Chapter 13
Business Continuity Management and Cybersecurity
Marsh Sek Seong Lim, Marsh Risk Consulting Business Continuity Leader for Asia, Singapore
The business continuity manager, Loretta, spoke solemnly to CEO Tom. “All our information and communications systems and services are under cyber attack. All our data and information files are locked by ransomware.”
Tom replied curtly, “But how can this cyber disaster occur? I was given assurances by the internal and external IT experts that our setup is extremely resilient, with the latest state-of-the-art cybersecurity protection and detection systems and services?”
Nathan, the chief risk officer interjected, “The organization took a prudent approach to implement an IT disaster recovery center (DRC), housing all critical servers and databases; including two or more data feeds to ensure critical data are regularly replicated to the DRC.”
Loretta chimed in, “Unfortunately, this allowed the attack and ransomware to infect the DRC systems and databases. We do not have an independent IT disaster recovery set up and no secondary back up storage media. The decision was made on the advice that the risk of such a scenario is very low. Our business continuity, crisis management, and communications plans—developed to enable us to recover at an alternate site when the primary site and data center activities are disrupted for a significant period—do not provide the processes and procedures to deal with this cyber disaster.”
Good International Practices for Cyber Risk Management and Business Continuity
Regardless as to the size or type of your enterprise, is your organization prepared for a cyber scenario like the one Tom is facing? As you read the following sections, refer to the chapter appendix as needed. It contains a glossary of some of the key terms used in this section.
Cyber and the Business Continuity Management System (BCMS)
A business continuity management system (BCMS) can be considered a specialized child and subset of its parent enterprise-level risk management system (ERM). The BCMS uses a business impact analysis (BIA) approach to focus on the critical single points of organization operational failure and crisis and the impact time intervals, processes, and mechanisms to recover the critical organization operations and functions from any disruption. A demonstrable business continuity management capability includes: risk assessment, business impact analysis, implemented recovery strategies, business continuity plan, establishing business continuity/crisis management teams, and review and testing.
A point of failure or crisis may be caused by a cyber breach. When that breach is not managed within the escalation procedures of its sibling cybersecurity incident management system, or it escalates further to a cyber crisis management state, then BCMS and all enterprise functions associated with the BCMS should be engaged.
There may be several approaches that can be adopted to identify and assess key cyber risk scenarios but the focus for business continuity management (BCM) should be on the potential impact from single points of failure over a period of time, and the potential costs and expenses to rectify the problem. The ISO 27000 Information Security family of standards offers a useful information security-based risk assessment approach that focused on the assessing risks to data assets. A standardized risk framework aligned to the ISO 27001 should be tailored to each organization and define the ratings for likelihood of occurrence and the impact criteria based on the confidentiality, integrity, and accessibility (or availability) of sensitive information.
Organizations should identify their risks and measure the effectiveness of their risk treatment and controls. These risks are likely to include:
- Data loss and theft of confidential data.
- Unauthorized access—both intentional and unintentional—by internal and external parties.
- Data loss or corruption when transferring and transmitting data using different communications media and devices.
A key aspect should be to determine the impact to the organization, business, key stakeholders, organization partners, and customers. Sources for impact assessment may come from an organization or sector historical losses or values from past internal incidents, industry surveys, or information from reports provided by relevant experts such as the major international insurers and research agencies like the World Economic Forum.
BCMS Components and ISO 22301
The international BCM standard called “ISO 22301: Societal security–Business continuity management systems–Requirements” provides a framework consisting of international best practices. This framework enables cyber incident and crisis management (ICM) and BCM to be integrated into an organization-wide risk management and response for potential major cyber incidents. Figure 13.1 offers a high level overview of the main cyber response components.
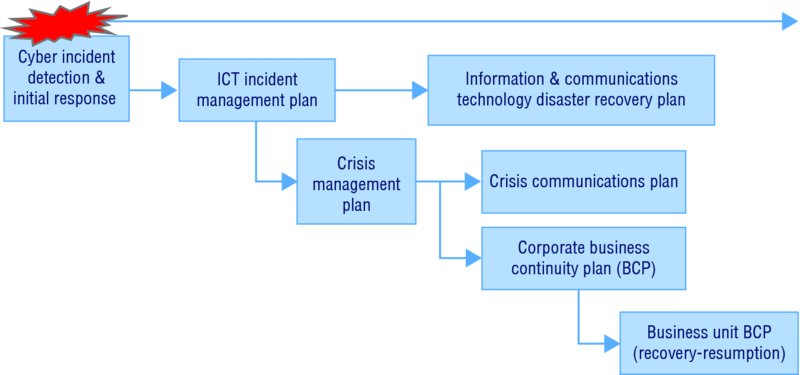
Figure 13.1 Conceptual overview of main cyber response components
Major cyber incidents can potentially have a significant impact over time, disrupting business and operation activities. Many organizations currently do not have adequate plans established based on maximum probable loss and most credible worst case cyber scenarios, such as a large scale distributed denial of service (DDoS) attacks. Many organizations currently design and implement IT and IT disaster recovery (DR) architectures that have a common physical network infrastructure. Unfortunately, the impact of a corporate or organization-wide cyber incident scenario has not been thoroughly analyzed. Cyber incident responses may be incorporated into existing plans, processes, and procedures—including information and communications technology (ICT) incident management plan (IMP), IT disaster recovery plan (DRP), crisis management plan (CMP), crisis communications plan (CCP), and business continuity plan (BCP). The ISO 27001 and 22301, international standards for information security and business continuity management systems, respectively, are international best practices and standards that may be used by organizations to implement policies and a framework to address cyber incidents.
The cyber response should include escalation and notification processes to alert the crisis management team (CMT) for incidents that will potentially have a significant impact on the IT services and data, as well as business operations. The cyber response typically has an impact severity matrix as a key component of the IT IMP; which enables an organization to gauge the severity of impact of a cyber attack or incident. The cyber impact severity matrix should constitute or be integrated with the impact matrices and criteria used in risk assessments, business impact analysis, and damage assessments. This facilitates the development and implementation of strategies, plans, processes, and procedures that will provide an integrated and seamless set of response plans (BCP, CMP, CCP, IT IMP, and IT DRP) to address major cyber incidents.
Embedding Cybersecurity Requirements in BCMS
BCM and IT DRP traditionally focus on the computer rooms or data center operations becoming inoperable, with significant damages to critical server and network equipment, typically caused by major incidents like power failure or fire. Business continuity and IT disaster recovery plans typically do not factor in major disruptions to IT services and business activities arising from cybersecurity issues, risks and attacks.
Enterprise leaders need to be concerned about data loss due to a cyber incident or attack. The impact from the start of an incident needs to be evaluated. The point in time where the last known good data record is available needs to be considered. Today, data protection typically involves replicating data to a remote site; where it is then transferred or backed up to a secondary storage media. Data replicated is typically transported via a wide area network. A potential key risk with significant impact is that the same transporting mechanism allows the same cyber attack to also target the offsite data, and possibly the backed-up data.
Organization users therefore need to evaluate the possibility of relying on earlier versions of data records to support the BCP and IT DRP. The earlier the last known good data record is retrieved from, the bigger the challenge; this implies recreating a larger column of data from alternative records.
BCP and IT DRP recovery prioritization and support resource requirements need to be ascertained in advance. Key areas to reevaluate are IT resources, IT DR provisions, PC, and other critical infrastructure equipment. Third party and outsourced services should be included in the study.
The impact severity criteria for risk assessment, BIA, damage assessment, and crisis management could be specified based on the number of critical organization operations and functions, and IT application services and databases that are affected by a major cyber incident. This should also take into consideration the time sensitive periods for these functions. Regulatory, statutory, and contractual requirements relevant to the organization activities also need to be included in the impact severity criteria.
The potential impact of major cybersecurity incidents relating to internal and third-party breaches and private data loss, and the associated consequences on the reputation and image of the organization, the branding of key products and services, as well as compliance and contractual obligations also need to be assessed.
Cyber incidents can also result in the disruption of telecommunications services and infrastructure for a significant period. Today, organizations are very dependent on the network infrastructure to support internal business and operation processes, and electronic (including mobile) commerce, so the unavailability of the telecommunication infrastructure and services will have grave implications to the organizations—even for crisis management and communications.
Developing and Implementing BCM Responses for Cyber Incidents
BCP, CMP, and IT DRP typically assume telecommunications infrastructure (including third-party service providers) is recovered. Besides the telecommunications infrastructure, IT systems, services, and databases at both the IT production and DR centers may be unavailable for a significant period of time during a major cyber incident. Therefore, the recovery period of the IT systems, infrastructure, services, and databases within the prioritized (planned) time frames need to be validated.
Enhancements to the BCM, CM, IT IMP, and IT DRP responses will likely be required to ensure the integrated responses adequately address cyber incident consequences. The minimum operating levels, and corresponding resource and service requirements to support the BCP, CMP, and IT DRP should be revised to cater for a major cyber incident.
Specialized resources to support the responses will be required—including consultants and service providers specializing in cybersecurity, cyber forensics, accounting forensics, crisis management, crisis communications, legal advisors, social media, and news monitoring etc.
The adequacy of the arrangements to support BCM, CMP, IT IMP, and IT DRP need to be validated. Therefore, organizations need to develop and conduct separate and integrated exercises to ascertain that the BCP, CMP, CCP, IT IMP, and IT DRP are effective against a major cyber incident. Independent exercises will validate the adequacy of the BCP, CMP, IT IMP, and IT DRP as individual plans. Exercising the plans in an integrated exercise will validate that the plans, processes, and procedures work seamlessly to mitigate an organization-wide cyber incident.
Organizations need to factor higher expenses and costs associated with the external services and subject matter experts into the BCM and IT DRP budgets. Transferring some of these increased costs through cyber insurance should be included as one of the key risk mitigation measures.
Conclusion
The following cyber risk management statement represents those organization capabilities CEO and board expect to be demonstrated in terms of cyber risk alignment with business continuity management for the enterprise.
Appendix: Glossary of Key Terms
- Business continuity plan (BCP):
-
Typically made up of the corporate wide or level BCP and the business unit BCPs. The BCPs focus on the continuity, recovery, and resumption of the critical business unit functions (that is, non-technology-based recovery). The corporate BCP contains the corporate level processes and procedures for business continuity, recovery, resumption, restoration, and return to normal operations. The business unit BCPs contain the recovery and resumption processes and procedures for the critical business functions; which were identified and prioritized during the business impact analysis. The prioritization for the recovery of critical business functions is established based on the impact over time when the function is disrupted for a significant period, and the recovery time objectives, which are determined based on internal and external dependencies and time-sensitive and peak processing periods. The recovery point objective of vital data and records will also influence the business continuity priorities.
- Crisis management plan (CMP):
-
Contains the processes and procedures for the senior management team to control and ensure coordination of major crisis incidents. The crisis communications plan complements the CMP. It contains the processes, procedures, and templates to manage internal and external communications during a crisis. Together, the CMP and CCP enable organizations to command, control and coordinate information, decisions, and communications during a crisis.
- Cyber incident and crisis management plan (ICMP):
-
Documents the processes and procedures for IT teams and management—a framework to respond to and manage cyber incidents. IT may incorporate cyber response incidents into the corporate IT response plan. Crisis management response actions for cyber incident may be embedded in the corporate crisis management plan. IT can incorporate response to cyber incidents in its incident response plan, however, from that point onwards the cyber incident can be treated as any other incident per organization’s incident management and crisis management plans.
- Disaster recovery plan (DRP):
-
Documents the processes and procedures for the recovery of IT servers, networks, applications, and databases; usually at an alternate site called the IT disaster recovery center. The IT DRP focuses on the technical recovery of IT systems and infrastructure.
About Marsh
Marsh is a global leader in insurance broking and risk management. In more than 130 countries, our experts in every facet of risk and across industries help clients to anticipate, quantify, and more fully understand the range of risks they face. We assist clients to define, design, and deliver innovative solutions to better quantify and manage risk. We offer risk management, risk consulting, insurance broking, alternative risk financing, and insurance program management services to businesses, government entities, organizations, and individuals around the world. Marsh is a wholly owned subsidiary of Marsh & McLennan Companies (NYSE: MMC), a global professional services firm offering clients advice and solutions in the areas of risk, strategy, and people. With 60,000 colleagues worldwide and annual revenue exceeding $13 billion, Marsh & McLennan Companies include global leaders Guy Carpenter, Mercer, and Oliver Wyman.
About Marsh Risk Consulting
Marsh Risk Consulting (MRC) is a strategic business unit within Marsh. MRC provides innovative risk management and organizational resilience solutions. Working collaboratively with clients, we identify key risks and develop the foundations for effective and sustainable risk management.
About Sek Seong Lim, CBCP, PMC
Sek Seong is the vice president and leader BCM & Resilience Service for Asia, Marsh Risk Consulting Singapore. He has been in professional and consulting services for almost 30 years. He specializes in BCM, CM, IT DRP, ISMS, and RM. He develops and implements strategies and plans for clients. Sek Seong has implemented BCMS (with CMP) for many clients, of which at least 25 have subsequently been certified compliant to the ISO 22301:2012 International BCM Standard. He regularly conducts training, speaks at public events, and conducts readiness assessments for clients. He was also on the original core development team that wrote the TR19 Technical Reference for BCM (then relaunched as SS540 Singapore Standard for BCM, which has since been withdrawn as the requirements in this standard are incorporated in the ISO 22301) and the SS507 Singapore Standard for BC-DR for Service Providers.
