Chapter 8
Treating Cyber Risks
John Hermans, Cyber Lead Partner Europe, Middle East, and Africa at KPMG, The Netherlands Ton Diemont, Senior Manager at KPMG, The Netherlands
CEO Tom challenged his chief risk officer, Nathan. “So give me the right guidelines for how to treat cyber risk and bring cybersecurity back to basics.”
Cybersecurity has been in the spotlight for the past few years. Due to the number and seriousness of cyber incidents, the media’s focus on such incidents, and the importance of tackling cyber issues in the extensive digitization of most organizations, this area requires the attention of directors and managers everywhere. But it needs to be tackled in the appropriate way and with the required subtlety, as a component of integral risk management.
Introduction
The fact that cybersecurity is important to every organization needs no further explanation. On an almost daily basis, various incidents demonstrate how great the risks are and that individual hackers and professionally organized cybercriminals are extremely active. The heads of organizations need to ensure that their organizations have set the proper priorities. To many, however, this is not a simple task because the world of cybersecurity seems elusive due to its specialist character and the technical jargon used. Generalists have difficulty grasping the complexities. In addition, it is difficult to distinguish between primary and secondary issues, while media coverage contributes to a culture of fear leading to the idea that almost every organization is helpless prey to malevolent forces. Almost no distinction is made between imposters on eBay, hackers who crash web sites, and organized criminal gangs using a systematic strategy to try to steal company secrets, which we call crown jewels. Such distinctions are extremely important because not all organizations are equally attractive to the different types of cybercriminals.
Partly due to the fact that concepts are often interwoven, cybersecurity remains a troublesome theme to many organization leaders. Nevertheless, this cannot be an excuse to devolve the issue to specialist professionals. It is truly essential that heads of organizations themselves actively lead the crusade for cybersecurity. Within the complexity of cybersecurity, leaders need to consider the relevant issues soundly and, at the very least, pose the right questions. But how should this be done?
Treating Cybersecurity Risk with the Proper Nuance in Line with an Organization’s Risk Profile
The seriousness of the cybersecurity risks means that cybersecurity does require boardroom attention—but in the appropriate context. Organizations need to avoid panicked responses that have not been thought through. The media regularly paint a dramatic picture of cybersecurity as if numerous organizations are helpless victims of cybercriminals. Moreover, all types of crime are lumped together, causing anxiety among organizations that is not based on the facts. Small and medium-sized enterprises (SMEs) have a completely different profile than multinationals, and an SME need have few worries about many of the incidents reported in the media.
The truth is more nuanced than the picture presented by the media. The risks are certainly controllable. Cybercriminals are not invincible geniuses, and the government and enterprises have significant knowledge of how to fight cybercrime. But we need to realize that 100 percent security is an illusion and that the pursuit of total security will lead not only to frustration but also possibly to a false sense of security.
In fact, we ought to start considering cybersecurity as “business as usual,” as a theme that deserves attention in much the same way as the risk of fire or fraud. These are themes that are tackled by management in a structural way, from a risk-management perspective, with the defenses and responses therefore not founded on the idea of building a system that is completely watertight.
Many organizations need to examine cybersecurity differently. They should not take decisions on the basis of fear of what is happening outside, but reason from the standpoint of their own strengths, from an awareness of the risks run by their own organization, in accordance with the risk profile of the organization and its specific nature.
The starting point of the exploration of an organization’s cyber risk is the determination of that organization’s risk profile and risk appetite. Questions that are relevant in determining this risk profile include: “How interesting is the organization to potential cyber criminals?”; “How dependent is the organization on the services of other organizations”; and “How much risk is the organization willing to accept?”
Determining the Cyber Risk Profile
In order to determine an organization’s cyber risk profile, we need to use a model that covers the following five aspects as shown in Figure 8.1.
- What is the organization’s internal and external context and environment? In which markets is the organization active? To what extent is the organization dependent on the digitization of the organization’s service provision? To what extent is the organization linked to another organization that could form an additional risk in this framework?
- What could be relevant intended targets within the organization, and also within the chain in which the organization is active?
- To which group of cybercriminals, and why, is the organization an attractive target (threats)? Which resources could the attacker deploy?
- Which vulnerabilities in the organization could cybercriminals exploit? This concerns not only technical vulnerabilities but also human actions. More importantly, what is the level of resilience? How fast can an organization be back in business after a cyber attack?
- What are the regulatory and legislative requirements with regard to cybersecurity that pertain to the organization?
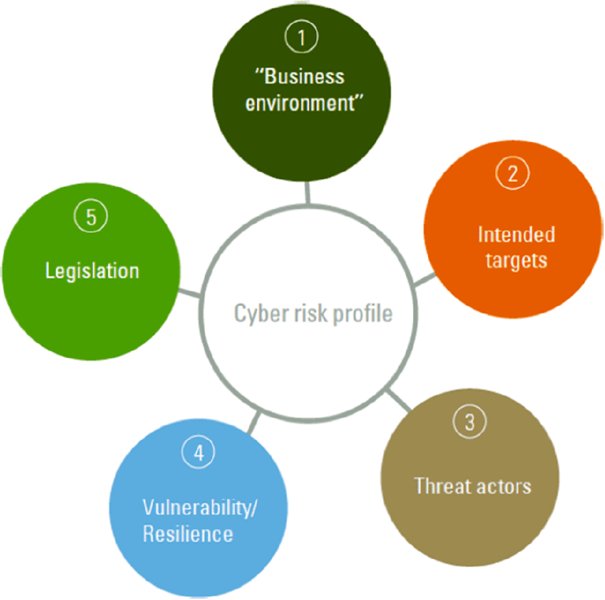
Figure 8.1 An organizational cyber risk profile
On the basis of an analysis of the five aspects mentioned above, an organization is able to determine its risk profile as well the amount of risk it is willing to accept (its “risk appetite”) and to implement the appropriate set of cybersecurity measures. As stated previously, it will never be possible to achieve 100 percent security, so there is no point in pursuing such an aim!
Treating Cyber Risk
Cyber risk management programs must consider an organization’s risk appetite. Specific cyber risks can and must be treated by applying the necessary measures and by reacting effectively when an organization is subjected to cyber attack. Figure 8.2 addresses the question, how does one select the right set of treatment measures?
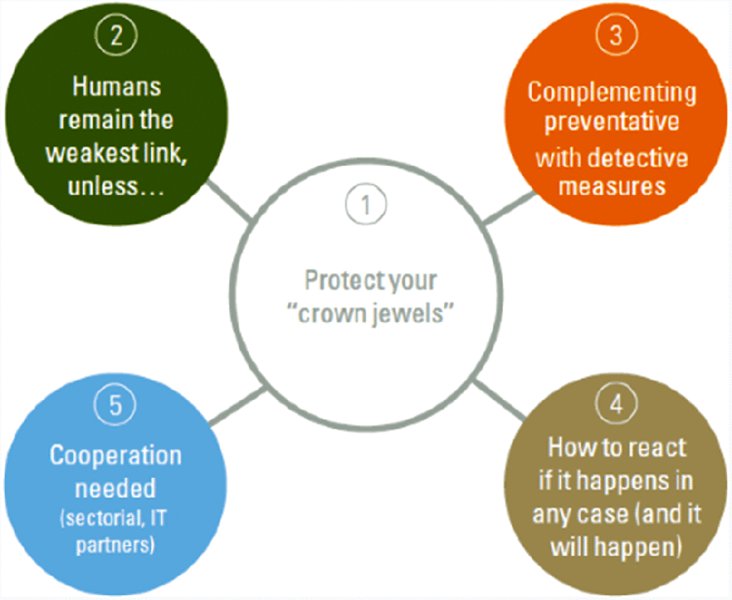
Figure 8.2 Selecting the right set of treatment measures
In this framework, a number of considerations are relevant.
Focus on Your Crown Jewels
In view of the fact that it is impossible to protect everything, cybersecurity requires special attention regarding the protection of the organization’s most valued information. It is therefore vital that an organization specify its crown jewels that need to be protected.
Humans Remain the Weakest Link
It is essential to have technical systems to protect, to identify intruders, and to respond to an attack, but human beings are actually the weakest link in many organizations. However, humans may also be the best asset in the organization’s defense, if they are properly informed and trained.
Complementing Preventative Measures with Detective Measures
Whereas organizations once primarily relied on preventative measures to avoid cybersecurity incidents, attention is increasingly being paid to the detection of attacks, in order to enable the organization to react immediately and appropriately. We see a growing use of technical monitoring facilities in many organizations to detect and analyze alien traffic.
Focus on an Organization’s Capability to Respond
As mentioned previously, we believe it is unfortunately only a question of time before an organization becomes a victim of a cyber incident. Instead of being a helpless victim, an organization can prepare for a serious attack. As such, it is vital for organizations to include the processing of cyber incidents in their crisis plans. An important part of this is the formulation of a protocol to be used in communications during a cyber incident.
Cooperation Is Essential
Besides being able to respond to incidents, it is crucial for organizations to remain up to date and informed of emerging threats, and to learn from other organizations how best to react to incidents. To facilitate this, there are organizations at various levels whose aim is to help other organizations in this area: at national level (the National Cyber Security Centre, for example), at sector level in various International Sharing and Analysis Centers (ISACs), and occasionally there are informal cooperative associations, such as a group of chief information security officers (CISOs) who work together to combat cybersecurity incidents within a particular industry. With the objective of generating a proactive approach to cybersecurity, it is vital to promote the active participation of organizations in such networks, which will help the organization to improve its own resilience. We must not forget, after all, that an incident at another organization is also a potential threat to one’s own organization.
Alignment of Cyber Risk Treatment
Technology alone is not the answer to cybersecurity issues. The answer lies in an integrated approach to cyber risk treatment, focusing on both the softer elements such as governance, culture and behavior, and the harder ones such as technology (Figure 8.3).
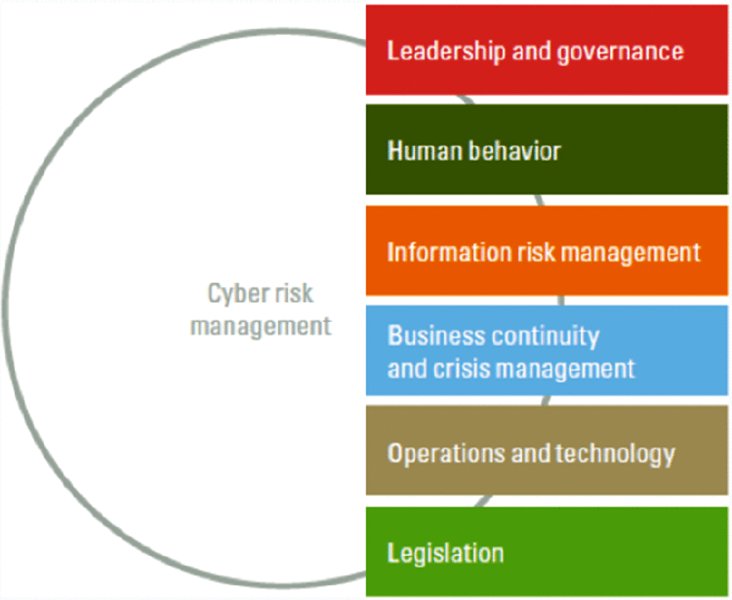
Figure 8.3 An integrated approach to cyber risk management
The kind of integral approach to cyber risk management shown in Figure 8.3 needs to include the following aspects:
- Leadership and governance. An organization’s leaders need to demon-strate, in word and deed, that they regard themselves as the owners of cybersecurity, and show that they intend to manage the associated risks adequately.
- Human behavior. Cybersecurity involves not only the appropriate technical measures but also the creation of a culture in which people are alert to, and aware of, ways in which they can contribute to security.
- Information risk management. An adequate approach to all-embracing and effective risk management with regard to information provision, also in relation to partner organizations.
- Business continuity and crisis management. Good preparation for possible incidents and the ability to minimize the impact of these incidents. This involves crisis and stakeholder management, among other aspects.
- Operations and technology. The implementation of checks and control measures in the organization in order to identify the cybersecurity risks and to minimize the impact of incidents.
- Legislation. Complying with legislation with regard to information protection.
The application of a holistic model incorporating all the above elements brings the following benefits:
- The minimization of the risk that the organization will be hit by a cyber attack from outside and the minimization of any consequences of a successful attack.
- Better decisions in the field of cybersecurity: the provision of information on measures, patterns of attack and incidents is thus optimized.
- Clear lines of communication on the theme of cybersecurity. Everyone knows his or her responsibilities and what must be done if incidents (or suspected incidents) occur.
- A contribution to a better reputation. An organization that is well prepared and has seriously considered the theme of cybersecurity is able to communicate on this theme in a way that inspires confidence.
- The enhancement of knowledge and competences regarding cybersecurity.
- The benchmarking of the organization in the field of cybersecurity in relation to its peers.
Practicing Cyber Risk Treatment
In order to continuously manage and mitigate the cyber risks, the organization needs to be able to address these risks in a flexible and ongoing manner. This requires a central and overarching perspective on those risks that require treatment and management attention as in Figure 8.4. An emerging threat landscape, a change in organization activities, and a shift to using new technologies: these are all indicators that the cyber risk landscape is changing. So far, current cybersecurity methodologies and cybersecurity models have not been able to capture this, in practice, in a dynamic way. For an organization to be able to provide a real-time and accurate view of the current risk environment would be the next step in the maturity of cyber risk management.
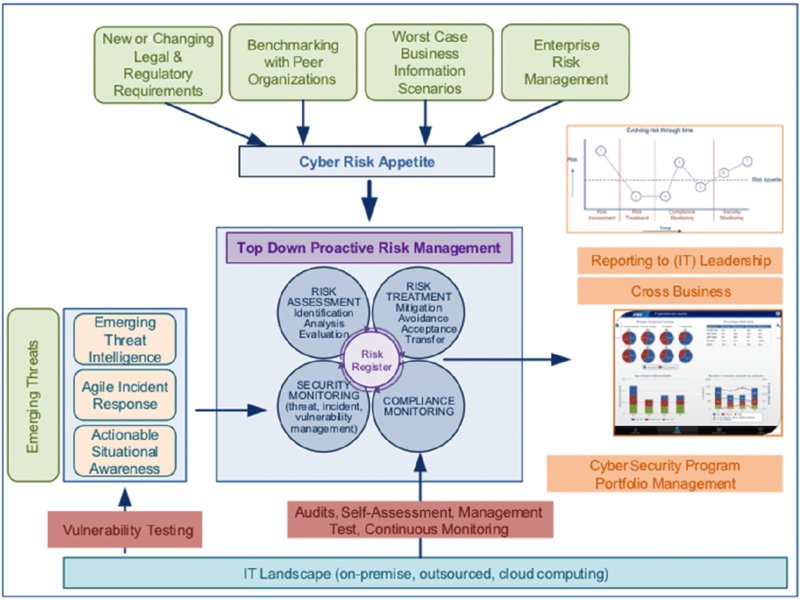
Figure 8.4 An overarching perspective over cyber risks requiring treatment
Business as Usual—to Be Integrated into Enterprise Risk Management
Cyber risk management should be to be linked to/integrated in the enterprise risk management (ERM) of an organization. Despite the topic and specific expertise, the approach must be fully aligned to existing risk management processes, and fits the recent developments to rationalize and unify risk frameworks, policies, standards, and processes. The rationalization and unification supports the required consistent risk language and classification schemes within an organization and will therefore be better and more quickly understood by all stakeholders and decision makers.
Cyber risk management must be part of the organization context and must be fully aligned with organization goals and needs. Only then will cyber risk management be able to show its added value by providing insight into organization opportunities and risks that should be avoided. This enables a top-down approach where information risk management (IRM) and ERM are aligned instead of existing in two separate worlds.
Business as Usual—to Be Integrated with the Regular Three Lines of Defense Applies for Model
Cybersecurity risk should be a primary business (first line of defense) responsibility and not be considered solely as an IT responsibility. Preferably, this responsibility should become part of the annual performance objectives of senior management demonstrating the importance and the tone at the top. The main focus for management is and should be addressing the customer needs and satisfaction and ensuring the continued availability of those primary business processes that customers rely on. Accountability and responsibility can be easily provided by utilizing the existing governance structures; hence, the composition and level of seniority is deemed adequate. Senior management should be supported by a multidisciplinary functional team of risk managers, security officers, compliance offices, legal and HR representatives (second line of defense), and included audit as the independent observer (third line of defense) in order to create full transparent and balanced views and supporting the appropriate steering and the right decisions with regard to cyber resilience.
Business as Usual—Managing Your Cyber Risks with a Predefined Risk Appetite
In many organizations it is a common “Pavlovian response” to immediately start drafting and implementing controls when a risk is identified, without asking what level of risk is acceptable. These decisions are often made, although with all good intentions, by cyber risk professionals without consultation with the appropriate business representatives.
The starting point of managing cyber risks is the same starting point of managing enterprise, defining the organization’s risk appetite, an exercise to be performed by business representatives instead of cybersecurity specialists. See ISO 31000:2009, Risk Management—Principles and Guidelines, which is the overarching risk management standard for most risk management processes. Why can this not be applied for cyber risk management? By selecting cyber as one of the scenarios, senior business management will be able, in conjunction with cyber specialists, to address the relevance of the threat.
More and more organizations formalize risk appetite statements to enable management to maneuver within the agreed and acceptable risk boundaries without constantly being blocked or hindered by risk management processes that are too rigid. Key with determining risk appetite statements is that such statement should contain both quantitative and qualitative components and follows the agreed approval process. The qualitative components are most applicable for cyber risk because the “crystal ball” for quantifying the impact of cyber risk is still based on empiric and rough estimations and is not yet founded on a proven quantitative methodology. Quantifying cyber risk is, unfortunately, still perceived as too complex, academic or mathematical.
We simply miss at this moment in time historical, actuarial data on cyber risks to underpin a quantitative cyber risk model, despite the good efforts of organizations like the World Economic Forum.
Defining the risk appetite for cyber requires a sound and structured process to define the risk appetite of the business, by using the technique of worst-case business information scenario planning. This process must translate the risk appetite into discrete levels of acceptable risk, taking into account factors like changing business models, new and/or changing legal and regulatory requirements, and emerging cybersecurity industry standards. A mechanism that can assist in defining the cyber risk appetite is the use of the annualized loss expectancy (ALE) methodology; expressing all losses to the expected annual loss provides a more consistent approach and evaluation of risks. ALE is defined as expected monetary loss that can be expected for an asset due to a risk over a one-year period; another motivation to relate nonfinancial risks to the financial impact.
A question that is often heard is: does the setting of risk appetite of cyber risks within smaller independent organizations differ from large organizations? No, basically not, most likely the thresholds for analyzing and evaluating risks differ, as larger organizations potentially have larger financial buffers and a higher appetite for risk.
Business as Usual—Using Your Embedded Risk Management Processes
When cyber is assessed as relevant for the organization, they can be assessed and treated by senior management and experienced specialists. The cyber risk assessment process (to identify, analyze, then evaluate risks) should be identical to that used for ERM and is used to arrive at how to priorities risks for treatment. The traditional risk treatment techniques “to avoid, accept, transfer, or mitigate” are on one set of options but they only treat risk as “threats” (risks with negative consequences). Modern-day treatment options also address opportunities (risks with negative consequences). Appropriate combined treatment options are not mutually exclusive, are appropriate to the case in hand, and should be aligned with the international standard ISO 31000:2009, Risk Management—Principles and Guidelines’ by:
- Avoiding the activity that gives rise to the risk;
- Taking or increasing the risk in order to pursue an opportunity;
- Removing the risk source;
- Changing the likelihood;
- Changing the consequences;
- Sharing the risk with other parties (e.g., risk financing, contracts); and,
- Retaining the risk by informed decision.
A key element in supporting this unification is to ensure that next to the financial impact criteria, the nonfinancial impact criteria for regulatory, customer, legal, compliance, operational, staff, and reputational occurrences are also being formalized and preferably linked to the financial criteria, meaning that a severe nonfinancial cyber occurrence is considered a high risk and treated equally as risk with a high financial impact.
Business as Usual—Treatment of Cyber Risks
Cyber risk treatment is prioritized, reiterative, and cyclical, with risk owners completing risk and control action plans that balance threat with opportunity to organization objectives and cost-benefit. Appropriate combined treatment options are not mutually exclusive, are appropriate to the case in hand, and should be aligned with the current ISO 31000:2009, Risk Management— Principles and Guidelines’ standard, as described in the previous section.
Prioritized risk treatment options should be aligned with existing organization objectives and strategies so that there is only a need to spend the money once. If this means that certain investments or improvements in the cyber resilience approach should be postponed, the organization should support and ensure a formal temporary risk assessment process is followed and a well-balanced acceptance and decision process is being followed.
The treatment of cyber risks should not differ from overarching ERM approaches. However, from a cybersecurity and cyber resilience perspective, it could imply that the defined and agreed security baselines and mandatory cyber controls or processes within an organization are being upgraded or enhanced and are subject to a more rigid form of periodic compliance and effectiveness measurement. For example, the organization could decide to monitor not only their crown jewels but all assets, as these are often targeted as stepping stones by the threat actors. By doing so the organization will potentially identify anomalies in their IT environment in an earlier stage, which implies that the response processes can be triggered much earlier as well.
Conclusion
The following cyber risk management statement represents those organi-zation capabilities CEO and board expect to be demonstrated in terms of treating cyber risks.
About KPMG
KPMG operates as a global network of independent member firms offering audit, tax and advisory services; working closely with clients, helping them to mitigate risks and grasp opportunities. Member firms’ clients include business corporations, governments, and public-sector agencies and not-for-profit organizations. They look to KPMG for a consistent standard of service based on high-order professional capabilities, industry insight, and local knowledge.
KPMG member firms can be found in 155 countries. Collectively, they employ more than 162,000 people across a range of disciplines. Sustaining and enhancing the quality of this professional workforce is KPMG’s primary objective. Wherever we operate, we want our firms to be no less than the professional employers of choice.
We contribute to the effective functioning of international capital markets. We support reforms that strengthen the markets’ credibility and their social responsibility. We believe that similar reform must extend to the professional realm.
About John Hermans
John is a partner at KPMG Advisory NV–Cyber Lead Partner Europe, Middle East, and Africa. He is responsible for KPMG’s cybersecurity services in the Netherlands as well within the EMA region. John is a recognized, frequent speaker on cyber strategies and cyber risk management at national and international conferences. In his daily professional life, John assisted many organizations across the globe in strategizing, planning, and executing their cyber journey. John has trained many supervisory and management board members in how to deal with cyber risk management.
About Ton Diemont
Ton is a senior manager at KPMG Advisory NV and a former head of IT risk within the operational risk management office as the chief information security officer (CISO) of an international bank. He has more than 21 years of information and operational risk management experience within the financial industry and has been responsible for developing and implementing IT risk, information security, and cybersecurity strategies; risk dashboards for executive boards and risk committees; aligning IT risk management processes to the operational risk management and nonfinancial risk methodologies and processes, and has been supporting ORM and IRM migrations toward ERM.
