorporated at network perimeter points to provide added security measures and to verify proper traffic behavior. A combination of intrusion detection, active audit, and a firewall at the network perimeter is the best defense against most known attacks.
If your corporate network is small, the screening router model may be a sufficient solution to providing secure access to the Internet. It is possible that the security measures used will not always catch spoofed traffic, but at least they should provide a reasonable level of a basic buffer from the Internet.
You can also use the screening router solution in larger networks to define a logical separation internally between some sensitive areas of your network—for example, using a firewall between the finance building and the rest of a large campus, or using firewalls at all network perimeter points (including dial-in points and branch-office connections).
One common variant of the screening router architecture is to place a subnet immediately behind the screening router and have this external LAN be used for all externally available services. A corporate web server, e-mail relay, or application host would be placed on this external LAN. In addition, a second router attached to this subnet can be configured such that administrative access to the servers supplying the externally available services is only allowed from internal corporate hosts. This scenario is often implemented for security policies that dictate that inbound data is allowed only for internally initiated connections and all Internet-destined data from the internal network is proxied through servers residing on the external LAN. It creates a physical separation and also a logical layer between the internal corporate LAN and the Internet.
Most screening routers use filtering capabilities to act as a firewall. How filters are created and to what extent they look at traffic is largely vendor dependent. The following sections examine how Cisco IOS routers provide filtering; most other vendors' devices have similar capabilities.
The Cisco IOS Software has an extended filtering capability to permit or deny specific traffic from entering or leaving the corporate network. These filters are called access control lists (ACLs).
Access control lists filter network traffic by controlling whether routed packets are forwarded or blocked at the router's interfaces. Your router examines each packet to determine whether to forward or drop the packet, based on the criteria specified within the ACLs. The ACL criteria can include the source address of the traffic, the destination address of the traffic, the upper-layer protocol, or other information.
NOTE
Sophisticated users can sometimes successfully evade or fool basic ACLs because the filters are typically based on spoofed or illegal addresses and well-known used services. However, it takes a little more effort to figure out valid IP addresses and services that a corporation may allow, so a minimal set of filtering should always be performed. Refer to Appendix D, “Mitigating Distributed Denial of Service Attacks,” for more information.
If the ACL is inbound, the Cisco IOS Software checks the ACL's criteria statements for a match when the router receives a packet. If the packet is permitted, the software continues to process the packet. If the packet is denied, the software discards the packet.
If the ACL is outbound, the software checks the ACL's criteria statements for a match after receiving and routing a packet to the outbound interface. If the packet is permitted, the software transmits the packet. If the packet is denied, the software discards the packet.
WARNING
Cisco IOS Software Release 11.1 and later releases introduced substantial changes to IP ACLs. These extensions are backward compatible; migrating from a release earlier than Release 11.1 to the current image will convert your ACLs automatically. However, previous releases are not upwardly compatible with these changes. Therefore, if you save an ACL with the current image and then use older software, the resulting ACL may not be interpreted correctly. This error can cause severe security problems. Save your old configuration file before booting Release 11.1 or later images.
You can specify ACLs for a number of different protocols. This example shows the output on a Cisco IOS device when performing an access-list:
Router(config)#access-list ?
<1-99> IP standard access list
<100-199> IP extended access list
<200-299> Protocol type-code access list
<300-399> DECnet access list
<600-699> Appletalk access list
<700-799> 48-bit MAC address access list
<800-899> IPX standard access list
<900-999> IPX extended access list
<1000-1099> IPX SAP access list
<1100-1199> Extended 48-bit MAC address access
list
<1200-1299> IPX summary address access list
Because we deal mainly with the IP protocol for Internet access, this discussion is restricted to the IP standard and IP extended ACLs. For details on other protocols, refer to the Cisco online documentation.
Standard IP access control lists use the source IP addresses for matching operations. The configuration command takes the following syntax:
access-list access-list-number {deny | permit} source [source-wildcard] [log]
NOTE
You can use the abbreviation any to specify a source and source mask of 0.0.0.0 through 255.255.255.255.
In Example 10-1, a standard ACL is created and applied to the incoming Internet traffic interface. The ACL denies all inbound traffic from the Internet that contains a source address from known reserved RFC addresses and permits any other traffic from the Internet to the corporate campus. Only the invalid traffic is logged, because there should be minimal logging unless a potential attack is in progress. It is also good practice to precede any access list configuration with the no access-list access-list-number command to clear out any previously defined commands.
Example 10-1. Standard Access List Configuration Commands on Incoming Interface
! clear out any previously defined list no access-list 9 ! source addresses from reserved address space defined in RFC 1918 access-list 9 deny 127.0.0.0 0.255.255.255 log access-list 9 deny 10.0.0.0 0.255.255.255 log access-list 9 deny 172.16.0.0 0.15.255.255 log access-list 9 deny 192.168.0.0 0.0.255.255 log access-list 9 permit any ! apply access-list 9 to the incoming Internet interface interface Serial 0/0 description to the Internet ip address 161.71.73.33 255.255.255.248 ip access-list 9 in
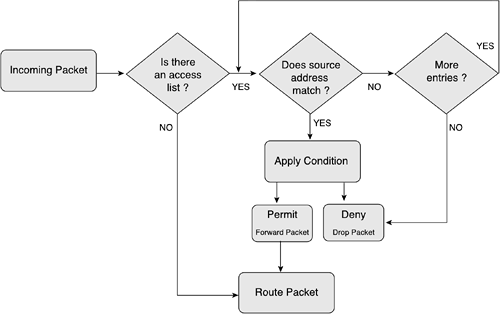
Figure 10-3 shows the algorithm used to process a standard ACL. As a packet reaches an interface, a process occurs to determine whether an access list should be checked. If the answer is no, the packet is forwarded for processing. If the answer is yes, the list is sequentially checked to determine whether there is a source address match. When there is a match, the appropriate condition is applied (to drop the packet and send an Internet Control Message Protocol [ICMP] unreachable message or to forward the packet). The last entry of an ACL is always an implicit deny all.
Extended IP ACLs provide finer granularity of control for the type of traffic that is permitted or denied. They use a combination of source and destination IP addresses and optional protocol-type information for matching operations.
The following command defines an extended IP ACL number and its access conditions:
access-list access-list-number {deny | permit} protocol source source-wildcard destination destination-wildcard [operator] [operand][precedence precedence] [tos tos] [established] [log | log-input]
NOTE
You can use the abbreviation host for a specific source and for a specific destination without having to include the source wildcard or the destination wildcard. The log-input parameter will include the interface that the packet applies to and is the recommended logging parameter.
For IP extended ACLs, you can define a number of well-known protocols:
Router(config)#access-list 101 permit ?
<0-255> An IP protocol number
eigrp Cisco's Enhanced IGRP routing protocol
gre Cisco's GRE tunneling
icmp Internet Control Message Protocol
igmp Internet Gateway Message Protocol
igrp Cisco's IGRP routing protocol
ip Any Internet protocol
ipinip IP in IP tunneling
nos KA9Q NOS-compatible IP over IP tunneling
ospf OSPF routing protocol
tcp Transmission Control Protocol
udp User Datagram Protocol
The most common protocols to filter are the TCP and UDP protocols. For the TCP protocol, you can filter on the following parameters (operators):
Router(config)#access-list 101 permit tcp any any ?
eq Match only packets on a given port number established
established Match established connections
gt Match only packets with a greater port number
log Log matches against this entry
lt Match only packets with a lower port number
neq Match only packets not on a given port number
precedence Match packets with a given precedence value
range Match only packets in the given range of port numbers
tos Match packets with the given TOS value
Here is a list of the more commonly used TCP port numbers (operands):
Router(config)#access-list 101 permit tcp any any eq ?
<0-65535> Port number
bgp Border Gateway Protocol (179)
chargen Character generator (19)
cmd Remote commands (rcmd, 514)
daytime Daytime (13)
discard Discard (9)
domain Domain Name Service (53)
echo Echo (7)
exec Exec (rsh, 512)
finger Finger (79)
ftp File Transfer Protocol (21)
ftp-data FTP data connections (used infrequently, 20)
gopher Gopher (70)
hostname NIC hostname server (101)
ident Ident Protocol (113)
irc Internet Relay Chat (194)
klogin Kerberos login (543)
kshell Kerberos shell (544)
login Login (rlogin, 513)
lpd Printer service (515)
nntp Network News Transport Protocol (119)
pop2 Post Office Protocol v2 (109)
pop3 Post Office Protocol v3 (110)
smtp Simple Mail Transport Protocol (25)
sunrpc Sun Remote Procedure Call (111)
syslog Syslog (514)
tacacs TAC Access Control System (49)
talk Talk (517)
telnet Telnet (23)
time Time (37)
uucp UNIX-to-UNIX Copy Program (540)
whois Nicname (43)
www World Wide Web (HTTP, 80)
For UDP, here is a list of the more commonly used port numbers:
Router(config)#access-list 101 permit udp any any eq ?
<0-65535> Port number
biff Biff (mail notification, comsat, 512)
bootpc Bootstrap Protocol (BOOTP) client (68)
bootps Bootstrap Protocol (BOOTP) server (67)
discard Discard (9)
dnsix DNSIX security protocol auditing (195)
domain Domain Name Service (DNS, 53)
echo Echo (7)
mobile-ip Mobile IP registration (434)
nameserver IEN116 name service (obsolete, 42)
netbios-dgm NetBios datagram service (138)
netbios-ns NetBios name service (137)
ntp Network Time Protocol (123)
rip Routing Information Protocol (router, in.routed, 520)
snmp Simple Network Management Protocol (161)
snmptrap SNMP Traps (162)
sunrpc Sun Remote Procedure Call (111)
syslog System Logger (514)
tacacs TAC Access Control System (49)
talk Talk (517)
tftp Trivial File Transfer Protocol (69)
time Time (37)
who Who service (rwho, 513)
xdmcp X Display Manager Control Protocol (177)
NOTE
When dealing with TCP or UDP port numbers, remember that these commonly known port numbers are always used as the destination port number. The source port number is more or less arbitrarily picked by the originating host from the range of numbers 0 to 65,535.
Keep in mind the following few things when configuring ACLs on Cisco IOS devices:
By default, the end of the ACL contains an implicit deny statement for everything if it does not find a match before reaching the end.
After the ACL has been created on the router, any subsequent additions (possibly entered from the terminal) are placed at the end of the list. In other words, you cannot selectively add or remove ACL command lines from a specific ACL.
The order of ACLs is important. The entries are searched in sequential order; the first match is the one acted on.
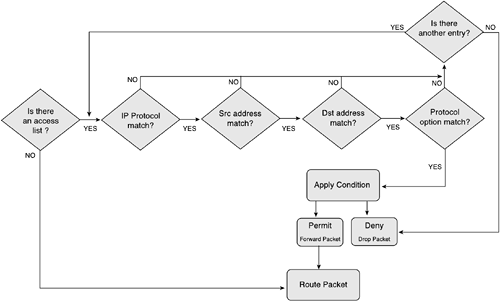
Figure 10-4 shows the algorithm used for an IP extended ACL.
NOTE
It is recommended that you create your ACLs on a secure FTP or Secure Copy Protocol (SCP) server and then download the ACLs to your router. This approach can considerably simplify maintenance of your ACLs because the order of ACL criteria statements is important and because you cannot reorder or delete criteria statements on your router. The secure FTP or SCP server should be well protected from both read and write access to ensure that only authorized personnel have access to the files. Also, remove references to the access lists on interfaces before changing or updating the access list. After completing the editing, you should again configure the interface to apply the access list. Although this opens a small window of potential exposure while the interfaces are without ACLs, this procedure is the “cleanest” way to update ACLs.
Example 10-2 shows the configuration commands of an extended IP ACL. It meets the following criteria:
It allows all incoming TCP traffic if the session was initiated within the internal corporate network.
It allows FTP control and FTP data traffic to the FTP server with the address 144.254.1.4.
It allows HTTP traffic to the web server with the address 144.254.1.3.
It denies all other traffic from entering the corporate network.
It logs all ACL violations.
Example 10-2. Configuration of an Extended Access List
! start with clearing out any previously established list no access list 101 ! create the access list access-list 101 permit tcp any any established access-list 101 permit tcp any host 144.254.1.4 eq ftp access-list 101 permit tcp any host 144.254.1.4 eq ftp-data access-list 101 permit tcp any host 144.254.1.3 eq www access-list 101 deny ip any any log-input ! configure the Internet interface and apply the inbound access-list 101 interface Serial 0/0 description to the Internet ip address 161.71.73.33 255.255.255.248 ip access-group 101 in
The order in which you create your ACL entries is important in Cisco IOS devices. When the router is deciding whether to forward or block a packet, the Cisco IOS Software tests the packet against each criteria statement in the order the statements were created. After a match is found, no more criteria statements are checked. From a performance standpoint, if you have the need for very long lists (for example, more than 100 entries), you should place the more common scenarios at the beginning of the list. If most of your incoming traffic is web related, for instance, you should place the criteria for web traffic at the top of the list. The other ordering criteria for statements is to go from the specific to the general. You need to be careful about reordering statements if the granularity differs for newer entries.
NOTE
You can use the established keyword only for the TCP upper-layer protocol filters. The expectation is that a session has been started from an internal source to an external source and this permitted traffic is the reply; therefore, it is an “established” session. The manner in which the established keyword filters TCP packets is based on whether the ACK or RST bit is set. (Set ACK and RST bits indicate that the packet is not the first in the session and, therefore, that the packet belongs to an established session.) Reflexive ACLs provide a more robust session-filtering mechanism and are described later in this chapter.
Turbo ACLs were introduced in Cisco IOS Software Release 12.1(6). A Turbo ACL is configured with the access-list compiled command. It is a technique that takes a standard or extended ACL, creates a set of data tables, and compiles them into fast lookup tables. The matching semantics are preserved while reducing the number of CPU operations to find a match. This allows for very large filter lists to be used without an increase in packet latency. The processing of Turbo ACLs takes a maximum of five steps, no matter what the size of the filter. This feature proves useful if you have filters that contain a large number of entries. (I recommend using it if you exceed 20 entries on any ACL.)
NOTE
Application-specific integrated circuit (ASIC)-based access control functionality is also available on some higher-end router platforms such as the Cisco 12000. This hardware-based filter processing greatly enhances the processing performance of large filter lists. Large corporations that have such requirements should follow the latest Cisco developments for this capability. So far, I have heard that Turbo lists are most effective on higher-end router platforms with access lists with more than 128 entries (448 entries for hardware-assisted Turbo).
Named ACLs were introduced in Cisco IOS Software Release 11.0. You can identify IP ACLs with an alphanumeric string (a name) rather than a number (1 to 199). Named ACLs enable you to configure more than 99 standard IP (and 100 extended IP) ACLs in a router. Currently, only packet and route filters can use a named list.
The advantage of using a named ACL is that you can selectively remove entries. However, you still cannot selectively add ACL command lines to a specific ACL—subsequent additions are still placed at the end of the list.
Consider the following before configuring named ACLs:
Access lists specified by name are not compatible with older releases.
Not all ACLs that accept a number will accept a name. Access lists for packet filters and route filters on interfaces can use a name.
A standard ACL and an extended ACL cannot have the same name.
An example of a named ACL is shown in the next section. (Reflexive ACLs require the use of extended named ACLs.)
Reflexive ACLs were introduced in Cisco IOS Software Release 11.3. They allow IP packets to be filtered based on upper-layer session information.
A common requirement for filtering is to permit IP traffic for sessions originating from within your network but to deny IP traffic for sessions originating from outside your network. Using basic extended ACLs, you can approximate session filtering by using the established keyword with the permit command. The established keyword filters TCP packets based on whether the ACK or RST bits are set. This method of using the established keyword is available only for the TCP upper-layer protocol. For the other upper-layer protocols (such as UDP, ICMP, and so forth), you have to either permit all incoming traffic or define all possible permissible source/destination host/port address pairs for each protocol.
Reflexive ACLs are much more suitable for true session filtering. After it has been configured, a reflexive ACL is triggered when a new IP upper-layer session (such as TCP or UDP) is initiated from inside your network, with a packet traveling to the external network. When triggered, the reflexive ACL generates a new, temporary entry. This entry permits traffic to enter your network if the traffic is part of the session, but does not permit traffic to enter your network if the traffic is not part of the session. The filter criterion is based on the ACK and RST bits as well as the source and destination addresses and port numbers. Session filtering uses temporary filters that are removed when a session is over, limiting the hacker's attack opportunity to a smaller time frame.
Temporary reflexive ACL entries are removed at the end of the session. For TCP sessions, the entry is removed 5 seconds after two set FIN bits are detected, or immediately after matching a TCP packet with the RST bit set. (Two set FIN bits in a session indicate that the session is about to end; the 5-second window allows the session to close gracefully. A set RST bit indicates an abrupt session close.) Alternatively, the temporary entry is removed after no packets of the session have been detected for a configurable length of time (called the timeout period).
For UDP and other protocols, the end of the session is determined differently than it is for TCP. Because other protocols are considered to be connectionless (sessionless) services, they have no session-tracking information embedded in their packets. Therefore, the end of a session is considered to be when no packets of the session have been detected for a configurable length of time (the timeout period).
Two restrictions apply to using the reflexive ACL feature:
Reflexive ACLs can be defined with extended named IP ACLs only. You cannot define reflexive ACLs with numbered or standard named IP ACLs or with other protocol ACLs.
Reflexive ACLs do not work with some applications that use port numbers that change during a session. If the port numbers for a return packet differ from those of the originating packet, the return packet will be denied, even if the packet is actually part of the same session.
The TCP-based application FTP is an example of an application with changing port numbers. With reflexive ACLs, if you start an FTP request from within your network, the request will not complete. Instead, you must use passive FTP when originating requests from within your network.
Figure 10-5 shows an example of how to use reflexive ACLs. Notice that the Ethernet interface connects to the internal corporate networks, and that the serial interface connects to the Internet. The configuration example permits both inbound and outbound TCP traffic on the serial interface—but only if the first packet in a given session originated from inside your corporate network.
Example 10-3 shows the configuration commands for a reflexive ACL.
Example 10-3. Configuring a Reflexive Access List
! Define the global idle timeout value for all reflexive access lists. ! If for 120 seconds there is no TCP traffic that is part of an ! established session, the corresponding reflexive access list ! entry will be removed. ip reflexive-list timeout 120 ! Define the outbound access list. This is the access list that ! evaluates all outbound traffic on interface Serial 1. ip access-list extended outboundfilters remark permit all outbound TCP traffic ! Define the reflexive access list tcptraffic. This entry permits all ! outbound TCP traffic and creates a new access list named tcptraffic. permit tcp any any reflect tcptraffic ! Define the inbound access list. This is the access list ! that evaluates all inbound traffic on interface Serial 1. ip access-list extended inboundfilters remark permit routing but deny ICMP and check all TCP traffic ! Define the inbound access list entries. Permit BGP and EIGRP ! but deny ICMP. The last entry points to the reflexive access list. ! If a packet does not match the first three entries, the packet will ! be evaluated against all the entries in the reflexive access list ! named tcptraffic. permit bgp any any permit eigrp any any deny icmp any any evaluate tcptraffic ! Define the interface where the session-filtering configuration is ! to be applied and apply access lists to the interface, for inbound ! traffic and for outbound traffic. interface Serial 1 description Access to the Internet ip access-group inboundfilters in ip access-group outboundfilters out
Although a screening router is a good first step toward providing Internet access security, a more secure solution relies on a more robust firewall architecture. Typically, this is accomplished with both a screening router and more intense firewall capabilities. In addition to primitive filtering capabilities, a firewall typically has the capability to provide the following:
Advanced packet-by-packet inspection
Application content filtering
Application authentication/authorization
Encryption technology
Network Address Translation (NAT)
The traffic-filtering capabilities must incorporate state information and often must also be able to filter on application content. E-mail virus scanning, Java applet filtering, and URL logging or blocking are some of the commonly implemented advanced functions in a firewall. Sometimes these application-specific functions are offloaded to separate devices to save CPU processing cycles on the firewall device itself.
Packet authentication and confidentiality using encryption is becoming a strong requirement. Implementing this functionality in a multivendor-interoperable way has become much easier with the emergence of IPsec products. IPsec authentication and confidentiality capabilities can be applied to many Internet access architectures to provide for authenticated, confidential traffic flow.
NAT is also commonly used but, as mentioned in Chapter 6, “Considerations for a Site Security Policy,” a legitimate network interface card (NIC)-assigned address should be used whenever possible to avoid any application or feature restrictions in the future. (This is strictly the author's opinion and mileage may vary depending on specific requirements.)
A robust firewall must have the capability to perform packet-by-packet inspection and filtering on specific packet session information. The firewall should inspect traffic that travels through it to discover and manage state information for TCP and UDP sessions. For many corporate environments, FTP, Telnet, HTTP traffic, Java applets, e-mail, DNS, and some popular voice and video applications must be supported. Controls must be in place to ensure as best as possible that any such traffic is valid traffic.
Most advanced session filters keep information relating to the following questions:
For IP traffic using the TCP protocol, advanced packet session filtering inspects all IP and TCP headers in every packet based on a combination of the following fields:
IP Destination Address
IP Source Address
IP Protocol
TCP Source Port
TCP Destination Port
TCP Flags:
SYN alone for a request to open a connection
SYN/ACK for a connection confirmation
ACK for a session in progress
FIN for session termination
These fields allow the monitoring of connection state information and provide a reasonable amount of certainty about when valid connections are in progress.
For IP traffic using the UDP protocol, advanced packet session filtering inspects all IP and UDP headers in every packet based on a combination of the following fields:
IP Destination Address
IP Source Address
IP Protocol
UDP Source Port
UDP Destination Port
Because UDP is a connectionless service, there are no actual UDP “sessions” per se. Most systems approximate sessions by examining UDP packet information and determining whether the packet is similar to other UDP packets recently seen.
Application content filtering refers to examining packet content in more detail to ensure validity of the content. Some of the more common applications whose content you may want to control or examine are described in the following sections.
The World Wide Web has played a large role in making the Internet a place to conduct business. Chapter 2, “Security Technologies,” described technologies such as S-HTTP and SSL that enable you to secure web transactions. However, program languages, such as Java and JavaScript, that are used to write interactive programs for web applications remain a security issue. Some corporations also want to restrict specific URL sites from their employees because of the sites' possibly illegal content.
When World Wide Web users download a web page with embedded Java or JavaScript programs (called applets), there is no control over whether the applet has approved content or whether it contains a virus or malicious program. You must prevent users from inadvertently downloading destructive Java applets into your network. To protect against this risk, you could require all users to disable Java in their browser. If this is not an agreeable solution, you can use methods to filter Java applets at the firewall, allowing users to download only those applets residing within the firewall and trusted applets from outside the firewall.
WARNING
Many firewalls do not detect or block encapsulated Java applets. Therefore, Java applets that are wrapped or encapsulated (for example, those in .zip or .jar format) are usually not blocked at the firewall. In addition, some firewalls may not detect or block applets loaded using FTP, Gopher, or HTTP on a nonstandard port.
Some corporations may want to restrict access to certain URLs because of the sites' inappropriate content (for example, pornographic material). By providing URL-filtering and blocking capabilities, the firewall can be used to restrict access to specified websites.
Simple Mail Transfer Protocol (SMTP) is used to handle e-mail exchange between mail servers on the Internet. Many firewalls have the capability to check SMTP messages for illegal commands. Any packets with illegal commands are usually dropped, and the SMTP session will hang and eventually time out.
In a Cisco PIX firewall, for example, an illegal command is any command except for the following legal commands:
Many multimedia applications used for videoconferencing—for example, CUseeMe, H.323 (for NetMeeting and ProShare), and RealAudio—use the TCP control channel to establish media channels. This control channel contains information that opens new media channels. Firewalls should have the capability to watch these control channels, to identify those ports that media channels use, and the capability to open additional channels on a dynamic basis.
Table 10-1 lists the most common applications that should be supported in firewalls if they are to have extensive application control support.
Table 10-1. Common Application Protocols
You should configure authentication and authorization controls for device access on all infrastructure devices, including the routers and firewalls that provide Internet access. These controls were discussed in Chapter 9. In addition, there may be a requirement to authenticate based on application access. For example, you may have a policy in place that requires all incoming HTTP sessions to be authenticated before they can access a specific web server.
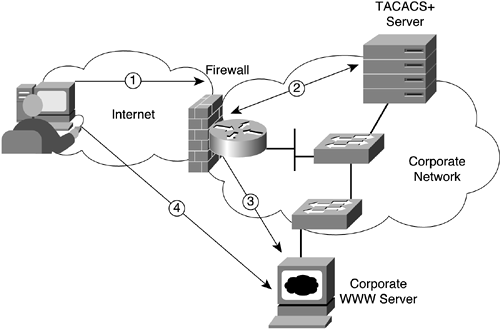
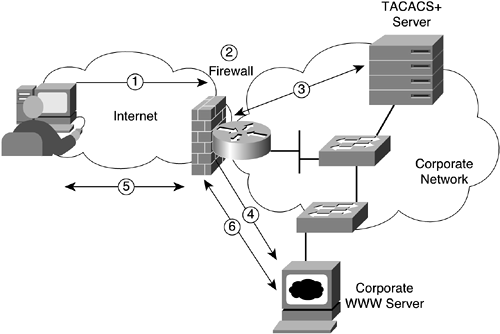
Figure 10-6 shows a sample scenario.
In this figure, the following steps are carried out:
The user from the Internet initiates an HTTP request to a specified corporate web server.
The firewall intercepts the connection and initiates the authentication process (shown here using TACACS+).
If the user authenticates successfully, the firewall completes the HTTP connection to the corporate web server.
The firewall forwards requests and responses without further intervention.
In addition to authentication, if you are using TACACS+ or RADIUS (which also include authorization methods), you can usually configure the firewall to permit access to specific hosts or services depending on user or host identity. It is up to the corporation to determine which users can access the network, which services those individuals can use, and which hosts they can access.
With the emergence of IPsec in many products, it is easier for corporate networks to implement authenticated and confidential data transfer sessions. Ideally, encrypted traffic (encrypted for the sake of authentication and confidentiality) should stay encrypted from the sender to the recipient. Because of the complexity and difficulty of deploying encryption for all hosts on the network, however, many companies use the network infrastructure to encrypt the traffic traversing untrusted networks.
NOTE
When talking about authentication in IPsec, it relates to data integrity and data origin authentication. Most other authentication (such as application layer authentication) relates to a user actually having to enter credentials to provide identification that allows access to a specific application or service.
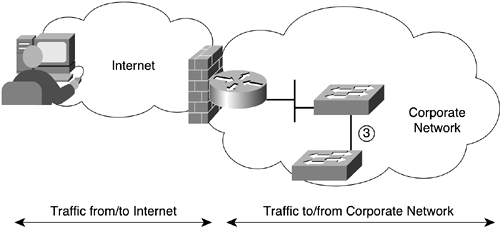
Because IPsec allows for authenticated traffic, confidential traffic, or both, you must make a variety of decisions about where to provide authentication and where to provide confidentiality measures. Figure 10-7 shows the network, and Table 10-2 lists the various combinations to be considered for traffic passing to or from the Internet and the corporate network. The traffic from/to the Internet is outside the firewall (the external network), and the traffic to/from the corporate network is inside the firewall (the internal network). Often, the policy chosen with regard to authentication and confidentiality will vary for traffic that traverses the external or internal network.
Table 10-2. Possible IPsec Use Through a Firewall
Policy Choices for Traffic from/to Internet | Policy Choices for Traffic to/from Corporate Network |
|---|---|
Authentication and confidentiality | Authentication and confidentiality |
Authentication and confidentiality | Authentication |
Authentication and confidentiality | No IPsec |
Authentication | Authentication |
Authentication | Authentication |
No IPsec | No IPsec |
In all cases for Table 10-2, the firewall is an IPsec endpoint that can operate in either IPsec transport or tunnel mode.
Refer to Chapter 2 for a more detailed explanation of IPsec.
NOTE
When using IPsec, authentication is always recommended and is in practice usually deployed using IPsec ESP with NULL encryption. Authentication ensures a high probability of data origin validation and that the data has not been altered in transit. Confidentiality measures should be used in addition to authentication for very sensitive data as determined by risk analysis.
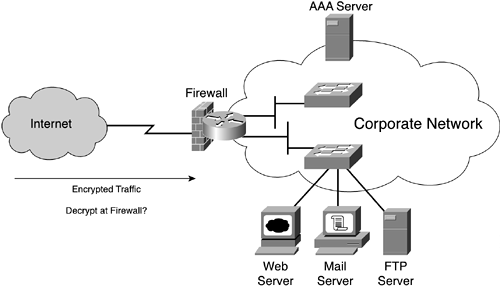
If traffic remains encrypted for confidentiality from sender to recipient, in many cases this means that the corporate Internet access firewall will have to be bypassed, which is commonly referred to as “crating a hole in the firewall.” By its very nature, encrypted traffic is kept confidential and the only filtering that can be done is on IP addresses and the destination protocol being used (IPsec Internet Key Exchange [IKE], IPsec ESP, SSL, and so on). This is usually not sufficient. Smaller corporations might want to use a scenario such as the one shown in Figure 10-8, in which a single device handles the routing and firewall functionality.
The considerations here for outside-encrypted traffic coming in to the corporate network takes two forms: The router/firewall can decrypt the traffic, or the assumption is made that the traffic is valid and therefore just forwarded to the destination within the network. If you decide on the latter, you will effectively bypass any security policy that mandates that all incoming traffic should be statefully inspected for potential security violations. It is much better to decrypt the traffic at the Internet access ingress point and perform a stateful firewall inspection. In addition, if you have decrypted the traffic, the router/firewall could take advantage of added functionality when certain application traffic may need to be authenticated by users before it is forwarded.
NOTE
Many current implementations that use SSL for secure web traffic tunnel SSL through the firewall. Future secure web transactions may use IPsec, where firewalls will not be bypassed.
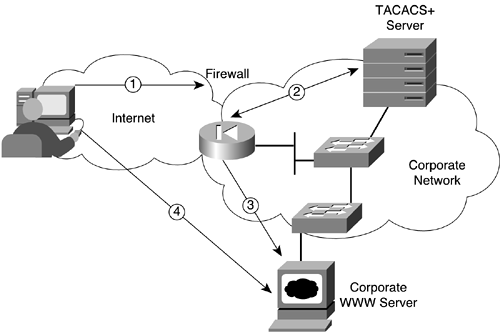
Figure 10-9 shows a sample scenario in which web traffic is encrypted using IPsec, but the firewall can still enforce user-authenticated web transactions.
In the figure, the following steps are carried out:
The user from the Internet initiates an encrypted HTTP request to a specified corporate web server.
The firewall decrypts the packet and recognizes that it is an HTTP request.
The firewall intercepts the connection and initiates the authentication process (shown here using TACACS+).
If the user authenticates successfully, the firewall completes the HTTP connection to the corporate web server.
The firewall subsequently decrypts all incoming web traffic and forwards the unencrypted packet to the internal corporate host. (All new web sessions are authenticated.)
The firewall takes all responses from the web server going to the host on the Internet and encrypts them before forwarding them to the Internet host.
If a requirement exists to encrypt the web traffic from the firewall to the internal web server, it can be accomplished at the expense of more CPU cycles. The firewall must first decrypt the incoming data, perform the firewall functionality (and possible user authentication), and then encrypt the data again before forwarding it to the internal web server. This is not necessarily an optimal solution, but it can provide for end-to-end encryption if you do not trust even your internal network.
Larger networks are more likely to have a scenario such as the one illustrated in Figure 10-10, where Internet access uses a combination of a screening router and a firewall. For this sort of architecture, the considerations are a bit more complex, as follows:
Encrypt/decrypt only between outside hosts and the screening router.
This approach allows the screening router to decrypt a packet coming from an untrusted outside network and perform a precursory filter check before passing the packet to the firewall for more complete inspection. This approach assumes that the internal network is secure and that no encryption is required within the corporate network.
Encrypt/decrypt only between outside hosts and the firewall.
After an initial filter check is performed using only IP addresses, the packet is sent to the firewall for inspection. Most likely the filter will permit any traffic through that uses IPsec and adheres to certain IP address constraints. The firewall then decrypts the packet and performs a stateful inspection (and possible user authentication). When the packet is declared valid, it is forwarded to its intended recipient within the corporate network.
Encrypt/decrypt on both the screening router and the firewall.
This approach allows the screening router to decrypt a packet coming from an untrusted outside network and perform a precursory filter check before passing the packet to the firewall for more complete inspection. When the firewall has completed its task, the firewall then encrypts the packet and forwards it to its intended recipient. The assumption here is that the corporate network is insecure and that the CPU cycles spent are necessary to protect the packet end to end (with the exception of when the packet gets passed from the screening router to the firewall, which is expected to be a secure connection).
Do not encrypt/decrypt.
This approach will bypass any stateful firewall inspection, and the assumption is made that all encrypted traffic can be trusted.
The decision as to which is the best approach in your environment can vary greatly and very much depends on the conclusions you came to when creating your corporate security policy. (The approach I prefer is to use the screening router to perform an initial filter check and then let the firewall decrypt the traffic and do a stateful analysis on the packet.) Whether or not to encrypt the traffic again depends on how much you trust the internal network and whether there are more firewalls to traverse before the packet actually reaches its intended destination.
Network Address Translation (NAT) is often used in environments that have private address space as opposed to a globally unique address. Private address space is not a security feature because, more often than not, the private address will be known. The Internet Assigned Numbers Authority (IANA) has reserved the following three blocks of IP address space for private networks:
10.0.0.0 through 10.255.255.255
172.16.0.0 through 172.31.255.255
192.168.0.0 through 192.168.255.255
The first block is a single Class A network number, the second block is a set of 16 contiguous Class B network numbers, and the third block is a set of 256 contiguous Class C network numbers. IANA has reserved these address blocks for private use because they were specified by RFC 1918.
If a corporation decides to use private addressing, these blocks of addresses should be used—unless, of course, there is a historical reason why some other private address space is being used. The more common reason is the infamous, “We'll never need to connect to the Internet!”
The question of whether to use private addressing is becoming a part of network design for many corporate TCP/IP application users. The Internet has grown beyond anyone's expectations. With this growth came concerns about Internet address depletion and, more importantly, address-allocation procedures and their impact on the Internet routing system. There are a few reasons why private address space could and should be used (such as for environments where external connectivity may not be required or is extremely limited). Some examples include the following:
A large organization where only a small number of specific hosts are allowed access to the Internet.
A large organization where outside Internet access is allowed only to a few specified hosts, such as web servers.
An organization that may have had to switch Internet service providers and received a new block of address space. It may have been too cost prohibitive or disruptive to change to the new address space at the time.
The cost of using private Internet address space is the potentially costly effort to renumber hosts and networks between public and private. If the company has any thought about opening up to global Internet access, it is recommended that the corporation start a transition plan for renumbering to a globally unique address if it is currently using private address space. The widespread use of Dynamic Host Configuration Protocol (DHCP) is making this process much easier and may help avoid possible future issues with non-NAT-able and non-proxy-able protocols.
If you decide to use private address space, however, you don't have to coordinate with IANA or an Internet registry. Addresses within this private address space are unique only within your network.
NOTE
Remember, if you need globally unique address space, you must obtain addresses from an Internet registry or your service provider. This is necessary if any part of your network is connected to the Internet. The trend in the past few years has been to get a block of globally unique addresses from your network service provider, with only larger corporations petitioning a regional or local Internet registry directly for addressing.
To use private address space, determine which hosts do not need to have network layer connectivity to the outside. These hosts are private hosts and will use private address space. Private hosts can communicate with all other hosts within the corporate network, both public and private, assuming that all addressing within the corporate network is unique. However, the private hosts cannot have IP connectivity to any host external to the corporate network without the use of NAT or proxies.
All public hosts use the globally unique address space assigned by an Internet registry. Public hosts can communicate with other hosts within the network and can have IP connectivity to external public hosts. Figure 10-10 shows the differences between public and private address spaces (assuming that NAT is not being used).
Because private addresses have no global meaning, routing information about private networks is not propagated on outside links, and packets with private source or destination addresses should not be forwarded across such links. Routers in networks that don't use private address space—especially those of Internet service providers—should be configured to reject (filter out) routing information about private networks.
With this scheme, many large networks need only a relatively small block of addresses from the globally unique IP address space. The Internet at large benefits through conservation of globally unique address space, and the corporate networks benefit from the increased flexibility provided by a relatively large private address space.
In its simplest configuration, NAT is performed in both directions on only one end of the communication and operates on the router or firewall connecting the inside corporate network to the outside Internet, as shown in Figure 10-11.
The inside corporate network is addressed with private addresses that must be converted into legal addresses before packets can be forwarded to the outside Internet.
NAT functionality can become quite complex, depending on the applications it has to support. Here are some of the functionalities you should consider when opting for NAT for Internet access:
Static address translation—. The user can establish a one-to-one mapping between the inside local addresses and the global addresses.
Dynamic source address translation—. The user can establish dynamic mapping between the inside local addresses and the global addresses. This is done by describing the local addresses to be translated and the pool of addresses from which to allocate global addresses, and then associating the two.
Dynamic port translation—. The user can conserve addresses in the global address pool by allowing source ports in TCP connections or UDP conversations to be translated. Different local addresses then map to the same global address, with port translation providing the necessary uniqueness. When translation is required, the new port number is picked out of the same range as the original, following the convention of Berkeley Standard Distribution (BSD):
(1–511, 512–1023, 1024–4999, 5000–65,535)
Destination address rotary translation—. A dynamic form of destination translation can be configured for some outside-to-inside traffic. After a mapping is set up, a destination address matching one of those addresses on an ACL is replaced with an address from a rotary pool. Allocation is done on a round-robin basis, performed only when a new connection is opened from the outside to the inside. All non-TCP traffic is passed untranslated (unless other translations are in effect).
When using NAT, you should always ensure that all corporate applications that require Internet access are supported through the firewall. Typically, the following protocols and applications are supported:
Any TCP-based protocol that does not carry the source or destination IP address in the data portion of the segment. These protocols include ICMP, HTTP, SMTP, and others.
Any UDP-based protocol that does not carry the source or destination IP address in the data portion of the datagram. These protocols include TFTP, NTP, and others.
Now it's time to consider two scenarios:
A Cisco IOS firewall
A PIX firewall used in conjunction with a screening Cisco IOS router
In both cases, you should use an intrusion detection system to help get more information in case an attack is attempted and to keep active audit logs of traffic coming into or leaving the corporate network.
NOTE
The intent of the following sections is to point out practical design examples for implementing robust firewall designs. Sample scenarios are given with configuration commands that may not have been covered in detail in this text. Refer to Appendix A under “Cisco Security Product Information” for places to get more detailed configuration command information.
The Cisco IOS firewall includes features that enable the required functionality of a robust firewall. The advanced traffic session filtering is performed using the Content-Based Access Control (CBAC) mechanism.
Advanced packet session filtering in Cisco IOS Software is supported as of Release 11.2 with the CBAC feature. By default, Cisco routers pass all routable traffic between all router interfaces.
CBAC not only examines network layer and transport layer information, it also examines the application layer protocol information (such as FTP connection information) to learn about the state of the TCP or UDP session. In this way, CBAC allows support of protocols that involve multiple channels created as a result of negotiations in the control channel. Most of the multimedia protocols—and some other protocols (such as FTP, remote-procedure call [RPC], and SQL*Net)—involve multiple channels.
CBAC inspects traffic that travels through the firewall to discover and manage state information for TCP and UDP sessions. This state information is used to create temporary openings in the firewall's ACLs to allow return traffic and additional data connections for permissible sessions (sessions that originated from within the protected internal network).
In many cases, you will configure CBAC in one direction only at a single interface. This arrangement causes traffic to be permitted back into the internal network only if the traffic is part of a permissible (valid, existing) session.
To define a set of inspection rules, use the ip inspect name global configuration command:
ip inspect name inspection-name protocol [timeout seconds]
You can configure CBAC to inspect the following types of transport and application layer protocols:
All TCP sessions, regardless of the application layer protocol (sometimes called single-channel or generic TCP inspection). This includes applications such as HTTP, Telnet, SSL, POP3, and so on. Generic TCP transport inspection works only for protocols that use a single TCP connection and are initiated from the client inside the trusted network.
All UDP sessions, regardless of the application layer protocol (sometimes called single-channel or generic UDP inspection). This includes applications such as IPsec IKE, DNS, TFTP, NTP, SNMP, and so on. Generic UDP transport inspection works only for protocols that use a single client host/port pair and a single server host/port pair.
FTP. CBAC watches the FTP authentication exchange and also prevents use of nonstandard ports for FTP data.
H.323 (such as NetMeeting, ProShare). Generic UDP must also be configured for NetMeeting because it uses additional nonstandard UDP ports.
RealAudio. CBAC will automatically track the RealAudio port assignments.
SMTP. Only RFC 821 standard SMTP commands are permitted when using CBAC.
When a protocol is configured for CBAC, the protocol's traffic is inspected, state information is maintained, and, in general, packets are allowed back through the firewall only if they belong to a permissible session.
NOTE
Before you configure Java inspection, you must configure a standard ACL that defines “friendly” and “hostile” external sites. You configure this ACL to permit traffic from friendly sites and to deny traffic from hostile sites. If you do not configure an ACL but use a “placeholder” ACL in the ip inspect name inspection-name http command, all Java applets are blocked.
Create a standard ACL that permits traffic only from friendly sites and that denies traffic from hostile sites. Block all Java applets except for applets from the friendly sites defined in the ACL. Java blocking works only with standard ACLs.
access-list access-list-number {deny | permit} source [source-wildcard] ip inspect name inspection-name http [java-list access-list] [timeout seconds]
CBAC does not provide intelligent filtering for all protocols; it works only for the protocols you specify. If you don't specify a certain protocol for CBAC, the existing ACLs determine how that protocol is filtered. No temporary openings are created for protocols that have not been specified for CBAC inspection.
CBAC also has mechanisms that can protect against denial-of-service (DoS) attacks. A number of commands control timeout and threshold values to manage session state information and help determine when to drop sessions that do not become fully established. Table 10-3 lists the configurable parameters and their associated default values.
Table 10-3. CBAC Default Timeout and Threshold Values
In some instances, it may be necessary to modify the default values, but that will depend on what speeds your links are and how conservative you want to be.
There is also a command you can use to protect a specific host and set a maximum threshold for half-open TCP sessions. This can protect critical web servers explicitly. The command is as follows:
ip inspect max-incomplete host number block-time minutes
The default values are 50 half-open sessions and 0 minutes.
NOTE
A half-open session for TCP means that the three-way handshake has not yet completed, and for UDP means that the firewall has not detected any return traffic.
You can also address fragmentation attacks using CBAC by using the following command:
ip inspect name inspect-name fragment [max number timeout seconds]
Without this command, the first packet fragment is verified against any application layer CBAC checks, but any subsequent fragment can only be checked for IP layer information. When the fragment CBAC functionality is enabled, the Cisco IOS firewall maintains state information and checks the fragment sequence number, Offset field, and length to ensure that it is a valid fragment. The amount of memory dedicated to maintain the fragment state is limited by the max parameter to reduce the router becoming a victim of a potential DoS attack. To override the global timeouts for the specified protocol, specify the number of seconds for a different idle timeout.
Example 10-4 shows a sample firewall configuration that implements the following policy:
Device access is limited to the username security_geeks.
Device authentication is performed from the local database.
Antispoofing filters are in place for Internet connections.
Only services initiated within the corporate environment are allowed, except for FTP and World Wide Web services to the FTP server and World Wide Web server.
Some special debugging tools are allowed to be initiated from the Internet to the corporate network to make troubleshooting available for traveling staff.
SNMP access is allowed only from specified internal corporate SNMP servers.
NOTE
The filters that allow incoming IP traffic are constructed in such a way that specified services are denied unless specifically permitted. This arrangement allows for more control of traffic coming into the corporate network and is the recommended method for environments with severe security concerns.
Example 10-4. The IOS CBAC Firewall Configuration
! Ensure all vty login, line, and username passwords are encrypted ! with minimal encryption (7) unless configured as a secret ! that uses MD5 encryption. service password-encryption ! Disable access to minor TCP services such as echo, ! chargen, discard, and daytime. no service udp-small-servers ! Disable access to minor UDP services such as echo, ! chargen, and discard. no service tcp-small-servers hostname imafirewall ! The enable secret enable secret 5 $1$dLOD$QR.onv68q3326pzM.Zexj1 ! Disable other unnecessary services. no service finger no service pad no ip bootp server ! Set local database authentication. username security_geeks password 7 082C495C0012001E010F02 ! Allow for subnet zero networks ip subnet-zero ! Don't need source routing. no ip source-route ! The following commands define the inspection rule "primaryfw", ! allowing the specified protocols to be inspected. Note that Java ! applets will be permitted according to access list 66, defined later ! in this configuration. ip inspect name primaryfw cuseeme timeout 3600 ip inspect name primaryfw ftp timeout 3600 ip inspect name primaryfw http java-list 66 timeout 3600 ip inspect name primaryfw rcmd timeout 3600 ip inspect name primaryfw realaudio timeout 3600 ip inspect name primaryfw smtp timeout 3600 ip inspect name primaryfw tftp timeout 30 ip inspect name primaryfw udp timeout 15 ip inspect name primaryfw tcp timeout 3600 ! The following interface configuration applies the "primaryfw" ! inspection rule to inbound traffic at Ethernet 0. Since this interface ! is connected to the internal corporate network side of the firewall, ! traffic entering Ethernet 0 is actually exiting the trusted internal ! network. Applying the inspection rule to this interface causes all ! traffic going from the corporate network to the ! Internet to be inspected; return traffic will only be ! permitted back through the firewall if it is part of a session that ! began from within the corporate network. Also note that access list ! 101 is applied to inbound traffic at Ethernet 0. Any traffic that ! passes the access list will be inspected by CBAC. (Traffic blocked by ! the access list will not be inspected.) ! ! Access list 108 prevents spoofing by allowing only the traffic destined to ! the corporate network to go out the Ethernet 0 interface. interface Ethernet0 description To Corporate Network ip address 144.254.1.1 255.255.255.0 no ip directed-broadcast no ip proxy-arp ip inspect primaryfw in ip access-group 101 in ip access-group 108 out no ip route-cache no cdp enable interface Ethernet 1 description DMZ for ftp and www servers ip address 144.254.2.1 255.255.255.0 no ip directed broadcast ip access-group 102 in no ip route-cache no cdp enable interface Serial0 description Frame Relay to Internet no ip address ip broadcast-address 0.0.0.0 encapsulation frame-relay IETF no ip route-cache no arp frame-relay bandwidth 56 service-module 56k clock source line service-module 56k network-type dds frame-relay lmi-type ansi ! Note that the following interface configuration applies access list ! 111 to inbound traffic at the external serial interface. (Inbound ! traffic is entering the network.) When CBAC inspection occurs on ! traffic exiting the network, temporary openings will be added to ! access list 111 to allow returning traffic that is part of existing ! sessions. interface Serial0.1 point-to-point ip unnumbered Ethernet0 ip access-group 111 in no ip route-cache bandwidth 56 no cdp enable frame-relay interface-dlci 16 ! set up default route. ip classless ip route 0.0.0.0 0.0.0.0 Serial0.1 ! Filter such that only devices on this network have SNMP access. access-list 6 permit 144.254.9.0 0.0.0.255 ! The following access list defines "friendly" and "hostile" sites for ! Java applet blocking. Because Java applet blocking is defined in the ! inspection rule "primaryfw" and references access list 66, applets ! will be actively denied if they are from any of the "deny" addresses ! and allowed only if they are from either of the two "permit" networks. access-list 66 deny 172.19.1.203 access-list 66 deny 172.19.2.147 access-list 66 permit 172.18.0.0 0.1.255.255 access-list 66 permit 192.168.1.0 0.0.0.255 access-list 66 deny any ! The following access list 101 is applied to interface Ethernet 0 ! above. This access list permits all traffic that should be CBAC ! inspected, and also provides antispoofing. The access list is ! deliberately set up to deny unknown IP protocols because no such ! unknown protocols will be in legitimate use. access-list 101 permit tcp 144.254.0.0 0.0.255.255 any access-list 101 permit udp 144.254.0.0 0.0.255.255 any access-list 101 permit icmp 144.254.0.0 0.0.255.255 any access-list 101 deny ip any any ! Anti-spoof filters for my own network address access-list 102 permit ip 144.254.2.0 0.0.0.255 any access-list 108 permit ip any 144.254.0.0 0.0.255.255 ! The following access list 111 is applied to interface Serial 0.1 ! above. This access list filters traffic coming in from the external ! Internet side. When CBAC inspection occurs, temporary openings will be ! added to the beginning of this access list to allow return traffic ! back into the internal network. This access list should restrict ! traffic that will be inspected by CBAC. ! Antispoofing filters rfc1918 and my own network address access-list 111 deny ip 127.0.0.0.0 0.255.255.255 any access-list 111 deny ip 10.0.0.0 0.255.255.255 any access-list 111 deny ip 172.16.0.0 0.15.255.255 any access-list 111 deny ip 192.168.0.0 0.0.255.255 any access-list 111 deny ip 144.254.0.0 0.0.255.255 any ! Allow Internet traffic for ftp, ftp-data and www to ftp server ! and www server on dmz. access-list 111 permit ip any host 144.254.2.2 eq ftp access-list 111 permit ip any host 144.254.2.2 eq ftp-data access-list 111 permit ip any host 144.254.2.3 eq http ! Port 22 is used for SSH, i.e.encrypted, RSA-authenticated remote login. Can be ! used to securely access specified corporate host(s) from the Internet. access-list 111 permit tcp any 144.254.9.0 0.0.0.255 eq 22 ! Sometimes Enhanced IGRP is run on the Internet link. When you use ! an input access list, you have to explicitly allow control ! traffic. This could be more restrictive, but there would have to be ! entries for the Enhanced IGRP multicast as well as for the corporation's ! own unicast address. access-list 111 permit eigrp any any ! These are the ICMP types actually used... ! administratively-prohibited is useful when you're trying to figure out ! why you can't reach something you think you should be able to reach. access-list 111 permit icmp any 144.254.0.0 0.0.255.255 administratively-prohibited ! This allows network admins who may be traveling or otherwise coming ! in through the Internet to ping hosts at the corporate ! office. access-list 111 permit icmp any 144.254.0.0 0.0.255.255 echo ! This allows outgoing pings access-list 111 permit icmp any 144.254.0.0 0.0.255.255 echo-reply ! Path MTU discovery requires too-big messages access-list 111 permit icmp any 144.254.0.0 0.0.255.255 packet-too-big ! Outgoing traceroute requires time-exceeded messages to come back access-list 111 permit icmp any 144.254.0.0 0.0.255.255 time-exceeded ! Incoming traceroute access-list 111 permit icmp any 144.254.0.0 0.0.255.255 traceroute ! Permits all unreachables because if you are trying to debug ! things from the corporate network, you want to see them. ! If no debugging was ever done from the network, it would be more ! appropriate to permit only port unreachables or no unreachables at ! all. access-list 111 permit icmp any 144.254.0.0 0.0.255.255 unreachable ! Final deny all which logs all access list violations via syslog access-list 111 deny ip any any log no cdp run snmp-server community public RO 6 ! device access controls line con 0 exec-timeout 2 30 login authentication security_geeks line aux 0 no exec transport input none line vty 0 4 exec-timeout 2 30 login authentication security_geeks ! Logging commands service timestamps log datetime localtime show-timezone logging on logging 144.254.5.5 logging console information
The PIX (Private Internet Exchange) firewall is a standalone device that is totally dedicated for secure stateful packet inspection. Its logic is engineered around the Adaptive Security Algorithm (ASA), and every inbound packet is checked against the ASA and the connection state information.
Security levels are assigned to various interfaces on the PIX firewall to help identify the default behavior in a multi-interface unit. Different variants of PIX firewalls can support from 2 to 10 interfaces. The numeric security-level value can range from 0 to 100 and is configured with the following command:
nameif hardware_id if_name security_level
The default behavior between the PIX firewall interfaces is as follows:
Traffic coming in from an interface with a higher security level and going to a destination interface with a lower security level—. Allow all IP-based traffic unless specifically restricted by ACLs.
Traffic coming in from an interface with a lower security level and going to a destination interface with a higher security level—. Drop all packets unless specifically allowed.
Traffic coming in from an interface with same security level as the destination interface security level—. No communication between the two networks.
In addition, there are some further considerations:
The first interface has a default security level of 100 and is named inside.
The second interface has a security level of 0 and is named outside.
Only one network should have a security level of 100.
Only one network should have a security level of 0.
Multiple perimeter networks can exist.
If a command requires two interface names, always specify the more secure name first and the less secure name second (for example, Static [inside, outside]).
Figure 10-12 shows how you can deploy different security levels on a PIX firewall with multiple interfaces.
The inside network has a security level of 100; the outside interface has a security level of 0. In addition, there are two separate perimeter networks: one with a security level of 60, and another with a security level of 30. Example 10-5 shows the configuration.
In many corporate environments, internal users are allowed access to all Internet resources, but traffic coming in from the Internet undergoes closer scrutiny. If your security policy requires that outside users access inside hosts and servers, use the static command to specify which IP addresses are visible on the outside interfaces. The command creates a permanent mapping (sometimes referred to as a translation slot or xlate) between a local IP address and a global IP address.
NOTE
NAT is the mechanism by which a PIX firewall allows communication between its interfaces. By default, the PIX firewall protects corporate network addresses from being visible to an external network. The nat command is used to enable or disable address translation for one or more internal addresses. As a rule of thumb, for access from a higher security level interface to a lower security level interface, use the nat command. From a lower security level interface to a higher security level interface, use the static command.
The static command must be followed by the conduit command (or access-list command in newer software versions) to specify which services outside users can access on the internal servers. These commands take the following form:
static [(internal_if_name, external_if_name)] global_ip local_ip [netmask network_mask] [max_conns [em_limit]] [norandomseq] conduit permit|deny protocol global_ip global_mask [operator port [port]] foreign_ip foreign_mask [operator port [port]]
Together, a static and conduit (or access-list) statement pair create an exception to the PIX firewall adaptive security mechanism by permitting connections from one firewall network interface to access hosts on another.
The conduit command is being phased out in favor of the access-list command, which can take the following form:
access-list acl-ID permit|deny protocol {source_addr | local_addr} {source_mask | local_mask} [operator port [port]] {destination_addr | remote_addr} {destination_mask | remote_mask} [operator port [port]]
It is very similar to the Cisco IOS access-list command with one extremely important exception. The netmask is defined in the opposite way. For Cisco IOS ACLs, the netmask is represented by using 0s to represent the network number and 1s to represent the host number. For PIX firewall ACLs, the netmask is represented by what's referred to as the natural mask, where 1s are used to represent the network number and 0s are used to represent the host number. The following example shows the difference:
Cisco IOS: access-list dontbeconfused permit tcp any 144.254.0.0 0.0.255.255
PIX firewall: access-list dontbeconfused permit tcp any 144.254.0.0 255.255.0.0
With the access-list command, greater functionality will be introduced in future PIX products; it would, therefore, be wise for you to convert to using them now. If you have more than 19 access list entries, you can use the command access-list compiled to more efficiently process ACLs. Note that this command is supported only for PIX firewall platforms that have 16 MB of Flash memory.
Outbound access control is accomplished using ACLs. The ACLs are created with the outbound command and are based on the following information:
IP source address
IP destination address
IP protocol type
Destination port number
An outbound command requires the use of the apply command. The apply command enables you to specify whether the ACL applies to inside users' ability to start outbound connections with the apply command's outgoing_src option, or whether the ACL applies to inside users' ability to access servers on the outside network with the apply command's outgoing_dest option.
The commands take the following form:
outbound list_ID permit|deny ip_address [netmask [java|port[-port]]] [protocol] outbound list_ID except ip_address [netmask [java|port[-port]]] [protocol] apply [(if_name)] list_ID outgoing_src|outgoing_dest
The outbound controls are typically used for the following situations:
Whether one or more inside users can create outbound connections (single IP address, single subnet, or all IP addresses)
Whether inside users can access specific outside servers
Which services inside users can use for outbound connections and to access outside servers
Whether outbound connections can execute Java applets on the inside network
Example 10-6 shows a configuration that permits only outbound HTTP traffic from a specified source address.
Whenever you permit outside users access to your network, you should establish a user authentication and authorization system. The PIX has a feature called Cut-Thru-Proxy that enables authentication based on FTP, HTTP, or Telnet traffic and subsequent authorization for any allowed application traffic. The example in Figure 10-13 shows the use of this feature.
In the figure, any outbound FTP or HTTP traffic must be successfully authenticated before the connection is established, as illustrated in Example 10-7.
Example 10-7. PIX Firewall Cut-Thru-Proxy Configuration
aaa authentication ftp, http inbound 0.0.0.0 0.0.0.0 tacacs+ aaa authorization ftp, http inbound 0.0.0.0 0.0.0.0 tacacs-server host 144.254.5.9 sharedsecret
When an outside user tries to access the corporate FTP server, the following sequence of steps occur:
The user from the Internet initiates an HTTP or FTP request to a specified corporate server.
The firewall intercepts the connection and initiates the authentication process (in this case, using TACACS+).
If the user authenticates successfully, the firewall completes the HTTP or FTP connection to the specified corporate server.
The firewall forwards requests and responses without further intervention.
Example 10-8 shows a corresponding sample user profile on the TACACS+ server that authorizes an authenticated user to use FTP on 144.254.1.4 and HTTP on 144.254.1.3.
The PIX firewall has numerous advanced features, including the following:
Support for IPsec and L2TP/PPTP-based virtual private networks (VPNs)
Flood Guard and Fragmentation Guard to protect against DoS attacks
Mail Guard to protect against attacks on a mail server
Support for high-performance URL filtering via integration with WebSense-based URL filtering solutions
AAA capabilities for scalable authentication, authorization, and accounting
Support for advanced Voice over IP standards
It is beyond the scope of this book to describe the PIX firewall functionality in detail, and only a brief introduction has been offered to familiarize the reader with the most basic commands. The book Cisco Secure PIX Firewalls (Cisco Press, 2001), by David W. Chapman, Jr. and Andy Fox, provides a comprehensive description of the PIX firewall. Chapter 12 in this book describes VPN scenarios and shows configuration examples using IPsec that also include the PIX firewall.
In this scenario, the Cisco IOS router is used as the screening router to provide basic filtering of traffic coming from the Internet. The PIX firewall provides the more robust firewall features, as shown in Figure 10-14.
The sample configurations in Examples 10-9 and 10-10 depict the implementation of the following Internet access security policy:
Device (screening router and firewall) access is through TACACS+ authentication and authorization.
The screening router has simple antispoofing filters.
Two illegal networks (192.168.0.0 and 10.0.0.0) must make use of NAT to convert to the legal address given by the ISP of 192.150.50.0.
Hosts on the 10.0.0.0 network can access everything.
Hosts on the 192.168.0.0 network can access the Internet but cannot access hosts on the 10.0.0.0 network.
Only Internet traffic from 144.254.0.0 can access the FTP server whose illegal 192.168.0.6 address must be assigned the legal address 192.150.50.6.
The FTP traffic must be authenticated using TACACS+.
All Internet web (HTTP) traffic is directed to host 192.168.0.2. (It must be assigned the legal address of 192.150.50.9.)
All outbound web traffic is sent to do a URL check by way of the WebSense server.
All Internet mail (SMTP) traffic is directed to host 10.0.1.99. (It must be assigned the legal address of 192.150.50.7.)
Example 10-9. Configuration of Cisco IOS Screening Router
! Ensure all vty login, line, and username passwords are encrypted ! with minimal encryption (7) unless configured as a secret ! that uses MD5 encryption. service password-encryption ! Disable access to minor TCP services such as echo, ! chargen, discard, and daytime. no service udp-small-servers ! Disable access to minor UDP services such as echo, ! chargen, and discard. no service tcp-small-servers hostname screen enable secret 5 $1$dLOD$QR.onv68q3326pzM.Zexj1 no service finger no service pad no ip bootp server no ip source-route ! Configure TACACS+ authentication as default - for users logging in as ! staff, there is a local database authentication in the event that the ! TACACS+ server is unavailable. aaa new-model aaa authentication login default tacacs+ aaa authentication login staff tacacs+ local aaa authorization exec tacacs+ local ! Interim accounting records will be sent every time there is ! new information to report ! accounting for all exec terminal sessions. aaa accounting update newinfo aaa accounting exec start-stop tacacs+ ! Set local database authentication. username staff password 7 082C495C0012001E010F02 ! Configure the interfaces. interface Serial 0/0 description to the Internet ip address 161.71.73.33 255.255.255.248 ip access-group 109 in interface Ethernet1/0 description To Corporate Network ip address 192.150.50.1 255.255.255.0 no ip directed-broadcast no ip proxy-arp ip access-group 108 in no ip route-cache no cdp enable ! Antispoof filter for internal network access-list 108 permit ip 192.150.50.0 0.0.0.255 any ! Antispoof filters for rfc1918 addresses. access-list 109 deny ip 127.0.0.0 0.255.255.255 any access-list 109 deny ip 10.0.0.0 0.255.255.255 any access-list 109 deny ip 172.16.0.0 0.15.255.255 any access-list 109 deny ip 192.168.0.0 0.0.255.255 any ! Allow any tcp traffic that has been established from the corporate network. access-list 109 permit tcp any any established ! allow Internet traffic for ftp and ftp-data only from network 144.254.0.0 access-list 109 permit tcp 144.254.0.0 0.0.255.255 host 192.150.50.8 eq ftp access-list 109 permit tcp 144.254.0.0 0.0.255.255 host 192.150.50.8 eq ftp-data ! Allow Internet traffic for smtp and www server to specific servers. access-list 109 permit tcp any host 192.150.50.9 eq http access-list 109 permit tcp any host 192.150.50.7 eq smtp ! Sometimes Enhanced IGRP is run on the Internet link. When you use ! an input access list, you have to explicitly allow control ! traffic. This could be more restrictive, but there would have to be ! entries for the Enhanced IGRP multicast as well as for the corporation's ! own unicast address. access-list 109 permit eigrp any any ! These are the ICMP types actually used... ! administratively-prohibited is useful when you're trying to figure out ! why you can't reach something you think you should be able to reach. access-list 109 permit icmp any 192.150.50.0 0.0.0.255 administratively-prohibited ! This allows network admins who may be traveling or otherwise coming ! in through the Internet to ping hosts at the corporate ! office: access-list 109 permit icmp any 192.150.50.0 0.0.0.255 echo ! This allows outgoing pings. access-list 109 permit icmp any 192.150.50.0 0.0.0.255 echo-reply ! Path MTU discovery requires too-big messages. access-list 109 permit icmp any 192.150.50.0 0.0.0.255 packet-too-big ! Outgoing traceroute requires time-exceeded messages to come back. access-list 109 permit icmp any 192.150.50.0 0.0.0.255 time-exceeded ! Incoming traceroute access-list 109 permit icmp any 192.150.50.0 0.0.0.255 traceroute ! Permits all unreachables because if you are trying to debug ! things from the corporate network, you want to see them. ! If no debugging was ever done from the network, it would be more ! appropriate to permit only port unreachables or no unreachables at ! all. access-list 109 permit icmp any 192.150.50.0 0.0.0.255 unreachable ! Final deny all which logs all access list violations via syslog access-list 109 deny ip any any log no cdp run ! configure tacacs+ parameters tacacs-server host 192.150.50.10 tacacs-server key thisisakey ! configure device access. line con 0 exec-timeout 2 30 login authentication staff line aux 0 no exec transport input none line vty 0 4 exec-timeout 2 30 login authentication default ! Configure logging. service timestamps log datetime localtime show-timezone logging on logging 192.150.50.11 logging console information
Example 10-10. Configuration of PIX Firewall
! Sets the security levels for each interface, specifies that each ! interface uses Ethernet, and assigns IP addresses and network ! masks. nameif ethernet0 outside security0 nameif ethernet1 inside security100 nameif ethernet2 dmz security50 interface ethernet0 auto interface ethernet1 auto interface ethernet2 auto ip address outside 192.150.50.3 255.255.255.255 ip address inside 10.0.0.1 255.255.255.0 ip address dmz 192.168.0.1 255.255.255.0 ! Specifies the host name for the PIX firewall. hostname pixfirewall ! Define enable password and Telnet password. enable password BjeuCKspwqCc94Ss encrypted passwd nU3DFZzS7jF1jYc5 encrypted ! The following performs defined protocol security checks. fixup protocol ftp 21 fixup protocol http 80 fixup protocol h323 1720 fixup protocol rsh 514 fixup protocol smtp 25 fixup protocol sqlnet 1521 ! ! Enables use of text strings instead of IP addresses. This makes your ! configuration files more readable. names ! Enables paging so that if 24 lines of information ! display, PIX firewall pauses the listing and prompts you ! to continue. pager lines 24 ! The logging host command specifies which host runs a syslog server. ! This command also causes the PIX firewall to start sending syslog ! messages to that host. The logging trap command sets syslog to send ! all possible messages to the syslog host. The no logging console ! command disables displaying messages to the console. logging on logging host 10.0.1.100 logging trap 7 logging facility 20 no logging console ! Sets the ARP timeout to 14,400 seconds (four hours). ! Entries are kept in the ARP table for four hours before ! they are flushed. Four hours is the standard default value ! for ARP timeouts. arp timeout 14400 ! Create a pool of addresses to be used with NAT. global (outside) 1 192.150.50.15-192.150.50.250 netmask 255.255.255.0 ! Enable IP communications between hosts on the 10.0.0.0 network and host on ! either the Internet or the 192.168.0.0 network. For communication to the ! Internet, the source IP address gets substituted with an address from the ! global pool. nat (inside) 1 10.0.0.0 255.0.0.0 0 0 ! Enables IP communications between hosts on the 192.168.0.0 network and ! the Internet. Any address starting with 192.168.0 will be substituted ! with an address from the global pool nat (dmz) 1 192.168.0.0 255.255.255.0 0 0 ! Define static translations for the FTP server, web server, SMTP server, ! TACACS+ server, and syslog server. static (dmz, outside) 192.150.50.6 192.168.0.6 netmask 255.255.255.255 0 0 static (dmz, outside) 192.150.50.9 192.168.0.2 netmask 255.255.255.255 0 0 static (inside, outside) 192.150.50.7 10.0.1.99 netmask 255.255.255.255 0 0 static (inside, outside) 192.150.50.10 10.0.0.100 netmask 255.255.255.255 0 0 static (inside, outside) 192.150.50.11 10.0.6.50 netmask 255.255.255.255 0 0 ! Allows packets from 10.0.0.0 network to go to the 192.168.0.0 network. statix (inside, dmz) 10.0.0.0 192.168.0.0 netmask 255.0.0.0 0 0 ! Enables www access to 192.168.0.2 - this command requires the static command ! above to know proper translated address. conduit permit tcp host 192.150.50.9 eq www any ! Enables SMTP access to 10.0.1.99 - this command requires the static command ! above to know proper translated address. conduit permit tcp host 192.150.50.7 eq smtp any ! Allow FTP access from hosts from 144.254.0.0 network. conduit permit tcp host 192.150.50.6 eq ftp 144.254.0.0 255.255.0.0 ! Sets RIP listening attributes. The three no rip interface passive lines ! cause the PIX firewall to not listen to RIP broadcasts on each interface. ! The no rip interface default lines causes PIX firewall to not ! broadcast a default route on any interface. no rip inside passive no rip outside passive no rip dmz passive no rip inside default no rip outside default no rip dmz default ! Sets the outside default route to the router attached to the Internet. route outside 0.0.0.0 0.0.0.0 192.150.50.1 1 ! Default values for the maximum duration that PIX firewall resources ! can remain idle until being freed. To improve system performance, ! you can set the xlate and conn timers from 24 hours to 1 hour. timeout xlate 24:00:00 conn 12:00:00 udp 0:02:00 timeout rpc 0:10:00 h323 0:05:00 uauth 0:05:00 ! Use WebSense server which has address 10.0.6.80 - all outbound URL requests are ! sent to the WebSense server. url-server (inside) host 10.0.6.80 timeout 5 filter url http 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 ! Authenticate FTP traffic via TACACS+. tacacs--server host 10.0.6.50 thisisakey aaa authentication ftp inbound 192.168.0.6 255.255.255.255 144.254.0.0 255.255.0.0 ! Give Telnet access to PIX firewall console to inside hosts on 10.0.8.0 subnet. telnet 10.0.8.0 255.255.255.0 ! Sets the maximum transmission unit value for Ethernet access. mtu outside 1500 mtu inside 1500 mtu dmz 1500
This chapter discussed general architectures for securing Internet access to the corporate network and showed two specific implementations that illustrate some configurations when using Cisco devices. Many variants are possible, depending on how open or restrictive your corporate environment is. It is often best to permit only IP services that are supported in the corporation and to deny all others. This arrangement allows for fairly strict control of traffic entering or leaving the corporate network through the Internet connection. For more robust Internet access monitoring and control, it is usually a good idea to include some kind of intrusion detection system and active audit component into the Internet access implementation architecture.