Chapter 2: Becoming a Trusted Sender
In This Chapter
![]() Understanding spam laws
Understanding spam laws
![]() Getting permission
Getting permission
![]() Familiarizing yourself with e-mail laws
Familiarizing yourself with e-mail laws
![]() Minimizing spam complaints
Minimizing spam complaints
Spam-blocking and -filtering technology has improved, but everyone who uses e-mail still deals with spam on one level or another. The main difference between the spam of today and the spam of the past is the fact that consumers increasingly apply the word to unwanted e-mails, whether or not those e-mails are technically spam.
Consumers are always skeptical of e-mails unless they know and trust the sender, and they’re more than willing to report your e-mails as spam to their Internet service provider (ISP) if your e-mail is unwanted or doesn’t appear trustworthy.
Every e-mail marketing strategy is subject to numerous legal and professional standards that apply to commercial e-mail. Consumers also expect marketing e-mails to come from a trusted source with just the right frequency and amount of relevant content. Here are the three authoritative benchmarks for determining whether your commercial e-mails are regarded as spam:
• Legal standards, as outlined in the CAN-SPAM Act of 2003 and the 2008 revisions to the Act
• Professional standards, as outlined by consumer advocates and the e-mail marketing industry
• Consumer preferences, as dictated by consumers themselves
Adhering to e-mail professionalism keeps your e-mails legally compliant and improves your relationships with the people who receive and open your e-mails. This chapter discusses how to become a trusted e-mail sender, minimizing consumer spam complaints while maximizing the trust between your business and your existing and future e-mail list subscribers.
Complying with Spam Laws
Spam is bothersome enough that lawmakers enacted the CAN-SPAM (Controlling the Assault of Non-Solicited Pornography and Marketing) Act of 2003 to help prosecute spammers. Names aside, the law makes certain e-mail marketing practices illegal and gives legal definitions to many best practices.
The following sections summarize the basic tenets of the CAN-SPAM Act of 2003 and the revisions made in 2008. You can read the CAN-SPAM Act at
http://business.ftc.gov/documents/bus61-can-spam-act-compliance-guide-business
and you can access the 2008 revisions at
www.ftc.gov/os/2008/05/R411008frn.pdf
to make sure that your own e-mails comply.
Determining which e-mails have to comply
The CAN-SPAM Act of 2003 applies to commercial e-mail messages, which the law distinguishes from transactional or relationship messages. In general, the CAN-SPAM Act defines the two separate kinds of e-mail messages as follows:
• A commercial e-mail is basically an e-mail containing an advertisement, promotion, or content from a business’s website.
• A transactional or relationship e-mail is basically anything other than a commercial e-mail.
Collecting e-mail addresses legally
The CAN-SPAM Act makes certain types of e-mail address collection illegal and requires permission from your e-mail list subscribers before you send certain types of content. (The CAN-SPAM Act uses the term affirmative consent instead of permission.)
• Never purchase an e-mail list from a company that allows you to keep the e-mail addresses as a data file. E-mail addresses kept in a data file are easily bought and sold, and e-mail addresses with explicit permission are too valuable to sell.
• Never collect e-mail addresses from websites and other online directories. This isn’t a good practice because you don’t have affirmative consent (or permission) from the owner.
• Don’t use an e-mail address collection service. The exception is a service that collects confirmed permission from every subscriber that it obtains.
• Don’t borrow an e-mail list from another business and send e-mail to that business’s e-mail list. Those subscribers didn’t explicitly opt in to receive your e-mails.
• Don’t rent an e-mail list unless you’re certain that the list rental company’s practices are legally compliant. Most rental companies don’t have permission-based lists. (You can read more about list rental in Chapter 3 of this minibook.)
Including required content in your e-mails
The CAN-SPAM Act requires you to include certain content in your e-mails. Include the following in your e-mails to stay CAN-SPAM–compliant:
• Provide a way for your subscribers to opt out of receiving future e-mails. You’re required to remove anyone who unsubscribes from your e-mail list permanently within ten days of the unsubscribe request, and you can’t add that person back without his explicit permission. When providing an opt-out mechanism, remember that it’s illegal to charge someone to opt out or to ask for any information other than an e-mail address and opt-out preferences. Your opt-out process also has to be accomplishable by replying to a single e-mail or by visiting a single web page. Your EMP can provide you with an opt-out link that automatically unsubscribes in one click.
• Make sure that your e-mail includes your physical address. If your business has multiple locations, include your main address or the physical address associated with each e-mail you send, as shown in Figure 2-1.
Figure 2-1: Adding a physical address to your e-mail is required under the CAN-SPAM Act.
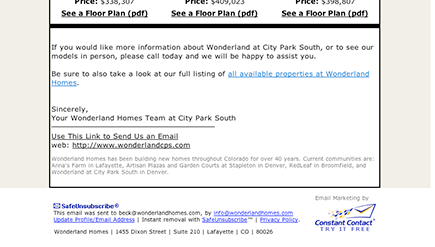
Courtesy of Wonderland Homes and Constant Contact
 If you work from home and don’t want your home address in every e-mail, the CAN-SPAM 2008 revisions confirm that you’re allowed to include your post office box address as long as the post office or box rental company associates the box to your legitimate business address.
If you work from home and don’t want your home address in every e-mail, the CAN-SPAM 2008 revisions confirm that you’re allowed to include your post office box address as long as the post office or box rental company associates the box to your legitimate business address.
• Make sure that your e-mail header information clearly identifies your business and doesn’t mislead your audience in any way. Your e-mail header includes your From line, Subject line, and e-mail address. Make sure that your e-mail’s From line information clearly and honestly represents your business. The term misleading is open to legal interpretation. Speak to your attorney if you have questions.
• Make sure that your e-mail’s Subject line isn’t misleading. Don’t use the Subject line to trick your audience into opening your e-mail or to misrepresent the offer contained in your e-mail.
• Make sure that your e-mail clearly states that the e-mail is a solicitation. The exception is when you have permission or affirmative consent from every individual on your list to send the solicitation. (Read more about permission later in this chapter.)
• Make sure that your e-mail complies with any applicable guidelines for sexually oriented material. If your e-mail contains such material, make sure that your e-mail’s Subject line complies with the CAN-SPAM Act supplementary guidelines and also clearly states that the content of the e-mail is adult in nature without being explicit in the way you describe the content. You can access the supplementary guidelines on the Federal Trade Commission (FTC) website at http://business.ftc.gov/documents/bus61-can-spam-act-compliance-guide- business.
Asking for Permission
According to a recent study conducted by the Messaging Anti-Abuse Working Group (www.maawg.org), the majority of consumers consider unrequested e-mails to be spam. Collecting information without asking for permission can cause prospective subscribers to hesitate — or worse, they could perceive you as a spammer who abuses their privacy. Obtaining permission also ensures that your list starts out in compliance with the current CAN-SPAM laws.
Taking some time to formulate a professional permission strategy before embarking on e-mail collection tactics can reward your overall e-mail strategy with loyal subscribers who love to open, read, and take action on the e-mails you send.
Deciding on a permission level
When formulating your permission strategy, put yourself in the prospective subscriber’s shoes so that you can assess the level of permission necessary to meet individual expectations.
Each type of permission is a two-way notion. You should be able to attest to each subscriber’s level of consent, and your subscriber should feel that he did indeed authorize you to send him e-mail. This type of two-way permission comes in three basic levels, each with a higher level of demonstrated consensus: implied, explicit, and confirmed.
Level 1: Implied permission
Implied permission happens when someone shares her e-mail address with you in the course of normal business communications. The transaction implies that the purpose of giving you the e-mail address is to receive e-mails from you in reply. This level of permission isn’t recommended as a best practice, even though it’s sometimes suitable in the recipient’s view. (Read on to find out why this isn’t a best practice.)
An example of implied permission is a prospective customer who fills out an online form to obtain a quote for your services. The form includes an E-Mail Address field. The prospect shares her e-mail address within the form, expecting that you’ll use that e-mail address to send the quote. If you send the quote and then begin sending weekly promotions without disclosing the fact that sharing an e-mail address on the quote form results in additional e-mails, however, you run the risk that your new subscriber will feel violated.
The main reason why implied permission isn’t considered one of e-mail professionalism’s best practices is that it doesn’t take much extra effort to move from implicit permission to a higher standard. In the previous example, the business owner could easily add a link to his permission policy under the E-Mail Address field. Or, he could insert text that reads
By sharing your e-mail address, you’ll receive your quote via e-mail along with concise weekly product updates to which you can safely unsubscribe at any time.
Level 2: Explicit permission
Explicit permission happens when you include text or language disclosing how you plan to use the prospective subscriber’s e-mail address. For example, an explicit subscriber might be a website visitor who clicks a Sign Up to Receive Our Weekly E-Newsletter link and then clicks another link on the following page to submit additional information that he types into an online form. Explicit permission also happens when prospective subscribers contact you and explicitly ask to be added to your e-mail list.
Explicit permission doesn’t have to be a lengthy or complicated process, but the benefits of obtaining explicit permission are worth having a straightforward process. Here are some examples of explicit permission that you can adapt to your own subscriber situations:
• Verbal: When someone shares his e-mail address by handing you a business card or dictates an e-mail address to you during a phone conversation, you could query, Is it alright if I send you my weekly event invitation e-mail?
• Written: If a prospective subscriber sends a single e-mail to you and you want to add him to your e-mail list, you could reply to the e-mail and ask, By the way, may I add your e-mail address to my list so that you can receive my monthly e-newsletter?
• Physical: Some subscribers physically add their e-mail address to a guest book or sign up via a paper form. If you have such an arrangement, you could post a professional-looking plaque or sign next to the guest book or sign-up form that states, Thank you for giving us permission to send you our weekly e-mail coupons by signing our guest book. We promise never to share your e-mail address with anyone outside the company without your permission.
• Incidental: Sometimes, you can ask for explicit permission in the context of a transaction related to your e-mail information. For example, you might want to give online shoppers the ability to receive cross-promotions by selecting a check box during the checkout process. The text describing the check box could read, Select this check box to receive periodic promotions that enhance the value of your purchase. Just be sure that the default setting on the check box is deselected (cleared), or else it’s no longer an example of explicit permission.
Level 3: Confirmed permission
Confirmed permission happens when someone implicitly or explicitly subscribes to your e-mail list, and you respond to the subscriber with an e-mail requiring the subscriber to confirm his interest by reading your intended usage and then clicking a confirmation link. If the subscriber doesn’t confirm, his e-mail address isn’t added to your list, even if he explicitly filled out and submitted a form or physically signed your guest book. Figure 2-2 shows an example of a confirmation e-mail.
Figure 2-2: A prospective subscriber must click an additional link for confirmed permission.

Courtesy of Constant Contact
Confirmed permission is the appropriate level if
• You send sensitive information.
• Your subscribers tend to forget signing up.
• You want to have a physical record of the subscriber’s authorization to send e-mail.
Confirmation e-mails generally have low response rates, so if you’re using explicit permission to build your list, you might lose subscribers who really want to be on the list but fail to read the confirmation e-mail and click the required link. The trade-off, however, is that your confirmed subscribers are more likely to receive and open your e-mails.
Inheriting a list: Getting permission after the fact
Sometimes, you might find yourself in possession of an e-mail list with questionable — or even no — permission. This often happens when you obtained your list in one of (or more of, but not limited to) the following scenarios:
• You purchased an existing business and inherited an e-mail list without knowing the source of the e-mail addresses on the list.
• Your list contains e-mail addresses collected over a long time period, and you can’t identify each type of associated permission.
• You purchased a list or built your list with low permission standards before you read this chapter — and now you’re wondering whether your list is useless.
Follow these steps to determine the permission status of an inherited list with questionable permission:
1. Sort your list by source.
If the source doesn’t imply a two-way business relationship and the recipient likely won’t recognize your e-mail address, discard the e-mail address or set aside the contact info to ask for permission.
Sources can include order forms, business cards, e-mail correspondence, guest books, or purchased lists. Inherited lists rarely detail the source as a field in a database or a note on the back of a business card, so determine the source by matching each record to other clues.
For example, if your list is contained in a customer relationship management system database, you might be able to export all the customers who made a purchase — and assume that names were obtained as the result of a business transaction.
 Always discard purchased lists because purchased lists are almost never permission-based to begin with. (See the section on building a list with list brokers in Chapter 3 of this minibook for more information about purchased lists.)
Always discard purchased lists because purchased lists are almost never permission-based to begin with. (See the section on building a list with list brokers in Chapter 3 of this minibook for more information about purchased lists.)
2. Sort your list by date; discard any addresses belonging to customers who haven’t made a purchase in over a year.
E-mail addresses belonging to customers who made purchases in years past and haven’t returned shouldn’t be used. Older e-mail addresses should be kept only if the person who owns the e-mail address is a recognizable current customer.
3. Check your list visually; discard any addresses that begin with ambiguous names or that are part of a distribution list.
Ambiguous names include Webmaster@ or Info@. Distribution lists (single e-mail addresses that forward the e-mail to multiple addresses behind the scenes) make it impossible to tell whether the underlying e-mail addresses are permission based.
4. Sort the rest of your list by category.
At this point, consider using different messaging, depending on your relationship to the person who owns the e-mail address. If the e-mail address belongs to a prospect, you might want to proceed more cautiously than if the e-mail address belongs to a person who has purchased a product several times.
5. Confirm permission to send e-mail.
If, and only if, an e-mail list passes the preceding four steps and you’re certain that the people who own the e-mail addresses on your list will recognize your business and your relationship to them personally, contact them to confirm permission.
• If you have a small list: Confirmation can be verified with a phone call or an e-mail containing a confirmation link.
• If you can’t contact people personally: Send a professionally written confirmation e-mail.
Verifying permission for an old, outdated, or questionable list can prove frustrating even if you follow these steps because people change their e-mail addresses from time to time and because your database might not include the information you need to effectively sort through an inherited list.
If the aforementioned steps seem highly labor intensive or prove to be impossible — or if you can’t make a determination because of the organizational state of your database — you should probably bite the bullet and discard the list or attempt to reestablish permission with the people on your inherited list without sending an e-mail.
If your list contains additional contact information other than the e-mail address, consider using direct mail, phone calls, and other advertising methods to drive the prospects through an explicit sign-up process on your website or at a physical location.
Minimizing Spam Complaints
Spam is also known as unsolicited commercial e-mail. Although numerous stories, analogies, and myths exist about the origin and meaning of spam, one thing is for sure — consumers don’t like receiving it.
Even if your e-mail doesn’t meet the legal definition of spam, consumers can easily report your e-mail as spam and thus impede your ability to send e-mail in the future. For example, Yahoo! customers can deem your e-mail as spam with a click of a button (see Figure 2-3). Most ISPs (including AOL, Yahoo!, Gmail, and Hotmail) give their customers Spam buttons to use to block suspected spammers.
Figure 2-3: Most ISPs allow customers to report e-mails as spam.
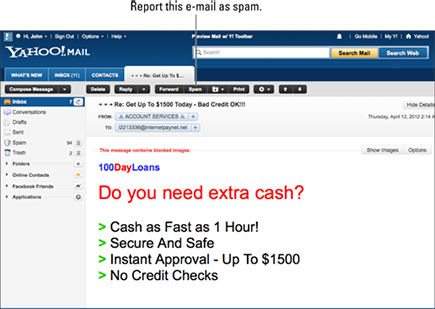
Because consumers have control over the Spam button, no e-mail marketing strategy is immune to complaints. Keeping your e-mails in line with the following guidelines is the best way to ensure that your spam complaints remain within industry tolerances.
Allowing your audience to unsubscribe from receiving e-mails
The CAN-SPAM Act requires that you include a way to let your audience unsubscribe from receiving future e-mails from you, but the law doesn’t specify which mechanisms are appropriate for processing unsubscribe requests. You can ask your subscribers to reply to your e-mails with their unsubscribe request and manually keep track of your unsubscribed prospects and customers, but this process can be tedious with larger lists.
The most professional practice, and the most automated, for processing unsubscribe requests is to use an EMP to automatically and permanently remove anyone who unsubscribes from all e-mail lists in one click. Figure 2-4 shows a one-click unsubscribe link in the footer of an e-mail.
Figure 2-4: E-mail recipients can safely unsubscribe in one click with this link.

Courtesy of Constant Contact
Most reputable EMPs automatically insert a one-click unsubscribe link into your e-mails. When a subscriber clicks the link, the EMP automatically removes the subscriber or changes the status of the subscriber in the EMP’s database to Unsubscribed so that the subscriber stops receiving e-mails immediately.
Keeping your e-mails from looking like spam
To avoid having your e-mails reported as spam, understand how consumers evaluate e-mails. When you think about whether your audience is likely to perceive your e-mail as spam, remember that spam is in the I of the receiver:
• I don’t want it. Unwanted marketing e-mails are perceived as spam by most consumers, especially if they feel that they didn’t authorize the sender to send it. Sometimes, consumers even start to perceive e-mails as spam after they receive them for months just because they no longer want them.
• I can’t verify it. If consumers can’t tell whether an e-mail came from a legitimate source, they perceive it as spam. Most consumers look at the From line in an e-mail header to determine whether an e-mail is familiar.
• I think it’s too frequent. Consumers tend to perceive frequent e-mails as spam when they feel that the content is irrelevant, repetitive, or too long.
Even when consumers don’t perceive your e-mail as spam, they might be inclined to click the Spam button on your e-mail for one or more of the following reasons:
• They can’t figure out how to unsubscribe from your e-mail.
• They don’t trust the unsubscribe link in your e-mail.
• They accidentally click the Spam button while sorting through their e-mail inbox.
• They unintentionally include your e-mail while clicking the Spam button on a large group of other spam e-mails.
Keeping spam complaints to a minimum is a matter of adhering to professional practices and consumer preferences over the course of your entire e-mail marketing strategy.
• Say thanks. Send a welcome e-mail immediately after the subscriber joins the list, as shown in Figure 2-5.
• Send e-mail reminders. Insert a paragraph of text at the top of every e-mail reminding the recipient how you obtained his e-mail address.
• Keep your e-mail frequency in line with your e-mail content and your e-mail list subscribers’ expectations. You can read more about the relationship between frequency and content later in this list.
• Reinforce branding. Include your logo and colors on your sign-up form and make sure that future e-mails match your brand. (Read more about this in Chapter 4 of this minibook.)
• Reinforce familiarity. Make sure that every e-mail’s From line is memorable and familiar. (Read more on this in Chapter 4 of this minibook.)
Figure 2-5: This welcome e-mail reinforces permission and helps reduce spam complaints.
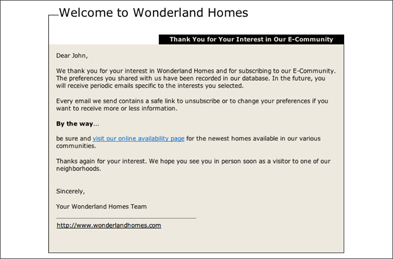
Courtesy of Wonderland Homes and Constant Contact
• Send a reminder letter. Send a permission reminder letter periodically that tells your subscribers exactly how you obtained their e-mail address and gives them links for updating their preferences and unsubscribing.
• Make your e-mail content valuable so that your e-mail list subscribers continue to want your e-mails. You can read more about creating value in your e-mails in Chapter 5 of this minibook.
• Make your sign-up process memorable for your list subscribers and clearly identify your business in every e-mail’s From line so that your audience can verify the source of your e-mails. Ideas for optimizing your e-mail’s From line appear in Chapter 4 of this minibook.
• Ask everyone who unsubscribes from your e-mail list to tell you why he or she doesn’t want your e-mail. You can then adjust your strategy accordingly.
• Use an EMP that authenticates your e-mails. You can read more about e-mail authentication in Chapter 7 of this minibook.
• Include a description of your e-mail content and your typical frequency in your sign-up process. For example, if you send a monthly e-mail newsletter along with periodic promotions to your e-mail list, your e-mail list sign-up form might include a sentence that reads
Signing up allows you to receive our monthly e-mail newsletter as well as periodic special offers related to our newest products.
• Send only the content that your e-mail list subscribers expect you to send. For example, if potential e-mail list subscribers share their e-mail address to receive a quote for your services, don’t send them offers unless they gave you permission as part of requesting a quote.
• Allow your e-mail list subscribers to choose their own interests. If you send several distinct types of e-mail content — such as coupons and event invitations — give your e-mail list subscribers a list of categories to choose from when signing up. Make sure to give them a mechanism for changing their interests, such as a link to their profile, in every e-mail.

 Although understanding that some e-mail messages fall outside the definition of commercial e-mail is important, understanding that all e-mails sent in the name of your business can be construed by the recipient as commercial in nature is equally important. Best practice is to make sure that all your business-related e-mails are legally compliant.
Although understanding that some e-mail messages fall outside the definition of commercial e-mail is important, understanding that all e-mails sent in the name of your business can be construed by the recipient as commercial in nature is equally important. Best practice is to make sure that all your business-related e-mails are legally compliant.