Microsoft consolidated the kind of security features that are common to many Microsoft Office programs in a dialog box it calls the Trust Center. Click the File tab, click Options, and then click Trust Center to display the dialog box shown in the background in Figure 4-1.
This category in the Excel Options dialog box contains links to disclaimers and declarations on the Web. Click the Trust Center Settings button to open the dialog box in the foreground in Figure 4-1, where the security settings live.
Note
If you work in an organization, the Trust Center might contain default settings specified by your network administrator that you cannot (or should not) modify. Contact your friendly internal administrator for more information.
The settings you can configure in the Trust Center determine how Excel responds when you open a file with active content—that is, any external file that contains links or code used to communicate with another location on the Internet or an intranet. When you open such a file, Excel investigates several measures of trustworthiness. Rules exist by which a publisher attains trusted status. Defined as reputable developers, trusted publishers must sign their code by using valid, current digital signatures that are issued by certified certificate authorities such as IntelliSafe. If you open a file that does not meet one of these criteria, a security alert appears, and you need to decide whether to run the active content anyway. But even if you add a publisher, unsigned code from that publisher still triggers a security alert. Most of the areas in the Trust Center dialog box deal with issues that directly affect the triggering of security alerts and the ability to run active content.
When you open a workbook with issues, Excel displays relevant security alerts and messages in the Message Bar, which appears right above the formula bar, as shown in Figure 4-2. Each message corresponds to a problem lurking within the file, and each includes a button offering a possible resolution. As you can see in Figure 4-2, the Message Bar can contain more than one message.
Note
For more information about code signing, see Using Digital Signatures on page 122.
Note
When you open a workbook with active content or other issues, any unresolved messages or alerts that appear in the Message Bar also appear in the Info category when you click the File tab.
A “publisher” is a software developer, which can range in relative scale and trustworthiness from a kid with a laptop to Microsoft. You might know the kid, and you might not trust Microsoft. Whatever the case, you can apply your unique level of paranoia by adding or deleting publishers and locations using the first two categories in the Trust Center dialog box. Excel populates the Trusted Publishers list whenever you open a macro or add-in for the first time that triggers a security alert. If you decide to enable the content, Excel adds the publisher to the list. Subsequent active content from the same publisher opens without triggering a security alert.
Trusted locations can be folders on your own hard disk or on a network; the more precise, the better. We recommend you designate trusted locations at the subfolder level—even the default Documents folder (a.k.a. The Folder Formerly Known As My Documents) is too broad, particularly if you work in a networked environment. It is better to designate subfolders of Documents—or better yet, use folders outside the Documents folder entirely—to minimize the ease with which others can locate interesting stuff on your computer to steal or to modify. Several trusted locations are installed with Excel, such as subfolder locations for template and startup files, as shown earlier in Figure 4-1.
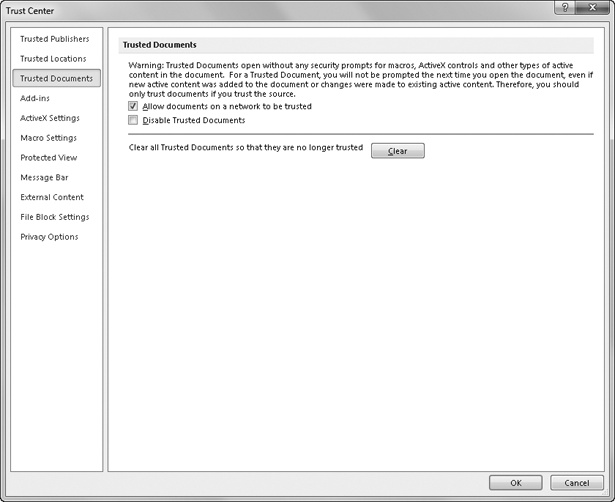
Each time you open a document that triggers a security alert and enable its content by clicking the Enable Content button in the Message Bar, you add the name of the document to the Trusted Documents list. The security alert no longer appears on subsequent openings. You can reset the Trusted Documents list (which actually appears nowhere) by clicking the Trusted Documents category in the Trust Center dialog box and clicking the Clear button, shown in Figure 4-3. Here you can also disable Trusted Documents (the feature, not the documents themselves) and choose to allow or deny global “trusted” status to all the documents that exist on your network.
The Add-Ins, ActiveX Settings, and Macro Settings categories in the Trust Center, as shown in Figure 4-4, deal with blocking active content. You have only two choices for add-ins: just disable them all or require them to be from a trusted publisher. If you decide on the latter, you can additionally disable the usual Message Bar notification when an add-in is unsigned.
Figure 4-4. Using the options in the Add-Ins, ActiveX Settings, and Macro Settings categories, you can enable or disable most types of active content that you might encounter.
ActiveX controls are more general than add-ins, and they can be designed to run on the Web or on your computer but always within a host application. ActiveX has been the language of choice for many malicious code developers (a.k.a. hackers) because it allows nearly unlimited access to your computer. You should never allow ActiveX controls without restriction—the minimum protection option should be Prompt Me Before Enabling All Controls With Minimal Restrictions. The option that mentions Safe For Initialization (SFI) controls refers to a sort of internal code-signing protocol set by the developer to verify its safety. Choosing this option puts code through a few more levels of restriction. The best solution if you want to stay safe yet you need to use certain ActiveX controls is to set up or utilize a trusted location to store the ActiveX controls you know to be safe.
Tip
INSIDE OUT Of Web Beacons and Homograph Attacks
The word exploits, which used to conjure images of heroic figures and derring-do, has come to describe the actions of malicious software. Phishing is a rather clever type of lure used by hackers trolling for data to reel unsuspecting prey into their virtual creels. Homographs use the extended international character set to create scam Web sites with Uniform Resource Locators (URLs) that replace one or more English-alphabet letters in the real domain names with similar ones from another language’s character set. You see what you think is a trusted URL, but if you access the site, you might end up sharing information with the phishermen instead of the trusted site. Where homographs are designed to lure you in, web beacons might be what you “win” after you get there. These are forms of spyware that infiltrate your system and then just sit there transmitting data—beacons of information—to malicious data-mining operations. These are just a few of the many clever methods being employed to rip you off. The Trust Center addresses some grim realities of this insecure world, but, of course, it shouldn’t be your only line of defense. Unfortunately, every Internet-connected computer needs to have an automatically updating antiviral/firewall application installed to fend off current and future exploits.
You can read more about all this in the Help system. The easiest way to get to the relevant topics is to open the Trust Center dialog box and then click the Help button (the little question mark icon in the upper-right corner) to display a Help topic about the currently active category.
Unlike ActiveX controls, macros are application-specific, but they can be destructive when they emanate from a malicious coder. The Trust Center Macro Settings category reveals options that are similar to those of ActiveX controls, as are the recommendations. The Trust Access To The VBA Project Object Model option is for developers only but might be desirable in a development environment where a shared Visual Basic for Applications project object model is known to be secure and isolated.
The Message Bar category in the Trust Center dialog box simply lets you turn off the display of security alerts in the Message Bar. It does not turn off the actual security features, just the notifications. The Message Bar is ordinarily turned on, unless you opt to disable all macros. ActiveX controls still generate their own security alerts.
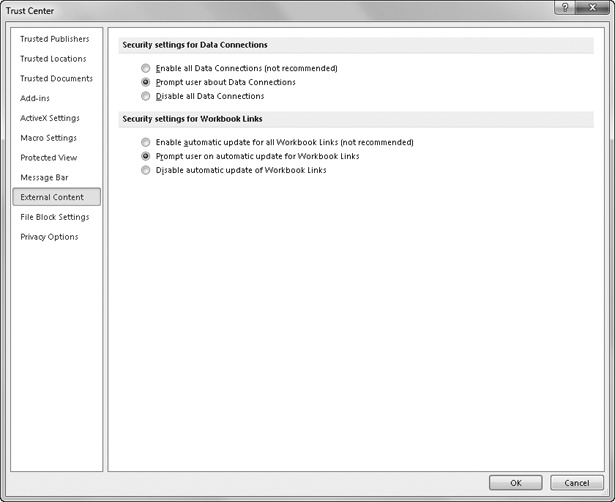
External content comes in many flavors, and people can use it in many ways to implement malicious intent. The Trust Center dialog box can intercept potential problems by blocking external content such as data connections, hyperlinks, and images, all of which can contain or facilitate malicious code. Figure 4-5 shows the External Content category of the Trust Center dialog box.
Figure 4-5. The External Content category contains settings that control data connections and links.
The real difference between the two sets of External Content options is that data connections are links to data from other programs, such as databases, while workbook links are external references used between Excel workbooks. If you do not control or do not have confidence in the linked or connected sources, it’s best to go with the default settings, prompting you for a decision whenever external content is encountered. As with most of these Trust Center options, allowing all data connections or workbook links is not recommended.
Excel 2010 allows you to disable the opening and/or saving of any individual file type it recognizes. The File Block Settings category in the Trust Center dialog box, shown in Figure 4-6, includes a list of file types that Excel recognizes, each with check boxes allowing you to block its opening or saving. Use the options below the list to select the way you’d like Excel to handle the opening of selected file types. You can block a file type by clicking Do Not Open Selected File Types or choose to open the file in Protected View, either read-only or editable.
If you want to restore the default file-block settings, which include the blockage of several old Excel file formats, click the Restore Defaults button. Some of the listed formats do not include a check box to block saving, either because it doesn’t work (dBase III/IV), or because several older formats have been subsumed into one newer format (Excel 2 through Excel 4 into Excel 95).
Excel 2010 includes more interactive features than ever. Excel uses the Internet behind the scenes to give you access to all the information you need at a moment’s notice. Many people want to know exactly when their computer is retrieving online information, so Microsoft lets you control these interactions by clicking the File tab, clicking Options, clicking Trust Center, and then clicking Trust Center Settings. In the Trust Center dialog box, click the Privacy Options category to display the dialog box shown in Figure 4-7.
Figure 4-7. If you are uncomfortable with Excel connecting automatically to the Web, you can specify otherwise.
The first set of options you see in Figure 4-7 control whether Excel can automatically communicate and share information over the Internet under various circumstances:
Connect To Office.com For Updated Content When I’m Connected To The Internet You might prefer to take control of Web interactions yourself, for example, if you use a dial-up Internet connection. If you clear this check box, you can still connect to the online Help content from within the Help dialog box. This also controls whether Excel automatically displays Web-based templates in the New category on the File menu.
Download A File Periodically That Helps Determine System Problems You need to decide whether to allow Microsoft to send diagnostic programs to your computer. If you worry about losing data to system crashes, you can select this check box to aid in any future system rehab and recovery efforts.
Sign Up For The Customer Experience Improvement Program Over the years, Microsoft’s on-site usability lab has been instrumental in helping refine products based on how people actually work. The Customer Experience Improvement Program is similar, except that instead of conducting tests in a controlled environment on the Microsoft corporate campus, data is accumulated in a collective “lab” that potentially includes your office. The usage data collected by this program is much more useful than that generated in the artificial environment of a laboratory. This program began with Excel 2003 and has been partially responsible for the changes you see in Excel 2010. It’s kind of like installing a Nielsen ratings box on your television—yes, you’re sharing information with them, but maybe the TV shows will get better.
Automatically Detect Installed Office Applications To Improve Office.com Search Results It’s hard to figure exactly how the applications you have installed might alter search results, but you can make a decision about it nonetheless.
Check Microsoft Office Documents That Are From Or Link To Suspicious Web Sites This option turns on what Microsoft calls spoofed Web site detection. This refers to a homograph-type phishing scheme using Web domain names that closely resemble trusted sites. It’s often hard to tell the difference with the naked eye, so you can let Excel do it for you. (See the sidebar “Of Web Beacons and Homograph Attacks” on page 116.)
Allow the Research Task Pane To Check For And Install New Services This option controls whether Excel automatically connects to the Web-based resources necessary for the operation of the tools made available by clicking the Research, Thesaurus, or Translate buttons on the Review tab.
Allow Sending Files To Improve File Validation If a file fails the built-in file format validation process, you’re prompted to send file validation information to Microsoft if this option remains selected.
For all these privacy issues, Microsoft won’t collect any personal information and promises that participants remain completely anonymous. You might want to return to the Excel Options dialog box and read the linked information in the Trust Center category before deciding whether to select these check boxes.
Tip
INSIDE OUT Of File Format Attacks and File Validation
Another flavor of malicious exploit is the file format attack. New in Excel 2010, Office File Validation helps detect file format attacks, which attempt to insert remotely triggered code bits by modifying the structure of a file. Interestingly, there is a short list of binary file types that are favorites for these attacks, including Excel 97-2003 Workbooks and Templates and Excel 5.0/95 files. Office File Validation checks these and others on the most-wanted list against a predefined set of rules, or schema, that defines the structure of each file type. Validation fails if the file does not conform to the rules. You are prompted to send validation information to Microsoft if a file fails validation. Clear the Allow Sending Files To Improve File Validation option on the Privacy Options page of the Trust Center if you’d rather not share and would rather not see the prompt.