CHAPTER SIXTEEN
High-Tech Banking—E-Payment Systems and Electronic Banking
CHAPTER STRUCTURE
Section III Retail Payment Systems
Section IV Plastic Money and E-Money
Section V Security Issues in E-Banking
KEY TAKEAWAYS FROM THE CHAPTER
- Understand how technology helps banks and customers.
- Learn about electronic payment and settlement systems.
- Understand e-banking—the concepts and the benefits.
- Understand retail payment systems and their benefits to banks and customers.
- Learn the concepts and usage of plastic money such as credit cards, debit cards, etc.
- Be aware of the security issues in e-banking.
SECTION I
BASIC CONCEPTS
Why Do We Need Technology in Banking?
Welcome to the digital age in banking. Over the last couple of decades, technology has assumed the vital role of not only a facilitator, but also a source of competitive advantage for banks. During the 1990s, efficiency and cost-cutting used to be the primary objectives of banks turning to new technology. At present, banks have evolved a strategic approach towards their investments in technology, since they have found that both revenue enhancement and cost-effectiveness count in their constant endeavour to improve their ROA and ROE.
The business of banking—especially financial services/retail banking—is undergoing a sea change, as business shifts increasingly to the online environment. The increasing number of customers transacting online woul move the ‘market place’ to ‘market space’, where banks would be forced to expand their product range to competitors’ products, while rapidly innovating their own value-added products.
Technology, and more specifically, the Internet, has evolved into an essential access channel. For banks, the Internet offers a cost effective means of innovating, publicizing and delivering services to the customer, as well as maintaining customer relationships. For the customer, the Internet has opened up enormous possibilities of convenience and choice.
Let us understand the role of technology as an enabler for improved transaction efficiency through the categorization provided in Figure 16.1.
FIGURE 16.1 CATEGORIZING FINANCIAL TRANSACTIONS THROUGH TECHNOLOGY

The effect of technology in banking has been dramatic. The bank-to-customer relationship has changed significantly, with open standards replacing proprietary front ends, and many-to-many networks substituting for single-line links. Most banks, today use Internet as their global expansion platform, offering an increasing array of financial services online.
Benefits of Electronic Banking
For Banks
The benefits of electronic banking (e-banking) for banks are as follows:
- Price: In the long run, a bank can reduce expenses by not paying for tellers or for managing branches. Also it is cheaper to make transactions over the Internet.
- Customer base: The Internet allows banks to reach new markets and high net worth individual, because there are no geographic boundaries with the Internet. The Internet also provides a level playing field for small banks who want to add to their customer base.
- Efficiency: Banks can become more efficient by providing Internet access for their customers. The Internet provides the bank with an almost paperless system.
- Customer service and satisfaction: Banking on the Internet not only allows the customer to access full range of available services but it also provides some services not offered at any of the branches. The customers can print information, forms and applications via the Internet and search for information efficiently instead of waiting in line and asking bank employees. With better and faster options, a bank will surely be able to create better customer relations and satisfaction.
- Image: A bank seems more state-of-the-art to a customer if they offer Internet access. A person may not want to use e-banking but having the service available gives a person the feeling that the bank is on the cutting edge.
For Customers
The benefits of e-banking for customers are as follows:
- Systematically Important Payment Systems (SIPS):High value clearing and Real Time Gross Settlement (RTGS) are classified under this category since they benefit large corporate and high net worth customers. Steps have already been initiated to merge the two payment services—the high-value clearing threshold has been raised from `1 lakh to `10 lakh, with the intention of progressively discontinuing the service, due to the availability of alternate channels for high-value transactions.
- Financial markets clearing and other important retail payment facilities: Financial markets clearing is intended primarily for government securities and foreign exchange markets. Retail payment systems, such as e-banking, give customer the control over nearly every aspect of managing his bank accounts. The customers can, buy and sell securities, check stock market information, check currency rates, check balances, see which cheques are cleared, transfer money, view transaction history and avoid going to an actual bank. The best benefit is that e-banking is free. At many banks the customer does not have to maintain a required minimum balance.
SECTION II
E-PAymENTS
The Importance of Payments and Settlement Systems
An important ingredient of an efficient and deep financial system is the ability of intermediaries to effect smooth and secure transfers of money and exchange financial claims embedded in financial instruments. The security of payment and settlement systems is critical for sustaining public trust in the financial intermediaries. (Please also see Chapter 1 where we discussed the role of ‘trust’ as the backbone of the financial system).
Hence central banks, as supervisors and regulators of payments and settlement systems through financial intermediaries, have to ensure development of efficient and secure systems to match the explosion in needs and sophistication of the financial sector.
Technology has been a primary contributor to new and innovative products and methods of payments and settlement in various countries around the world. Similarly, the power of technology has been harnessed to enable central banks to carry out their regulatory and supervisory roles as well.
International Standards and Codes for Payment and Settlement Systems
The Committee on Payment and Settlement Systems (CPSS) was set up by the Bank for International Settlements (BIS, www.bis.org, please also refer to chapter on Capital Adequacy) as a standing committee, with the objectivet of strengthening financial market infrastructure through promoting sound and efficient payment and settlement systems.
CPSS was formed by G 10 central banks in 2001 with the specific objective of formulating broad supervisory standards and guidelines for payment and settlement systems. It serves as a forum for central banks to monitor and analyse developments in domestic payment, clearing and settlement systems as well as in cross-border and multicurrency settlement schemes. The membership of CPSS has widened beyond the G10 countries, to include about 25 central banks in 2009. The RBI is a member of CPSS.
The Committee has also forged relationships with many non-CPSS central banks in order to help strengthen payment systems globally. Apart from setting standards, the CPSS also publishes reference works on payment systems in select countries—widely known as the ‘Red book’.
After formalizing the ‘Core Principles of Systemically Important Payment Systems’ in 2001, CPSS published in 2002, along with IOSCO, its ‘Recommendations for Securities Settlement Systems (SSS)’. This was followed up with the CPSS-IOSCO ‘Recommendations for Central counter parties (CCP)’ in 2004. Box 16.1 summarizes the CPSS core principles and recommendations.
BOX 16.1 CPSS—CORE PRINCIPLES AND RECOMMENDATIONS
- CPSS core principles for Systematically Important Payment Systems (SIPS)
The CPSS defines payment systems as a ‘set of instruments, procedures and rules for the transfer of funds among system participants’. SIPS is further defined as the ‘payment systems which, if it is insufficiently protected against credit, liquidity, legal, operational and other risks, the disruptions within the system could trigger or transmit further disruptions among its participants, or generate systemic disruptions in the financial markets or more widely across the economy’. Accordingly, a system is considered SIPS if at least one of the following conditions is met—(a) it is the only or the principal payment system or the principal system in terms of the aggregate value of payments, (b) it handles mostly payments of high individual value, and (c) it is used for the settlement of financial market or other payment systems.
- CPSS–IOSCO Recommendations for Securities Settlement Systems (SSS)
The 19 recommendations for SSS can be construed as ‘standards’ to enhance safety and efficiency. The recommendations/standards cover all aspects of securities settlements, particularly, the legal framework, settlement cycles, central counterparties, operational reliability, governance, transparency, regulation and oversight.
- CPSS–IOSCO Recommendations for Central Counter Parties (CCP)
We have seen in earlier chapters that the role of a CCP is to reduce risk to market participants by interposing itself between counterparties to financial contracts, imposing controls and enhancing liquidity. However, failure of risk management of a CCP could have catastrophic consequences on markets as well as payment and settlement systems. The 15 recommendations (in the nature of standards) for CCPs broadly cover the legal and participation requirements, risk management procedures, operational reliability, efficiency, governance, transparency, regulation and oversight.
It is to be noted that CPSS has not set specific standards for Retail Payment Systems.
Payment and Settlement Systems in India
The RBI has spearheaded a vast change in the use of technology for making banking in India safer, more secure, smoother and more efficient. RBI was empowered in 2007 through the enactment of the Payment and Settlement Act, 2007, to regulate and supervise payment and settlement systems in India, formulate relevant policies and provide a legal basis for multilateral netting and settlement finality. To operationalize the Act, RBI framed the ‘Board for Regulation and Supervision of Payment and Settlement Systems Regulations, 2008’ and ‘Payment and Settlement Systems Regulations, 2008’.
Payment systems in India can be bifurcated into ‘paper-based’ and ‘electronic’ payment systems. Another classification, based on users, can be into ‘large-value payment systems’ and ‘retail payment systems’. See Figure 16.2 for the components of each classification.
FIGURE 16.2 ALTERNATE CLASSIFICATION OF PAYMENT SYSTEMS

We can infer from Figure 16.2, that while the classification ‘paper-based’ versus ‘electronic’ conveys the mode of payment and settlement, the alternate classification—‘large value’ versus ‘retail’—convey their relative importance to the stability of the financial system.
The large-value system (sometimes also termed ‘bulk payment system’) is characterized by relatively low volumes but high values, as contrasted with retail payment systems where high volumes (number of transactions) and low values are typical. Being high value, the large value payment system carries systemic risks that could affect the stability of the payment systems of the financial sector as a whole. Therefore, according to the BIS (CPSS) standards, both high-value clearing and RTGS would be classified as SIPS.
Though retail payments are not termed ‘SIPS’, their relative importance to the economy cannot be undermined due to the sheer volume and geographical coverage that these systems demand.
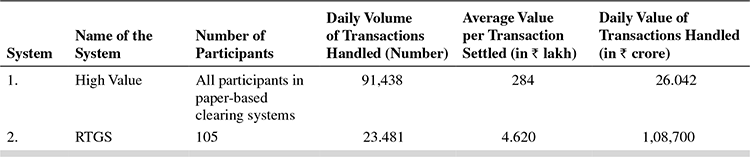
Box 16.2 describes the salient features of RTGS, the fastest growing segment of SIPS.
BOX 16.2 SALIENT FEATURES OF RTGS
The Rationale
The traditional payment system involves settlement of payments on a settlement day (next day, 2 days after and so on) and interest is invariably computed to accrue on a daily basis. Even in the inter-bank foreign exchange and money market contracts, spot transaction means 2 business days. Settlement for clearing cheques presented to clearing houses takes place on a netting basis at a particular time either on same day or on the next day. These conventions make sense, when book-keeping is done manually. However, this system gives rise to risks, such as credit risk, liquidity risk, operational risk, legal risk and systemic risk. Such risks could cause widespread liquidity problems.
The RTGS, was introduced to solve these problems in the banking sector. It is a software package which provides an online settlement of payments between financial institutions, i.e., bank to bank fund transfer and settlement same day. In this system, payment instructions between banks are processed and settled individually and continuously throughout the day. This is in contrast to net settlement that takes place only afterwards, typically at the end of the day. Under the RTGS system, payee banks and their customers receive funds during the day, enabling them to use the funds immediately without exposing themselves to risk. To initiate a fund transfer, the bank has to send a payment message, which is subsequently routed to the central bank and to the receiving bank as the system processes and settles the transfer. The RTGS system settles payments on a transaction-by-transaction basis as soon as they are accepted by the system. It is a large-value fund transfer system whereby financial intermediaries can settle inter-bank transfers for their own account as well as for their customers.
RTGS in India
Operationalized as part of SIPS in March 2004, the RTGS began with four banks settling only interbank transactions. In 2006, it was expanded to customer transactions (multilateral net settlement). The RTGS operated with 105 members in 2009.
The first transaction was put through by the State Bank of India, which made an interbank payment. The RTGS system now allows high-value customer payments to happen through this system. High value for the purpose of RTGS is defined as transactions of ₹1 lakh (0.1 million) and above. Subsequently, all customer payments would be enabled on the RTGS system.
The RTGS system is owned and operated by the RBI. Direct membership is restricted and open to commercial banks, primary dealers, clearing houses and others as decided by RBI. The commercial banks are called ‘type A’ members, which enables them to submit customer-based transactions. Primary dealers are ‘type B’ and clearing houses ‘type D’ members. RTGS membership and operations are governed by RTGS Membership Regulations and Business Operating guidelines, 2004 (and subsequent amendments).
Settlement of RTGS transactions are done in the RBI books. To enable them transact, members open an ‘RTGS settlement account’ with the RBI, Mumbai. The member has to fund this account at the beginning of every RTGS processing day from the member‘s current account with RBI. At the end of the day, the balance in the account is swept back to the member’s current account.
Members are provided with a participant interface gateway server with which participants/members connect to the RBI system through the INFINET.1 The software is supplied by the RBI. The banks procure the hardware, which is specified by the RBI. Participants are advised to get a dedicated lease line link between PT gateway and the local hub of the RBI.
RTGS is a gross settlement system in which both processing and final settlement of fund transfer instructions take place continuously (i.e., in real time). As it is a gross settlement system, fund transfers are settled individually, without netting debits against credits. RTGS systems are able to minimize or eliminate the inter-bank risks in the settlement process.
The RTGS system has reduced the time for processing payments from 24 hours (which could go up to a week) for cheques at present, to a matter of a few minutes. The launch of the system is expected to phase out cheques from the banking system in due course. Importantly, RTGS systems can offer a powerful mechanism for reducing systemic risk. As central banks have a common interest in limiting systemic risk, this capability has often been the key motive for many central banks to adopt the RTGS system for larger-value money transfer.
SECTION III
RETAIL PAymENT SySTEmS
Retail payment systems are required primarily for purposes such as payments for goods and services, bill payments, cash payments and so on. Figure 16.3 shows the major purposes for individuals to require e-banking facilities, and the instruments available to satisfy the requirements.
FIGURE 16.3 E-BANKING—PURPOSE AND INSTRUMENTS AVAILABLE
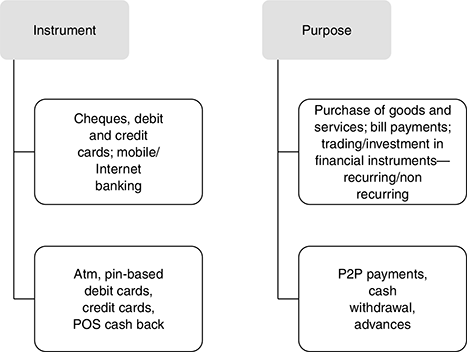
To achieve the purposes shown in Figure 16.3, retail customers can resort to paper-based clearing and settlement or electronic payment and settlement, as shown in Figure 16.2.
The paper-based payment and settlement mechanisms in vogue in India are as follows:
- Magnetic Ink Character Recognition (MICR) and non-MICR cheques
- High-value clearing
- Speed clearing of cheques drawn on outstation CBS branches of drawee bank processed in local clearing
- Cheque truncation
The Electronic clearing and settlement systems being operated are as follows:
- Electronic Clearing Service (ECS), National Electronic Clearing Service (NECS)
- Electronic Funds Transfer (EFT)
- National Electronic Funds Transfer (NEFT)
While the volume of electronic transactions has grown over the years, the value of electronic transactions has far exceeded paper-based transactions during this period. One obvious inference is that electronic transactions have become more popular in high-value transactions than in retail payment systems.
Paper-Based Instruments in Retail Payment Systems—An Overview
- Cheques: The most common form of notational money 2 is an account with cheque facility. A cheque is an order authorizing the transfer of money from one account to another. When a cheque is accepted as payment, the recipient’s bank collects the value of the cheque after presenting it to the bank on which it is drawn. Cheques can be returned for insufficient funds. The person who wrote the cheque can stop payment on it by notifying the bank that holds the account if a cheque is lost or stolen. Apart from cheques as described above, there are banker’s cheques and demand drafts, which are special kinds of cheques. A banker’s cheque is drawn by a bank on its own funds. It is a direct obligation of the bank—hence individual consumers cannot write banker’s cheques. A demand draft is guaranteed to be good by the bank on which it is drawn. Both banker’s cheques and demand drafts are considered insured deposits.
Traveller’s cheques are also included in a bank’s net transaction accounts and are subject to reserve requirements.3 Traveller’s cheques issued by a bank are covered by deposit insurance.
The clearing and settlement of cheques drawn on different banks necessitates banks in the area coming together for transfer of funds and final settlement. This is done through ‘clearing houses’ at various centres. Further, where the process was manual hitherto, as in the 1029 non-MICR clearing houses at various centres, Magnetic Media-based clearing system is also implemented.
The clearing and settlement process takes two days—on day 1, the cheques are presented at the clearing house, and on day 2, the funds are settled or cheques returned.
The volume and value of paper-based cheques have been increasing over the years, but at a declining rate, presumably due to the impact of electronic payment systems (see Table 16.1).
- Magnetic Ink Character Recognition (MICR): Magnetic Ink Character Recognition is a character recognition system that uses special ink and character. The cheque, which contains this ink, needs to be read, and passed through a machine, which magnetizes the ink and then translates the magnetic information into characters. Banks use MICR technology on cheques, which provides secure, high-speed method of scanning and processing information.
- Speed clearing: This new clearing arrangement was introduced in India in 2008 for collection of outstation cheques through local clearing, provided such cheques were drawn on ‘core banking’4 solution (CBS) enabled branches of paying banks. Cheques drawn on outstation CBS branches of a bank can be processed in local clearing, thus, reducing the time taken for realization of outstation cheques, thus enabling payment on a (T + 1) or (T + 2) basis. Speed clearing had been introduced at 53 centres as of March 2009.
- High-value clearing: This is a paper-based clearing for large value payments, currently operational at 27 major cities. The clearing process is completed on the same day for cheques of ₹1 lakh and above payable in the same city. This means that the cheque proceeds will be received and can be withdrawn by the beneficiary the same day. Table 16.1 shows the volume of transactions in SIPS in India. It can be seen that while the value of transactions handled is much lower compared with RTGS, the number of transactions is much higher. However, with RTGS picking up, high-value clearing process may be gradually phased out. As a first step, a decision has been taken by the RBI that no new high-value clearing centres would be opened.
- 5. Cheque truncation: We have seen from the discussion above that the use of electronic payment systems is increasing due to the advantages that such systems offer to the customer. However, since paper-based payment systems continue to be used in a big way, cheque truncation was introduced to speed up the process of cheque clearing, and thus reduce the cost of transit or possibility of loss of cheque in transit, thus enhancing customer service.
Truncation is the process of stopping the transit of a paper-based cheque from the drawer to the drawee branch of a bank. The physical cheque will be ‘truncated’ at some point en route to the drawee branch, and would be replaced by an electronic image of the cheque. Cheque truncation, thus is a more secure alternative to the actual movement of physical instruments from place to place.
Cheque truncation has been introduced in the national capital region (NCR), New Delhi on a pilot basis, and will be extended to more centres. The process is expected to be more efficient and cost effective, especially in the case of clearing and settlement of outstation cheques.
Member banks of clearing house in the NCR and INFINET can participate in the cheque truncation system.
Electronic Retail Payment Systems—An Overview
Electronic Clearing Service (ECS)
Bulk and repetitive payments like interest/dividend are mostly paper-based involving printing of warrants (in costly MICR format), dispatching them by post and reconciliation thereof after payment by the agency banks. The difficulties are as follows:
- It requires an expensive administrative machinery for printing, dispatching and reconciliation.
- Bunching of a large number of instruments in clearing results in operational bottlenecks and pressures on the cheque processing system.
- Chances of loss of instruments in transit and their fraudulent encashment.
- The customer has also to keep track of the receipt/non-receipt of the instrument and take efforts to deposit the instrument with the bank on receipt of the same.
- Banks find processing of such a large volume of instruments not only error prone and monotonous, but also a strain on the cheque clearing system.
ECS is a retail payment system that facilitates bulk payments (such as dividend payment) and bulk receipts (such as utility payments). These two aspects are handled by two components of the system—ECS (credit) and ECS (debit). The facility is available at 75 major centres as of 2009.
- ECS (Credit): ECS (Credit) facilitates bulk payments, where an institution makes payment to several retail customers. Examples are payment of dividend/interest warrants to investors, payment of salaries to employees and so on. In such cases, it follows that the account of the institution remitting the payment should be debited and the payments remitted to beneficiaries’ accounts. Hence, the company or entity making the payment has to have the bank account details of the individual beneficiaries.
- ECS (Debit): ECS (Debit) is the opposite of ECS (credit). Here, many individuals/ firms pay to one firm or utility. Thus, the accounts of various customers of the utility in different banks have to be debited and the amounts have to be credited to the utility company’s account with designated banks. Using a specific mandate, the utility can also advise the customers’ banks to debit payments on due dates.
Settlement in this system currently takes place on (T + 0) basis and the cycle gets completed on (T + 1) basis. The clearing and settlement transactions through ECS occur at the respective centres.
- ECS (Centralized): A third facility called the NECS is centralized and available at the Reserve Bank, Mumbai. NECS-Credit, like ECS (credit), facilitates multiple credits to beneficiary accounts at destination branches across the country against a single debit in the account of a user with the sponsor bank from a single central location at Mumbai. Similarly, the NECS-Debit would facilitate multiple debits to destination account holders across the country against a single credit to the user account at Mumbai. The NECS is a nationwide system leveraging on CBS of member banks. All CBS bank branches are participants in the system, irrespective of their location. As of 31 March 2009, as many as 114 banks with 26,275 branches participated in NECS.
The ECS systems works in the following steps:
Step 1:The corporate body institution (called user) which has to make payments to a large number of customers/ investors would prepare the payment data on a magnetic media (i.e., tape or floppy) and submit the same to its banker (sponsor bank).
Step 2: The sponsor bank would present the payment data to the local bankers’ clearing house (managed by the Reserve Bank of India at 15 centres and by the State Bank of India or associate banks at 31 other centres) authorizing the manager of the clearing house to debit the sponsor bank’s account and credit the accounts (destination bank) of the banks where the beneficiaries of the transactions maintain their accounts.
Step 3: On receiving this authorization, the clearing house will process the data and work out an inter-bank funds settlement.
Step 4: The clearing house will furnish to the service branches of the destination banks branch-wise credit reports indicating the beneficiary details, such as the names of the branches where the accounts are maintained, the names of the beneficiaries, account type, account numbers and the respective amounts.
Step 5: The service branches will, in turn, pass on the advices to the concerned branches of their bank, which will credit the beneficiaries’ accounts on the appointed date.
Benefit to an organization: The ECS system offers following benefits to an organization.
- Savings in administrative cost presently being incurred for printing of paper instruments in MICR format and dispatching them by registered post.
- Loss of instruments in transit or fraudulent encashment thereof totally eliminated.
- Reconciliation of transactions is made automatic. By the time the ECS cycle is completed, the user institution gets an electronic data file from its bank with the date of payment and banker’s confirmation thereon.
- Cash management becomes easier as arrangement for funds is required to be made only on the specified date.
- Ensuring better customer/investor service.
- Paying the way the best companies in the world pay to their shareholders/investors and customers.
Benefit to the customer: The ECS system offers following benefits to the customers.
- Payment on the due date.
- Effortless receipt—no need to visit the bank to deposite the dividend/interest warrant.
- Probability of loss of instrument in transit or fraudulent encashment thereof and consequent correspondence with the company are completely eliminated.
Electronic Funds Transfer (EFT) and National Electronic Funds Transfer (NEFT)
Electronic funds transfer system was introduced by RBI in 1997 as an inter-city, intra-city and inter-bank, intra-bank fund transfer mechanism by which funds can be transferred by any bank branch to any other bank branch from one city to another. EFTs process pre-authorized debits or credits from one bank account to another within a 48-hour period. It is similar to standing instructions maintained in customers’ accounts, which are carried out automatically at pre-appointed dates.
First, customers have to sign a form that authorizes the bank to deduct their payment on a certain date. Details, such as the payee and beneficiary’s account, amount and date are programmed into the account. According to the billing cycle, the amount of customers’ bill is then automatically debited from their checking account and deposited into the payees’ account. In the case of payroll, the account is debited and employee’s account is credited for each pay period.
The key benefits of EFTs are as follows.
- For receivables, benefits include prompt payment of customers’ bills each month and early notice of insufficient funds. While there is a small fee per transaction for this service, EFTs eliminate the need to print, process and send a monthly bill in many instances. It is estimated that an EFT can save as much as USD 2.25 to USD 3.00 or more per customer. Thus, it lowers labour cost to prepare statements as well as postage and the cost of paper used to print statements. EFTs also reduce late payments and the need to send out reminder notices.
- EFTs can actually increase customer retention. This is most likely to occur in businesses that bill the same amount on a month-to-month basis for ongoing services, such as pest control companies, newspapers, pool services, security companies and the like. Having the fee automatically deducted from the customer’s checking account increases the retention of those who might otherwise let the service lapse.
- It saves on billing and administrative costs, dramatically improves cash flow and eliminates many collection hassles.
The EFT system was replaced in November 2005 by the NEFT, an electronic message-based payment system using Public Key Infrastructure6 technology to ensure end to end security. NEFT uses the INFINET to connect bank branches for electronic transfer of funds. NEFT was available at about 63,000 branches of various banks at the end of 2009. To make NEFT more retail customer friendly, RBI has permitted initiation of transactions by accepting cash from walk in customers (earlier account to account transfers were mandatory), permitting credit card payments and extending settlement time. These measures have yielded tangible results in the forms of sizeable increase in retail electronic fund transfers during 2008–09 (please see Table 16.1). Several changes/upgraded versions of the software and security features are being released periodically by RBI.
Participants in the clearing and settlement process: Information technology has revolutionized the way payments and settlements are being done throughout the world. The Indian system has also seen several innovations, in line with international recommendations and standards (see Box 16.1), though some of them are yet to penetrate the entire market.
Box 16.3 provides an overview of the various participants in the clearing and settlement process
BOX 16.37 MAIN PARTICIPANTS IN THE CLEARING AND SETTLEMENT PROCESS
Clearing corporation: The clearing corporation is responsible for post-trade activities such as the risk management, confirmation, delivery and settlement of trades executed on a stock exchange.
Clearing members: Clearing members are responsible for settling these obligations as determined by the clearing house/ clearing corporation. They do so by making available funds and/or securities in the designated accounts with clearing bank/ depositories on the date of settlement.
Custodians: Custodians are clearing members but not trading members. They settle trades on behalf of trading members, when a particular trade is assigned to them for settlement. The custodian is required to confirm whether he is going to settle that trade or not. If he confirms to settle the trade, then clearing corporation assigns that particular obligation to him.
Clearing banks: Clearing banks are a key link between the clearing members and clearing corporation/house to effect settlement of funds. Every clearing member is required to open a dedicated clearing account with one of the designated clearing banks. Based on the clearing member’s obligation as determined through clearing, the clearing member makes funds available in the clearing account for the pay-in and receives funds in case of a pay-out.
Depositories: Depository holds securities in dematerialized form for the investors in their beneficiary accounts. Each clearing member is required to maintain a clearing pool account with the depositories. He is required to make available the required securities in the designated account on settlement day. The depository runs an electronic file to transfer the securities from accounts of the custodians/clearing member to that of clearing corporation/house and viceversa as per the schedule of allocation of securities.
Professional clearing member:NSCCL admits special category of members known as professional clearing members (PCMs). PCMs may clear and settle trades excuted for their clients (individuals, institutions, etc). In such cases, the functions and responsibilities of the PCM are similar to that of the custodians. PCMs also undertake clearing and settlement responsibilities of the trading members. The PCM in this case has no trading rights, but has clearing rights, i.e., he clears the trades of his associate trading members and institutional clients.
SECTION IV
PLASTIC MONEY AND E-MONEY
Plastic money refers to substitution of currency at the time when a payment is taking place by using a card normally made of plastic (hence the name, plastic cards) representing such substitution.
There can be several objectives for such substitution. Most important among these would be the need to postpone actual payment, or pre-purchase payment on the card that is issued. Whatever be the objective, the most important advantage of plastic money is protection to the user from the risks of carrying cash. Since it is the exclusive property of the cardholder, it means that it can be used only by him.
The prevalent types of plastic money are:
- Credit Cards
- Debit Cards
- Other payment channels/products
Credit Cards
Credit cards started off as a type of payment cards issued by some merchants for the convenience of their customers. It is believed that the first such card was issued by Sears in 1910, which was quickly emulated by other retailers who issued cards containing vital information about the customer, which was recorded when the card was put through a processing device. The popular ‘Diner’s Club’ card was introduced in 1949 to be used in multiple restaurants that were willing to participate in the scheme. It is to be noted here that these cards had to be paid in full each month, and, therefore, had very little ‘credit’ or ‘loan’ component to them.
Today, credit cards are synonymous with a form of short term, revolving credit to the cardholder. As pointed out in the chapter on bank lending, a revolving credit replenishes automatically when loan installments are met. For typical card accounts in the form of revolving credit, the cardholders are billed monthly for purchases made with the credit card. Every month, cardholders have the option of paying back the entire outstanding amount on the credit card, or the minimum payment stipulated, say 2 per cent or 3 per cent of the outstanding balance. Typically, a grace period of about a month or more is granted, during which no interest will be charged on the ‘loan’. Cardholders who pay the minimum amount every month are considered current on their account. If one payment is not made on time, the account would be considered delinquent after a predetermined period. Hence, it is evident that credit card is very similar to a loan account with a bank.
Credit cards can be issued through various channels. The most common are ‘general purpose’ cards, such as Visa or MasterCard. These are accepted by most merchants/retailers. It is also the practice of individual banks to issue co-branded cards with Visa or Master network.
Credit cards can be broadly classified into three types. These are as follows:
- Bank cards, i.e., MasterCard, Visa, Maestro, etc.—This type of cards are sponsored by individual banks and considered all-purpose cards. Each bank decides credit limits, annual fees, terms and conditions.
- Travel and Entertainment cards, e.g., American Express or Diner’s Club—This type of cards are used by people for travel and entertainment expenses. In many cases, unlike credit cards, cardholders are expected to pay the balance outstanding in full every month. Hence, while credit cards permit users to carry balances over several months, provided the minimum payment is made every month, ‘travel and entertainment’ cardholders will have to pay back the ‘credit’ in 1 or 2 months at most.
- Company or Retail Store cards, such as Walmart, Reliance, BP, Shell or Mobil—This type of cards are used in the retail store or gas station. These are issuer-specific and cannot be used for all purposes as can be done for bank-issued credit cards.
The Parties to Credit Card Transactions
The following are the principal players in credit card transactions:
- Card issuers
- Card holders/users
- Member establishments (MEs)
- Member affiliates (MAs)
- Clearing agencies
- Credit card affiliates
The role of each party in credit card transactions is described briefly in the following paragraphs:
- Card issuers: Card issuers are predominantly banks. Almost all banks today offer credit card services to retail customers. Credit card business is attractive to banks because of the potentially high returns. For example, banks charge member establishments (ME) a commission of about 2 per cent. To customers, banks offer a credit period of about 45 days, but charge at the rate of say 2.5 per cent per month on the entire outstanding amount at the end of the credit period. Thus, on a single purchase through a credit card, assuming the customer does not pay within the credit period, the bank can earn up to 4.5–5 per cent per month, which is a significant 55–60 per cent per year. From our discussion on corporate lending in earlier chapters, it is clear that banks do not earn such high returns on other types of advances.
Of course, credit cards also mean cost to the bank—the cost of marketing the credit cards, making of the card with tamper proof features, credit information, processing, investigation, follow up to recover receivables, bad debt losses at the other end of the spectrum—that can be quite high.
- Card holders: The cardholders or users could be individuals or business entities. As for other types of lending, the amount that can be drawn against the credit card is based on creditworthiness criteria. After his account gets approved by the credit issuer bank, the customer is issued a credit card, with which the customer would be able to make purchases from merchants accepting that credit card up to a pre-established credit limit.
- Member Establishments (ME): These are the establishments/ merchants who accept valid credit cards as payment for goods/services, in place of cash. MEs can be large retail establishments, restaurants, hospitals, gas filling stations, travel agencies—in short, any entity which can generate a good volume of business to justify usage of credit cards. As mentioned earlier, MEs will have to pay a ‘fee’ in the form of commission for every credit card payment they accept. Sometimes, this fee is passed on to the cardholder, which implies that the cardholder pays more for usage of the card.
- Member Affiliates (MA): A large organization that wishes to issue credit cards in its name without investing in the elaborate infrastructure for servicing credit cards may opt for the ‘affiliate’ route. The affiliate enters into an agreement with a card issuer, who authorizes the affiliate to issue credit cards in its name, along with that of the original issuer. Many large hotel chains are MAs. The other kind of affiliate arrangement could happen between banks as well.
- Clearing agencies or card associations: Mastercard international and Visa international are the two leading international card issuers who also act as clearing agencies. The card issuers associate themselves with one of these agencies to enable the cardholder of one affiliate to use the card at the member establishment of another affiliate. They are also called ‘credit card affiliates’ when the logos of both the clearing agency and the issuer are embossed on the face of the card.
Box 16.4 describes how credit card settlements are made in practice where affiliates are involved.
BOX 16.4 SETTLEMENTS PROCESS THROUGH CREDIT CARD NETWORKS
When a purchase is made, the credit card holder agrees to pay the card issuer. The cardholder gives his or her consent to pay, by signing a receipt with a record of the card details and indicating the amount to be paid or by entering a Personal Identification Number (PIN). Also, many merchants now accept verbal authorizations in person or via telephone and electronic authorization using the Internet, known as a Card Not Present (CNP) transaction.
Electronic verification systems allow merchants to verify, almost immediately, that the card is valid and the credit card customer has sufficient credit to cover the purchase. The verification is performed using a credit card payment terminal or Point of Sale (POS) system with a communications link to the merchant’s acquiring bank. Data from the card is obtained from a magnetic stripe or chip on the card.
The process works as follows:
Step 1: A Visa or MasterCard cardholder makes a purchase from an ME.
Step 2: The ME transmits the transaction information to his bank—called the ‘acquirer’. The acquirer contacts the card-issuing bank with the details through the card association (Master or Visa) requesting authorization of the transaction.
Step 3: The card-issuing bank verifies that the transaction is bona fide, and passing the transaction would keep the outstanding balance on the card within sanctioned limits. Thereafter, the transaction is authorized.
Step 4: The ME now requests for payment from his bank, which in turn, routes the request to the card association.
Step 5: The card association processes the request for payment with the acquirer and the issuer, and requests the issuer to make payment.
Step 6: The card association forwards payment to the acquirer, after deducting its fees for mediation, as well as the issuer’s fee for the transaction
Step 7: The issuing bank transmits funds (less its fee) to the card association
Step 8: The acquirer pays the ME for the cardholder’s purchase, after deducting its fee.
Step 9: The cardholder gets his monthly statement from the issuing bank at the end of the billing cycle, reflecting the payment to the ME.
How Do Credit Card Issuers Make Money?
There are three main sources of income for credit card issuers—fees paid by MEs, interest on cardholder balances and other fees charged to cardholders. A Visa or Mastercard affiliation involves more than a simple transaction between customer and the ME, as we can see from the process described above. In this case, the issuing bank takes a major share of the merchant’s discount (say ₹1.50 out of ₹2 on every ₹100 transaction), while the acquiring bank would take ₹0.50. Apart from interest payable by the cardholder on unpaid balances on the credit card, the issuing bank earns from other charges, such as annual charges, penalty fees for late payments, over the limit transactions, fees for cash advances and so on.
The ‘expenses’ of credit card issuers can be classified into four main categories—(a) marketing and operations that account for a bulk of the expenses; (b) cost of funds (see chapter on loan pricing); (c) losses due to delinquencies or write-offs where outstanding balances could not be recovered; and (d) losses due to frauds. (We will discuss ‘Internet frauds’ in the following section.).
The marketing and operations expenses increase as card issuers compete to differentiate themselves in the market. It is not uncommon to see and own cards with additional benefits such as insurance coverage, purchase protection, rewards or points-based programmes and cash back offers.
It can thus be seen that while credit card companies do levy hefty charges on their customers, their profitability will have to be monitored closely due to the possibility of expenses shooting up due to competition and other factors. As discussed in our earlier chapter on ‘Loan pricing,’ since the delinquency rates are high, they have to be compensated by higher risk premiums, translating into higher interest rates.
Credit Cards—Benefits
To summarize, the following benefits accrue to customers from the usage of credit cards:
- Deferred payment of bills
- Revolving credit
- Rewards from card issuers
The benefits to merchants are as follows:
- Immediate payment
- Assured payment
- Increased consumer spending
Debit Cards
To a customer, credit and debit cards may be look-alikes. Both are almost the same size, provide the same payment function and may also carry the Master/Visa card logo that makes them acceptable at merchant establishments where credit cards are accepted. But debit cards are quite different from credit cards.
If credit cards advocate ‘pay later’, debit cards signify ‘pay now’. The debit card is a product through which the customer’s own account with the card issuer is debited immediately to the extent of the transaction value. Further, the debit card does not allow the customer to ‘borrow’, nor does it provide ‘revolving credit’.
Since debit cards do not provide the ‘benefits’ provided by credit cards, why would customers prefer them?
Customers who prefer debit cards do so because they do not want to go into debt for their necessary or luxury purchases. Customers cannot spend beyond what their account holds. More importantly, there is no monthly bill-ing or interest charges.
The debit card programme requires a ‘POS’ terminal at the member establishment. The debit card, behind which there is a magnetic strip, is inserted into the machine by the customer at the time of billing for purchases made. The merchant keys in the transaction amount. There are two types of debit system followed at the point of payment—one a ‘signature-based’ card, where the customer swipes the card and signs the sales receipt, and the second a ‘PIN-based’ transaction.
The PIN is known only to the cardholder and the issuing bank. Once the PIN is entered, the machine places an automatic call to the bank, checks the balance in the customer’s account, and reduces the balance to the extent of the transaction value. The merchant’s account is credited for the transaction value.
Benefits to Customers
The following are the benefits enjoyed by the customers:
- Payment convenience and safety: The customer does not have to carry a cheque-book or large sums of cash.
- Wide acceptance: Debit cards are more widely accepted than cheques. They are suited for online shopping and travel.
- Easier qualification: Since debit cards use the customer’s own money, not his credit, they are often easier to get than credit cards.
Benefits to Merchants
Benefits to the merchants are as follows:
- Fast approvals: Authorized transactions in seconds.
- Fraud prevention: Purchase amounts are 100 per cent authorized at the POS, reducing losses due to fraudulent checks
- Increased sales: Statistics show the average ticket sale is increased with debit acceptance.
- Minimum investment and charges: Involves adding a low-cost PIN pad that works with existing equipment. Merchants prefer PIN-based debit cards since the charges are lower.
- Security: Online debit transactions are encrypted to protect the integrity of the cardholder’s personal banking information.
- Cash management: Funds are available sooner than with personal cheques. Debit transactions are funded within 2–3 days of batch settlement
The key differences between debit and credit cards are summarized in TABLE 16.2.
TABLE 16.2 KEY POINTS OF DIFFERENCE BETWEEN CREDIT AND DEBIT CARDS

Credit and Debit Cards in India
The data shows a deceleration in growth rates of both credit and debit cards (volume and value) in 2008–09, presumably a reflection of the global credit crisis and the consequent economic slowdown. More remarkable is the fact that the decline is more marked in the case of credit cards than in debit cards, evidencing the reluctance of the Indian consumer to spend on consumer goods on credit. Another noteworthy feature is that debit cards are primarily value-added ATM (ATM, defined later in the chapter) cards. As a result, while the number of debit cards in circulation are substantially higher than the number of credit cards, the number of transactions recorded using debit cards at POS terminals (used for purchases) are very low. The debit cards are mainly used as ATM cards. This is reflected in the fact that the monthly usage of debit cards at ATM machines is around 179 million and the number of transaction at POS terminals is 8.7 million in March 2008.
Other Payment Channels/Products
Automated Teller Machines (ATM)
Despite the development of electronic payment systems, customers still prefer cash for various transactions. Cash delivery is increasingly being done on the huge base of Automated Teller Machines (ATMs), which are being increasingly networked together to permit customers to collect cash from different banks as well as in other countries. ATM and credit card networks are linked in, and VISA and MasterCard holders have long enjoyed the facility to draw cash from ATMs. ATM networks are increasingly being developed by non-banking organizations as well.
As ATMs gain popularity, banks in India have started looking at alternative uses for the investment made. Some banks have tapped the vast potential of ATM structures to provide innovative and value-added services to customers, such as funds transfers, bill payment services, mobile phone recharge and so on.
Mobile Banking
The rapid spread of the ‘mobile phone’ era has helped banks use this mode for transactions. Mobile banking can be used for small-value payments at relatively lower costs, and, therefore is being used in many developing countries as a delivery channel to facilitate financial inclusion.8 In countries where mobile banking has been introduced, there are two distinct models that can be operated—the bank-led and telecom company-led models. India has adopted the bank-led model, while the telecom company led-model may be preferred in countries with relatively lower coverage of formal banking facilities (an example of this being Kenya).
RBI provided guidelines for mobile banking transactions in India in October 2008. The salient features of these guidelines are (a) banks have to obtain RBI approval for providing mobile banking facility to customers, (b) the facility can be provided only in Indian rupees to the banks’ own customers, or holders of debit/credit cards, and (c) banks should adhere to prescribed technology and security standards and limits set. The guidelines also mandate inter-operability among service providers, so that monopolistic practices by a few operators are avoided.
Prepaid Payment Instruments
These are payment instruments, such as smart cards, magnetic strip cards, Internet accounts, Internet wallets, mobile accounts, mobile wallets and so on, where value is stored in advance to be used when required. The ‘value stored’ is the value paid by cash, debit or credit card by the instrument holder. Purchase of goods and services is made against the stored value in the prepaid instruments. Hence, these instruments serve as a convenient and relatively risk-free mode of payment in lieu of cash, and for e-payments through Internet/mobile. More than convenience or efficiency, the safety and security of these payment instruments and the underlying technology have to be ensured.
The flow of information and funds for a generic stored value card is provided in Box 16.5.
BOX 16.5 FLOW OF INFORMATION AND FUNDS IN A GENERIC ‘STORED-VALUE’ CARD (SMART CARDS)
Assume the customer buys a stored-value card, say a Petro card, with cash or with a debit or credit card. The purchase of the card sets off a chain of settlement transactions. When the customer pays with a stored-value card, the system transfers electronic notations, or tokens, from the card to the merchant’s electronic cash register. The merchant periodically contacts the computer network connected to the bank issuing the stored-value cards and presents the tokens for payment. The network then informs the customer’s bank to pay the amount of purchase to the merchant’s bank, and the two banks make a net settlement. The banks keep a percentage of the payment (the discount) as compensation for the services they and the networks have provided.
These and other issues have been addressed in the RBI guidelines for ‘Issuance and operation of prepaid instruments in India’ dated 27 April 2009 that can be accessed at the RBI Web site.
The salient features of these guidelines are summarized as follows:
- The prepaid instruments are categorized as: (a) closed payment instruments; (b) semi-closed instruments (c) semi-open; and (d) open payment instruments.
- Closed system payment instruments, for which examples are gift vouchers issued by certain merchants, or prepaid mobile services or telephone-calling cards. It is evident that these instruments are intended for exclusive use at the specified establishment or for availing services from a service provider. These instruments typically cannot be reloaded (except mobile services) or redeemed, nor do they permit cash withdrawals. As these instruments do not facilitate payments and settlement for third party services, issue and operation of such instruments are not classified as payment systems.
- Semi-closed system payment instruments are similar to closed instruments, except that they have wider scope of operation. Examples are instruments generally issued by third party service providers, such as those redeemable at a group of establishments (associated say with a particular shopping mall, or tourist resorts or other establishments) specified by the issuer. The establishments have entered into specific contracts with the issuer to accept the payment instruments. These instruments can be issued in reloadable or non-reloadable formats but do not permit cash withdrawals.
- Semi-open and open system payment instruments are basically in the nature of credit/debit cards that can be used for purchase of goods and services at any card-accepting merchant locations/POS terminals. They can be issued in reloadable and non-reloadable formats. The essential difference is that semi open instruments do not provide the option of cash withdrawal, while open payment systems do.
- Banks can issue all categories of prepaid cards, and non-banks/NBFCs can issue semi closed system prepaid instruments, provided the preconditions stipulated by RBI are fulfilled. Other eligible issuers can issue only closed system instruments.
- Semi-open and open instruments are vulnerable to frauds and misuse. Hence, safeguards should be in place to prevent money laundering and other types of misuse.
- The prepaid card should have minimum validity of 6 months from date of issue/activation.
- The maximum value for which a prepaid card can be issued is ₹50,000.
- The money collected against issue of such instruments would be substantial. But, since it is payable to merchants and others with whom the instrument holders transact, the money received by the issuer should be treated as ‘float’ money and invested in liquid, near cash and safe investments. Where banks are the issuers, the money collected is treated as part of NDTL for the purpose of reserve maintenance.9 If the issuers are non-banks, they will have to maintain the outstanding balance in an ‘escrow account’10 with a commercial bank. The escrow account is intended only for making payments to participating merchant establishments—hence, banks do not pay interest on these balances, and cannot grant loans against these funds.
SECTION V
SECURITy ISSUES IN E-BANKING
It is evident that e-banking is here to stay. However, the advent of high technology has also brought with it new operational risks in the form of security risks. The safety of banks, the integrity of the country’s payment and settlement systems, and the trust that customers impose in the safety of the system are all intertwined to ultimately contribute to financial stability. The challenge for the future will be to identify and address risks to banking safety and security without hampering technological innovations in banking.
Internet-banking has evolved into a mass market product—an essential service whose quality can affect the customers’ loyalty to and satisfaction with their bank. And, not surprisingly, it is Internet-banking that is posing the gravest risk to banks’ viability and sustenance. Hackers and fraudsters have realized the immense potential of Internet-banking to give them ill-gotten monetary gains.
Therefore, as new technologies evolve to make banking faster and more convenient for customers, the concerns about e-payment security have increased. The ‘conventional’ risks of unauthorized access, identity theft or network attacks have been exacerbated by ‘contemporary’ threats—phishing and pharming, spear phishing, carding and skimming, crimeware and spyware, money laundering, mules, scams, spams, Nigerian advance fee fraud—and still counting.
Real Life Example 1
Nordea lost more than $1,000,000 in aggregate due to a sophisticated malware attack, which recorded user’s account details and sent them to fraudsters. These transfers were made in several small amounts between 2005 and 2007, in order to circumvent the bank’s fraud detection mechanisms
Often inadequately protected, personal computers are the first point of attack for cyber criminals. Users are attracted to various offers that seem to be coming in from their banks and fall prey to Internet fraud.
The most prevalent types of Internet frauds are discussed as follows:
- Identity Thefts In the virtual world, a person’s identity is defined by the user name, passwords or account names. Identity theft is the misuse of personal data or documents in order to impersonate another individual to carry out illegal or fraudulent activities, e.g., to abuse the victim’s banking facilities or other assets. Especially affected are popular transaction types, such as card transactions at ATMs, online banking transactions or the use of credit card numbers for Internet payments.
Some of the largest identity thefts have happened in the US (Table 16.3), as reported by McAfee.
Real Life Example 2
Stephen Watt was a member of a conspiracy which, between 2003 and 2008, unlawfully gained electronic access to corporate computer networks using various techniques, downloaded customers’ credit and debit card information, and fraudulently used that information and sold the information to others for fraudulent use. Watt modified and provided a ‘sniffer’ program used by the conspirators to monitor and capture the data crossing TJX’s computer network.
Watt pleaded guilty to conspiracy charges on 28 October 2008. He was sentenced to 2 years’ imprisonment, to be followed by 3 years of supervised release, a condition of which was electronic monitoring of any computer use. He was ordered to pay restitution in the amount of $171.5 million dollars.
- 2. Carding/Skimming ‘Carding’ sites can be found on the Internet, where fraudsters buy and sell access to bank accounts, stolen card numbers, dumps from magnetic strips and even personal profiles.
‘Skimming’ constitutes the unnoticed duplication of electronic data from a payment card. A copying device is installed in front of the original card slot of an ATM, which transcribes the information from the magnetic stripe on a card inserted by a customer. Sometimes these devices could be a camera or a fake touch pad to duplicate the keystrokes used for password entry.
The vital information obtained by these methods enables fraudsters to easily create duplicate cards and withdraw money from the accounts in question. Instances of skimming can also occur at cash registers.
Real Life Example 3
In May 2008, McAfee12 found a set of bank accounts for sale. The most expensive was also the most highly funded: an account at European bank BNP Paribas with a balance of €30,792, selling online for just €2,200. In addition to the discounted rate, the seller offered a 24-hour guarantee: if the buyer could not log in within that period or if the account no longer contained the money, a replacement account would be provided!
- 3. Phishing ‘Phishing’ is a famous word these days—signifying fraudulent capture and recording of customers’ security details, to be used later for committing fraud. It originates from the analogy that Internet fraudsters are using email lures to ‘fish’ for passwords and financial data from myriads of Internet users.
Phishing can take on several forms such as the following:
- Email phishing signifies creation of email messages and web pages that exactly resemble existing sites in order to deceive users to part with financial, personal or password data to fraudsters.
- Pharming is the use of malware/ spyware to redirect Internet users from genuine Web sites to fraudulent ones. It carries out modifications in the name resolution system, such that when a user opens the Web site of his bank, it actually takes the user to the fraudulent Web site.
- Spear phishing is a highly targeted phishing attack that focuses on a whole group—such as employees of a certain firm, government agency or organization. The message would appear as though it is generated by the employer, asking for updating of passwords or any other personal information. Spear phishing could, therefore, gain access and wreak havoc on an entire company’s computer system.
- Phlash phishing uses Macromedia Flash to build an entire Web site. The use of Flash is intended to make it more difficult to determine whether or not the page is malicious, and could also bypass antiphishing toolbars.
- Vishing (voice phishing) may begin with an email or telephone call. The email warns that the user’s bank account has been cyber attacked and, therefore the user has to call a certain telephone number, which will ask for the account number and other details. The phone call version purports to be even more authentic. The caller already knows the user’s credit card number and asks for the valuable 3-digit code at the back of the card. Such calls can be set up quickly and automatically by voice over Internet protocols (VoIP).
- Man in middle attacks (phishing in sessions) is a rapidly growing threat to online banking security. Fake Web sites are set up to closely replicate the bank’s authentic Web sites. The bank customer receives an email purportedly from the bank, asking the customer to click on a link provided on the bank ‘Web site’. Once this is done, the customer is automatically taken to the fake bank Web site. In another approach, the customer’s Internet connection is already tampered with; hence, when the customer tries to visit the genuine bank Web site, he invariably gets connected to the fake Web site. The noteworthy feature is that, to the customer, the fake Web site will appear identical to the genuine Web site, including encryption symbols. However, details entered by the customer will reach the fake Web site and not the real one. Once the details are received, special software connects to the real bank Web site, impersonates the customer, and carries through financial transactions. Even the bank cannot discern the difference since all details are in place. While both the bank and the customer believe that they are communicating directly with each other, the fraudster can easily put through and modify any information that is transmitted.
- Man in the browser attacks have reached an even higher level of sophistication. In these cases, rather than intercepting communication between the customer’s computer and the bank Web site, the malicious software (malware) installed on the customer’s computer intercepts communication between the customer and his web browser.
The malware (such as ‘trojans’) gets installed when a customer opens an email attachment or downloads a file from a Web site. Just visiting a web site, or viewing an email, may be sufficient for a fraudster to install malware without the customer’s permission or knowledge. In some cases, criminals tamper with existing genuine Web sites, so that they will infect their visitors. The customer is unlikely to notice the difference, as it is believed that as much as 80 per cent of new malware is undetected by anti-virus software. Normal web browsing will be unaffected, but the malware will recognize when the customer visits their online bank Web site. Then, the malware can freely alter the web page as it is displayed to the customer, and modify the requests sent back to the bank. For example, in case of funds transfer made by the customer, the malware could change the amount transferred and the destination account number to that of the fraudster. Similarly, once the bank confirms that the transfer has occurred, the malware will change what is displayed to the customer, making the customer believe that the intended original transaction has been executed.
In 2006, Citibank customers were targeted by a Man in the Middle attack. An email asked customers to confirm their address, stating that suspicious activity was detected. The site asked for account details, including the one-time password from the tokens issued to customers. If they were incorrect, the customers were asked to re-enter them.
Real Life Example 5
AT&T’s back-end systems were broken into by attackers. This system stored data on customers who had ordered certain equipment. The attackers sent emails to many of these customers, quoting authentic information already provided by them to create confidence, and then asking them to provide further personal information.
Real Life Example 6
In 2007, ABN AMRO’s online banking service suffered a malware-based attack. Customers were sent emails with attachment, claiming to be from the bank itself. The customers responding to the email would visit the bank site that would redirect them to a fake site that asked for account details. Even though ABN AMRO deployed two-factor card reader-based authentication, the fraudsters were able to get away with transactions while the one-time password was still valid.
It can be seen that this fraud technique can circumvent security measures since it is more sophisticated than simply gathering details from the customer. This technique has already been instrumental for large amounts of losses, and has gone to such levels of sophistication that ‘kits’ are available from the Internet, enabling even relatively unskilled fraudsters to launch advanced attacks.
Phishing activities as well as anti phishing measures have reached such levels of frenzied activity, that an Anti Phishing Working group (APWG) has been formed as a ‘global pan industrial and law enforcement association, focussed on eliminating the fraud and identity theft that result from phishing, pharming and email spoofing of all types’. The APWG publishes periodical research reports on phishing activity, as well as customer guidance and other helplines that can be accessed at www.antiphishing.org.
- 4. Mules ‘Mules’ are individuals ‘recruited’ over the Internet with the sole purpose of being intermediaries for illegally acquired funds. These funds could have been acquired through methods such as phishing and other types of scams. The name ‘mule’ is suggestive of the transport method that smugglers are believed to have adopted for moving their illegally acquired goods.
Mules earn sizeable sums of money—deducting 5 per cent to 10 per cent of the transferred amount as fee for their ‘services’. The money is transferred through anonymous transfer services, such as Western Union or e-gold.13
Contrary to popular belief, mules are not innocent people tricked into illegal business. They are typically mercenary volunteers with scant respect for the law—and for this very reason, they are turning ‘professionals.’
Real Life Example 7—Money Mules in India
As the number of online job seekers increase exponentially in India, so do online frauds. Many ‘money mules’ are individuals desperately seeking jobs online, and are lured into the ‘profession’ due to their greed to make quick money. They are ‘recruited’ as money mules, and follow ‘instructions’ without being aware of their implications, and ultimately end up in prison.
The recruitment operation takes place as follows. A foreign company, pretending to have clients in India, calls for application for an India branch manager responsible for ‘collections’. When an online job seeker expresses interest, an online interview is conducted and the job seeker is appointed with the responsibility of transferring money deposited into his personal account by the foreign company’s clients. In the bargain, the ‘recruit’ earns around 10 per cent commission apart from the monthly ‘salary’ promised to him. The ‘recruit’ is the ‘money mule’.
The action then moves to other gullible people lured either by promises of lottery wins or job offers abroad. They are instructed to contact the money mule and deposit a specified amount in the mule’s bank account. The mule then transfers say 90 per cent to the fraudster abroad. Both the mule and the deceived persons may land in trouble later with the Indian authorities for illegal acts.
The police confirm that online frauds are increasing, and many of them originate in Nigeria (see ‘Nigerian advance fee fraud’ in Real life example 9).
Real Life Example 8—Nigerian Advance Fee Fraud (419 fraud)
The fraud is named after the Nigerian law that covers it. The fraud begins with the arrival of an email from a family member of an (usually) African dignitary, who claims that following the death of an influential family member, a huge sum of money is locked up in a bank account at some location. The sender of the email solicits the recipient’s help to release the money, and lures the recipient with hefty compensation for the help. Once the unwitting recipient is tempted, the fraudsters demand an ‘advance’—either in the form of a bank account opened for this purpose or a fee. Once this is accomplished, there may be a series of expenses the victim has to contend with, sometimes leading to physical threats. The victim realizes after some time that the blocked money does not exist, and that he has been hoodwinked.
McAfee and other e-security experts predict heightened security threats in 2010 and thereafter. An illustrative description is given as follows:
- Banking Trojans14 are predicted to become even more sophisticated—for example, they could interrupt legitimate transactions and make unauthorized withdrawals, even where security systems are tight.
- Malware via email attachments are expected to increase, targeting all types of banking customers—corporate houses, individuals and other entities.
- Botnets, the infrastructure that launches nearly every type of cyber attack, are predicted to grow in ‘stature’ to operate a peer-to-peer architecture, i.e., connecting computer to computer without a centralized control point. Hence, detection becomes very difficult.
- HTML 5 and the evolution of new programming languages are expected to provide new avenues for cyber criminals to write malware targeting specific users.
The examples and discussion so far show that security issues pose grave threats to users and stiff challenges to those responsible for tackling and controlling them. Cyber crime also poses systemic risk. A single user’s loss may be limited but the consequences of such attacks would entail indirect costs—identification and legal proof of fraudulent transactions, cleaning of records, issuing/devising new instruments/payment systems, the threat of contagion to other payment systems—all of which would involve system-wide responses.
CHAPTER SUMMARY
- Over the last couple of decades, technology has assumed the vital role of not only a facilitator, but also a source of competitive advantage for banks. The business of banking—especially financial services / retail banking—is undergoing a sea change, as business shifts increasingly to the online environment. The increasing number of customers transacting online would move the ‘market place’ to ‘market space’, where banks would be forced to expand their product range to competitors’ products, while rapidly innovating their own value-added products.
- The Internet has evolved into an essential access channel. For banks, the Internet offers a cost effective means of innovating, publicizing and delivering services to the customer, as well as maintaining customer relationships. For the customer, the Internet has opened up enormous possibilities of convenience and choice.
- The security of payment and settlement systems is critical for sustaining public trust in banks and other parts of the financial system. Hence, central banks, as supervisors and regulators of payments and settlement systems through financial intermediaries, have to ensure development of efficient and secure systems to match the explosion in needs and sophistication of the financial sector.
- The Committee on Payment and Settlement Systems (CPSS) was set up by the Bank for International Settlements with the objective of strengthening financial market infrastructure through promoting sound and efficient payment and settlement systems. The membership of CPSS has widened to include about 25 central banks in 2009. The RBI is a member of CPSS.
- RBI was empowered in 2007 through the enactment of the Payment and Settlement Act, 2007, to regulate and supervise payment and settlement systems in India. To operationalize the Act, RBI framed the ‘Board for Regulation and Supervision of Payment and Settlement Systems Regulations, 2008’ and ‘Payment and Settlement Systems Regulations, 2008’.
- Payment systems in India can be bifurcated into ‘paper-based’ and ‘electronic’ payment systems. Another classification, based on users, can be into ‘large-value payment systems’ and ‘retail payment systems’.
- The paper-based payment and settlement mechanisms in vogue in India are MICR and non-MICR cheques, highvalue clearing, speed clearing, cheque truncation, etc.
- The electronic clearing and settlement systems being operated are ECS/NECS, EFT/NEFT.
- Though retail payments are not termed Systematically Important Payment Systems (SIPS), their relative importance to the economy cannot be undermined due to the sheer volume and geographical coverage that these systems demand.
- Retail payment systems are required primarily for purposes, such as payments for goods and services, bill payments, cash payments and so on.
- Plastic money refers to substitution of currency at the time when a payment is taking place, by using a card normally made of plastic representing such substitution. There can be several objectives for such substitution. Most important among these would be the need to postpone actual payment, or pre-purchase payment on the card that is issued. Whatever be the objective, the most important advantage of plastic money is protection to the user from the risks of carrying cash. Since it is the exclusive property of the cardholder it means that it can be used only by him. The categories are (a) credit cards, (b) debit cards and (c) other payment channels and products. Some of the popular channels under (c) are ATMs, Mobile banking services and prepaid instruments.
- However, the advent of high technology has also brought with it new operational risks in the form of security risks. The safety of banks, the integrity of the country’s payment and settlement systems, and the trust that customers impose in the safety of the system are all intertwined to ultimately contribute to financial stability. The challenge for the future will be to identify and address risks to banking safety and security without hampering technological innovations in banking.
- The ‘conventional’ risks of unauthorized access, identity theft or network attacks have been exacerbated by ‘contemporary’ threats—phishing and pharming, spear phishing, carding and skimming, crimeware and spyware, money laundering, mules, scams, spams, Nigerian advance fee fraud—and still counting.
TEST YOUR UNDER STANDING
- Why do countries require technology in banking?
- Are e-payments a necessity? Whom do they benefit? What are the risks?
- What are the essential differences between credit cards, debit cards and other prepaid cards? Rank the three types of cards on the following parameters:
Feature Credit Cards-rank Debit Cards-rank Prepaid Cards-rank Which card is the safest for the user? Which card is the safest for the banker/ issuer? Which card is the safest for the merchant? Which card is the most convenient for the user? Which card is the most convenient to the merchant? Which card is the most convenient to the issuer? - What is ‘systemic risk’ and why are SIPS important in this context?
- Which of the variants of ‘phishing’ could you be faced with if you encounter the following while banking online?
- A voice says ‘Welcome to account verification. Please enter your account number’.
- A flash player pops up urging you to install the update.
- Your mail id is used as the salutation on your bank site, urging you to update confidential information.
- You receive an email with a link to your bank Web site asking you to open the link and update personal information.
- A seemingly genuine bank site opens with the security ‘lock’ icon in the login space, but no lock sign in the status bar.
- In an attempt to make the e-payment system more secure, Bank A makes a basic assumption that all customer computers are not safe. It, therefore asks customers to use virtual keyboards and additional transaction security systems. Would the bank succeed in fending off e-attacks?
- What will be your course of action if you suspect phishing? Whom will you report the incident to?
- Can a ‘payment risk’ due to security lapses translate into ‘reputation risk’ for a bank? What are the consequences of reputation risk?
- You are on a foreign posting and are looking for a house on rent. You find a prospective house online. The landlord asks for your details but refuses to give you his address, and does not permit you to see the house unless you transfer some funds in foreign currency to his Western Union account. What will be your reaction and subsequent action?
TOPICS FOR FURTHER DISCUSSION
- What is the status of the RTGS system in other countries? How can a system like RTGS be successful in preventing systemic risk?
- Access the site www.antiphishing.org. What are the kinds of action being taken by the international community to fend off cyber attacks?
- Make a country study of anonymous payment methods and related laws. What conclusions can you draw?
ENDNOTES
- INFINET stands for Indian Financial Network—the communication backbone for the Indian banking and financial sector. All banks and financial institutions are members of the INFINET, which functions as a closed user group.
- Most money exists not as cash but as notations in the ledgers of depository institutions (banks and other financial institutions). Debiting one party’s account and crediting another party’s account execute notational money transactions. Banks must be prepared to convert notational demand deposits into cash on demand by the customer.
- Please refer to chapter ‘Monetary Policy Implications for Bank Management’ for a discussion on ‘reserve requirements’.
- Core banking applications help provide complete frontand backend automation of banks. These applications also help banks achieve centralized processing and provide anywhere, anytime 24 × 7 non-stop services, not possible with traditional localized branch automation systems that are available only during their working hours. Core banking applications help integrate the enterprise to existing in-house applications to offer a single customer view. These applications provide automation across multiple delivery channels.
- RBI, (2009) Committe for financial sector assessment, Vol. V Chapter V, Table 1, page 265.
- Public Key Infrastructure (PKI) offers authentication of online transactions, by providing each user with an electronic identity in the form of a digital certificate and a private cryptographic key. It is usually stored in a secure media, such as a smart card or an i-key. The person could make use of the identity to digitally sign documents or transactions.
- RBI, (2009), Committee for financial sector assessment, Vol. V, Chapter V, Box 2, page 276
- Studies indicate that formal banking reaches 37 per cent of the population, while mobile phones are owned by more than 50 per cent of the population. For every 10,000 people, these countries on an average have one bank branch and one ATM, but 5,100 mobile phones.
- NDTL and reserve requirements are dealt within the chapter ‘Monetary Policy Implications for Bank Management’
- Escrow is a legal agreement created for a specific purpose and period, and deposited with a third party. It is valid until the performance of an act or the happening of an event specified in the agreement. Before making the deposit of the money paid by holders of prepaid instruments with the bank, the agreement between non-banks and the cardholders should specify the terms of the agreement, and more specifically, when the agreement is to be released. The bank holding the escrow account will not be a party to the agreement, but will function as a ‘custodian’ who has no right to alter the terms of the agreement. The custodian bank is also bound by duty to act according to the trust placed in it and therefore would be liable for wrong payments.
- McAfee Report titled ‘Financial Frauds and Internet Banking: Threats and Countermeasures’, (2009), page 6, by Francois Paget, McAfee Avert Labs, US, accessed at www.mcafee.com, can also be accessed at www.avertlabs.com
- Ibid, page 8.
- Cyber criminals prefer anonymous (and convenient) services, such as these to carry out their activities. There are currently about 20 such known services in operation. Many countries are now cracking down on such services through appropriate legislation. For example, e-gold’s founders are currently under investigation. Web money is a Russian entity with 4 million customers, whose customers’ integrity is under question. Western Union, the American money transfer agent with presence in more than 200 countries, set up to facilitate fund transfers to family members, is also allegedly being misused. (source: www.mcafee.com)
- The Trojan.Satiloler family monitors traffic sent and received by web browsers. It can inject malicious code into web pages received even before the user can read them. For example, in an online banking Web site, the Trojan can replace all the functions with its own functions. This enables the Trojan to control information flow on the site without the user’s knowledge, sometimes irrespective of the authentication mode used. Hence, a clean and trusted system is the first prerequisite to avoid this malware attack. A variation, called the Banbra Trojan, targets those using virtual keyboards provided on banking Web sites to enter passwords and confidential information. It captures the movement of the mouse as the user types in the password and sends a video file to the cyber criminal, thus enabling online frauds. (source: www.cert-in.org.in)