Defining a site security policy is one of the basic building blocks of designing an enterprise network. It is as critical as defining bandwidth requirements or redundancy needs. RFC 2196, The Site Security Handbook, defines a site security policy as follows:
A security policy is a formal statement of rules by which people who are given access to an organization's technology and information assets must abide.
The policy should be formed with representation from key corporate individuals: management members who have budget and policy authority, technical staff who know what can and cannot be supported, and legal personnel who know the legal ramifications of various policy choices.
Benefits of creating a corporate security policy include the following:
Providing a framework for implementing security features in the network infrastructure
Providing a process by which you can audit existing network security
Identifying procedures that are considered expedient, prudent, advantageous, and productive
Enabling global security implementation and enforcement
Creating a basis for legal action if necessary
A successful security policy must be committed to paper and show that the issues have been well thought out. Following are some key characteristics of a good security policy:
It must be capable of being implemented technically.
It must be capable of being implemented organizationally.
It must be enforceable with security tools where appropriate and with sanctions where prevention is not technically feasible.
It must clearly define the areas of responsibility for the users, administrators, and management.
It must be flexible and adaptable to changing environments.
A security policy should not determine how a business operates; the nature of the business should dictate the security policy. Defining a company's security policy can seem difficult, but by defining the policy before choosing security methods, organizations can avoid having to redesign security methodologies after they are implemented.
This chapter focuses on how to start the process of defining a corporate security policy. Risk assessment and asset identification are reviewed, along with other considerations for forming a policy. After identifying the global corporate security considerations, you can define a security policy specific to the corporate network and determine the implementation details.
Many companies have existing guidelines for security procedures in a corporate environment. These can be in the form of a statement of conduct rules for employees—which, to some extent, outlines how employees are to deal with confidential technology, intellectual property rights, and other confidential corporate information. These guidelines can be a basis for establishing a strategy for an enterprise network security policy because they establish corporate rules for what information is valuable to the company from a business point of view. The following is an example of a corporate statement of conduct.
For existing computer networks, in addition to the corporate statement of conduct, an anonymous user survey can be conducted to gather information on the possible circumvention of security procedures. This survey can result in invaluable information from people who may be circumventing security procedures for productivity reasons without any malicious intent. The circumvented security procedures can then be re-evaluated to determine how the policy can reflect security measures that can practically be implemented. Following is a sample survey questionnaire you can use.
It is important to recognize that the business opportunities are what drive the need for security procedures in the first place. If a corporation does not have many secrets to guard—perhaps because all the information and data available on the network is nonconfidential and freely available—security procedures may be minimal. However, the more likely it is that a security breach will have negative business implications resulting in lost revenues, the more stringent the security policies should be.
Risk management is a systematic approach to determine appropriate corporate security measures. How to address security, where to address security, and the type and strength of security controls requires considerable thought.
Before the proliferation of computer networks, confidential data was kept under lock and key, and people were trusted to keep confidential documents in a safe place. In extremely secure environments of the past, such as where classified work for the Department of Defense (DoD) was carried out, your briefcase, purse, and so on were inspected every night on the way out the door. You could not leave the building with any magnetic media or classified computer printouts. (The printers attached to secured machines used specially colored paper.)
In today's environments, all those physical security checks are made obsolete by the computer network. Why try to smuggle a magnetic tape out of the building when you can encrypt it and send it out in e-mail? Computer networks have created an environment in which data can be accessed, moved, or destroyed electronically if there are no electronic lock-and-key mechanisms in place to safeguard the corporation's secrets. New avenues of risk are created and must be managed.
Risk assessment is a combination of identifying critical assets, placing a value on the asset, and determining the likelihood of security breaches. When the critical resources have been identified and the likelihood and costs associated with the compromise, destruction, or unavailability of these critical resources have been assessed, a decision can be made as to what level of risk is acceptable to the company. The result of the risk assessment is unique to the organization because it depends on the business needs, trustworthiness of its users, and the location of critical assets.
It is impossible to know who might be an organization's potential enemy. A better approach is for the organization to know itself. Companies must understand what they want to protect, what access is needed to those assets, and how these considerations work together. Companies should be more concerned about their assets and their associated value than about an attacker's motivation.
The corporation must identify the things that require protection. Table 6-1 lists some possible network assets to take into consideration.
Table 6-1. Network Assets
Asset | Description |
|---|---|
Workstations, personal computers, printers, routers, switches, modems, terminal servers, firewalls, remote access servers, and application-specific servers | |
Source programs, object programs, utilities, diagnostic programs, operating systems, and communication programs | |
Data stored online and archived offline, backups, audit logs, databases, and data in transit over communication media | |
Users, administrators, and hardware maintainers | |
Software programs, internal hardware and software evaluations, systems, and local administrative procedures |
The inventory of the corporation's assets should be conducted globally to ensure consistent handling and evaluation of corporate assets.
Placing values on corporate assets can be a very subjective process. For intangible assets—usually some form of software, data, or documentation—it can be useful to represent the value in terms of importance or criticality. In this way, the relative loss of the asset becomes more important than placing a “correct” value on it. The value of tangible assets can be based on replacement value and, as in the case of intangible assets, the immediate impact of the loss and the consequences of a loss.
The replacement value can encompass the monetary cost of purchasing security hardware (such as firewalls and encrypting devices) and software (such as one-time password generators and audit tools) and the cost of retraining security personnel. For data loss, the immediate impact caused by inaccessible or corrupt data may be a missed presentation deadline that consequently results in the account being lost.
Estimating the worth of data can be difficult in some situations—especially when an established research environment has to evolve to meet changing business needs. Business needs may place a higher value on some data because of its potential patent royalty or other monetary gains. Classifying data according to varying levels of criticality can be a preliminary step in establishing its value. A simple rating system of high, medium, and low can be the starting point for evaluating the relative criticality of data. The data can take many forms, including the following:
Administrative data—. Correspondence and such information as property records and personnel information that is generally available to the public.
Financial data—. Budgeting and expenditure information relating to corporate operations.
Client data—. Information relating to the client that is of a personal nature, or information developed as a result of tests, observations, or counseling.
Research data—. Information resulting from, or used to support, any corporate research activity.
Proprietary data—. Information that cannot be released to the public without the permission of the owner.
Table 6-2 shows an example of how you can classify different types of data and apply a criticality rating.
Table 6-2. Data Classification
NOTE
Some data is more critical because of its time sensitivity. For example, impending patent data and new product data are highly sensitive either until the patent is applied for or until the product is announced.
When the assets have been identified and valued, it is time to start looking at the likelihood of security breaches.
After identifying the network assets, you have to determine the possible threats to the assets and the likelihood that the asset is vulnerable to a given threat. A threat can be any person, object, or event that, if realized, can potentially cause damage to the network or networked device. Threats can be malicious (such as the intentional modification of sensitive information) or accidental (such as an error in a calculation or the accidental deletion of a file).
A vulnerability is a weakness in a network that can be exploited by a threat. For example, unauthorized access (the threat) to the network can occur by an outsider guessing an obvious password. The vulnerability exploited is the poor password choice made by a user. Reducing or eliminating the vulnerable aspects of the network can reduce or eliminate the risk of threats to the network. For example, a tool that can help users choose robust passwords may reduce the chance that users will select poor passwords and, thus, reduce the threat of unauthorized network access.
The threats, as discussed in Chapter 5, “Threats in an Enterprise Network,” are usually in the following forms:
Eavesdropping and information theft
Disabling access to network resources (denial-of-service attacks)
Unauthorized access to resources
Data manipulation
If these threats are realized and networking devices or data is compromised, what are the immediate impacts and further consequences? Will it result in embarrassment or bankruptcy? The greater the possibility of bankruptcy, the more stringent the security measures should be.
The following sections consider corporate impacts and consequences in the event of data compromise, loss of data integrity, and unavailability of networked resources.
Any information stored or transferred electronically can potentially be stolen. Data can be stolen if an intruder has unauthorized access to a system or can eavesdrop on confidential data exchanges. Depending on the type of information disclosed, the results can range from inconsequential to catastrophic. In financial institutions, monetary transactions can cause great loss to the institution itself or to customers who may represent loss of revenue if they take their business elsewhere.
You should create a priority list of the information that is most valuable to the corporation. Data pertaining to customer accounts, personnel data, and data related to finances is almost always extremely sensitive and, therefore, valuable. The security policy should reflect where different classes of sensitive data are stored, how the data is stored, and who has access to the different classes of data.
Loss of data integrity can be extremely costly to many corporations. Loss of integrity can result in negative press and, therefore, loss of reputation—which translates into loss of customers and revenue. An obvious example is in the financial environment: A bank or other financial institution would have a large probability of bankruptcy if it were to become publicly known that any account data had been compromised. The public would be hard-pressed to place trust in that institution to reliably handle its financial business.
In addition to the losses incurred from a negative reputation, the costs are extremely high to investigate and restore the compromised data. The data has to be restored from a backup, if a backup exists, and an investigation must be performed to determine whether, when, and how the data was compromised. The hours of work required to analyze and restore any compromised data can be quite numerous.
When determining possible security risks, the corporation should take into account all the ways that integrity can be compromised. Data integrity goes right to the heart of your operation:
How you perform backups
Where you store the backups
How you physically secure live data
Who has physical access to the media that contains your data
Insurance underwriters, for example, confirm that four out of five companies that lose files in a fire go out of business because they cannot recover from the loss. Because so many businesses are now running with all their “actual” data on magnetic media, imagine what someone could do to your business just by noting that you don't make regular backups and that you leave your computers out in the open where he can crash your disks? The security policy should clearly state how to best preserve data integrity for its valuable assets.
When networked resources become unavailable, the resulting business losses can be catastrophic. In today's environment, in which businesses rely more and more on business transactions over computer networks, if critical systems are inaccessible, losses can be tallied in the millions of dollars.
Businesses must estimate the costs of possible system downtime caused by equipment failure, acts of nature (such as flooding, fire, and lightning), or some denial-of-service (DoS) attack. Network resources can become unavailable because of system upgrades that introduce new software bugs, faulty configurations, or inadequate capacity planning. This area is closely coupled with system reliability and redundancy, which is why a security policy should be established while the network is being designed.
For all possible threats, you must evaluate the risk. Many methodologies are available to measure risk. The common approaches are to define risk in quantitative terms, qualitative terms, or a combination of both. Quantitative risk evaluation uses empirical data and known probabilities and statistics. Qualitative risk analysis uses an intuitive assessment. Regardless of the mechanism you use, the important aspect is that how you quantify the loss and the likelihood of the loss occurring should be consistent and meaningful to the people who make the decisions about how to guard against the risks.
NOTE
Automatic risk analysis tools are available in many sophisticated spreadsheet software packages. Because of a lack of standards in how to perform risk analysis, however, the manner in which most losses and the likelihood of the losses are quantified and are represented should be clearly understood. If the methodology is fully understood and acceptable, an automatic risk analysis tool may be an adequate solution for evaluating risk.
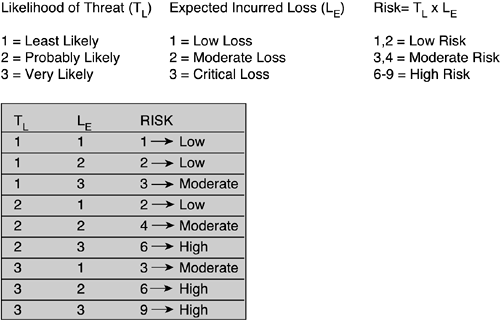
Figure 6-1 shows a simple example of calculating risk by using the relative likelihood that the threat can occur and the value of the expected incurred loss.
A more specific example (taken from an existing LAN administration guide used at the National Institutes of Health) is given in Table 6-3. This table tries to determine how critical security considerations are for different LANs using a combination of network importance, the probability of a harmful occurrence, and the probability that a degradation of LAN performance will occur after the harmful occurrence is in effect.
Table 6-3. Relative Risk Calculation for LANs
LAN | A[1] | I[1] | C[1] | NI[2] | PO[3] | PD[4] | RR[5] |
|---|---|---|---|---|---|---|---|
Admin | 2 | 3 | 1 | 6 | Very low 0.1 | Low 0.3 | 3.8 |
Eng | 2 | 3 | 2 | 8 | Moderate 0.5 | Moderate 0.5 | 2.0 |
Finance | 2 | 3 | 3 | 18 | Low 0.3 | Low 0.3 | 8.8 |
[1] A = Availability, I = Integrity, and C = Confidentiality [2] NI = Network Importance. NI is the value of A multiplied by the value of I multiplied by the value of C. [3] PO= Prevent an Occurrence. PO is determined by considering the number of users, previous accreditation, frequency of backups, and compliance with mandatory safeguards requirements. [4] PD = Prevent Degradation. The capability to PD of A, I, and C for a LAN in the event of a harmful occurrence is determined using the relative need to protect the LAN's availability, integrity, and confidentiality with regard to the sensitivity of data and the criticality of the data-processing capability. [5] RR = Relative Risk. RR equals NI multiplied by (1–PO) multiplied by (1–PD). | |||||||
Establishing network importance is significant to managers because doing so facilitates the allocation of resources (to implement additional security services) to protect the assets that are part of the LAN. In terms of potential vulnerability, the more important a network is to a corporation, the greater the percentage of available resources that should be devoted to its protection.
Network importance is a term used to describe the relative importance of a LAN with regard to other corporate LANs. A measure of the RR associated with a harmful occurrence can be expressed as follows:
RR = NI × [(1 – PO) × (1 – PD)]
In this expression, NI is network importance, (1 – PO) is proportional to the probability of a harmful occurrence, and (1 – PD) is proportional to the probability that a degradation in LAN performance will result after an occurrence has been initiated.
The importance of the RR calculation is that it provides management with the information required to rank the risk associated with the various corporate networks relative to one another. This ranking of network importance can facilitate the allocation of resources for the implementation of additional safeguards.
In Table 6-3, the left column identifies the evaluated LANs. The next three columns record the ratings for availability, integrity, and confidentiality. The NI column is completed by multiplying the values in the previous three columns. This number establishes the relative importance of each LAN based on the need to protect the LAN. The numbers recorded under both the PO and PD columns are determined using those qualitative ratings (very low, low, moderate, high, very high) and the following scale:
Very low | 0.1 |
Low | 0.3 |
Moderate | 0.5 |
High | 0.7 |
Very high | 0.9 |
The RR column is calculated using the following equation:
RR = NI × [(1 – PO) × (1 – PD)]
Note that the magnitude of the difference in RR between the various LANs is not important. What is important is the relative value. The number reflected in the right column of Table 6-3 represents relative risk such that the higher the number, the greater the relative risk. Thus, the LAN with the highest number represents the greatest relative risk to the corporation.
For the LANs listed in Table 6-3, the financial LAN has the most risk and the engineering LAN has the least risk. Under normal circumstances, the higher the position of the LAN on the relative scale, the higher its priority should be for allocation of protection resources to implement additional safeguards. In some cases, however, resources are not available to implement all the needed upgrades. So, a balance must be achieved in which the resources available are applied to achieve the greatest risk reduction.
After assessing all the risks, the corporation must determine how much risk it is willing to accept and to what degree the assets should be protected. Risk mitigation is the process of selecting appropriate controls to reduce risk to an acceptable level. The level of acceptable risk is determined by comparing the risk of security hole exposure to the cost of implementing and enforcing the security policy. If some threats are highly unlikely, it may not be worth the cost of creating a tight security policy to protect the assets. A good rule to follow is to assess the cost of certain losses and not to spend more to protect something than it is actually worth.
To develop an acceptable security policy, you must consider a number of costs to ensure that the policy is enforceable. There are performance costs to be considered because both encryption and decryption take time and processing power. An offhand decision to encrypt all traffic may result in severely degraded performance everywhere; that policy may have to be re-evaluated. There are also opportunity costs to be considered. What are the lost opportunities if your company moves more slowly than the competition because of hampered communication and the increased overhead that security procedures—not to mention security audits—impose?
The costs of implementing and managing security procedures must be weighed against the cost of potential benefits. It must be understood that security measures do not make it impossible for an unauthorized user to access information and perform unauthorized tasks on a network computer system; security measures can only make it harder for unauthorized access to occur. A very simplistic example is that of packet filters. Even if the corporation simply implemented packet filters to accept outside data traffic from specified networks, the intruder must first find out which IP network addresses were accepted before attempting to gain access to the internal corporate network through those addresses. Perhaps this may not be very difficult, but it can be a deterrent to some random, bored intruders looking for something to do in their spare time.
A more sophisticated example is that of trying to crack encrypted traffic. Even a weak algorithm and a short key can stop some attackers from gaining access to valued information. A stronger algorithm and a longer key takes more sophisticated machines and more time to break. The point is to slow down the attack and increase the cost of the attack until it becomes too expensive to be worthwhile for the intruder.
Now that you have learned to deal with risk management, it is time to start looking at additional issues that relate to creating the security policy for an enterprise network infrastructure. Special areas of more stringent security needs are places most vulnerable to attacks, such as network interconnections, remote dialup access points, remote wireless access points, and critical network infrastructure devices and servers.
It is helpful to divide the corporate network into separate components that can be addressed separately. You also need a framework for the security policy that addresses all the elements of a security architecture. The framework must be adhered to by all areas of the corporation to ensure a consistent security approach throughout the enterprise environment.
Traditionally, in the days when network environments consisted primarily of a centralized point-to-point architecture with predetermined information paths, security was fairly straightforward. Securing the link itself provided reasonable assurance of maintaining the integrity, access, and privacy of the information.
Modern enterprise internetworks provide a tremendous opportunity for corporations to remain competitive while increasing overall efficiency. This opportunity comes with a cost. Today's open networking technologies pose a threat to the overall security of the enterprise. This openness can mean that a corporation has little control over who accesses its information resources and the path over which that information flows. Traditional security systems based on point-to-point, nonpacketized transmission media simply were not designed to address the evolving WAN and LAN technologies at the heart of today's enterprise network in which data travels across public networks.
When creating a security policy, you must balance easy accessibility of information with adequate mechanisms of identifying authorized users, ensuring data integrity, and confidentiality. A security policy must be enforceable, both technically and organizationally. It is usually easiest to break an enterprise network into three distinct components, as shown in Figure 6-2:
The main campus infrastructure
Remote access connectivity (this includes dial-in, wireless, and virtual private networking)
Internet connectivity
The main campus infrastructure typically is located within a constrained geographic area and is the core of the enterprise network. Remote access is a broad concept that comprises of all the methods that may be used to connect remote branches, telecommuters, and mobile dialup users to the corporate infrastructure. Therefore, remote access consists of Public Switched Telephone Network (PSTN) or Integrated Services Digital Network (ISDN) services, wireless LANs, or virtual private networks (VPNs). The Internet access connects the main campus through a local Internet service provider (ISP) to the Internet.
NOTE
The astute reader may be wondering how remote access and Internet access actually differ. Remote access typically deals with providing inbound connectivity to the corporate network resources, whereas Internet connectivity deals with providing outbound connectivity to resources outside the corporate network. Both can be referred to as the network edge.
Each of these three components may have different security needs. It is important to have a global corporate security framework in place that addresses all the elements of a security architecture so that individual policies can be consistent with the overall site security architecture. For example, having a strong policy with regard to Internet access and having weak restrictions on modem usage is inconsistent with an overall philosophy of strong security restrictions on external access.
The global framework must include the following elements of a security architecture:
Identity
Integrity
Confidentiality
Availability
Audit
Each of these elements must be taken into consideration when determining the corporate policy.
In this book, identity is defined as the element of the security architecture that encompasses both authentication and authorization. Authentication answers the question, “Who are you and where are you?” Authorization answers the question, “What are you allowed to access?” Identity mechanisms must be carefully deployed because even the most careful of security policies can be circumvented if the implementations are hard to use. A classic example is that of passwords or personal identification code (PIN) numbers scribbled on a sticky pad and attached to the computer monitor or telephone—a real solution for the user who has to remember a multitude of passwords.
Another example of poorly implemented security is when employees use an easily guessed password so that they don't have to write it down. An ad hoc study at Bell Labs some years ago found that a surprisingly high percentage of the people logging on to systems chose a password that was a child's name, dog's name, wife's name, and so on. Corporations can install systems that ensure that the passwords selected by its employees are not proper names, words found in the dictionary, or other logical sequences of characters. However, verification and authorization systems that are cumbersome or unnecessarily redundant can frustrate users and should be avoided.
Companies must create appropriate barriers inside their systems so that if intruders do access one part of the corporate environment, they do not automatically have access to the rest of it. Just as the creation of security barriers applies to physical buildings (access to the building itself does not let you access every room in the building), it should also apply to network access. That is, the computer network infrastructure should be partitioned to provide as much protection as necessary for specific components of the network. Although maintaining a high level of security on the entire corporate environment is difficult, it is often possible to do so for a smaller sensitive component.
In this book, integrity is the element of the security architecture that encompasses network infrastructure device security (physical and logical access) to protect against undesirable changes in the network infrastructure and perimeter security to ensure that any traffic traversing the network is valid.
Physical access to a computer (or router or switch or firewall) usually gives a sufficiently sophisticated user total control over that device. Physical access to a network link usually allows a person to tap into that link, jam it, or inject traffic into it. Software security measures can often be circumvented when physical access to the hardware is not controlled. Therefore, for corporate facilities, physical security should be based on security guards, closed-circuit television, and card-key entry systems. With these measures in place, organizations can feel confident that within their physical facilities, assets are protected and high user productivity is maintained.
Logical access security refers to providing identity mechanisms (authentication and authorization) that must be satisfied before the user is allowed access to integral network infrastructure components (such as routers and firewalls). The logical access can be obtained in any number of ways, including access via console ports, virtual terminal ports (Telnet or Secure Shell [SSH]), auxiliary ports, Simple Network Management Protocol (SNMP), or web-based access. Perimeter security deals with firewall-type functionality, determining which traffic is permitted or denied from various areas of the network. Often, firewalls are placed between the Internet and the main campus or between the dialup connection and the main campus.
Confidentiality is the element of the security architecture that ensures that data communication is kept private between the sender and receiver of information. A strong policy statement should dictate to users the types of information deemed sensitive enough to warrant encryption. A program-level policy may dictate the broad categories of information that must be stringently protected, whereas a system-level policy may detail the specific types of information and the specific environments that warrant encryption protection.
At whatever level the policy is dictated, the decision to use encryption should be made by the authority within the organization charged with ensuring protection of sensitive information. If a strong policy that defines what information to encrypt does not exist, the owner of the data should ultimately make the decision about whether to encrypt information.
Availability is the process of ensuring that all critical resources are accessible when needed. Keeping data available means that you must have planned system upgrades and configuration changes that are fully tested to avoid catastrophic surprises caused by software bugs or misconfigurations.
Physical security and logical security are also part of ensuring availability. Physical security ensures that no malicious tampering can take place and that acts of nature will not cause systems to be inaccessible. It also ensures that hardware failures are handled in a timely manner. Logical security ensures that traffic can be rerouted and that malicious software threats can be deterred.
The audit element of the security architecture is necessary to verify and monitor the corporate security policy. A software audit verifies the correct implementation of the security policy in the corporate network infrastructure. Subsequent logging and monitoring of events can help detect any unusual behavior and possible intrusions.
To test the effectiveness of the security infrastructure, security auditing should occur frequently and at regular intervals. Auditing should include new system installation checks, methods to discover possible malicious insider activity, possible presence of a specific class of problems (DoS attacks), and overall compliance with the site security policy.
An audit log, generated by all the various operating systems running in your infrastructure, can be used to determine the extent of the damage from a successful attack. Audit trails are most often put to use after the fact to reconstruct what happened during damage assessment. The problem to avoid is logging every event such that the amount of data to sift through becomes insurmountable. If you log too much data and an intrusion does occur, that intrusion will definitely be logged—along with hundreds of other insignificant events. The intrusion will most likely remain undetected by the people responsible for detecting such things because the intrusion is hidden under a mountain of other data being generated by the system.
NOTE
If your network or system is designed and implemented well, think about logging the kinds of activity that would most likely indicate a first-stage attack. Don't log every event—just the unusual ones. This information can give you a warning that something is amiss without burying you in too much inconsequential detail.
When creating data log files, consider the following points:
Use a program to filter through the audit data and bring to your attention the truly serious issues.
Do not audit every little issue in your network or system.
Understanding how a system normally functions, knowing what is expected and unexpected behavior, and being familiar with how devices are usually used can help the organization detect security problems. Noticing unusual events can help catch intruders before they can damage the system. Software auditing tools can help companies detect, log, and track those unusual events. In addition, sophisticated intrusion detection systems (IDSs) may be deployed.
The security policy should address personnel security considerations as well. Personnel security issues include processes and procedures for establishing identity confirmation, privilege rights required to access certain information, accountability for the proper use and security of the systems being accessed, and proper training to make sure that employees understand and fulfill their security responsibilities.
The most serious breaches of corporate security come from the inside (for example, a disgruntled employee). Internal security breaches can take the form of intellectual property being leaked or disseminated to competitors, employees quitting and going to competitors with proprietary material, or a consultant simply selling off your company's materials for fiscal gain. A serious example of the last scenario happened in the mid-1980s. A consultant sold off proprietary details of IBM's then latest storage management system to Fujitsu. IBM sued Fujitsu and won a considerable sum of money as a result. Yet the amount IBM won in the settlement could not come close to the estimated $1 billion in lost revenue as a result of Fujitsu stealing IBM's technology.
Disgruntled employee problems are the hardest for corporate management to handle in this litigious age because there are so many lawyers who will take the flimsiest of employee termination cases on contingency in hopes of obtaining a tidy out-of-court settlement from the company. Companies know that it costs more to fight the suit in court than to pay the malcontent $25K to get rid of him, so the majority of companies will pay some sum of money to get rid of a problem employee who makes a legal threat. Sadly, the disgruntled employee is now loose on the job market again—without the public record of a court case for future employers to find in any background check.
Are background checks even performed? Not every company does them. This brings us to the topic of personnel security audits, a controversial topic because it can infringe on a person's right to privacy. Procedures for background checks should be included in the security policy—the level of screening required may vary from minimal to full background checks, depending on the sensitivity of the information the individual will handle or the risk and magnitude of loss that can be caused by the individual. Beyond that, any subsequent personal auditing is a sensitive area.
In some industry sectors, such as the financial and legal sectors, it is widely accepted that phone conversations are recorded to deter insider trading or client confidentiality infringements. Employees sign a waiver accepting this policy. A corporation should get legal advice about the latest rulings for personal privacy legislation, because it relates to the workplace, before putting any auditing mechanisms in place.
Another significant issue that needs to be addressed in a corporate security policy definition is the internal misuse of corporate resources. File sharing in particular is a large target because of its potential financial and legal risk to the corporation employing users of such software. Obtaining and sharing pirated or copyright-violated materials is expressly forbidden in many corporate statements of conduct. In many instances, the security architecture is increasingly being used to track these types of corporate misuse.
Companies must be firmer in handling insider security breaches and take corrective action on what is uncovered in a policy or personnel audit. The security policy must be reflected in corporate human resources policies. It is not enough to say, “Our proprietary information is ours, and you can't go around disclosing it.” The company must give explicit examples with explicit consequences, putting a clause in an employment agreement that reads, “Give away even one corporate secret to an outsider, and you will be summarily fired.” By doing this, a problem employee can be dealt with more quickly, with more confidence that most lawyers won't accept the case. Establish a clear standard of behavior as well as penalties for violations of that standard and make them part of the employee handbook. If employees then violate the standard, they can't claim that they didn't know about the standard or the penalties.
This chapter detailed the process of defining a corporate security policy. The first step is identifying the global corporate security considerations. Second, critical resources need to be identified and the likelihood and costs associated with the compromise, destruction, or unavailability of these critical resources have to be assessed. Third, a decision can be made as to what level of risk is acceptable to the company. After the acceptable risk has been determined for given vulnerabilities, a security policy specific to the corporation can be defined that includes the security services of identity, integrity, confidentiality, availability, and auditing.
The following questions provide you with an opportunity to test your knowledge of the topics covered in this chapter. You can find the answers to these questions in Appendix E, “Answers to Review Questions.”