Chapter 7: Maximizing E-Mail Deliverability
In This Chapter
![]() Dealing with bounced and blocked e-mail
Dealing with bounced and blocked e-mail
![]() Understanding e-mail content filters
Understanding e-mail content filters
![]() Maximizing delivery rates
Maximizing delivery rates
![]() Working with emerging delivery technology
Working with emerging delivery technology
Thinking about the early days of postal mail delivery conjures up images of Pony Express riders traveling long distances and risking their lives to get mail delivered, proudly in the name of the United States of America. Although sticking a stamp on a letter or postcard and dropping it off at a U.S. Postal Service office doesn’t necessarily assure its delivery to someone’s mailbox, mail carriers most often do succeed in delivering your mail to the mailbox of the intended addressee. Or, they return your mail to the mailbox specified in the return address, along with a clear reason for the failed delivery.
E-mail delivery, though, isn’t quite as trustworthy as the U.S. Postal Service. Even e-mail sent to a correct e-mail address doesn’t always reach the inbox, and returned e-mail doesn’t always include unmistakable reasons for the failed delivery.
However, the good news is that the positives of e-mail marketing greatly outweigh the deliverability issues inherent to sending commercial e-mail. This chapter uncovers the various reasons why some e-mail fails to reach an inbox and then offers solutions for maximizing your e-mail delivery rates.
Managing Bounced and Blocked E-Mail
Sometimes, e-mail is simply returned to the sender either by the e-mail server or by a software application, such as an e-mail program or delivery control system. You hear the terms bounced and blocked applied to returned e-mail somewhat interchangeably, but the two have some slight differences:
• Bounced: A bounced e-mail happens on a per-e-mail basis when an e-mail is returned because of conditions that make a particular e-mail undeliverable, such as a full e-mail inbox or an e-mail address that is misspelled or doesn’t exist. Bounces can be hard or soft, which you discover in a bit.
• Blocked: A blocked e-mail happens on an all-inclusive basis when an e-mail is returned because of characteristics that make a particular type of e-mail unwanted, such as when a systems administrator decides to refuse all e-mails with attachments or all e-mails from a particular sender.
E-mail is usually returned with code that indicates the reason for the bounce or the block. Most of the time, the code is unintelligible to the average human. Figure 7-1 shows an example of an e-mail returned to the sender with a bounce code.
When you team with an E-Mail Marketing Provider (EMP), you don’t have to spend time scanning through lines of HTML because most EMPs automatically file bounced and blocked e-mails into a bounce report. A bounce report shows how many of your e-mails bounced and were blocked as well as the plain-English reason for the bounce or block response.
Figure 7-2 shows a bounce report generated by an EMP. You can see the number of bounced e-mails by category as well as individual bounced e-mails and associated database records.
Figure 7-1: A bounce code can be difficult to interpret without the help of an EMP.

Figure 7-2: Use a summary bounce report to see the number of bounced e-mails by category.
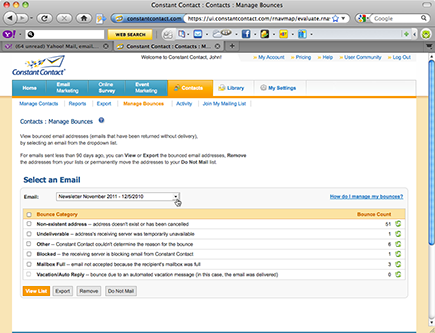
Courtesy Constant Contact
Taking action on bounced e-mail
Bounced e-mails are generally unavoidable because the causes of bounced e-mail fall outside your direct control. However, you can take some reasonably effective steps to minimize bounced e-mail.
The following sections show you how to deal with bounces and when to take corrective action.
Dealing with hard bounces
A hard bounce is an e-mail that’s returned because a permanent condition makes delivering the e-mail impossible. When your EMP’s bounce report shows e-mails delivered to nonexistent addresses, your e-mail can’t be delivered to that address no matter what action you take. Nonexistent e-mail addresses are either
• Misspelled (for example, name@hotmai.lcom)
• Invalid (such as when your subscriber’s e-mail address is no longer in service due to a job change)
You can check your hard-bounce report for obviously misspelled e-mail addresses and correct them in your database. Most of the time, though, you can’t tell whether an e-mail address is misspelled or invalid. In those cases, you need to obtain a new e-mail address.
Dealing with soft bounces
A soft bounce happens when the delivery of an e-mail is delayed temporarily. Soft bounces happen because of technical conditions inherent in the technology that make e-mail delivery possible. Examples include
• A full mailbox
• A server that’s temporarily down
• A software application that can’t accept the e-mail
Reducing blocked e-mails
Blocked e-mails are sometimes temporary and sometimes permanent, depending on whether the server or software blocking the e-mail does so in response to the content of a single e-mail or the characteristics of a specific type of e-mail. The following sections show how you can keep from being blocked by someone on your e-mail list.
Responding to a challenge response system
A challenge response system is a software program that returns all unrecognized e-mail to the sender with instructions for getting the e-mail delivered that only a live person is capable of following, to verify that the sender is a real human being — not a computer generating e-mail addresses. Figure 7-3 shows an e-mail returned by a challenge response system that asks the sender to click a link and fill out a form.
Figure 7-3: This challenge response e-mail asks the sender to verify its legitimacy.
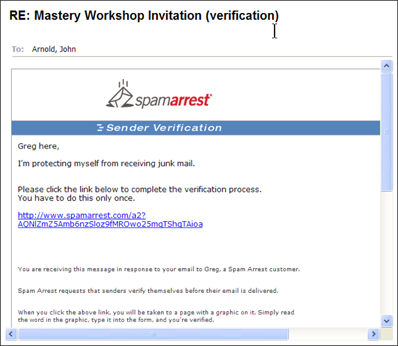
Courtesy of SpamArrest
Challenge responses are generated by third-party applications that integrate into e-mail applications. For example, someone who wants to eliminate computer-generated spam might purchase a challenge response application to verify all e-mails sent to his AOL e-mail address. If you send e-mail to someone with a challenge response system, the returned e-mail might ask you to click a link and enter specific characters in a form field or reply to the e-mail with a specific subject line. Following the instructions in the returned e-mail adds your server address or e-mail address to the subscriber’s friends list or address book so that future e-mails are delivered without a challenge. Spam-blocking technology is getting better all the time, so you probably won’t run into challenge responses too much.
Keeping your e-mail address or server off a block list
A block list (also known as a blacklist) is a database that contains the domain names and server addresses of suspected spammers. Block lists are maintained by Internet service providers (ISPs) and other companies that monitor spam complaints across the Internet. Server addresses and domain names are added to block lists based on the number of spam complaints logged by consumers.
If you send an e-mail that gets too many spam complaints, the server you use to send your e-mail might be added to one or more block lists. To keep your server off of block lists, keep the number of spam complaints you receive under 1 in 1,000 e-mails and use a reputable E-Mail Marketing Provider. (You can read more about avoiding spam complaints in Chapter 2 of this minibook.)
Avoiding spam trap e-mail addresses
A spam trap is a false e-mail address placed on the Internet by a company with an interest in reducing spam. When spammers using web crawlers to capture e-mail addresses try to send an e-mail to the spam trap e-mail address, the sender’s domain and server address are automatically added to the block list. (A web crawler is a computer program that searches the Internet for specific types of content, such as lines of text that look like an e-mail address.) Many companies share their spam trap block lists. If you happen to send e-mail to a spam trap address, your deliverability could be doomed.
Here are some ways to avoid spam trap e-mail addresses:
 • Don’t surf the Internet to obtain e-mail addresses. Besides risking your deliverability, this behavior is also illegal.
• Don’t surf the Internet to obtain e-mail addresses. Besides risking your deliverability, this behavior is also illegal.
• Don’t send e-mail to a purchased list. Purchased lists are often collected without permission and can contain spam trap addresses.
• Send a welcome e-mail to every new list subscriber and immediately remove e-mail addresses that return your welcome e-mail. That way, you can weed out anyone who tries to maliciously join your e-mail list by using a known spam trap address.
Getting past e-mail firewalls
An e-mail firewall is a piece of hardware or a software application programmed to identify and block e-mails that appear untrustworthy. Firewalls can be customized and configured to block almost any e-mail element. For example, a system administrator at one company might configure a firewall to block e-mails with certain types of content, and another system administrator might configure a firewall to block e-mails from certain senders while ignoring the content altogether.
Because firewalls have so many variables, telling whether your e-mail is being blocked by a firewall is usually impossible. If you use an EMP that provides blocked e-mail addresses in its bounced report, however, you can at least find out which e-mail addresses are being blocked and then take action to try to get the e-mail delivered.
Changing your tactics to get e-mail delivered to a blocked address is difficult, but the following remedies might prove effective:
• Ask your audience to add your e-mail address to their address book or contacts list when they sign up for your e-mail list. Some content- blocking systems allow e-mail to go through if the sender’s e-mail address is in the recipient’s address book.
 In your welcome letter and subscription reminders, give your audience instructions for adding your e-mail address, as shown in Figure 7-4. This e-mail asks the reader to help ensure delivery by adding the sender’s e-mail address to the reader’s address book.
In your welcome letter and subscription reminders, give your audience instructions for adding your e-mail address, as shown in Figure 7-4. This e-mail asks the reader to help ensure delivery by adding the sender’s e-mail address to the reader’s address book.
Figure 7-4: Help ensure delivery.
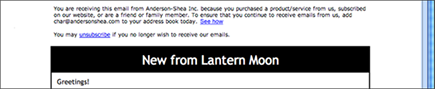
Courtesy of Anderson-Shea, Inc.
• Obtain an alternative e-mail address from each of your blocked subscribers. Sometimes, half the battle with blocked e-mail is knowing that a particular e-mail address is being blocked. When your EMP’s bounce report shows a particular blocked e-mail address, you can ask your subscriber to provide a different address.
• If the blocked e-mail address is a work address, ask the IT expert at your subscriber’s company to add your EMP’s e-mail server address to the friends list on the company’s e-mail server. A friends list (also known as a white list) is a database containing e-mail addresses from welcome senders. Some firewalls ignore their blocking instructions when the sender’s e-mail address exists in the friends list.
Reducing Filtered E-Mail
An e-mail filter is a program that scans the content of your e-mail to identify whether your e-mail contains unwanted content. If your e-mail contains content that’s identified as potentially unwanted, the program places the e-mail into a holding place (such as a junk folder) or tags the e-mail with a message to identify it as potentially unwanted.
Sometimes an e-mail is filtered even though the recipient wants the e-mail. Desirable e-mail content that still gets filtered is a false positive. False positives are all too common because of the enormous amount of spam e-mail content that’s similar in nature to legitimate e-mail content. Some e-mail filters result in more false positives than others because the people behind the filters get to decide what kinds of content are considered unwanted. For example, an e-mail that contains the word drug might be filtered by a systems administrator who believes that certain prescription drug advertisements are spam, even if the word is being used by a bookstore to describe a book.
Unfortunately, you can’t tell whether your e-mail is filtered unless the recipient notifies you that your e-mail landed in the junk folder or that your e-mail is being delivered with a filter tag. The following sections explain how you can get a higher percentage of your e-mail through the most common types of filters.
Establish your sender reputation
Getting more e-mail delivered starts with sending your e-mail from a reputable e-mail server. According to a recent study conducted by Return Path (www.returnpath.com), 77 percent of e-mail delivery issues occur because of the sender’s reputation. Most companies that provide e-mail delivery for their customers consider the reputation of the sender when filtering e-mail.
• Authenticate your e-mail: Authentication allows e-mail servers to identify the sender of an e-mail. (Authentication is covered later in this chapter.)
• Eliminate customers with high spam complaints: EMPs send e-mails from their own servers on behalf of their customers even though the e-mails appear to come from their customers. Because too many spam complaints might cause the EMP’s servers to become block listed, make sure that your EMP takes action when one of its customers receives too many spam complaints. Reputable EMPs keep their overall complaint rates low — and your sender reputation as clean as possible.
• Affirm the quality of its customers’ e-mail lists: Although EMPs can’t guarantee or predetermine the quality of their customers’ e-mail lists, reputable EMPs require customers to adhere to strict permission policies to caution their customers when attempting to use e-mail addresses that could generate a high number of complaints.
• Adopt a policy for spam tolerance: Some businesses, such as those in the financial and medical industries, inherently receive a lot of spam complaints because their legitimate e-mail content looks similar to a lot of spam e-mails. Use an EMP that either has options for such businesses or has a policy to refer such businesses to another service that specializes in industries where spam complaints may be higher than average.
• Keep customers from sending repeated e-mails to unknown users: Spammers send billions of e-mails to every possible e-mail address hoping to uncover real addresses. Because ISPs (such as AOL, Yahoo!, and Hotmail) spend a lot of money bouncing e-mails sent by spammers, they aren’t appreciative of e-mails sent to nonexistent addresses. As a result, your deliverability could suffer if your e-mail server is labeled as a nuisance. To help protect your sender reputation (as well as that of the EMP), most reputable EMPs stop sending your e-mail to nonexistent e-mail addresses after two or three attempts even if you don’t remove the e-mail addresses yourself.
Understand automatic content filtering
A small percentage of e-mail content filters are controlled completely by e-mail system administrators to keep their users from administering their own filter settings. The e-mail system administrator (usually IT personnel at a company, or an ISP) sets up the automatic filter with specific global parameters that apply to all e-mail users in the same way.
Automatic filtering affects a relatively small percentage of your e-mails. You can’t do much about it unless you happen to know the system administrator and you can coax him or her into relaxing a particular company’s filtering standards.
Understand user-controlled content filtering
The majority of e-mail filters are included within e-mail programs and written with broad consumer preferences in mind to filter e-mail content that has spam-like characteristics. E-mail filters within e-mail programs almost always allow the user to access the default filter settings and alter them according to user preferences.
• Generic Subject lines and anonymous From lines
• PDF attachments containing advertisements
• Images of entire advertisements without any plain text
• Excessive promotional phrases and words
Most consumers don’t alter their default e-mail filter settings manually, so avoiding false positive filtering by the most common e-mail filters is partly a matter of building your e-mails to exclude the most commonly filtered content. Figure 7-5 shows a sample of the headers in a junk e-mail folder.
Figure 7-5: Filters often look for spam-like content.

You can prevent your e-mails from looking like spam if you do the following:
• Don’t include your subscriber’s first name in the Subject line of your e-mails. The practice is common among spammers because most consumers can’t understand how a complete stranger could know their first name. (Spammers use web crawler programs to pull the information out of your e-mail headers.) After being tricked a few times, most consumers associate this technique with spam.
• Always include a From line in your e-mail header. Excluding the From line is an attempt by spammers to trick people into opening e-mails in the hope that the consumers are curious to find out who the e-mail is from. Most filters automatically identify e-mails with no From line as untrustworthy.
• Avoid excessive punctuation (such as strings of exclamation points!!!!!) and “crafty” symbols (such as ¢ents or dollar $ign$). Spammers often use strings of punctuation to make their offers more eye-catching, and the practice is just as attention-catching to e-mail filters.
• Don’t send marketing e-mails with attachments. Consumers are understandably nervous about e-mail with unfamiliar attachments, and e-mails sent to more than a few people with attachments are usually filtered.
• DON’T WRITE SENTENCES IN ALL CAPITAL LETTERS. Writing in all capital letters draws attention to e-mail headlines, and this tack is as annoying to consumers as it is noticeable to e-mail filters.
Building your e-mail content with the most common filter settings gets more of your e-mail delivered to the inbox, but several types of user-controlled filters aren’t so simple to sidestep.
Individual filters
A small percentage of consumers do access their filter settings to make changes. Figure 7-6 shows some of the individual filter settings available in Yahoo! Mail.
Figure 7-6: Yahoo! Mail allows users to access and personalize filter settings.
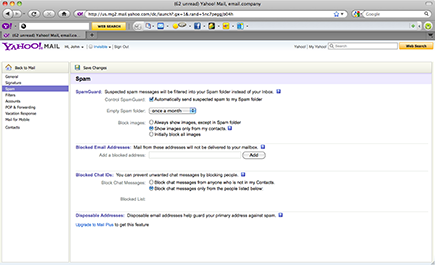
If someone on your e-mail list accesses his personal filter settings to set up a filter, your e-mail content is obviously subject to being filtered based on the personal settings for that user. Because you can’t know every personal setting in an individual filter, you can do little to get your e-mail through. Accessing filter settings allows the user to personally filter one or more of the following e-mails:
• From specific senders
• Containing specific words or phrases
• With links or images (usually converted to plain text only)
• From senders not in the user’s address book
• With certain domain extensions, such as .biz or .info
• With certain types of encoding, such as international languages
• With attachments
Trained content filters
Some filters begin with broad default settings and are automatically updated based on whether the user identifies certain e-mails as unwanted. The most common example is the Spam button (as you can read about in Chapter 2 of this minibook), which is a clickable link in an e-mail program that reports the e-mail as spam to the e-mail system administrator. Clicking a Spam button not only reports an e-mail as unwanted but also scans the content to identify content that recurs frequently in the reported e-mails.
When a user clicks a Spam button, a filter scans the e-mail to look for words, phrases, and other types of content to determine whether there is a pattern to the types of content being reported as spam by the user. For example, if a user continues to click the Spam button on multiple e-mails containing the phrase discount meds, the filter begins to learn that phrase and automatically filters any e-mails containing that phrase to a junk folder.
Understanding E-Mail Authentication
Filtering and blocking technologies are constantly improving. Although it might seem as if spammers are always one step ahead of the game, several promising technologies are emerging to help reduce spam.
Spammers forge the e-mail addresses they send e-mails from by using technical tricks to replace the legitimate header information in an e-mail with false information. Several major ISPs have developed technology to validate the From information in an e-mail. The following is a list of the most popular sender authentication methods. The list also represents the most likely technology to emerge as standards for your own deliverability.
• Sender ID: This technology, developed by Microsoft, uses an algorithm to select a header field containing the e-mail address responsible for sending the e-mail. The sending e-mail address is then checked against a list of authorized e-mail servers for that e-mail address.
• DomainKeys: This technology, developed by Yahoo!, uses cryptography to generate a set of unique public and private encryption keys. All outgoing messages are digitally signed by the sender using the private key (known only to authorized senders), and the public key is published with the sender’s Domain Name Service (DNS) so that recipients can use the public key to validate that the correct private key was used by the sender.
• Sender Policy Framework (SPF): SPF is similar to Sender ID in that the technology validates the sender’s From information by allowing the owner of a specific domain to specify his or her e-mail sending policy or SPF. When someone receives an e-mail that appears to originate from the specified domain, the e-mail server receiving the message can check the SPF record to see whether the e-mail complies with that domain’s specific policy.
Self-publishing your own authentication information is beyond the scope of this book, but you can easily employ authentication technology in your e-mails by using a reputable EMP that complies with current authentication standards to send your e-mails.

 Although some bounced or blocked e-mails will never get delivered, some bounced and blocked e-mails are
Although some bounced or blocked e-mails will never get delivered, some bounced and blocked e-mails are