Chapter 21
Cybersecurity for Operations and Communications
EY Chad Holmes, Principal, Cybersecurity, Ernst & Young LLP (EY US) James Phillippe, Principal, Cybersecurity, Ernst & Young LLP (EY US)
CEO Tom challenged Maria, his chief information security officer (CISO). “I’m told ISO 217001 has at least 10 categories of operations and communications requirements relevant to cyber risk. But I want you to boil it down. Are we confident we understand how the threat landscape in the digital world applies to our organization and strategy and how to mature our prioritized operational cybersecurity capabilities around this?”
Do You Know What You Do Not Know?
Big Data. Smart devices. The Internet of Things. Robotic process automation. Behavioral analytics. 3D printing. The increasing digitization of your organization is yielding rewards in efficiency and cost-effectiveness. What is not as clear are the increasing risks that these advances are bringing to your organization’s operations.
You should understand these risks, and how to prevent them from damaging your organization. You need insight into not only the vulnerabilities of your IT systems, but to the data those systems produce, looking deeply into your organization environment. You have to gain fluency in the current portfolio of threats, how they are detected, and what strategies your organization needs to follow in order to treat them.
You may be tempted to assign responsibility for this effort with your information security leaders and team. Is not the solution in firewalls and virus protection software? If it were that simple. Cybersecurity is an organizational problem that requires a comprehensive enterprise-wide organization solution, one that starts with visibility and provides insight. Both come from data and the analytical discipline to discover its secrets.
Uncovering the threats is just part of the solution. Your security team needs to predict how threats will unfold and inform the strategies to treat them.
There are five crucial areas that need your focus:
- Threat landscape
- Data and its integrity
- The digital revolution
- Your organization and organizational changes
- Your people
We propose that your organization’s security operations are likely obsolete, and not adequately prepared to face the challenges that are literally changing day by day. In this chapter, we examine these critical five carefully, and we illustrate what your organization’s response should be.
Threat Landscape—What Do You Know About Your Organization Risk and Who Is Targeting You?
Some threats are explicit, a deliberate effort to breach your defenses and steal intellectual property. These can be Hollywood-style hackers, bypassing your firewall and exposing vast amounts of critical information, or they can be small, subtle attacks that ship information outside your organization by exploiting side doors and hidden windows. Who are these people? What do they want? What tactics do they use?
Information security is changing at a rapidly accelerating rate. Threat actors are increasingly relentless, making the response to information security incidents an ever more complex challenge.
According to EY’s Global Information Security Survey 2015, 36 percent do not have a threat intelligence program, with a further 30 percent only having an informal approach, while 5 percent say that their organization has achieved an advanced threat intelligence function.
Data and Its Integrity—Does Your Risk Analysis Produce Insight?
Think of the amount of data your organization processes each day across multiple departments and disciplines. Now consider the additional data that is created in the background at a systems level as that processing occurs.
Now think about what your organization’s strategy is for accessing, analyzing and evaluating data to reveal actionable insight. In particular, understanding the motivations and aims of threat actors to predict issues before they arise is the current cutting edge of information security.
For example, attackers may alter rather than steal your data. Imagine financial results changing to provoke errors, data analysis corrupted, or introduction of additional data to complicate your own. As innovation relies entirely on intellectual property, your risk multiplies as the scope of attacks intending to compromise that property widens. These threats complicate staffing, as the shifting landscape challenges knowledge and processes.
Fifty-seven percent say that lack of skilled resources is challenging information security’s contribution and value to the organization (EY, 2015).
Digital Revolution—What Threats Will Emerge as Organizations Continue to Digitize?
Attackers have avenues into your organization apart from the usual channels, thanks to several factors:
- Organizations are transforming and moving into the digital era.
- The adoption of the cloud and the Internet of Things are gaining traction.
- The near-continual demand for access to information among people of all levels throughout the organization.
Can we predict the changes in the threat environment that this revolution brings?
Cybersecurity helps make the digital world fully operational and sustainable. Cybersecurity is key to unlocking innovation and expansion, and by adopting a tailored and risk-centric approach to cybersecurity, organizations can refocus on opportunities and exploration. The operational imperatives of safety, quality, and productivity depend on such innovation, and the cybersecurity ramifications of the ongoing digital revolution can reveal much about the eventual success of an organization’s efforts.
Vendor consolidation brings unforeseen complications, including increasing gaps in visibility, lack of access to appropriate data, security countermeasure orchestration breaking down, security playbooks falling apart, and data security weakening. In digital, that can mean security response delays, data integrity, and connectivity and process issues, all of which can affect operations and risk to be compromised.
Eighty-eight percent of respondents do not believe their information security fully meets the organization’s needs (EY, 2015).
Changes—How Will Your Organization or Operational Changes Affect Risk?
When the organization contemplates partnerships, marketing initiatives, mergers or acquisitions, how does it lever security intelligence? It’s an axiom that balancing risk and reward is the key to sustainable organization success, but you should be aware of unseen risk, just as in other areas of the risk environment.
Ownership of data and information can become muddied during periods of change; security processes and procedures are set aside, and lines of responsibility are blurred. Strategic decisions can overbalance an organization in one area, leaving it vulnerable in another. Internal communication of significant organization decisions and strategies frequently omits the security infrastructure—they do not know what they do not know.
Twenty-seven percent say that data protection policies and procedures are informal or that ad hoc policies are in place (EY, 2015).
People—How Do You Know Whether an Insider or Outsider Presents a Risk?
Cellular telephones, portable hard drives, USB drives, social media, tablets, laptops—it is common for employees, customers, vendors, and suppliers to have direct access to your networks whether they are inside your facility or not. The security of these channels is only as effective as the countermeasure you have deployed, which is sometimes just a password that they have chosen.
Well-intentioned people can be led astray. Phishing involves posing as a reputable entity in electronic communications with the aim of manipulating the recipient to reveal confidential information. To most eyes, the communication seems authentic, and the request to reply or click a link quite reasonable. The result, however, ranges from exposing passwords to releasing personally identifiable information, to encryption of data, to infecting a device with malware.
How should you evaluate these risks?
Fifty-six percent expect the most likely source of a cyber attack to be an employee. Thirty-six percent expect an external contractor working on-site. Only 31 percent of all third parties are risk-rated and have appropriate due diligence applied (EY, 2015).
What’s Hindering Your Cybersecurity Operations?
- “Smart” devices and services bring a mass of data, increasing vulnerabilities for exploitation; automation removes humans from decision-making processes. What is the appropriate balance between efficiency and security?
- Social media and “bring your own device” (BYOD) with employees, customers, citizens “always on” and sharing information—not fully appreciating the implications for privacy and confidentiality. How can organizations get employee attention that leads to positive behavior?
- Human frailty remains a serious risk, and one that’s difficult to manage. How should organizations evaluate people’s readiness for operating in a more security-minded way?
- Rafts of new legislation and regulations are forcing changes in processes, which means that other vulnerabilities are created, further changing the threat landscape, and the attack surface of an organization. What roles do governmental factors play in risk assessments?
Challenges from Within
Organizations need to know which threats represent the most urgent risk to the operation of your organization. You need a framework that brings together a communication strategy, cyber threat information, and the treatment options so that you can ask better questions, get better answers, and make better decisions. Security teams can have a hard time translating a broad vision or top-line strategy to a direct impact on specific critical assets.
Acting upon cybersecurity intelligence requires organizational discipline and integrated strategy. Figure 21.1 summarizes how a security operations center (SOC) acts as the linchpin between cybersecurity threats and effective response and management.
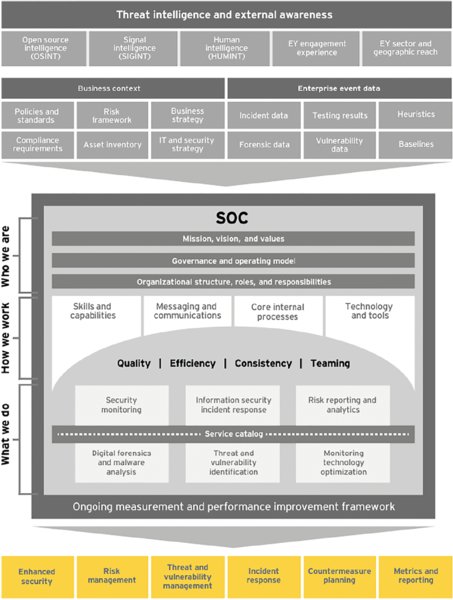
Figure 21.1 The big picture: How your organization can integrate and expand your cybersecurity protocol
Translating intelligence into action for organizations is hardly simple. Figure 21.2 offers a checklist to get started. It sets up the organization for the more specific steps it can take now that follows in the next section.

Figure 21.2 Checklist of do’s and don’ts for getting started
What to Do Now
Cyber risk prevention relies on the communications and operations teams’ support. Your organization should undertake the following tasks immediately.
Drive for Clarity
The lack of linkage down to physical assets, applications and ultimately data is a root cause for many of the communication and prioritization challenges. In the ideal situation, when a security operations team detects a potential compromise of a system, they should be able to communicate its organization impact. To be able to do that, they need to clearly understand what data is on what system, the value of that data, and what could go wrong with the organization if the system were to become unavailable, lost, or have an integrity issue or be compromised.
Fill in the Knowledge Gap
Understanding both the strategic and technical elements of the threat environment is challenging, and experience is a great teacher. Operations teams need front-line experience with behavioral analytics, insider threats modeling, advanced persistent threats groups, communication strategies, and state-sponsored actors. Your executive teams may not have this background, and the gap can create a frustrating communication issue, where security feels they must educate executives to enable them to make sound decisions and provide support. Executives accustomed to not knowing the details of such matters can be in denial about their complexity, increasing risk. Who wants to create a tense culture around security within the executive suite?
Understand the Speed of Change
We have designed security infrastructure historically on the premise that steady and continuous investments and an effort to “move the needle” year over year will allow organizations to keep pace and address the evolving threat landscape. Not anymore.
Security challenges are accelerating alongside the digital transformation, including robotics, artificial intelligence, analytics and so on, as mentioned earlier. New technology breeds broader attacks. You and your team do not have time to enact a multiyear investment strategy; your organization needs tools right now to disrupt, safeguard and recover from the next threat.
To push past the comfortable confines of “business as usual,” you need to understand how attackers think and how they act; your security team has to think like the attackers, understanding how they manipulate these new attack opportunities.
Know Your Assets
Understanding your critical organization risks and knowing what attackers may want from your organization enables you to establish targeted defense through prioritization (of assets, people, organization areas) and hardening of vulnerabilities. Assessing the threat landscape particular to your organization (based on your operating environment, critical assets, and organization strategy) allows you to understand the most likely threat actors and methods they may use, which can be played out in scenarios to gauge readiness.
This all informs your SOC and should be the basis on which it will support your organization. Putting in place a more advanced SOC and using cyber threat intelligence to effectively align operations helps enable you to conduct “active defense operations,” where you send intelligent feelers to look for potential attackers, analyze and assess the threat, and neutralize the threat before it can damage critical assets. Similarly, you can use an advanced SOC to operate in the same way and actively hunt down unwanted anomalies or confirmed attackers in your systems.
Make Cyber Risk More Tangible
You need a comprehensive threat radar that covers a variety of indicators and can raise communication triggers when a certain threshold is crossed. Each time your SOC analysts identify an attack in early stages, they can demonstrate value by extrapolating the damage that otherwise would have been caused had the scenario played out to its worst case. Organizations can continue adding to that value chain by adopting an “active defense” process.
In “active defense,” you gain a dynamic and proactive component to security operations, integrating and enhancing existing security capabilities to yield greater effectiveness against attackers. Adopting an iterative cycle with built-in mechanisms for continuous improvement, you can realize gains in efficiency, accountability, and governance capabilities, which translate directly into improved return on investment (ROI).
Adapt to Your Environment—Establish/Improve Your SOC
The most essential action for organizations is to either set up or revisit an SOC that brings together the relevant systems and constituencies required to monitor, analyze, and respond to the threat environment. A mature SOC can prioritize what needs to be protected by defining the communication strategies and leveraging advances in technology to operate more efficiently and effectively. The initiation, integration, and advancement of core SOC capabilities is crucial to the success of security operations.
An effective SOC has these characteristics.
- Monitoring and response. The SOC monitors for threat indicators to detect attacks before critical company services are disrupted or high-value assets compromised. SOC personnel also conduct investigations to determine cause and scope of security incidents, coordinate containment, and recovery and communication activities.
- Cyber threat intelligence capabilities are more than simply data. Intelligence is information from sources from technical logs to news reporting that has been analyzed. It should quantify and qualify threats, be timely, accurate, actionable and relevant, and be used to establish a threat level and drive appropriate strategic and tactical countermeasures. A mature cyber threat intelligence program also provides forecasting to inform an organization’s decision makers and support operations.
- Vulnerability management is the function responsible for proactively identifying, assessing and consistently managing the organization’s exposure to cyber attacks, and tracking, validating and providing metrics on the remediation of vulnerabilities. It must be integrated into other enterprise functions and should encompass all vulnerabilities.
- Today’s SOCs have the task of monitoring enormous volumes of data to find pieces of information that signify an event worthy of action or further review. The SOC can bring unique value to that effort by using behavior-based analytics on the data providing visibility into trends and patterns that may have been obscured otherwise. Through that analysis we are able to innovate in real time, reducing development life cycles by orders of magnitude. This shifts the traditional security operations paradigm from reactive to proactive and enables agility and innovation at the speed of attackers.
Adapt Your Organization
In the age of digital transformation, the speed of change, combined with ineffective communications, a lack of understanding of what is important and an executive knowledge gap, creates an environment in which security operations teams are not able to be as agile as needed. In response, organizations are recognizing the opportunity to leapfrog their competitors and threats by avoiding attachment to prior investment decisions. That requires a high level of executive sponsorship and awareness of security, as well as confidence that outcomes may be more easily achieved through new technologies and concepts.
Conclusion
The following cyber risk management statement represents those organization capabilities the CEO and the board expect to be demonstrated in terms of cybersecurity for communications and operations.
About EY
EY is a global leader in assurance, tax, transaction and advisory services. The insights and services we deliver help build trust and confidence in the capital markets and in economies the world over. We play a critical role in building a better working world for our people, for our clients and for our communities.
About Chad Holmes
Chad Holmes is a principal, CTO, and Strategy, Technology and Growth leader for the EY Advisory Cybersecurity practice. Chad has over 18 years of experience in cybersecurity and has held leadership roles in high-tech security companies, health care, architecture, and financial organizations.
About James Phillippe
James Phillippe is a principal in Advisory at EY. He serves as EY’s Global Cyber Threat Management leader, which includes responsibility for the global network of Advanced Security Centers (ASCs). James has over 18 years of experience and has held a leadership role within the ASCs since their creation in 2002.
