On a large network, virtually all administrative chores are centralized; you probably have little or no control over the configuration of Windows 2000. Truth be told, most people who aren't professional computer nerds don't want to have to deal with technical matters. However, if you're using Windows 2000 Pro as a stand-alone machine (or on a peer-to-peer network), you can't call the administrator when something goes wrong—you are the administrator.
This chapter describes the Windows 2000 tools that fall under the category of "administration."
If there's one thing Windows 2000 is good at, it's security. In fact, there are so many ways to make your computer and data secure, you can easily tie yourself into knots.
How much security is enough? The decisions are much like the ones you have to make about your home. Yes, you can install a burglar alarm, locks, bars on windows, and a guard dog. You'll increase security, but also increase the chances of setting off false alarms, losing keys, getting trapped in a fire, and getting bitten. Computer security offers the same tradeoffs: You want enough security to discourage invaders, but not so much that you're constantly running into roadblocks of your own making.
Here are a few of the steps you can take to keep your data private:
Keep your computer and data physically secure. If people wander into your workspace all the time, always log off before leaving your computer, or use a password-protected screen saver. Save your data to a secure server (if there is one) on the network.
Install antivirus software. Install an antivirus program designed for Windows 2000. Make sure it's set to scan every floppy disk and downloaded file. Check the software company's Web site for downloadable updates to the antivirus software at least once every two weeks.
Use a firewall if you have a persistent Internet connection. For a dial-up connection, the security settings of Internet Explorer offer adequate protection; you can set them to be quite strict.
However, if your connection to the Internet is "up" all the time—that is, if you have a DSL or cable connection—you need something more. Consider buying firewall or proxy server software to rule out the possibility of Internet hackers.
If your data needs protection, consider encryption. The Encrypting File System (EFS) in Windows 2000 can encrypt files or folders (on NTFS partitions; see Section A.2.3). Once you've protected a file in this way, you can use it normally. But if someone with another user account tries to open the file, he'll see only an Access Denied message.
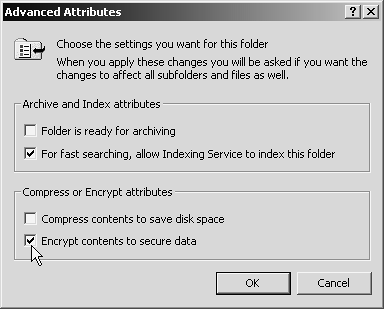
To encrypt a file or folder, right-click its icon; choose Properties from the shortcut menu. Click the Advanced button to bring up the Advanced Attributes dialog box (Figure 17-1), and turn on "Encrypt contents to secure data." (Turning off this same checkbox decrypts the file.)
Figure 17-1. If you encrypt an individual file, your word processor (and other programs) may save a new copy of the file when you edit it, deleting the encrypted copy in the process. Unless you remember to encrypt the new version every time, you could end up saving an unencrypted version. That's why it's a good idea to encrypt folders, not individual files, so that new files added to the folder will also be encrypted.
If your email is sensitive, consider encryption and digital identification. The usual advice is to put nothing in your email that you wouldn't want posted on the bulletin board of your local supermarket. If your company owns the computer and network that you're using for the email, that's very good advice.
Outside of work, think of your email like regular postal mail: Your letters pass through many hands, and yet you entrust your mortgage payment, tax returns, and valentines to snail mail with every expectation that they'll arrive unopened. Nevertheless, it would be foolish to put your plans to commit tax fraud, embezzlement, or adultery in any kind of mail.
If your mail and data are of a kind that a business rival, disgruntled hacker, or divorce lawyer would love to get their hands on, get the Microsoft Windows 2000 High Encryption Pack—but not before reading http://www.microsoft.com/security/new.asp and getting up to speed.
If email security is important to you, consider getting a digital ID—a software certificate that verifies that you are who you say you are and lets you encrypt your outgoing email. To get a digital ID, open Outlook or Outlook Express, choose Tools→Options, and then click the Security tab. If you click the Get a Digital ID button, Windows connects you to information about digital IDs, how they work, and how to get one.