Chapter 3
Principles Behind Cyber Risk Management
RIMS, the risk management society™ Carol Fox, Vice President, Strategic Initiatives at RIMS, USA
Tom was wondering why his head of human resources, Grace, was sitting alongside his chief strategy officer George. Tom asked, “So what do our people have to do with principles guiding our cyber strategy, risks, and actions?” Grace replied, “Lots. Our people enact the principles—principles that provide the foundation for desirable and positive behavior.”
Cyber Risk Management Principles Guide Actions
Principles provide the foundation for people’s desirable and positive behavior in carrying out their respective responsibilities within an organization. Principles aid in determining whether decisions and the resulting actions are helpful or harmful.
Principles from the ISO 31000:2009 international risk management standard can support an organization that chooses to implement COBIT 5 GEIT2 and its five principles:
- Meeting stakeholder needs.
- Covering the enterprise end-to-end.
- Applying a single, integrated framework.
- Enabling a holistic approach.
- Separating governance from management.
In this chapter, principles from the ISO 31000:2009, Risk management—Principles and guidelines3 are described to guide desirable and positive actions that are in line with the organization’s enterprise-wide approach to governance and management of enterprise information technology (IT). The two sets of principles are organized in Table 3.1. At times, the word cyber is inserted in the text to emphasize an IT-specific risk management perspective. However, the noted risk management principles are meant to apply across the entire organization, whether or not decisions and activities are related to IT.
Table 3.1 COBIT 5 GEIT Principles
| COBIT 5 GEIT PRINCIPLES | |||||
| ISO 31000 RISK MANAGEMENT PRINCIPLES | Meet stakeholder needs: | Covering the enterprise end-to-end: | Applying a single, integrated framework: | Enabling a holistic approach: | Separating governance front management: |
| Risk management is transparent and inclusive. | Risk management creates and protects value. | Risk management is systematic, structured, and timely. | Risk management is an integral part of all organizational processes. | Risk management facilitates continual improvement of the organization. | |
| Risk management is dynamic, iterative, and responsive to change. | Risk management is tailored. | Risk management takes human and cultural factors into account. | |||
| Risk management explicitly addresses uncertainty. | Risk management is part of decision making. | ||||
| Risk management is based on the best available information. | |||||
Meeting Stakeholder Needs
The first COBIT 5 principle “addresses the need to align individual and departmental objectives and priorities with enterprise and stakeholders needs.”4 The principle recognizes that stakeholder needs and enterprise goals change over time.
Being Transparent and Inclusive
One of the principles noted in the ISO 31000 standard holds that “risk management is transparent and inclusive.” The principle states that “appropriate and timely involvement of stakeholders and, in particular, decision makers at all levels of the organization, ensures that [cyber] risk management remains relevant and up-to-date.”
Examples of stakeholders in cyber risk assessment processes might include:
- Customers, clients, stockholders, employees, contractors, and supply chain partners (e.g., outsourced partners and critical infrastructure suppliers);
- Government and regulatory authorities;
- Nongovernmental organizations;
- Civil society groups; and
- Members of the public (including the media).5
This principle is demonstrated when the organization can answer questions such as “What is each stakeholder expecting from the organization when it comes to managing cyber risk?”; “What are the regulations that apply to the digital information and sensitive data that is accessed, used, stored, and transmitted by the organization?”; and “What are the voluntary or contractual obligations that the organization has taken on with respect to its network, systems and data availability, reliability, security, and privacy?” The answers may differ depending on the stakeholder.
Being Responsive to Change
Once these questions are asked and answered, the risk management principle that “risk management is dynamic, iterative, and responsive to change” applies in meeting changing stakeholder needs. This principle explicitly states that [cyber] “risk management continually senses and responds to change. As external and internal events occur, context and knowledge change, monitoring and review of risks take place, new risks emerge, some change, and others disappear.”6 Given the disruptive nature of technology and speed of change, this principle addresses the intersection between stakeholders (and their respective and, at times, differing needs) and changes in internal and external circumstances. Technology refreshes, operational process changes, new applications/software solutions—and changes in how each of the stakeholders access and use the organization’s network, systems, and data—all create opportunities as well as threats.
This principle is demonstrated when uncertainties and changes that modify IT assets, the organization’s objectives or stakeholder needs are integrated into the organization’s formal and informal change management processes, wherever these processes occur.
Covering the Enterprise End to End
This COBIT 5 principle recognizes that managing IT as an asset is an essential element of business value creation, covering “all functions and processes within the enterprise” to “enable the enterprise to achieve the goal of satisfying stakeholder needs.”7 Accountability for managing IT assets in this regard rests with business managers rather than IT functional roles.
Creating and Protecting Value
Three ISO 31000 principles relate to this foundational element. The first, “risk management creates and protects value,” focuses on the idea that [cyber] risk management “contributes to the demonstrable achievement of objectives and improvement of performance. …” This principle is demonstrated when the process for considering uncertainties and decisions related to IT assets by business managers includes recognition of the organizational value to be gained or the value protected.
Tailoring
The second, “risk management is tailored,” emphasizes that [cyber] “risk management is aligned with the organization’s external and internal context and risk profile.” The principle acknowledges the potential differences in the entity’s operations, stakeholders, and business environment, with the expectation that these differences are taken into account. This principle is demonstrated when assessment methodologies, decisions, and resulting actions are customized based on the circumstances, proprietary knowledge, and the set of risks under consideration.
Addressing Uncertainty
The third, “risk management explicitly addresses uncertainty,” relates to behaviors in which people acknowledge that the future can be different from the past. This principle encourages “risk management [that] explicitly takes account of uncertainty, the nature of that uncertainty, and how it can be addressed.” The principle recognizes that not everything can be known, that circumstances change, and that ambiguity requires planning so that the enterprise can adapt in an unpredictable environment. This principle may be demonstrated through the use of assessment methodologies that examine potential factors and emerging issues that could affect desired outcomes, scan for changes in the organization’s environment, consider various scenarios, and make plans for management action.
Applying a Single, Integrated Framework
In this third COBIT 5 principle, the use of an overarching framework that incorporates relevant standards and frameworks—including the ISO 31000 risk management series—is provided as a “consistent and integrated source of guidance … addressing specific GEIT aspects … in an effective way.”8 ISO 31000 is noted to apply within two areas in COBIT 5: (1) Evaluate, Direct, and Monitor; and (2) Align, Plan, and Organize, while being interconnected with a number of complementary standards at the same time.
Being Structured
One of the ISO 31000 principles, “risk management is systematic, structured, and timely” states that “a systematic, timely and structured approach to [cyber] risk management contributes to efficiency and to consistent, comparable and reliable results.” This principle infers that people apply management-directed criteria, metrics, and processes that can be replicated and used whenever and wherever decisions concerning IT assets and related environments are made. In order to achieve consistency and effectiveness throughout the enterprise, the criteria, metrics, and processes for considering risk should be aligned with that used for non-IT related issues. This principle is demonstrated when the enterprise establishes and communicates a clear and naturally integrated way of dealing with risk that is appropriate for business management to meet stakeholder needs, and is applicable to governing and managing enterprise IT.
Enabling a Holistic Approach
The fourth COBIT 5 principle “emphasizes that efficient and effective implementation of GEIT requires a holistic approach that takes into account several interacting components or mechanisms …”—“enablers” in COBIT terms.9 Four of these enablers (processes; culture; information; and people, skills, and competencies) relate directly to four ISO 31000 principles.
Integrating into the Organization
The first, “risk management is an integral part of all organizational processes” explains that [cyber] “risk management is not a stand-alone activity that is separate from the main activities and processes of the organization. Risk management is part of the responsibilities of management and an integral part of all organizational processes, including strategic planning and all project and change management processes.” Since all activities of an organization involve risk, risk management is a natural intersection for incorporating legal, human resources, operations, IT management and protection, information security, physical security, privacy, and compliance functions and processes needed for a holistic cyber risk approach. Figure 3.1 illustrates how risk management unifies the organizational processes across the cyber enterprise.
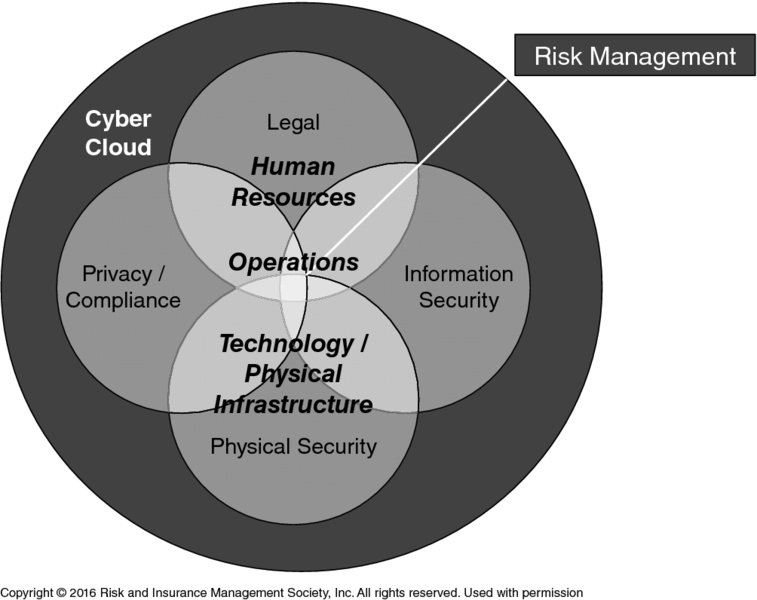
Figure 3.1 Risk management unifies processes
This principle is demonstrated by people working collaboratively across the various organizational systems in managing cyber risks to influence people, processes, and technology. It is further demonstrated when risk management is embedded into processes, such as strategic planning and change management, which influence the direction and modifications necessary to achieve the enterprise mission.
Considering Human and Cultural Factors
A different principle, “risk management takes human and cultural factors into account,” is closely aligned with COBIT’s enabler of culture, ethics, and behavior. In this ISO 31000 principle, “risk management recognizes the capabilities, perceptions, and intentions of external and internal people that can facilitate or hinder achievement of the organization’s objectives.” The principle suggests that evaluation of these capabilities, perceptions, and intentions can provide insights into external uncertainties, such as disruptive consumer preferences, behavior of industry or supply chain participants, and competing inventions. Internal uncertainties, such as innovation, ethical behavior, and motivations can be evaluated for consistency with the expectations set by management and rewarded through performance. This principle is demonstrated internally through management’s clear expectations and rewards for behaviors consistent with the enterprise’s core values, and is carried out through the decisions and resulting actions that individuals take. This principle is further demonstrated when the organization can answer questions such as:
- Is this project, initiative, or activity consistent with cultural expectations for managing cyber risk?
- Will the people involved, both internally and externally, behave in the way we anticipate?
- If not, are there other alternatives or actions that can be taken to reduce the potential negative effects of the related uncertainty and increase the potential positive effects of the related uncertainty?
The answers may differ depending on the project, initiative, or activity as well as the individuals or groups of individuals involved.
Being Part of Decision Making
A related ISO 31000 principle, “risk management is part of decision making,” connects two COBIT 5 enablers: culture (as discussed earlier) and people, skills, and competencies. This principle emphasizes that [cyber] “risk management helps decision makers make informed choices, prioritize actions and distinguish among alternative courses of action.” Decisions are made by all individuals within an enterprise as they carry out their activities. Most are automatic and made in the moment, requiring no formal risk assessments, but are highly dependent on the competencies and skills of the individual for managing risk. People who are making decisions that are of significant importance or are complex, such as those involved in a project or initiative, benefit from using risk management techniques to assess and evaluate the uncertainties related to each of the available options and identify potential unintended consequences. Those who are making decisions that have a strategic importance and are complex benefit from using more formal decision-making and risk management processes, applying multiple risk management techniques.10
All decisions, however, are influenced by the biases of those making decisions, as well as by the individuals’ respective skills and competencies. As noted in the ANSI/ASIS/RIMS Risk Assessment Standard RA.1-2015, “Biases may sometimes lead to perceptual distortion, inaccurate judgment, and illogical analysis of information. There is a common tendency to acquire and process information by filtering it through one’s own likes, dislikes, and experiences. Inherent bias is the effect of underlying factors and assumptions that impact information collection and analysis. Cognitive biases are tendencies to think in certain ways or a failure to imagine plausible alternatives.” Bias considerations can be flagged and addressed using a vigorous [cyber] risk management lens.
This principle is demonstrated when people responsible for complex decisions (such as those related to strategy, projects, and initiatives, particularly those that are of significant or strategic importance) apply formal risk decision quality and management processes and techniques, and when risk management techniques and process are used in less complex projects and initiatives. It is further demonstrated by coaching and training people who are expected to take risk into account in their daily decision-making activities.
Using the Best Available Information
Another ISO 31000 principle, “risk management is based on the best available information”—which is directly related to the COBIT 5 enabler “information”—notes that “inputs to the process of managing risk are based on information sources, such as historical data, experience, stakeholder feedback, observation, forecasts and expert judgement.” This principle encourages a fact-based approach, while recognizing limitations of data, modeling, and divergence of opinion among experts. The importance of agreeing to the validity of the underlying information to be used is key. This principle is demonstrated by clear agreement as to what constitutes verifiable evidence and, when unavailable, what constitutes reliable information or estimates.11
Separating Governance from Management
The fifth COBIT 5 principle “makes a distinction between governance and management.”12 The principle separates governance activities of evaluating, directing, and monitoring (based on business needs) from the management activities of planning, building, running, and monitoring. Both sets of activities are supported by GEIT processes. This principle contemplates a repeatable, closed-loop system in which management feedback is given “to ensure alignment with the direction that was set by the governance body and, thus, achieve the enterprise objectives.”13 While not specifically stated, such a feedback system naturally and continually improves the IT capabilities of the enterprise as it achieves its objectives.
Maturity Strategy and Continual Improvement
This principle is closely aligned with the ISO 31000 principle “risk management facilitates continual improvement of the organization.” This principle holds that “organizations should develop and implement strategies to improve their [cyber] risk management maturity alongside all other aspects of their organization.” This principle views continual improvement as being driven through a risk maturity strategy that aligns naturally with activities and processes found in separating governance from management. As people use risk management processes and techniques, they gain insights into the uncertainties that affect objectives, weigh alternatives, and make decisions that result in beneficial actions. As their risk management capabilities improve and mature over time, they naturally and consistently apply the above principles in determining whether decisions and the resulting actions are helpful or harmful. This principle is demonstrated when cyber risk management is embedded not only in IT-related governance and management activities and decisions, but in all the governance and management activities of the enterprise.
Conclusion
The cyber risk management statement in the “Principles Guide Actions” box represents those organizational capabilities the CEO and board expect to be demonstrated in terms of cyber risk management principles to guide actions.
Notes
About RIMS
As the preeminent organization dedicated to advancing the practice of risk management, RIMS, the risk management society™, is a global not-for-profit organization representing more than 3,500 industrial, service, nonprofit, charitable and government entities throughout the world. Founded in 1950, RIMS is dedicated to advancing risk management for organizational success, bringing networking, professional development, and education opportunities to its membership of more than 11,000 risk management professionals who are located in more than 60 countries. For more information on RIMS, visit www.RIMS.org.
About Carol Fox
Carol Fox, ARM, is the Vice President, Strategic Initiatives at RIMS, the risk management society™. While at RIMS, she’s led the development of numerous RIMS publications, including An Overview of Widely Used Risk Management Standards and Guidelines, ERM Best Practices in the Cyber World, and RIMS Strategic Risk Management Implementation Guide.
A Miami University graduate, she’s held progressively responsible risk management positions in the customer care, telecommunications, manufacturing, defense, and insurance industries. Prior to joining RIMS, she was senior director of risk management at Convergys Corporation with responsibility for business continuity, crisis management, safety, and claims. At the direction of the chief technology officer, she launched and managed a cross-functional IT security project that protected $100 million in recurring revenue.
Carol is the chair of the U.S. Technical Advisory Group for the ISO 31000 family of risk management standards, is a participant on the COSO ERM Advisory Council, and serves on Miami University’s William Isaac & Michael Oxley Center of Business Leadership Advisory Board. Known for her risk management experience and writings, she received RIMS’s prestigious 2009 Harry & Dorothy Goodell Award. In 2011, Treasury & Risk named her as one of the 100 Most Influential People in Finance.
