Chapter 22 Novell eDirectory for eBusiness
This chapter covers the following testing objectives for Novell Course 575: Novell eDirectory Design and Implementation:
![]() Explain Why eDirectory Design Is Important to the Success of Your eBusiness
Explain Why eDirectory Design Is Important to the Success of Your eBusiness
![]() Complete a Needs Analysis
Complete a Needs Analysis
![]() Implement the Network Infrastructure
Implement the Network Infrastructure
![]() Create a User Accessibility Needs Strategy for eBusiness
Create a User Accessibility Needs Strategy for eBusiness
![]() Implement the eDirectory Tree Structure
Implement the eDirectory Tree Structure
![]() Implement a Partition and Replica Strategy for Your eDirectory Tree
Implement a Partition and Replica Strategy for Your eDirectory Tree
Welcome to eWorld!
A sure sign that we live in a new century is the electronicization of everything we see, feel, hear, and touch: eLearning, email, eBay and, of course, eBusiness.
eBusiness is the catalyst for success in the Internet generation. Today’s most powerful eBusinesses use the Internet to share data with and strengthen relationships between their employees, customers, business partners, and suppliers. Today, major corporations around the world are rethinking their businesses in terms of the Internet and its new capabilities. Companies are using the Web to purchase products and services from other companies, to collaborate on sales promotions, to complete joint research, and to participate in a plethora of other business-related activities.
Previous versions of eDirectory provided services for the standard corporate networking environment. eDirectory 8.7 provides a full-service directory with fault tolerance, security, and scalability in the Internet-based eBusiness environment.
Throughout Part III, we’ve explored eDirectory design from the network’s point of view. You learned that eDirectory design can have a profound effect on the success or failure of your net, and we illustrated this point by preparing, designing, and implementing ACME’s eDirectory tree. I’m sure you’ll agree that the previous four chapters have been challenging and rewarding at the same time.
Now, in this final chapter of the CNE Study Guide for NetWare 6, we’ll explore eDirectory design and implementation from an eBusiness point of view. You’ll discover the technologies and products that Novell provides for eBusinesses, and learn what it takes to succeed in the Internet generation. Then we’ll plot specific strategies for tree, partition, and accessibility design for eBusiness. Finally, in the ultimate lesson, we’ll implement eDirectory for eBusiness by pulling together everything you’ve learned throughout this study guide.
So, let’s get started, and not waste any eTime.
Test Objective Covered:
![]() Explain Why eDirectory Design Is Important to the Success of Your eBusiness
Explain Why eDirectory Design Is Important to the Success of Your eBusiness
Simply stated, eBusiness is business conducted on the Internet. eBusiness includes buying and selling products and services, accommodating customers, and collaborating with business partners over the Net. The key to a successful eBusiness design is to shift your thinking from inward to outward. Outward thinking means to focus on the application requirements of your customers and business partners. You’ll need to answer questions, such as How many objects can I expect? What applications do my customers need to run? What type of firewall security is required?
An effective eBusiness communication strategy includes an automated Web site with eDirectory on the backend. With eDirectory design, this equates to creating an application that effectively serves your external customers over the Internet.
In this lesson, we’ll rediscover eDirectory from an eBusiness point of view. We’ll study:
![]() eDirectory features for eBusiness
eDirectory features for eBusiness
![]() eDirectory technologies for eBusiness
eDirectory technologies for eBusiness
![]() eDirectory products for eBusiness
eDirectory products for eBusiness
![]() eDirectory roles for eBusiness
eDirectory roles for eBusiness
So, let’s start at the beginning: What can eDirectory do for your eBusiness?
TIP
Your eBusiness strategy must accommodate two different communication schemes:
![]() Business-to-Business (B2B)—B2B organizations exchange goods and services directly over secure network connections. This eliminates paperwork and other tedious expenses.
Business-to-Business (B2B)—B2B organizations exchange goods and services directly over secure network connections. This eliminates paperwork and other tedious expenses.
![]() Business-to-Customer (B2C)—A business allows customers to download, make transactions, and gain access to information over the Internet.
Business-to-Customer (B2C)—A business allows customers to download, make transactions, and gain access to information over the Internet.
eDirectory provides many features and technologies to help you build an infrastructure for your eBusiness. First and foremost, fault tolerance is critical for eBusiness. When the network hosting your business is down, your customers could become annoyed and take their business elsewhere. This is much more serious than inconveniencing internal employees. For every minute your business is unavailable, your company is potentially losing millions of dollars and hundreds of customers.
Another eDirectory feature that positively affects your eBusiness is user accessibility. The goal is to provide seamless electronic access to authorized users while keeping the bad guys out. eDirectory provides an excellent balance of accessibility and security. Remember, we live in a world of instant gratification, and customer patience is measured in seconds. If logging in takes a long time or is inconvenient, users will go elsewhere to find the same service.
The scalability provided by eDirectory is also very helpful in the eBusiness environment. For example, you can have seven applications running on seven servers, each with its own profile-based customization. This enables you to service your customers in a very personalized, yet efficient way. When you create an eDirectory design specifically for eBusiness, you can
![]() Deploy eDirectory-enabled custom applications
Deploy eDirectory-enabled custom applications
![]() Support open standards such as XML and Java
Support open standards such as XML and Java
![]() Increase productivity and collaboration with your business partners
Increase productivity and collaboration with your business partners
![]() Expose needed portions of your network resources to specific business partners over the Internet while maintaining a high level of security
Expose needed portions of your network resources to specific business partners over the Internet while maintaining a high level of security
![]() Accelerate business processes, allowing your eBusiness partners to communicate directly with each other and automatically update their databases with the most current information
Accelerate business processes, allowing your eBusiness partners to communicate directly with each other and automatically update their databases with the most current information
![]() Build customer loyalty and create highly personalized profiles
Build customer loyalty and create highly personalized profiles
Now that you understand the benefits eDirectory provides in an eBusiness environment, let’s look at two specific eBusiness-related technologies: DirXML and tree federation.
With an eDirectory-enabled eBusiness, you can tailor your services and applications to the individual needs of customers and business partners. The following are two specific directory technologies that provide great value in an eBusiness environment:
![]() DirXML
DirXML
![]() Tree federation
Tree federation
DirXML is a relatively new Novell technology that allows communication between two isolated directory trees. DirXML extends the data replication and synchronization capabilities of eDirectory to other data sources, including isolated eDirectory trees. This eliminates the isolation of your data and enables you to communicate directly with other customer and partner trees.
TIP
Although DirXML isn’t covered in detail in this course, you should check it out by visiting Novell’s Web site, attending Novell Course 992, “Directory and Database Integration Using DirXML,” or visiting Novell’s ATT course covering NSure 2.0.
Tree federation uses DirXML to combine multiple eDirectory trees into a united federation—just like in Star Trek. With this new Novell technology, you no longer need to create separate objects in multiple trees. Instead, object management is united across multiple trees.
Tree federation of eDirectory trees provides powerful opportunities for business relationships among companies, customers, and business partners. The following is a list of advantages of using tree federation for eBusiness:
![]() Single point of administration—Tree federation removes the requirements to replicate User objects in order to grant rights to other trees. With this technology, the owner of the tree creates and manages the User objects, whereas administrators in federated trees simply grant rights to them.
Single point of administration—Tree federation removes the requirements to replicate User objects in order to grant rights to other trees. With this technology, the owner of the tree creates and manages the User objects, whereas administrators in federated trees simply grant rights to them.
![]() Merging benefits—Merging federated trees is very simple. You just have to make sure that the appropriate rights are granted. No other messy administrative pain is required.
Merging benefits—Merging federated trees is very simple. You just have to make sure that the appropriate rights are granted. No other messy administrative pain is required.
![]() Internet standard namespace implementation—With federation, you can create a special Internet-standard namespace DNS-routed tree. What is a DNS-routed tree? It’s an eDirectory tree installed with a tree name of DNS. Now you can have the best of both worlds. The objects in a DNS-routed federated tree exist in the DNS namespace, but can be managed in the central eDirectory tree.
Internet standard namespace implementation—With federation, you can create a special Internet-standard namespace DNS-routed tree. What is a DNS-routed tree? It’s an eDirectory tree installed with a tree name of DNS. Now you can have the best of both worlds. The objects in a DNS-routed federated tree exist in the DNS namespace, but can be managed in the central eDirectory tree.
Of course, tree federation does have disadvantages as well:
![]() Requires visibility through a firewall—Federated trees must be visible through a company’s firewall. Because of this, they need special security considerations and trusted domains.
Requires visibility through a firewall—Federated trees must be visible through a company’s firewall. Because of this, they need special security considerations and trusted domains.
![]() Required VPN—Communication between federated trees occurs using NetWare Core Protocols (NCPs). Because NCP packets are not secure, federated trees must be connected by virtual private networks (VPNs).
Required VPN—Communication between federated trees occurs using NetWare Core Protocols (NCPs). Because NCP packets are not secure, federated trees must be connected by virtual private networks (VPNs).
![]() Limited application port—Applications written to use 100% LDAP communication with eDirectory should have no problem working with DNS-federated trees. However, applications that must resolve to the tree root might not work in the federated environment because they will never be able to find the true united root.
Limited application port—Applications written to use 100% LDAP communication with eDirectory should have no problem working with DNS-federated trees. However, applications that must resolve to the tree root might not work in the federated environment because they will never be able to find the true united root.
Now that you’ve learned two of eDirectory’s most powerful eBusiness technologies, let’s take a look at the goodies that Novell provides for eBusiness.
Novell embraces the Internet through its pervasive oneNet vision:
In a oneNet World, individuals must be able to access their own information, the way they want it, anytime, anywhere, from any device.
Novell Net services secure and power all types of networks across all leading operating systems. In addition, almost all tools, utilities, and features in NetWare 6 touch Novell Web services.
All of these Novell products enhance your eBusiness deployment. In summary, these products and services are designed to unify diverse networks and technologies for the purpose of simplifying eBusiness processes and communication. The following is a description of Novell’s eDirectory-enabled products for eBusiness:
![]() iLogin—iLogin provides a corporate portal for accessing all company services from a single location. This portal technology can be customized to include a variety of “gadgets.”
iLogin—iLogin provides a corporate portal for accessing all company services from a single location. This portal technology can be customized to include a variety of “gadgets.”
![]() eLogin—Allows external Novell partners, CNEs, CNIs, and developers to access their Novell accounts through a single login.
eLogin—Allows external Novell partners, CNEs, CNIs, and developers to access their Novell accounts through a single login.
![]() eGuide—Allows users to query a variety of sources and retrieve information through a Web-based application. When eGuide is coupled with eDirectory 8.7, companies can implement a complete out-of-the-box corporate address book solution, with no need to enter information in multiple applications or databases. Furthermore, the default eGuide protocol is LDAP, thus giving users access to myriad public directories on the Internet.
eGuide—Allows users to query a variety of sources and retrieve information through a Web-based application. When eGuide is coupled with eDirectory 8.7, companies can implement a complete out-of-the-box corporate address book solution, with no need to enter information in multiple applications or databases. Furthermore, the default eGuide protocol is LDAP, thus giving users access to myriad public directories on the Internet.
![]() Novell OnDemand—Enables you to offer access to electronic goods and services over the Internet on a fee basis using eDirectory 8.5 (or above).
Novell OnDemand—Enables you to offer access to electronic goods and services over the Internet on a fee basis using eDirectory 8.5 (or above).
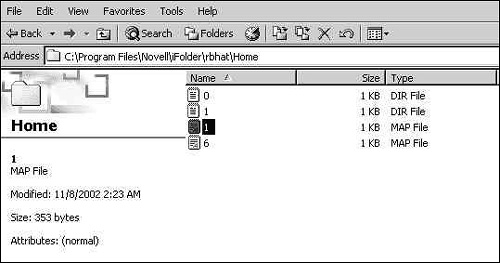
![]() iFolder—iFolder provides a central Web-based home folder for simple, secure access to your personal file from any machine on any network. You can store, copy, move, and delete files in iFolder in the same way you do from your workstation. The beauty of iFolder is that it enables you to update your files across desktop computers, laptops, and other connected devices wherever you happen to be.
iFolder—iFolder provides a central Web-based home folder for simple, secure access to your personal file from any machine on any network. You can store, copy, move, and delete files in iFolder in the same way you do from your workstation. The beauty of iFolder is that it enables you to update your files across desktop computers, laptops, and other connected devices wherever you happen to be.
![]() GroupWise WebAccess—GroupWise WebAccess is the Web version of the GroupWise messaging system. GroupWise WebAccess enables you to send and receive email messages, appointments, tasks, notes, and attached files via a simple, browser-based interface. No client installation is required.
GroupWise WebAccess—GroupWise WebAccess is the Web version of the GroupWise messaging system. GroupWise WebAccess enables you to send and receive email messages, appointments, tasks, notes, and attached files via a simple, browser-based interface. No client installation is required.
![]() Novell Account Management—A directory-enabled solution that enables you to integrate Windows NT, Sun Solaris, and Linux user management functions into eDirectory. This facility makes it possible for you to manage a network of multiple platforms and operating systems from a single interface.
Novell Account Management—A directory-enabled solution that enables you to integrate Windows NT, Sun Solaris, and Linux user management functions into eDirectory. This facility makes it possible for you to manage a network of multiple platforms and operating systems from a single interface.
![]() BorderManager Firewall Services—Protects confidential data and manages user access to intranet and Internet content. You can also use its caching technology to accelerate access to frequently visited Web pages. In addition, the BorderManager Firewall Services augments your existing firewall protection system.
BorderManager Firewall Services—Protects confidential data and manages user access to intranet and Internet content. You can also use its caching technology to accelerate access to frequently visited Web pages. In addition, the BorderManager Firewall Services augments your existing firewall protection system.
![]() BorderManager VPN Services—Provides a secure, remote, connectivity system to create your own virtual private network. With this Novell product, you can provide remote offices, mobile users, customers, and business partners with secure access to your confidential data over the Internet. In addition, BorderManager VPN Services significantly lowers your security administration costs.
BorderManager VPN Services—Provides a secure, remote, connectivity system to create your own virtual private network. With this Novell product, you can provide remote offices, mobile users, customers, and business partners with secure access to your confidential data over the Internet. In addition, BorderManager VPN Services significantly lowers your security administration costs.
![]() Novell Portal Services (NPS)—NPS is a portal integration toolkit for creating secure, customizable portals on the foundation of NetWare 6. NPS helps you integrate internal and external content to increase user productivity. Furthermore, iChain and NPS together enable you to merge eDirectory with an Internet caching system (ICS).
Novell Portal Services (NPS)—NPS is a portal integration toolkit for creating secure, customizable portals on the foundation of NetWare 6. NPS helps you integrate internal and external content to increase user productivity. Furthermore, iChain and NPS together enable you to merge eDirectory with an Internet caching system (ICS).
![]() Internet printing—Offers secure print services across multiple network operating systems. Refer to Chapter 20, “Novell eDirectory Accessibility and Printing Design,” for a more in-depth lesson Novell’s Internet printing strategy for eDirectory.
Internet printing—Offers secure print services across multiple network operating systems. Refer to Chapter 20, “Novell eDirectory Accessibility and Printing Design,” for a more in-depth lesson Novell’s Internet printing strategy for eDirectory.
![]() Novell Modular Authentication Service (NMAS)—The Enterprise edition of NMAS provides a single, cost-effective point of administration for managing, grading, and accessing all authentication methods of your eBusiness.
Novell Modular Authentication Service (NMAS)—The Enterprise edition of NMAS provides a single, cost-effective point of administration for managing, grading, and accessing all authentication methods of your eBusiness.
![]() NDS Authentication Services—NDS-AS provides a single-password authentication system for your network. In addition, NDS-AS includes interfaces for many network platforms and applications to consolidate passwords in a single source.
NDS Authentication Services—NDS-AS provides a single-password authentication system for your network. In addition, NDS-AS includes interfaces for many network platforms and applications to consolidate passwords in a single source.
![]() Novell cryptography support modules—NICI and SSL enable you to secure your eDirectory system with the appropriate 56-bit and/or 1024-bit RSA Cryptography.
Novell cryptography support modules—NICI and SSL enable you to secure your eDirectory system with the appropriate 56-bit and/or 1024-bit RSA Cryptography.
![]() ScheMax—Enables you to make modifications to the eDirectory schema and assists you in managing your eDirectory for eBusiness. With ScheMax, you can administer the eDirectory schema, add classes and attributes, create utility snap-ins, deliver eDirectory content to users, and set attribute entry policies. ScheMax includes a schema administrator, a schema viewer, and a NetWare Administrator snap-in management tool that you can use to modify the eDirectory schema directly.
ScheMax—Enables you to make modifications to the eDirectory schema and assists you in managing your eDirectory for eBusiness. With ScheMax, you can administer the eDirectory schema, add classes and attributes, create utility snap-ins, deliver eDirectory content to users, and set attribute entry policies. ScheMax includes a schema administrator, a schema viewer, and a NetWare Administrator snap-in management tool that you can use to modify the eDirectory schema directly.
![]() Single Sign-On—Eliminates the need for multiple passwords. Novell Single Sign-on V2.1 with v-GO is a directory-enabled software solution.
Single Sign-On—Eliminates the need for multiple passwords. Novell Single Sign-on V2.1 with v-GO is a directory-enabled software solution.
All of these fabulous products provide you with all the tools you need to build a successful eDirectory-based eBusiness. Of course, you can’t do it alone. Now, let’s recruit an eBusiness team.
As we discussed in Chapter 18, “Novell eDirectory Preparation,” you need to recruit a skills-based project team to create an effective eDirectory design. Project members can perform single roles, multiple roles, or specific subtasks within a role. It all depends on the size of your organization and the complexity of your network.
In Chapter 18, we focused on the four roles required in most eDirectory design projects: project manager, eDirectory expert, server administrator, and connectivity specialist. In addition, you might want to consider adding a printing expert, workstation expert, online help personnel, application specialist, and some security developers to the team. After you’ve established a product team, you should make sure that all members have a clear understanding of their responsibilities and priorities.
In addition to the eDirectory roles discussed in Chapter 18, you might need to expand the design team to include the following four eBusiness specialists:
![]() Directory integration expert—If you must synchronize data between multiple trees or integrate separate directories, the directory integration expert can lead the charge. Think of this person as the Captain Picard of your federation starship.
Directory integration expert—If you must synchronize data between multiple trees or integrate separate directories, the directory integration expert can lead the charge. Think of this person as the Captain Picard of your federation starship.
![]() Internet application and database expert—Most eBusiness solutions rely on Internet applications and databases for success. As such, you’ll need experts to implement these critical elements. If you’re creating customized applications, you might also need a developer.
Internet application and database expert—Most eBusiness solutions rely on Internet applications and databases for success. As such, you’ll need experts to implement these critical elements. If you’re creating customized applications, you might also need a developer.
![]() DirXML driver writer—If your federation includes two separate trees, you’ll need a developer capable of writing the required DirXML drivers for communication.
DirXML driver writer—If your federation includes two separate trees, you’ll need a developer capable of writing the required DirXML drivers for communication.
![]() Security expert—To ensure that your data is secure, you need a security expert—especially in today’s economy when eBusiness data drives the eConomy.
Security expert—To ensure that your data is secure, you need a security expert—especially in today’s economy when eBusiness data drives the eConomy.
That completes our first lesson in eBusiness fundamentals. In this lesson, we explored the eDirectory technologies, products and roles required to succeed in today’s eBusiness environment. Of course, this is only the beginning. Now it’s time to tackle eDirectory design for eBusiness.
Test Objectives Covered:
![]() Complete a Needs Analysis
Complete a Needs Analysis
![]() Implement the Network Infrastructure
Implement the Network Infrastructure
![]() Create a User Accessibility Needs Strategy for eBusiness
Create a User Accessibility Needs Strategy for eBusiness
![]() Implement the eDirectory Tree Structure
Implement the eDirectory Tree Structure
![]() Implement a Partition and Replica Strategy for Your eDirectory Tree
Implement a Partition and Replica Strategy for Your eDirectory Tree
Believe it not, your eDirectory design could make or break your company. While most executives are focusing on finances, sales, and marketing, the really smart eBusiness executives are focusing on eDirectory design. After all, the flexibility of your network dictates the quality of communication between employees, customers, and business partners. And we all know that communication is the key to profitability.
Most of the eDirectory design principles that you learned in the previous four chapters apply to eBusiness. However, there are exceptions in which you’ll need to enhance your design for eBusiness. First, your design must focus on applications and databases, not users. You should design the tree so that apps and data can access the information they need all over the Web. If you develop in-house eBusiness applications, make sure that developers design the applications to work with eDirectory.
Second, your design must anticipate growth. eBusiness companies often have unexpected growth spurts and your network must be able to accommodate this. Set up containers where you anticipate growth so that you can easily partition data onto different servers if needed. Also, consider the effect that partition size has on synchronization and estimate the growth of objects within a given partition.
Finally, make sure to design the eDirectory tree to meet your eBusiness goals and objectives. In this lesson, we’ll explore specific eBusiness design guidelines for the following eDirectory components:
![]() Tree design—When you design the upper and lower layers of the eDirectory tree, you’ll want to focus on making the system both productive for customers and easy to manage for employees. Some of the key tree design decisions you’ll have to make include the number of trees you’ll use and the tree structure for your eBusiness.
Tree design—When you design the upper and lower layers of the eDirectory tree, you’ll want to focus on making the system both productive for customers and easy to manage for employees. Some of the key tree design decisions you’ll have to make include the number of trees you’ll use and the tree structure for your eBusiness.
![]() Partition and replica design—Next, your design should include partition boundaries and replica placement. This helps provide scalability, fault tolerance, and resource access. From an eDirectory perspective, partition and replica design focuses on support for applications and managing growth.
Partition and replica design—Next, your design should include partition boundaries and replica placement. This helps provide scalability, fault tolerance, and resource access. From an eDirectory perspective, partition and replica design focuses on support for applications and managing growth.
![]() Accessibility design—Finally, the system should be designed so that both physical and logical resources are easily accessible to employees, customers, and business partners. eDirectory access points and firewalls are two very important design considerations when building a tree for eBusiness.
Accessibility design—Finally, the system should be designed so that both physical and logical resources are easily accessible to employees, customers, and business partners. eDirectory access points and firewalls are two very important design considerations when building a tree for eBusiness.
This is all it takes to design a successful eDirectory for business. Don’t hyperventilate—I’m here to walk you through every step...one at a time. Let’s start at the beginning: tree design for eBusiness.
eDirectory tree design is the most important phase in the design and implementation process. The tree design is even more important when you’re building a network to support employees, customers, and business partners. You should take extra caution in designing eBusiness trees because decisions you make today can have a large affect on your company’s profitability in the future. Furthermore, this importance is amplified when the network spans multiple business partners and geographically separated customers.
To build an efficient tree design for eBusiness, you must follow a series of critical design guidelines, namely:
![]() Tree federation—First, you must determine whether your eBusiness federation will include one, two, or three eDirectory trees.
Tree federation—First, you must determine whether your eBusiness federation will include one, two, or three eDirectory trees.
![]() Tree structure—Second, you must build a flexible eDirectory tree structure to accommodate a variety of geographical sites, hardware, administrative techniques, and access points.
Tree structure—Second, you must build a flexible eDirectory tree structure to accommodate a variety of geographical sites, hardware, administrative techniques, and access points.
Let’s explore eDirectory tree design for eBusiness.
Your eDirectory design should include a specific layout for all the trees in your eBusiness federation. For most organizations, a single tree works best because you have a single user identity on the network, simple administration of security, and a single point of management. However, eBusiness requirements sometimes call for multiple trees. The following are tree design guidelines for creating your eBusiness federation:
![]() One eDirectory tree—If your internal and external customers frequently share information, use a single tree. With one tree, you have a single user identity and a global schema. In Figure 22.1, the workforce and service tree provides both internal enterprise and external eBusiness data.
One eDirectory tree—If your internal and external customers frequently share information, use a single tree. With one tree, you have a single user identity and a global schema. In Figure 22.1, the workforce and service tree provides both internal enterprise and external eBusiness data.
![]() Two eDirectory trees—If your internal and external customers serve different purposes, create two trees and communicate via DirXML. In a multi-tree environment, users in each tree are restricted from accessing the other tree, making the trees more secure. Additionally, if network resources such as printers are included in the eBusiness tree, you should consider creating a second tree for customer facing Web servers. For example, Figure 22.2 shows a workforce tree for internal employees inside the firewall and a services tree for external customers outside the firewall. In a multi-tree environment, you have a flexible resource environment, different schemas, added security, and quicker changes. However, you also have multiple identities, multiple sign-ons, multiple points of administration, and possible data inconsistencies.
Two eDirectory trees—If your internal and external customers serve different purposes, create two trees and communicate via DirXML. In a multi-tree environment, users in each tree are restricted from accessing the other tree, making the trees more secure. Additionally, if network resources such as printers are included in the eBusiness tree, you should consider creating a second tree for customer facing Web servers. For example, Figure 22.2 shows a workforce tree for internal employees inside the firewall and a services tree for external customers outside the firewall. In a multi-tree environment, you have a flexible resource environment, different schemas, added security, and quicker changes. However, you also have multiple identities, multiple sign-ons, multiple points of administration, and possible data inconsistencies.
![]() Three eDirectory trees—You might consider creating a third tree if you have resources and/or objects that you don’t want to mix with the external services portion of your eBusiness network. Adding more trees resolves political issues about modifying the schema, and enables you to protect your services tree from accidental or intentional damage.
Three eDirectory trees—You might consider creating a third tree if you have resources and/or objects that you don’t want to mix with the external services portion of your eBusiness network. Adding more trees resolves political issues about modifying the schema, and enables you to protect your services tree from accidental or intentional damage.
When using DirXML for multi-tree communications, consider using a DNS-rooted tree for tree federation. The objects in this tree exist in the DNS namespace, and therefore, they’re accessible via the Web. There is one caveat: DNS-rooted trees must live inside the same firewall in order to exchange server and replica information.
When deciding on a tree structure for your eBusiness, remember the design guidelines we explored earlier in Chapter 19, “Novell eDirectory Tree Design.” In summary, we learned that a pyramid shape with geographical top layers and functional bottom layers usually does the trick. However, eBusiness requirements can alter this ideal approach somewhat. Here are some additional guidelines that you should consider when designing a tree structure for eBusiness:
![]() Tree shape—As you design your eBusiness tree, you must decide whether you’re going to have a pyramid or flat shape. Check out the preferred pyramid shape in Figure 22.3. Some of the factors you might consider when designing your eBusiness tree shape include the number of objects you plan in your tree, the potential for growth, and the way your applications will find information. For example, applications prefer a flat structure, but are capable of using a pyramid design if asked to do so. In addition, applications specifically access information more efficiently when the information is placed in a separate container. On the other hand, security management is easier in a pyramid structure because containers create natural groups for rights inheritance. Also, large growth encourages partitioning, and partitioning a flat structure is very difficult. Finally, estimate the number of objects you plan for each organization within your eDirectory tree for a five-year period. Then make eDirectory an access point to your information rather than the actual repository.
Tree shape—As you design your eBusiness tree, you must decide whether you’re going to have a pyramid or flat shape. Check out the preferred pyramid shape in Figure 22.3. Some of the factors you might consider when designing your eBusiness tree shape include the number of objects you plan in your tree, the potential for growth, and the way your applications will find information. For example, applications prefer a flat structure, but are capable of using a pyramid design if asked to do so. In addition, applications specifically access information more efficiently when the information is placed in a separate container. On the other hand, security management is easier in a pyramid structure because containers create natural groups for rights inheritance. Also, large growth encourages partitioning, and partitioning a flat structure is very difficult. Finally, estimate the number of objects you plan for each organization within your eDirectory tree for a five-year period. Then make eDirectory an access point to your information rather than the actual repository.
![]() Tree location—Most eBusiness trees have a central Web site that does not span WANs. However, service companies (such as banks) have service Web sites located in the geographical areas they serve. If geographical distribution is part of your assessment needs, build the tree around these locations. Fundamentally, this means the upper layers of your tree design will be geographical, whereas the lower layers will be functional.
Tree location—Most eBusiness trees have a central Web site that does not span WANs. However, service companies (such as banks) have service Web sites located in the geographical areas they serve. If geographical distribution is part of your assessment needs, build the tree around these locations. Fundamentally, this means the upper layers of your tree design will be geographical, whereas the lower layers will be functional.
![]() Hardware limitations—Although there’s no limit to the number of objects in a given container, you should consider your hardware limitations when creating the most efficient tree design. This is especially true for eBusinesses, because Web server access equals revenue. Make sure that your eDirectory tree design supports the hardware you need to take care of your customers.
Hardware limitations—Although there’s no limit to the number of objects in a given container, you should consider your hardware limitations when creating the most efficient tree design. This is especially true for eBusinesses, because Web server access equals revenue. Make sure that your eDirectory tree design supports the hardware you need to take care of your customers.
![]() Tree population—In an eBusiness environment, you can use one of two methods to populate your tree: You can gather information about your users and populate the tree manually, or you can load an existing database into eDirectory using the LDIF import facility discussed in Chapter 5, “NetWare 6 eDirectory Management.”
Tree population—In an eBusiness environment, you can use one of two methods to populate your tree: You can gather information about your users and populate the tree manually, or you can load an existing database into eDirectory using the LDIF import facility discussed in Chapter 5, “NetWare 6 eDirectory Management.”
![]() Tree administration—Consider creating a separate container so that your server and administration objects are not intermixed with users and/or customer resources. In addition, you should add LDAP server objects and LDAP group objects to this container. Finally, when you partition the tree, make sure to partition this administration container with the Tree Root object.
Tree administration—Consider creating a separate container so that your server and administration objects are not intermixed with users and/or customer resources. In addition, you should add LDAP server objects and LDAP group objects to this container. Finally, when you partition the tree, make sure to partition this administration container with the Tree Root object.
![]() User container—Because users have to log in and might need special rights, consider putting them in separate containers and partitions. As with everything else, this depends on your design and your eBusiness needs. Furthermore, consider separating customers from business partners for security and accessibility purposes.
User container—Because users have to log in and might need special rights, consider putting them in separate containers and partitions. As with everything else, this depends on your design and your eBusiness needs. Furthermore, consider separating customers from business partners for security and accessibility purposes.
Congratulations! You’re now the proud owner of a new eBusiness tree design. Let’s review: tree federation, pyramid, geographical organization, tree population, and customer containers—all done. Well, at least with the rough draft. Next, you must consider how you’re going to optimize partitioning and replica placement for eBusiness.
Our next stop along the eBusiness design tour is partitioning and replication. After the eDirectory tree has been designed, we must break it into little pieces (partitioning) and scatter them around the network (replica placement).
From an eBusiness point of view, partitioning focuses on application accessibility, growth accommodation, and synchronization. In this section, we’ll learn various partition design guidelines for the top and bottom layers of our eDirectory tree. Then we’ll move on to replica placement for eBusiness and discover a variety of strategies for placing replicas to optimize eBusiness fault tolerance, LDAP optimization, and user accessibility.
Let’s start at the beginning with eBusiness partitioning design.
As you learned in Chapters 5 and 17, eDirectory partitioning is one of the most important aspects of eDirectory design because it directly affects your network’s performance, accessibility and fault tolerance. This is especially true when designing eDirectory for eBusiness.
eBusiness places exceptional pressure on the performance of your eDirectory tree because more than just internal employees use it. Your tree becomes the cornerstone of communication between employees, customers, and business partners. As such, you must enhance your partitioning design to accommodate serious eBusiness pressures. Follow these guidelines when partitioning for eBusiness:
![]() Partition before populating tree—You should create your eDirectory partitions before populating the tree with distributed objects. This automates the placement of the objects for efficient synchronization.
Partition before populating tree—You should create your eDirectory partitions before populating the tree with distributed objects. This automates the placement of the objects for efficient synchronization.
![]() Optimize partitions to work with applications and databases—Design your eBusiness tree with few partitions so that applications and databases can easily access the information they need.
Optimize partitions to work with applications and databases—Design your eBusiness tree with few partitions so that applications and databases can easily access the information they need.
![]() Create partitions near users—Create partitions around local servers in each geographic area so that the information is near those using it.
Create partitions near users—Create partitions around local servers in each geographic area so that the information is near those using it.
![]() Don’t span a WAN link—Avoid creating partitions across WAN links because doing so creates unnecessary synchronization traffic between two or more locations.
Don’t span a WAN link—Avoid creating partitions across WAN links because doing so creates unnecessary synchronization traffic between two or more locations.
![]() Partition with future growth in mind—During partitioning design, anticipate future growth and add containers to accommodate object expansion. This enables you to partition around containers when network performance is sluggish. A partition with 500,000 objects is generally manageable, depending upon other factors, such as hardware, synchronization traffic, and geographic distribution.
Partition with future growth in mind—During partitioning design, anticipate future growth and add containers to accommodate object expansion. This enables you to partition around containers when network performance is sluggish. A partition with 500,000 objects is generally manageable, depending upon other factors, such as hardware, synchronization traffic, and geographic distribution.
![]() Partition for efficient synchronization—A well-partitioned eDirectory can synchronize in 30–60 minutes. Try to estimate how long synchronization will take when partitioning for eBusiness. The frequency of changes and the relationships between objects affects the efficiency of synchronization.
Partition for efficient synchronization—A well-partitioned eDirectory can synchronize in 30–60 minutes. Try to estimate how long synchronization will take when partitioning for eBusiness. The frequency of changes and the relationships between objects affects the efficiency of synchronization.
![]() Smaller is better—When building a large tree, or one with potential for growth, maintain the default partition at the tree root level. Then split your tree to two or more partitions as needed. If you create separate containers for administration purposes, partition along those boundaries as well. If you split the load over multiple servers, create partitions only when needed.
Smaller is better—When building a large tree, or one with potential for growth, maintain the default partition at the tree root level. Then split your tree to two or more partitions as needed. If you create separate containers for administration purposes, partition along those boundaries as well. If you split the load over multiple servers, create partitions only when needed.
After you’ve designed an eBusiness partitioning strategy, the next step is to distribute replicas for fault tolerance, network performance, and user accessibility. First and foremost, your replication strategy should increase the availability of partitions by spreading multiple copies of eDirectory to distributed servers. Second, distributed replicas increase eDirectory and client performance by ensuring that eBusiness users access resources locally. Finally, replication enhances user accessibility by distributing applications through filtered replicas.
Follow these guidelines when placing replicas for eBusiness:
![]() Place at least three replicas—Create at least three replicas of your eDirectory tree and distribute them on geographically separated servers. These replicas will enhance your network’s fault tolerance and load balancing, even if the tree structure is flat.
Place at least three replicas—Create at least three replicas of your eDirectory tree and distribute them on geographically separated servers. These replicas will enhance your network’s fault tolerance and load balancing, even if the tree structure is flat.
![]() Create a replica server—Store a full replica of each partition in each replica ring on a single server. This server becomes your eBusiness replica server. This deployment allows eBusiness applications to have central access to all the information they need on a single server, which makes your network operate faster and more efficiently. Then you replicate this configuration on at least two other servers for fault tolerance.
Create a replica server—Store a full replica of each partition in each replica ring on a single server. This server becomes your eBusiness replica server. This deployment allows eBusiness applications to have central access to all the information they need on a single server, which makes your network operate faster and more efficiently. Then you replicate this configuration on at least two other servers for fault tolerance.
![]() Use filtered replicas for application accessibility—Use a filtered replica for applications that access specific types of information. This provides you with an option to increase the distribution of application data when replica placement of the whole partition is not the most efficient use of the server.
Use filtered replicas for application accessibility—Use a filtered replica for applications that access specific types of information. This provides you with an option to increase the distribution of application data when replica placement of the whole partition is not the most efficient use of the server.
![]() Load balance LDAP—LDAP does not load balance itself. To load balance LDAP automatically, consider using Layer 4 switches and distribute LDAP replicas accordingly.
Load balance LDAP—LDAP does not load balance itself. To load balance LDAP automatically, consider using Layer 4 switches and distribute LDAP replicas accordingly.
![]() Place replicas locally—Place replicas on local servers for efficiency and speed. Also consider the type of connection your customers or business partners might be using. If they’re likely to use slow connections, place as many replicas as possible on their geographically closest server.
Place replicas locally—Place replicas on local servers for efficiency and speed. Also consider the type of connection your customers or business partners might be using. If they’re likely to use slow connections, place as many replicas as possible on their geographically closest server.
Well, that completes our discussion of eBusiness partitioning and replication. There’s only one topic remaining—accessibility design—and it almost always gets overlooked. Accessibility transcends everything you do in eBusiness. If you ignore accessibility during the design phase, some users, and even worse, some customers, will invariably get left out in the cold. As a CNE, it’s your job to make sure that this doesn’t happen.
The goal of accessibility design is to simplify user access to network resources. This is even more critical than eBusiness environment because your users are customers. And customers control the financial future of your business.
The main purpose of planning an eBusiness implementation for eDirectory is to accommodate access to corporate applications and databases. When designing your eBusiness tree, consider the needs of the following eDirectory access points:
![]() Directory—DirXML can provide communication between disparate directories, such as Novell eDirectory and Microsoft Active Directory.
Directory—DirXML can provide communication between disparate directories, such as Novell eDirectory and Microsoft Active Directory.
![]() Applications and databases—DirXML can also provide communication between applications and databases, such as PeopleSoft, Oracle, Notes, and Microsoft Exchange.
Applications and databases—DirXML can also provide communication between applications and databases, such as PeopleSoft, Oracle, Notes, and Microsoft Exchange.
![]() Trees—Tree federation can help users access services on another company’s tree. Similarly, DirXML can allow the same object to exist in two isolated trees.
Trees—Tree federation can help users access services on another company’s tree. Similarly, DirXML can allow the same object to exist in two isolated trees.
![]() Servers—You can place specific replicas for applications or databases on a single replica server. In addition, running LDAP on the replica server gives you an additional LDAP access point.
Servers—You can place specific replicas for applications or databases on a single replica server. In addition, running LDAP on the replica server gives you an additional LDAP access point.
![]() Partitions and replicas—You can partition information that you place outside the corporate firewall. Additionally, some applications might require their own space, so consider placing them in their own partition.
Partitions and replicas—You can partition information that you place outside the corporate firewall. Additionally, some applications might require their own space, so consider placing them in their own partition.
![]() Filtered replicas—Filtered replicas enable you to place a portion of a partition inside or outside the corporate firewall.
Filtered replicas—Filtered replicas enable you to place a portion of a partition inside or outside the corporate firewall.
![]() Containers—Applications that share specific needs should be placed in the same container and replicated together.
Containers—Applications that share specific needs should be placed in the same container and replicated together.
![]() Groups—Sometimes you need to use groups to accommodate additional security for related objects within a container.
Groups—Sometimes you need to use groups to accommodate additional security for related objects within a container.
![]() URLs—Some applications might use URLs as access points. Make sure that they are securely accessible from outside your corporate firewall.
URLs—Some applications might use URLs as access points. Make sure that they are securely accessible from outside your corporate firewall.
![]() Attributes—eDirectory attributes allow your customers to search for individual resources by Common Name (CN).
Attributes—eDirectory attributes allow your customers to search for individual resources by Common Name (CN).
![]() Auxiliary classes—Auxiliary classes enable you to group and place attributes on specific classes of objects. These attributes allow applications to locate objects on individual configurations. Remember, you must extend the schema to initialize auxiliary classes.
Auxiliary classes—Auxiliary classes enable you to group and place attributes on specific classes of objects. These attributes allow applications to locate objects on individual configurations. Remember, you must extend the schema to initialize auxiliary classes.
Your corporate firewall plays an important role in allowing or disallowing user access to the eBusiness points just described. In addition, the firewall plays an important part in securing your eBusiness Web site, delivering LDAP, and accessing applications.
As you can see in Figure 22.4, you can extend your eDirectory tree beyond the corporate firewall to allow your eBusiness services secure access to valuable eDirectory data. However, when you extend your tree beyond the firewall, you should keep the design outside the firewall small and simple. Also, allow only your Web server to have internal access through the firewall; don’t extend this capability directly to users and business partners. Finally, put only data that does not require any security outside the firewall.
Congratulations! You’ve built an eDirectory design specifically for eBusiness. Wow, that is quite an accomplishment. Believe me, your employees, customers, and business partners will thank you with greater efficiency, productivity, and profitability.
Let’s review: First, we started with a tree design optimized for B2B and B2C communications. Then, we refined our design to integrate applications, anticipate growth, and provide simpler customer accessibility. After that, we partitioned the tree into smaller pieces to distribute applications closest to the users who need them. Next, we replicated those pieces and scattered them for fault tolerance and improved network performance. Finally, we optimized our user accessibility design with several access points and secure firewall protection.
Now that your eBusiness design is complete, it’s time for the final step: eDirectory implementation. It’s time for action!
Test Objectives Covered:
![]() Implement the Network Infrastructure (continued)
Implement the Network Infrastructure (continued)
![]() Create a User Accessibility Needs Strategy for eBusiness (continued)
Create a User Accessibility Needs Strategy for eBusiness (continued)
![]() Implement the eDirectory Tree Structure (continued)
Implement the eDirectory Tree Structure (continued)
![]() Implement a Partition and Replica Strategy for Your eDirectory Tree (continued)
Implement a Partition and Replica Strategy for Your eDirectory Tree (continued)
As you learned in the preceding chapter, eDirectory implementation transcends all other design tasks. This is prime time!
eDirectory implementation for eBusiness gives you the opportunity to put all of your preparation and design work into action. After you’ve designed your tree, you must install the servers, build the tree, place the resources, and implement a user environment plan (UEP). Before you can jump into action, you must gather information about your company, your customers, and your business partners.
Data gathering and needs analysis is an important part of eDirectory implementation. In addition to the typical eDirectory design inputs (discussed in Chapter 18), you’ll need to further analyze the needs of your eBusiness. For example, what applications are you going to run and who will be accessing them? How many objects will you have to accommodate for your customers and/or business partners? What are the security relationships between internal and external objects? All these questions must be answered before you can tackle eDirectory implementation for eBusiness.
In Chapter 21, “Novell eDirectory Implementation,” we explored the four phases of eDirectory implementation. Now, let’s review them from an eBusiness point of view:
![]() Phase 1: Building the eDirectory tree—In Chapter 19, you learned how to create a preliminary eDirectory tree design. The top layers should be location based and the bottom layers should be functional. In this chapter, we enhanced this design from an eBusiness perspective. Now, during eDirectory implementation, you get an opportunity to build the design using several NetWare 6 utilities. Make sure to follow the guidelines presented in this chapter when building the eDirectory tree for eBusiness.
Phase 1: Building the eDirectory tree—In Chapter 19, you learned how to create a preliminary eDirectory tree design. The top layers should be location based and the bottom layers should be functional. In this chapter, we enhanced this design from an eBusiness perspective. Now, during eDirectory implementation, you get an opportunity to build the design using several NetWare 6 utilities. Make sure to follow the guidelines presented in this chapter when building the eDirectory tree for eBusiness.
![]() Phase 2: Managing eDirectory partitions—In Chapter 5, you learned how to create and distribute eDirectory partitions and replicas. When your network servers are up and running, you can use iMonitor to make additional partitions and distribute them as replicas. In this chapter, we discovered some time-proven guidelines for partitioning and replication from an eBusiness perspective. Make sure to follow these rules when implementing your eBusiness partitioning strategy.
Phase 2: Managing eDirectory partitions—In Chapter 5, you learned how to create and distribute eDirectory partitions and replicas. When your network servers are up and running, you can use iMonitor to make additional partitions and distribute them as replicas. In this chapter, we discovered some time-proven guidelines for partitioning and replication from an eBusiness perspective. Make sure to follow these rules when implementing your eBusiness partitioning strategy.
![]() Phase 3: Merging eDirectory trees—In Chapter 21, we studied detailed eDirectory merging considerations and step-by-step instructions. In many cases, you might need to merge multiple eDirectory trees into a unified network as part of your implementation strategy. However, you learned in this chapter that eBusiness encourages communication between separate trees by using DirXML and tree federation. Make sure to study the eBusiness benefits of separate trees before eDirectory merging.
Phase 3: Merging eDirectory trees—In Chapter 21, we studied detailed eDirectory merging considerations and step-by-step instructions. In many cases, you might need to merge multiple eDirectory trees into a unified network as part of your implementation strategy. However, you learned in this chapter that eBusiness encourages communication between separate trees by using DirXML and tree federation. Make sure to study the eBusiness benefits of separate trees before eDirectory merging.
![]() Phase 4: Implementing a user environment plan—Finally, you should implement a UEP to manage how users will access Directory resources on your new network. When building a UEP for eBusiness, consider the data access needs of your customers and the ways in which they use your applications. This requires a detailed strategy for delivering secure access points and supporting firewall communications. Make sure to follow the guidelines outlined in the previous lesson when you implement your eBusiness UEP.
Phase 4: Implementing a user environment plan—Finally, you should implement a UEP to manage how users will access Directory resources on your new network. When building a UEP for eBusiness, consider the data access needs of your customers and the ways in which they use your applications. This requires a detailed strategy for delivering secure access points and supporting firewall communications. Make sure to follow the guidelines outlined in the previous lesson when you implement your eBusiness UEP.
Congratulations! You’ve completed CNE Study Guide for NetWare 6. Wow, what a journey! You should be very proud of yourself.
You made it!! You’ve successfully traversed the entire NetWare 6 CNE program (or at least most of it). In this comprehensive CNE study guide, we covered the following three courses:
![]() Part I: Novell Network Management for NetWare 6 (Novell Course 3004)—In Part I, we built on the Fundamentals of Novell Networking (Novell Course 3001) with a plethora of advanced CNE tasks, including installation, migration, IP services, and Novell’s Internet infrastructure. At the core of Part I, we tackled four advanced management arenas: advanced server management, advanced client management, advanced eDirectory management, and advanced security management. Finally, we completed Novell Course 3004 with a comprehensive look at NetWare 6 optimization and the NetWare troubleshooting model.
Part I: Novell Network Management for NetWare 6 (Novell Course 3004)—In Part I, we built on the Fundamentals of Novell Networking (Novell Course 3001) with a plethora of advanced CNE tasks, including installation, migration, IP services, and Novell’s Internet infrastructure. At the core of Part I, we tackled four advanced management arenas: advanced server management, advanced client management, advanced eDirectory management, and advanced security management. Finally, we completed Novell Course 3004 with a comprehensive look at NetWare 6 optimization and the NetWare troubleshooting model.
![]() Part II: Advanced Novell Network Management with NetWare 6 (Novell Course 3005)—In Part II, we shifted our focus from advanced management to advanced troubleshooting. As a CNE troubleshooter, you mastered NetWare 6 migration, advanced storage maintenance, iFolder troubleshooting, high availability with NCS, server troubleshooting, and advanced eDirectory troubleshooting. And don’t forget your CNE medical bag full of troubleshooting tools.
Part II: Advanced Novell Network Management with NetWare 6 (Novell Course 3005)—In Part II, we shifted our focus from advanced management to advanced troubleshooting. As a CNE troubleshooter, you mastered NetWare 6 migration, advanced storage maintenance, iFolder troubleshooting, high availability with NCS, server troubleshooting, and advanced eDirectory troubleshooting. And don’t forget your CNE medical bag full of troubleshooting tools.
![]() Part III: Novell eDirectory Design and Implementation (Novell Course 575)—In Part III, we expanded our NetWare 6 LAN into the realm of global eDirectory connectivity. We mastered the first three steps in saving the Net—namely, eDirectory preparation, eDirectory design, and eDirectory implementation. In the first step, we gathered ACME data and built a project team. Then, in step 2, we constructed ACME’s eDirectory tree with the help of naming standards, tree design guidelines, and resource accessibility. Finally, in step 3, we executed the plan with a comprehensive eDirectory implementation schedule.
Part III: Novell eDirectory Design and Implementation (Novell Course 575)—In Part III, we expanded our NetWare 6 LAN into the realm of global eDirectory connectivity. We mastered the first three steps in saving the Net—namely, eDirectory preparation, eDirectory design, and eDirectory implementation. In the first step, we gathered ACME data and built a project team. Then, in step 2, we constructed ACME’s eDirectory tree with the help of naming standards, tree design guidelines, and resource accessibility. Finally, in step 3, we executed the plan with a comprehensive eDirectory implementation schedule.
All in a day’s work. With these great skills, there’s no limit to where you can go from here!
Well, that does it! The End...Finito...Kaput. Everything you wanted to know about NetWare 6, but were afraid to ask. I hope you’ve had as much fun reading this book as I’ve had writing it. It’s been a long and winding road—a life changer. Thanks for spending the last 1,400 pages with me, and I bid you a fond farewell in the only way I know how:
“Cheers!”
“The pleasure has been all mine!”
“God Doesn’t Play Dice with the Universe!”
“So long and thanks for all the fish!”
“Live Well!”
“May the force be with you...”
“Where we go from here is a choice I leave to you......”
—David James Clarke IV ![]()